Remove obsolete files/folders
This commit is contained in:
parent
6af743c99c
commit
38db586d5a
@ -1,209 +0,0 @@
|
||||
{
|
||||
"$schema": "https://schema.management.azure.com/schemas/2015-01-01/deploymentTemplate.json#",
|
||||
"contentVersion": "1.0.0.0",
|
||||
"parameters": {
|
||||
"SitesEshopfunctionsName": {
|
||||
"type": "string",
|
||||
"metadata": {
|
||||
"description": "Name of the Azure Functions namespace"
|
||||
},
|
||||
"defaultValue": "mktfunctionsdemo"
|
||||
}
|
||||
},
|
||||
"variables": {
|
||||
"SitesEshopfunctionsName": "[parameters('SitesEshopfunctionsName')]",
|
||||
"WebConfigName": "[concat(variables('SitesEshopfunctionsName'), '/web')]",
|
||||
"Location": "[resourceGroup().location]",
|
||||
"ServerFarmPlan": "[concat(trim(variables('location')), 'Plan')]",
|
||||
"StorageAccounts": "[concat(variables('SitesEshopfunctionsName'), 'st')]"
|
||||
},
|
||||
"resources": [
|
||||
{
|
||||
"type": "Microsoft.Storage/storageAccounts",
|
||||
"sku": {
|
||||
"name": "Standard_LRS",
|
||||
"tier": "Standard"
|
||||
},
|
||||
"kind": "Storage",
|
||||
"name": "[variables('StorageAccounts')]",
|
||||
"apiVersion": "2016-01-01",
|
||||
"location": "[variables('Location')]",
|
||||
"tags": {},
|
||||
"scale": null,
|
||||
"properties": {},
|
||||
"dependsOn": []
|
||||
},
|
||||
{
|
||||
"type": "Microsoft.Web/serverfarms",
|
||||
"sku": {
|
||||
"name": "Y1",
|
||||
"tier": "Dynamic",
|
||||
"size": "Y1",
|
||||
"family": "Y",
|
||||
"capacity": 0
|
||||
},
|
||||
"kind": "functionapp",
|
||||
"name": "[variables('ServerFarmPlan')]",
|
||||
"apiVersion": "2015-08-01",
|
||||
"location": "[variables('Location')]",
|
||||
"scale": null,
|
||||
"properties": {
|
||||
"name": "[variables('ServerFarmPlan')]",
|
||||
"numberOfWorkers": 0
|
||||
},
|
||||
"dependsOn": []
|
||||
},
|
||||
{
|
||||
"type": "Microsoft.Web/sites",
|
||||
"kind": "functionapp",
|
||||
"name": "[variables('SitesEshopfunctionsName')]",
|
||||
"apiVersion": "2015-08-01",
|
||||
"location": "[variables('Location')]",
|
||||
"scale": null,
|
||||
"properties": {
|
||||
"name": "[variables('SitesEshopfunctionsName')]",
|
||||
"hostNames": [
|
||||
"[concat(variables('SitesEshopfunctionsName'),'.azurewebsites.net')]"
|
||||
],
|
||||
"enabledHostNames": [
|
||||
"[concat(variables('SitesEshopfunctionsName'),'.azurewebsites.net')]",
|
||||
"[concat(variables('SitesEshopfunctionsName'),'.scm.azurewebsites.net')]"
|
||||
],
|
||||
"hostNameSslStates": [
|
||||
{
|
||||
"name": "[concat(variables('SitesEshopfunctionsName'),'.azurewebsites.net')]",
|
||||
"sslState": 0,
|
||||
"thumbprint": null,
|
||||
"ipBasedSslState": 0
|
||||
},
|
||||
{
|
||||
"name": "[concat(variables('SitesEshopfunctionsName'),'.scm.azurewebsites.net')]",
|
||||
"sslState": 0,
|
||||
"thumbprint": null,
|
||||
"ipBasedSslState": 0
|
||||
}
|
||||
],
|
||||
"serverFarmId": "[resourceId('Microsoft.Web/serverfarms', variables('ServerFarmPlan'))]"
|
||||
},
|
||||
"dependsOn": [
|
||||
"[resourceId('Microsoft.Web/serverfarms', variables('ServerFarmPlan'))]"
|
||||
]
|
||||
},
|
||||
{
|
||||
"type": "Microsoft.Web/sites/config",
|
||||
"name": "[variables('WebConfigName')]",
|
||||
"apiVersion": "2015-08-01",
|
||||
"location": "[variables('Location')]",
|
||||
"scale": null,
|
||||
"properties": {
|
||||
"numberOfWorkers": 1,
|
||||
"defaultDocuments": [
|
||||
"Default.htm",
|
||||
"Default.html",
|
||||
"Default.asp",
|
||||
"index.htm",
|
||||
"index.html",
|
||||
"iisstart.htm",
|
||||
"default.aspx",
|
||||
"index.php",
|
||||
"hostingstart.html"
|
||||
],
|
||||
"netFrameworkVersion": "v4.0",
|
||||
"phpVersion": "5.6",
|
||||
"pythonVersion": "",
|
||||
"nodeVersion": "",
|
||||
"linuxFxVersion": "",
|
||||
"requestTracingEnabled": false,
|
||||
"remoteDebuggingEnabled": false,
|
||||
"remoteDebuggingVersion": null,
|
||||
"httpLoggingEnabled": false,
|
||||
"logsDirectorySizeLimit": 35,
|
||||
"detailedErrorLoggingEnabled": false,
|
||||
"publishingUsername": "$eshopfunctions",
|
||||
"publishingPassword": null,
|
||||
"appSettings": null,
|
||||
"metadata": null,
|
||||
"connectionStrings": null,
|
||||
"machineKey": null,
|
||||
"handlerMappings": null,
|
||||
"documentRoot": null,
|
||||
"scmType": "None",
|
||||
"use32BitWorkerProcess": true,
|
||||
"webSocketsEnabled": false,
|
||||
"alwaysOn": false,
|
||||
"javaVersion": null,
|
||||
"javaContainer": null,
|
||||
"javaContainerVersion": null,
|
||||
"appCommandLine": "",
|
||||
"managedPipelineMode": 0,
|
||||
"virtualApplications": [
|
||||
{
|
||||
"virtualPath": "/",
|
||||
"physicalPath": "site\\wwwroot",
|
||||
"preloadEnabled": false,
|
||||
"virtualDirectories": null
|
||||
}
|
||||
],
|
||||
"winAuthAdminState": 0,
|
||||
"winAuthTenantState": 0,
|
||||
"customAppPoolIdentityAdminState": false,
|
||||
"customAppPoolIdentityTenantState": false,
|
||||
"runtimeADUser": null,
|
||||
"runtimeADUserPassword": null,
|
||||
"loadBalancing": 1,
|
||||
"routingRules": [],
|
||||
"experiments": {
|
||||
"rampUpRules": []
|
||||
},
|
||||
"limits": null,
|
||||
"autoHealEnabled": false,
|
||||
"autoHealRules": {
|
||||
"triggers": null,
|
||||
"actions": null
|
||||
},
|
||||
"tracingOptions": null,
|
||||
"vnetName": "",
|
||||
"siteAuthEnabled": false,
|
||||
"siteAuthSettings": {
|
||||
"enabled": null,
|
||||
"unauthenticatedClientAction": null,
|
||||
"tokenStoreEnabled": null,
|
||||
"allowedExternalRedirectUrls": null,
|
||||
"defaultProvider": null,
|
||||
"clientId": null,
|
||||
"clientSecret": null,
|
||||
"issuer": null,
|
||||
"allowedAudiences": null,
|
||||
"additionalLoginParams": null,
|
||||
"isAadAutoProvisioned": false,
|
||||
"googleClientId": null,
|
||||
"googleClientSecret": null,
|
||||
"googleOAuthScopes": null,
|
||||
"facebookAppId": null,
|
||||
"facebookAppSecret": null,
|
||||
"facebookOAuthScopes": null,
|
||||
"twitterConsumerKey": null,
|
||||
"twitterConsumerSecret": null,
|
||||
"microsoftAccountClientId": null,
|
||||
"microsoftAccountClientSecret": null,
|
||||
"microsoftAccountOAuthScopes": null
|
||||
},
|
||||
"cors": {
|
||||
"allowedOrigins": [
|
||||
"https://functions.azure.com",
|
||||
"https://functions-staging.azure.com",
|
||||
"https://functions-next.azure.com"
|
||||
]
|
||||
},
|
||||
"push": null,
|
||||
"apiDefinition": null,
|
||||
"autoSwapSlotName": null,
|
||||
"localMySqlEnabled": false,
|
||||
"ipSecurityRestrictions": null
|
||||
},
|
||||
"dependsOn": [
|
||||
"[resourceId('Microsoft.Web/sites', variables('SitesEshopfunctionsName'))]"
|
||||
]
|
||||
}
|
||||
]
|
||||
}
|
||||
@ -1,9 +0,0 @@
|
||||
{
|
||||
"$schema": "https://schema.management.azure.com/schemas/2015-01-01/deploymentParameters.json#",
|
||||
"contentVersion": "1.0.0.0",
|
||||
"parameters": {
|
||||
"SitesEshopfunctionsName": {
|
||||
"value": "eshopfunctionsapp"
|
||||
}
|
||||
}
|
||||
}
|
||||
@ -1,39 +0,0 @@
|
||||
# Deploying Azure Functions
|
||||
|
||||
The ARM template `azurefunctionsdeploy.json` and its parameter file (`azurefunctionsdeploy.parameters.json`) are used to deploy Marketing azure functions.
|
||||
|
||||
## Editing azurefunctionsdeploy.parameters.json file
|
||||
|
||||
You can edit the `azurefunctionsdeploy.parameters.parameters.json` file to set your values, but is not needed. The only parameter that can be set is:
|
||||
|
||||
1. `SitesEshopfunctionsName` is a string that is used to create the Azure function app name.
|
||||
|
||||
## Deploy the template
|
||||
|
||||
Once parameter file is edited you can deploy it using [create-resources script](../readme.md).
|
||||
|
||||
i. e. if you are in Windows, to deploy the Azure Functions environment in a new resourcegroup located in westus, go to `deploy\az` folder and type:
|
||||
|
||||
```
|
||||
create-resources.cmd azurefunctions\azurefunctionsdeploy newResourceGroup -c westus
|
||||
```
|
||||
## Deploy Marketing azure function with Visual Studio.
|
||||
|
||||
You need to deploy the Marketing azure function from Visual Studio 2017 15.3 from the the Marketing-functions project in the solution eShopOnContainers-AzureFunctions.sln (Visual Studio publish tool).
|
||||
|
||||
## Setting Azure function configurations
|
||||
|
||||
Once deployed, go to azure portal and set the connection string for the azure function under the name "SqlConnection". The value must be the connection string which points to MarketingDB.
|
||||
|
||||
Example:
|
||||
|
||||
"SqlConnection": "Server=tcp:eshopsql.database.windows.net,1433;Initial Catalog=marketingdb;"
|
||||
|
||||
In appsettings section, add a new entry named "MarketingStorageUri". The value must be the uri of the blob storage where the campaign images are stored.
|
||||
|
||||
Example:
|
||||
|
||||
"MarketingStorageUri": "https://marketingcampaign.blob.core.windows.net/pics/"
|
||||
|
||||
|
||||
|
||||
@ -1,53 +0,0 @@
|
||||
Param(
|
||||
[parameter(Mandatory=$true)][string]$vaultName,
|
||||
[parameter(Mandatory=$true)][string]$certName,
|
||||
[parameter(Mandatory=$true)][string]$certPwd,
|
||||
[parameter(Mandatory=$true)][string]$subjectName,
|
||||
[parameter(Mandatory=$false)][string]$ValidityInMonths=12,
|
||||
[parameter(Mandatory=$true)][string]$saveDir
|
||||
)
|
||||
|
||||
|
||||
#Log in Azure Account
|
||||
Login-AzureRmAccount
|
||||
|
||||
|
||||
# Create Cert in KeyVault
|
||||
Write-Host "Creating certificate in Azure KeyVault..." -ForegroundColor Yellow
|
||||
$policy = New-AzureKeyVaultCertificatePolicy -SubjectName $subjectName -IssuerName Self -ValidityInMonths $ValidityInMonths
|
||||
Add-AzureKeyVaultCertificate -VaultName $vaultName -Name $certName -CertificatePolicy $policy
|
||||
|
||||
# Downloading Certificate
|
||||
Write-Host "Downloading Certificate from KeyVault..." -ForegroundColor Yellow
|
||||
|
||||
$Stoploop = $false
|
||||
$Retrycount = 0
|
||||
|
||||
do {
|
||||
try {
|
||||
|
||||
$kvSecret = Get-AzureKeyVaultSecret -VaultName $vaultName -Name $certName -ErrorAction SilentlyContinue
|
||||
$kvSecretBytes = [System.Convert]::FromBase64String($kvSecret.SecretValueText)
|
||||
$certCollection = New-Object System.Security.Cryptography.X509Certificates.X509Certificate2Collection
|
||||
$certCollection.Import($kvSecretBytes,$null,[System.Security.Cryptography.X509Certificates.X509KeyStorageFlags]::Exportable)
|
||||
$protectedCertificateBytes = $certCollection.Export([System.Security.Cryptography.X509Certificates.X509ContentType]::Pkcs12, $certPwd)
|
||||
[System.IO.File]::WriteAllBytes($saveDir + "\" + $certName + ".pfx", $protectedCertificateBytes)
|
||||
|
||||
$Stoploop = $true
|
||||
Write-Host "Finished!" -ForegroundColor Yellow
|
||||
}
|
||||
catch {
|
||||
if ($Retrycount -gt 5){
|
||||
$Stoploop = $true
|
||||
Write-Host "Not possible to retrieve the certificate!" -ForegroundColor Yellow
|
||||
}
|
||||
else {
|
||||
Start-Sleep -Seconds 20
|
||||
$Retrycount = $Retrycount + 1
|
||||
}
|
||||
}
|
||||
}
|
||||
While ($Stoploop -eq $false)
|
||||
|
||||
# Show Certificate Values
|
||||
Get-AzureKeyVaultCertificate -VaultName $vaultName -Name $certName
|
||||
@ -1,134 +0,0 @@
|
||||
# Deploying a Service Fabric cluster based on Linux nodes
|
||||
|
||||
## A. Unsecured cluster (SF Linux cluster)
|
||||
For a secured cluster, see option B. below.
|
||||
|
||||
You can always deploy a SF cluster through the Azure portal, as explained in this article: https://docs.microsoft.com/en-us/azure/service-fabric/service-fabric-get-started-azure-cluster
|
||||
|
||||
However, when creating a cluster, there are quite a few configurations to take into account, like enabling the internal DNS service or Reverse Proxy service, choosing between Linux/Windows, open/publish your application ports in the load-balancer and most of all (the most complex setup) how to create a secure cluster.
|
||||
|
||||
Because of those reasons, we have created a set of ARM templates and scripts so you can create, re-create and configure the SF clusters much faster, as explained below:
|
||||
|
||||
Within eShopOnContainers root folder, at the folder [..\deploy\az\servicefabric\LinuxContainers](https://github.com/dotnet-architecture/eShopOnContainers/tree/dev/deploy/az/servicefabric/LinuxContainers), you can find the ARM template `servicefabricdeploy.json` and its parameters file (`servicefabricdeploy.parameters.json`) to create a Service Fabric cluster environment for Linux Containers.
|
||||
|
||||
## Edit the servicefabricdeploy.parameters.json file
|
||||
|
||||
Edit the following params in `servicefabricdeploy.parameters.json` file to set your values:
|
||||
|
||||
- clusterName: Name of your SF cluster
|
||||
- clusterLocation: Datacenter location, like westus or westeurope
|
||||
- computeLocation: Datacenter location, like westus or westeurope
|
||||
- adminUserName: user-name for VMs administration
|
||||
- adminPassword: user-password for VMs administration
|
||||
- dnsName: Name assigned to your SF dns
|
||||
|
||||
Optionally, you could modify which ports are opened in the LoadBalancer for the multiple eShopOnContainer apps and API services.
|
||||
By default, they are setup as:
|
||||
- webMvcHttpPort: 5100
|
||||
- webSpaHttpPort: 5104
|
||||
- webStatusHttpPort: 5107
|
||||
- IdSrvHttpRule: 5105
|
||||
- BasketApiHttpRule: 5103
|
||||
- CatalogApiHttpRule: 5101
|
||||
- OrderingApiHttpRule: 5102
|
||||
- MarketingApiHttpRule: 5110
|
||||
- LocationsApiHttpRule: 5109
|
||||
|
||||
## Deploy the Service Fabric cluster using the script and ARM templates
|
||||
|
||||
Once parameter file is edited you can deploy it using [create-resources script](../readme.md).
|
||||
|
||||
For example, to deploy the cluster to a new resourcegroup located in westus, go to `deploy\az` folder and type:
|
||||
|
||||
```
|
||||
create-resources.cmd servicefabric\LinuxContainers\servicefabricdeploy qa-eshop-sflinux-resgrp -c westus
|
||||
```
|
||||
|
||||
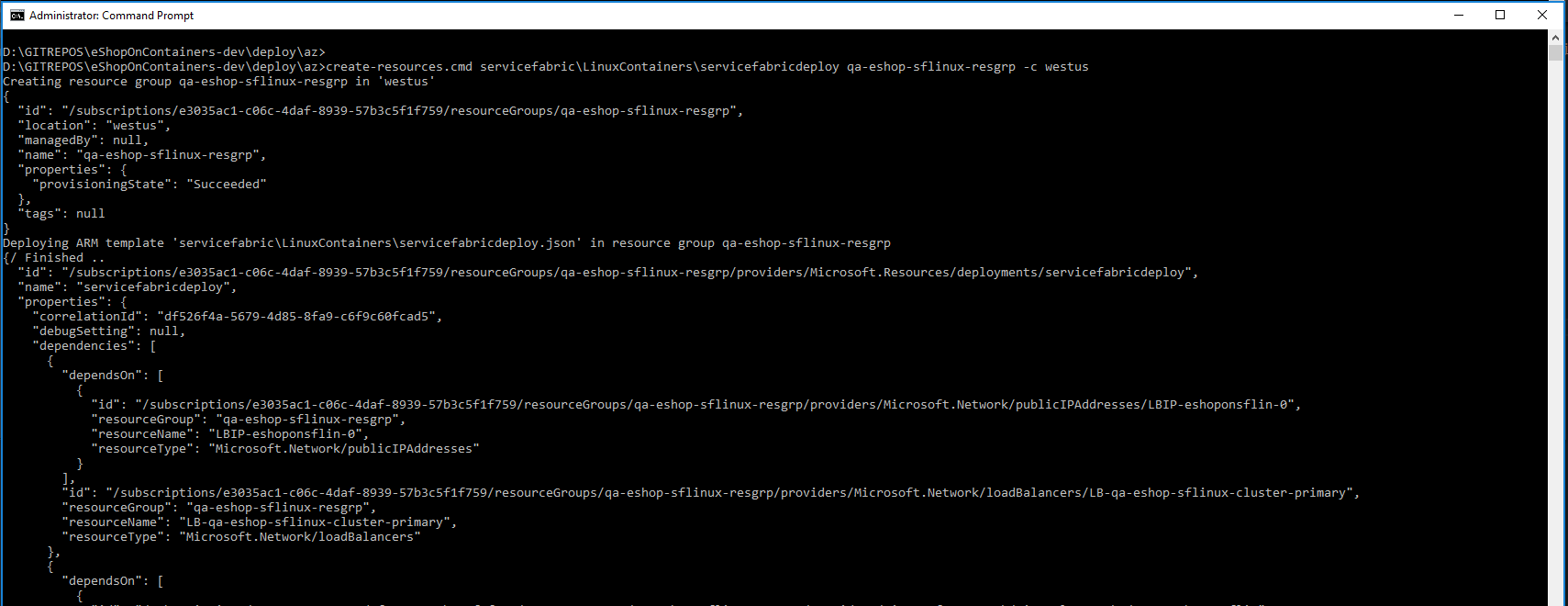
You should see a similar execution to the following:
|
||||
|
||||
|
||||
Now, if you go to your subscription in Azure, you should be able to see the SF cluster already created and available, like in the following image:
|
||||
|
||||
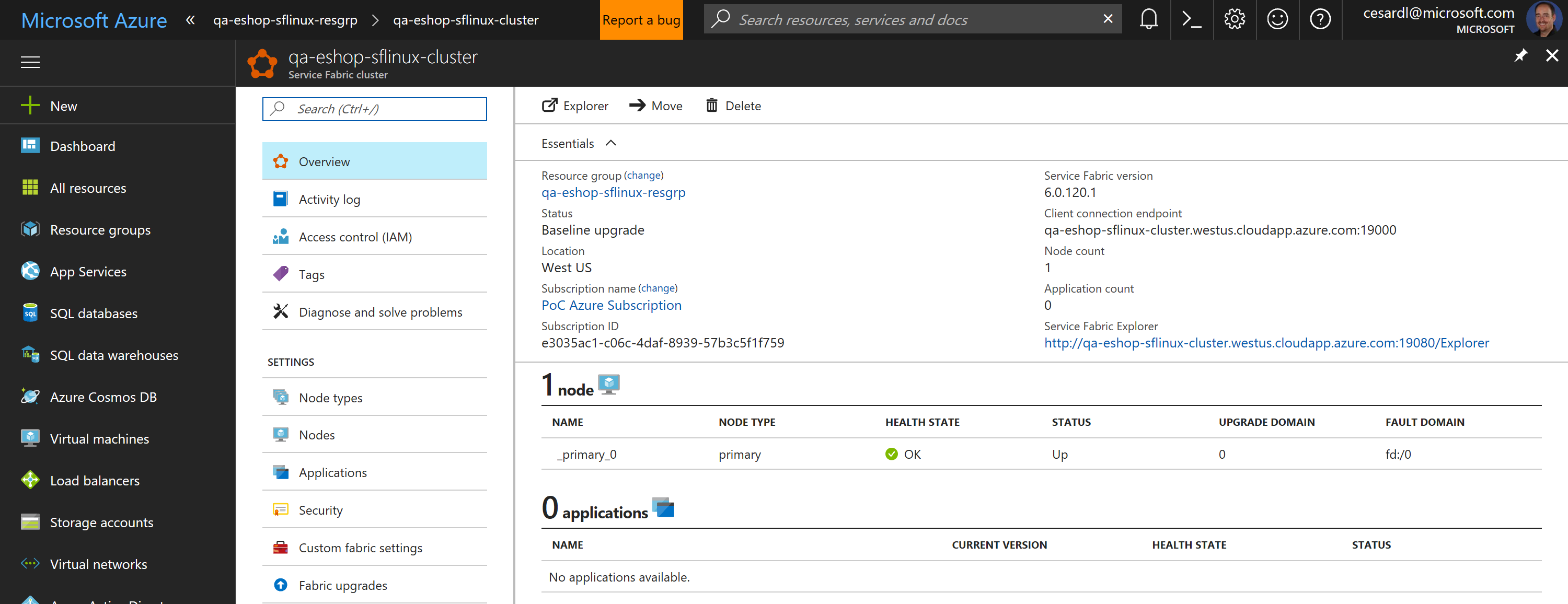
|
||||
|
||||
In this case, this is an unsecured SF cluster with a single Linux node, good for initial tests and getting started with SF.
|
||||
|
||||
## B. Secured cluster (SF Linux cluster)
|
||||
|
||||
Within eShopOnContainers root folder, at the folder [..\deploy\az\servicefabric\LinuxContainers](https://github.com/dotnet-architecture/eShopOnContainers/tree/dev/deploy/az/servicefabric/LinuxContainers), you can find the ARM template `servicefabricdeploysecured.json` and its parameter file (`servicefabricdeploysecured.parameters.json`) to create a secured Service Fabric cluster environment for Linux Containers (IN THIS CASE, IT IS A SECURED CLUSTER USING A CERTIFICATE).
|
||||
|
||||
The ARM template `servicefabricdeploysecured.json` and its parameter file (`servicefabricdeploysecured.parameters.json`) are used to create a service fabric cluster environment for linux containers secured with a certificate.
|
||||
|
||||
## Create Azure Keyvault service
|
||||
Go to PortalAzure and create a Keyvault service. Make sure Enable access for deployment checkboxes are selected.
|
||||
|
||||
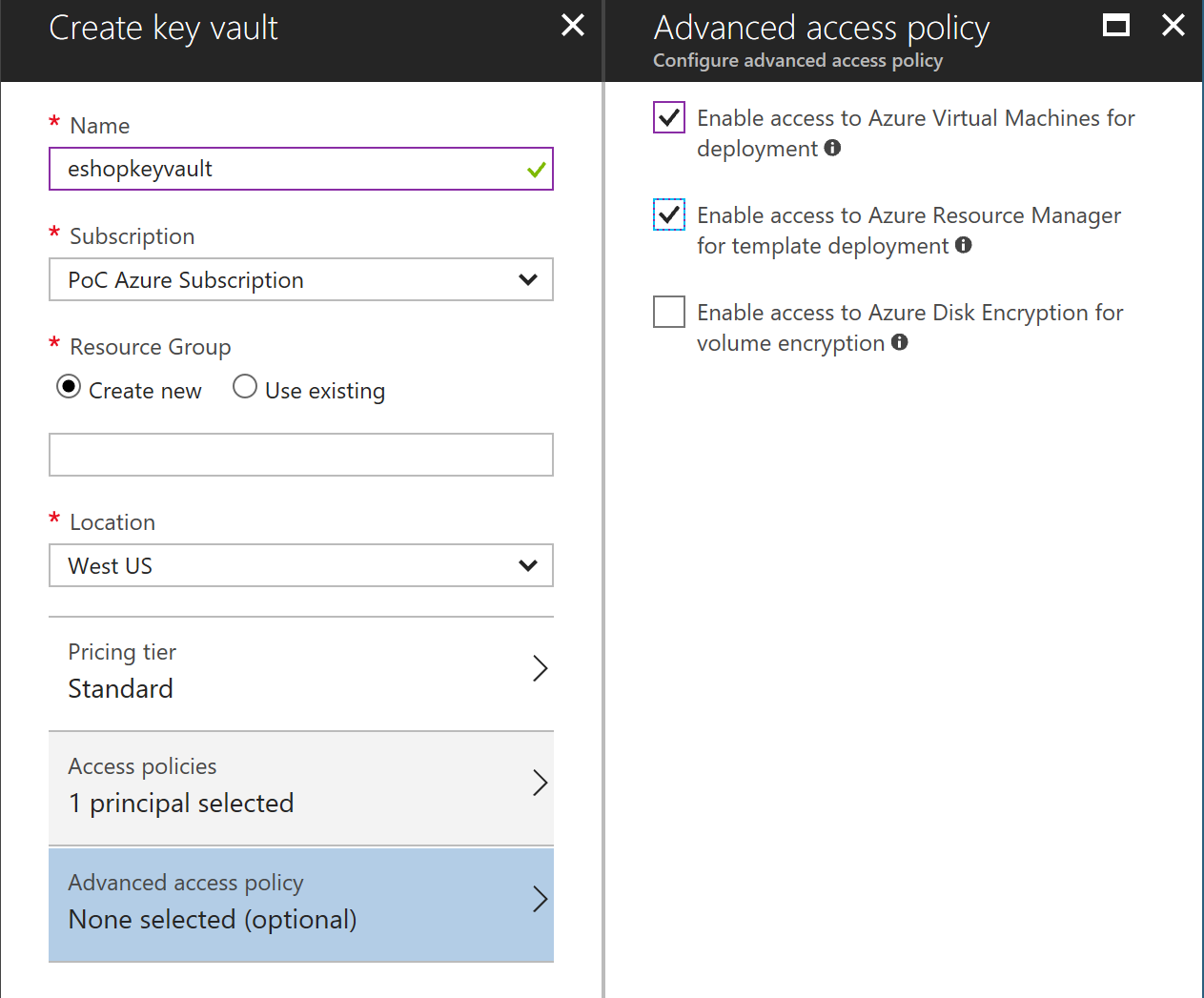
|
||||
|
||||
## Generate a certificate in Azure Keyvault
|
||||
In a POWER-SHELL window, move to the folder [..\deploy\az\servicefabric\LinuxContainers](https://github.com/dotnet-architecture/eShopOnContainers/tree/dev/deploy/az/servicefabric/LinuxContainers).
|
||||
|
||||
**Select your Azure subscription** You might have [several Azure subscriptions](https://docs.microsoft.com/en-us/cli/azure/account#set) as shown if you type the following.
|
||||
|
||||
>```
|
||||
>az account list
|
||||
>```
|
||||
If you have multiple subscription accounts, you first need to select the Azure subscription account you want to target. Type the following:
|
||||
>```
|
||||
>az account set --subscription "Your Azure Subscription Name or ID"
|
||||
>```
|
||||
|
||||
Execute the gen-keyvaultcert.ps1 script to generate and download a certificate from Keyvault.
|
||||
|
||||
```
|
||||
.\gen-keyvaultcert.ps1 -vaultName <your_keyvault_service> -certName <your_cert_name> -certPwd <your_cert_pwd> -subjectName CN=<your_sf_dns_name>.westeurope.cloudapp.azure.com -saveDir C:\Users\<user>\Downloads
|
||||
|
||||
```
|
||||
|
||||
You should see a similar execution to the following:
|
||||
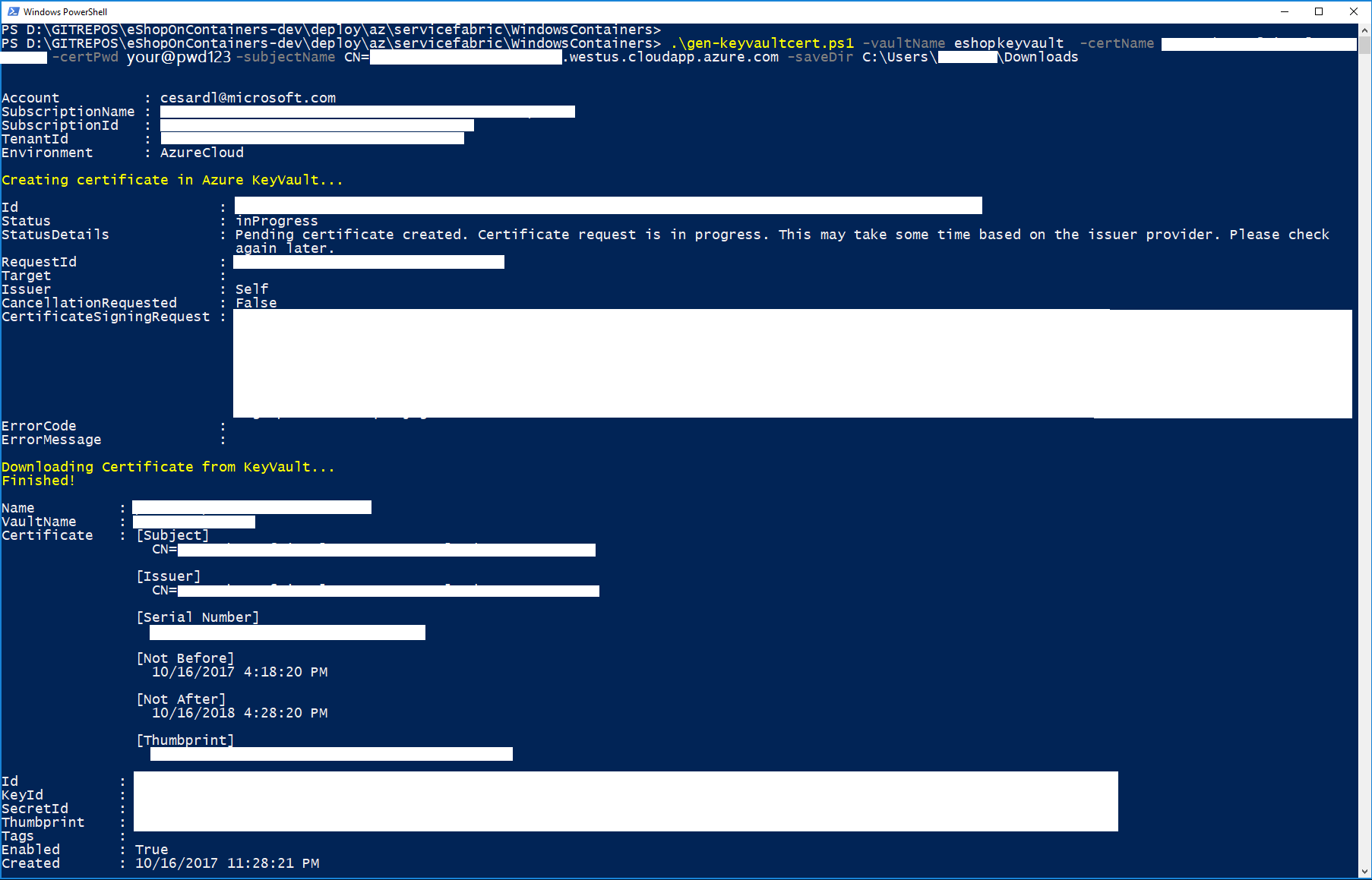
|
||||
|
||||
IMPORTANT: At this point, copy/cut the .PFX certificate file saved in the downloads forlder and save it in a secure place.
|
||||
|
||||
## Install the certificate
|
||||
Install the certificate (by double-clicking on the .PFX file) under 'Current User' store location (by default location) and check it as exportable.
|
||||
|
||||
<img src="https://github.com/dotnet-architecture/eShopOnContainers/blob/dev/img/sf/install-cert.PNG">
|
||||
|
||||
Also, install the same certificate as CA (Certificate Authority) under Current User, too.
|
||||
|
||||
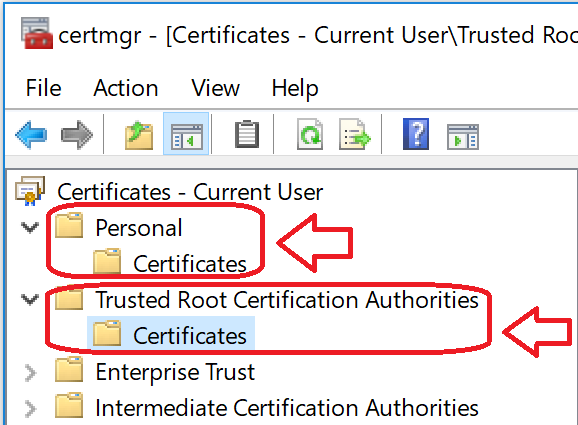
|
||||
|
||||
## Editing servicefabricdeploysecured.parameters.json file
|
||||
|
||||
Edit the parameters in `servicefabricdeploysecured.parameters.json` in a similar way you can do with the unsecured .json file shown above (clusterName, dnsName, etc.), plus edit the following values:
|
||||
|
||||
- sourceVaultValue: Your Azure Keyvault's RESOURCE ID (check Azure keyvault properties, similar to: /subscriptions/e1234ac1-c09c-3jaf-6767-98b3c5f1f246/resourceGroups/eshop-global-resgrp/providers/Microsoft.KeyVault/vaults/eshopkeyvault")
|
||||
|
||||
- certificateUrlValue: Your certificate Secret Identifier (check Azure Keyvault secret certificate properties, should be in the format of https://<name of the vault>.vault.azure.net:443/secrets/<exact location>, similar to:
|
||||
https://eshopkeyvault.vault.azure.net/secrets/pro-eshop-sflinux-cluster-cert/fd47684442c04cdj83b3hfe4h8e08123)
|
||||
|
||||
- certificateThumbprint: certificate thumbprint (check azure Keyvault certificate thumbprint, something like 69JK453486D55A6818577Z0699100365HDK70FCE)
|
||||
|
||||
## Deploy the secured SF Linux cluster
|
||||
|
||||
Once parameters file is edited you can deploy it using [create-resources script](../readme.md).
|
||||
Use a command prompt window positioned into the deploy\az folder.
|
||||
|
||||
```
|
||||
create-resources.cmd servicefabric\LinuxContainers\servicefabricdeploysecured pro-eshop-sflinux-resgrp -c westus
|
||||
```
|
||||
The execution should be something like the following:
|
||||
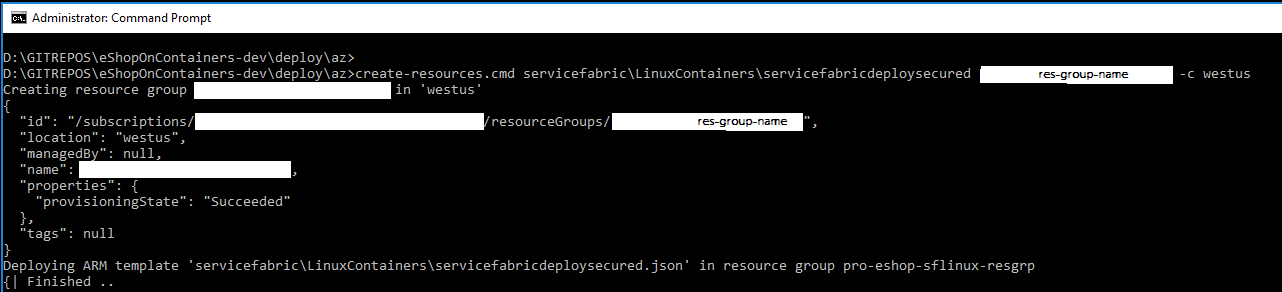
|
||||
|
||||
Once the cluster is created you can explore it with Azure's portal, like in the following image:
|
||||
|
||||
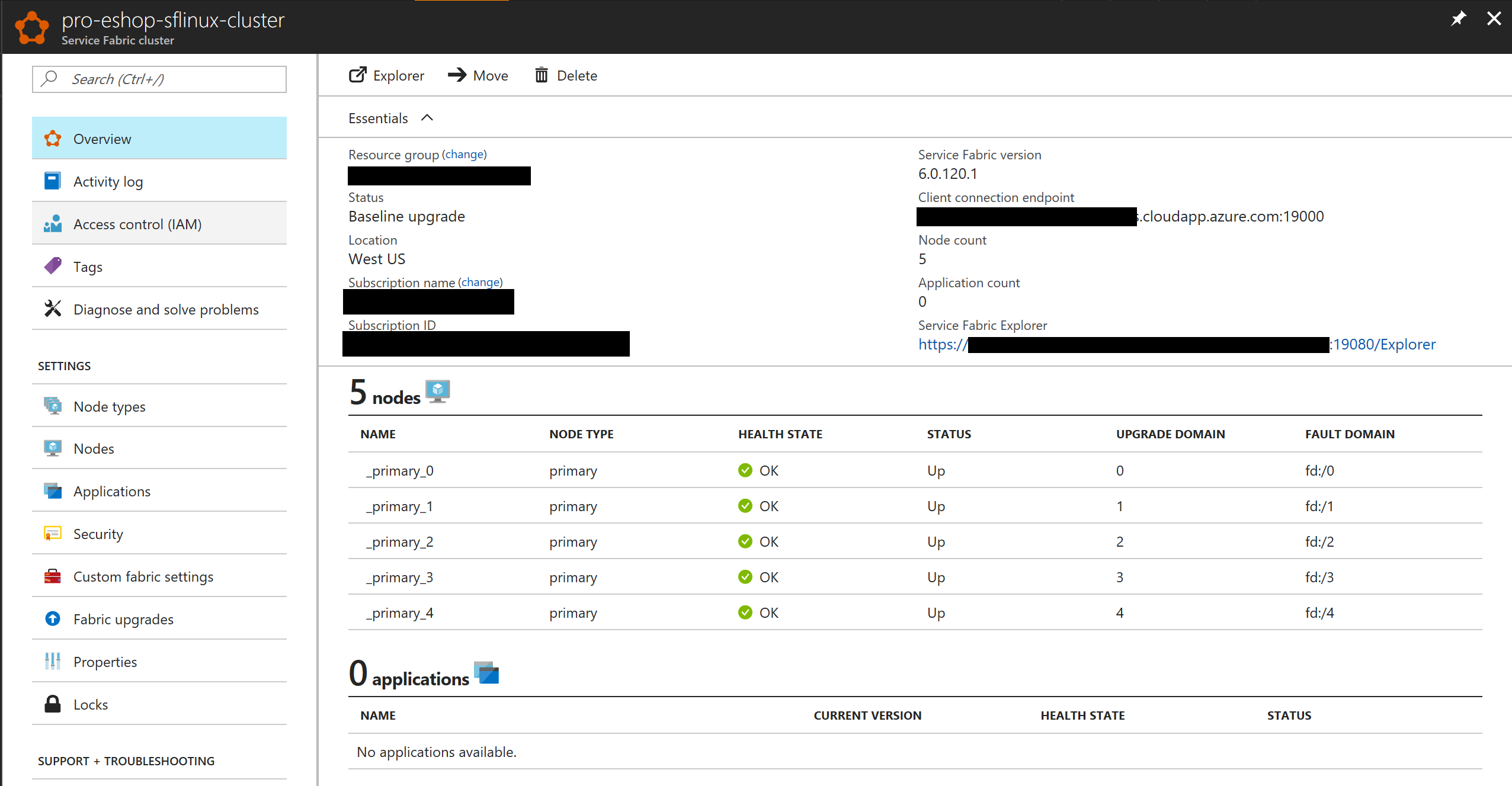
|
||||
|
||||
## Deploy eShopOnServiceFabric with Visual Studio.
|
||||
|
||||
Modify the cloud.xml file of each Service Fabric application in PublishProfile directory and set your certificate settings to be able to deploy eshopOnContainers in the secured cluster:
|
||||
|
||||
<img src="../../../../img/sf/cloud_publishProfile.png">
|
||||
|
||||
|
||||
|
||||
@ -1,751 +0,0 @@
|
||||
{
|
||||
"$schema": "http://schema.management.azure.com/schemas/2015-01-01/deploymentTemplate.json",
|
||||
"contentVersion": "1.0.0.0",
|
||||
"parameters": {
|
||||
"clusterLocation": {
|
||||
"type": "string",
|
||||
"metadata": {
|
||||
"description": "Location of the Cluster"
|
||||
}
|
||||
},
|
||||
"clusterName": {
|
||||
"type": "string",
|
||||
"defaultValue": "Cluster",
|
||||
"metadata": {
|
||||
"description": "Name of your cluster - Between 3 and 23 characters. Letters and numbers only"
|
||||
}
|
||||
},
|
||||
"nt0applicationStartPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 20000
|
||||
},
|
||||
"nt0applicationEndPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 30000
|
||||
},
|
||||
"nt0ephemeralStartPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 49152
|
||||
},
|
||||
"nt0ephemeralEndPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 65534
|
||||
},
|
||||
"nt0fabricTcpGatewayPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 19000
|
||||
},
|
||||
"nt0fabricHttpGatewayPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 19080
|
||||
},
|
||||
"webMvcHttpPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 5100
|
||||
},
|
||||
"webSpaHttpPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 5104
|
||||
},
|
||||
"webStatusHttpPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 5107
|
||||
},
|
||||
"IdSrvHttpRule": {
|
||||
"type": "int",
|
||||
"defaultValue": 5105
|
||||
},
|
||||
"BasketApiHttpRule": {
|
||||
"type": "int",
|
||||
"defaultValue": 5103
|
||||
},
|
||||
"CatalogApiHttpRule": {
|
||||
"type": "int",
|
||||
"defaultValue": 5101
|
||||
},
|
||||
"OrderingApiHttpRule": {
|
||||
"type": "int",
|
||||
"defaultValue": 5102
|
||||
},
|
||||
"MarketingApiHttpRule": {
|
||||
"type": "int",
|
||||
"defaultValue": 5110
|
||||
},
|
||||
"LocationsApiHttpRule": {
|
||||
"type": "int",
|
||||
"defaultValue": 5109
|
||||
},
|
||||
"subnet0Name": {
|
||||
"type": "string",
|
||||
"defaultValue": "Subnet-0"
|
||||
},
|
||||
"subnet0Prefix": {
|
||||
"type": "string",
|
||||
"defaultValue": "10.0.0.0/24"
|
||||
},
|
||||
"computeLocation": {
|
||||
"type": "string"
|
||||
},
|
||||
"publicIPAddressName": {
|
||||
"type": "string",
|
||||
"defaultValue": "PublicIP-VM"
|
||||
},
|
||||
"publicIPAddressType": {
|
||||
"type": "string",
|
||||
"allowedValues": [
|
||||
"Dynamic"
|
||||
],
|
||||
"defaultValue": "Dynamic"
|
||||
},
|
||||
"vmStorageAccountContainerName": {
|
||||
"type": "string",
|
||||
"defaultValue": "vhds"
|
||||
},
|
||||
"adminUserName": {
|
||||
"type": "string",
|
||||
"defaultValue": "testadm",
|
||||
"metadata": {
|
||||
"description": "Remote desktop user Id"
|
||||
}
|
||||
},
|
||||
"adminPassword": {
|
||||
"type": "securestring",
|
||||
"metadata": {
|
||||
"description": "Remote desktop user password. Must be a strong password"
|
||||
}
|
||||
},
|
||||
"virtualNetworkName": {
|
||||
"type": "string",
|
||||
"defaultValue": "VNet"
|
||||
},
|
||||
"addressPrefix": {
|
||||
"type": "string",
|
||||
"defaultValue": "10.0.0.0/16"
|
||||
},
|
||||
"dnsName": {
|
||||
"type": "string"
|
||||
},
|
||||
"nicName": {
|
||||
"type": "string",
|
||||
"defaultValue": "NIC"
|
||||
},
|
||||
"lbName": {
|
||||
"type": "string",
|
||||
"defaultValue": "LoadBalancer"
|
||||
},
|
||||
"lbIPName": {
|
||||
"type": "string",
|
||||
"defaultValue": "PublicIP-LB-FE"
|
||||
},
|
||||
"overProvision": {
|
||||
"type": "string",
|
||||
"defaultValue": "false"
|
||||
},
|
||||
"vmImagePublisher": {
|
||||
"type": "string",
|
||||
"defaultValue": "Microsoft.Azure.ServiceFabric"
|
||||
},
|
||||
"vmImageOffer": {
|
||||
"type": "string",
|
||||
"defaultValue": "UbuntuServer"
|
||||
},
|
||||
"vmImageSku": {
|
||||
"type": "string",
|
||||
"defaultValue": "16.04"
|
||||
},
|
||||
"vmImageVersion": {
|
||||
"type": "string",
|
||||
"defaultValue": "6.0.12"
|
||||
},
|
||||
"storageAccountType": {
|
||||
"type": "string",
|
||||
"allowedValues": [
|
||||
"Standard_LRS",
|
||||
"Standard_GRS"
|
||||
],
|
||||
"defaultValue": "Standard_LRS",
|
||||
"metadata": {
|
||||
"description": "Replication option for the VM image storage account"
|
||||
}
|
||||
},
|
||||
"supportLogStorageAccountType": {
|
||||
"type": "string",
|
||||
"allowedValues": [
|
||||
"Standard_LRS",
|
||||
"Standard_GRS"
|
||||
],
|
||||
"defaultValue": "Standard_LRS",
|
||||
"metadata": {
|
||||
"description": "Replication option for the support log storage account"
|
||||
}
|
||||
},
|
||||
"supportLogStorageAccountName": {
|
||||
"type": "string",
|
||||
"defaultValue": "[toLower( concat('sflogs', uniqueString(resourceGroup().id),'2'))]",
|
||||
"metadata": {
|
||||
"description": "Name for the storage account that contains support logs from the cluster"
|
||||
}
|
||||
},
|
||||
"applicationDiagnosticsStorageAccountType": {
|
||||
"type": "string",
|
||||
"allowedValues": [
|
||||
"Standard_LRS",
|
||||
"Standard_GRS"
|
||||
],
|
||||
"defaultValue": "Standard_LRS",
|
||||
"metadata": {
|
||||
"description": "Replication option for the application diagnostics storage account"
|
||||
}
|
||||
},
|
||||
"applicationDiagnosticsStorageAccountName": {
|
||||
"type": "string",
|
||||
"defaultValue": "[toLower(concat(uniqueString(resourceGroup().id), '3' ))]",
|
||||
"metadata": {
|
||||
"description": "Name for the storage account that contains application diagnostics data from the cluster"
|
||||
}
|
||||
},
|
||||
"nt0InstanceCount": {
|
||||
"type": "int",
|
||||
"defaultValue": 1,
|
||||
"metadata": {
|
||||
"description": "Instance count for node type"
|
||||
}
|
||||
},
|
||||
"vmNodeType0Name": {
|
||||
"type": "string",
|
||||
"defaultValue": "primary",
|
||||
"maxLength": 9
|
||||
},
|
||||
"vmNodeType0Size": {
|
||||
"type": "string",
|
||||
"defaultValue": "Standard_D1_v2"
|
||||
}
|
||||
},
|
||||
"variables": {
|
||||
"vmssApiVersion": "2017-03-30",
|
||||
"lbApiVersion": "2015-06-15",
|
||||
"vNetApiVersion": "2015-06-15",
|
||||
"storageApiVersion": "2016-01-01",
|
||||
"publicIPApiVersion": "2015-06-15",
|
||||
"vnetID": "[resourceId('Microsoft.Network/virtualNetworks',parameters('virtualNetworkName'))]",
|
||||
"subnet0Ref": "[concat(variables('vnetID'),'/subnets/',parameters('subnet0Name'))]",
|
||||
"wadlogs": "<WadCfg><DiagnosticMonitorConfiguration>",
|
||||
"wadperfcounters1": "<PerformanceCounters scheduledTransferPeriod=\"PT1M\"><PerformanceCounterConfiguration counterSpecifier=\"\\Memory\\AvailableMemory\" sampleRate=\"PT15S\" unit=\"Bytes\"><annotation displayName=\"Memory available\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\Memory\\PercentAvailableMemory\" sampleRate=\"PT15S\" unit=\"Percent\"><annotation displayName=\"Mem. percent available\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\Memory\\UsedMemory\" sampleRate=\"PT15S\" unit=\"Bytes\"><annotation displayName=\"Memory used\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\Memory\\PercentUsedMemory\" sampleRate=\"PT15S\" unit=\"Percent\"><annotation displayName=\"Memory percentage\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\Memory\\PercentUsedByCache\" sampleRate=\"PT15S\" unit=\"Percent\"><annotation displayName=\"Mem. used by cache\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\Processor\\PercentIdleTime\" sampleRate=\"PT15S\" unit=\"Percent\"><annotation displayName=\"CPU idle time\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\Processor\\PercentUserTime\" sampleRate=\"PT15S\" unit=\"Percent\"><annotation displayName=\"CPU user time\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\Processor\\PercentProcessorTime\" sampleRate=\"PT15S\" unit=\"Percent\"><annotation displayName=\"CPU percentage guest OS\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\Processor\\PercentIOWaitTime\" sampleRate=\"PT15S\" unit=\"Percent\"><annotation displayName=\"CPU IO wait time\" locale=\"en-us\"/></PerformanceCounterConfiguration>",
|
||||
"wadperfcounters2": "<PerformanceCounterConfiguration counterSpecifier=\"\\PhysicalDisk\\BytesPerSecond\" sampleRate=\"PT15S\" unit=\"BytesPerSecond\"><annotation displayName=\"Disk total bytes\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\PhysicalDisk\\ReadBytesPerSecond\" sampleRate=\"PT15S\" unit=\"BytesPerSecond\"><annotation displayName=\"Disk read guest OS\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\PhysicalDisk\\WriteBytesPerSecond\" sampleRate=\"PT15S\" unit=\"BytesPerSecond\"><annotation displayName=\"Disk write guest OS\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\PhysicalDisk\\TransfersPerSecond\" sampleRate=\"PT15S\" unit=\"CountPerSecond\"><annotation displayName=\"Disk transfers\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\PhysicalDisk\\ReadsPerSecond\" sampleRate=\"PT15S\" unit=\"CountPerSecond\"><annotation displayName=\"Disk reads\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\PhysicalDisk\\WritesPerSecond\" sampleRate=\"PT15S\" unit=\"CountPerSecond\"><annotation displayName=\"Disk writes\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\PhysicalDisk\\AverageReadTime\" sampleRate=\"PT15S\" unit=\"Seconds\"><annotation displayName=\"Disk read time\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\PhysicalDisk\\AverageWriteTime\" sampleRate=\"PT15S\" unit=\"Seconds\"><annotation displayName=\"Disk write time\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\PhysicalDisk\\AverageTransferTime\" sampleRate=\"PT15S\" unit=\"Seconds\"><annotation displayName=\"Disk transfer time\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\PhysicalDisk\\AverageDiskQueueLength\" sampleRate=\"PT15S\" unit=\"Count\"><annotation displayName=\"Disk queue length\" locale=\"en-us\"/></PerformanceCounterConfiguration></PerformanceCounters>",
|
||||
"wadcfgxstart": "[concat(variables('wadlogs'),variables('wadperfcounters1'),variables('wadperfcounters2'),'<Metrics resourceId=\"')]",
|
||||
"wadcfgxend": "[concat('\"><MetricAggregation scheduledTransferPeriod=\"PT1H\"/><MetricAggregation scheduledTransferPeriod=\"PT1M\"/></Metrics></DiagnosticMonitorConfiguration></WadCfg>')]",
|
||||
"lbID0": "[resourceId('Microsoft.Network/loadBalancers', concat('LB','-', parameters('clusterName'),'-',parameters('vmNodeType0Name')))]",
|
||||
"lbIPConfig0": "[concat(variables('lbID0'),'/frontendIPConfigurations/LoadBalancerIPConfig')]",
|
||||
"lbPoolID0": "[concat(variables('lbID0'),'/backendAddressPools/LoadBalancerBEAddressPool')]",
|
||||
"lbProbeID0": "[concat(variables('lbID0'),'/probes/FabricGatewayProbe')]",
|
||||
"lbHttpProbeID0": "[concat(variables('lbID0'),'/probes/FabricHttpGatewayProbe')]",
|
||||
"lbNatPoolID0": "[concat(variables('lbID0'),'/inboundNatPools/LoadBalancerBEAddressNatPool')]",
|
||||
"vmStorageAccountName0": "[toLower(concat(uniqueString(resourceGroup().id), '1', '0' ))]",
|
||||
"wadmetricsresourceid0": "[concat('/subscriptions/',subscription().subscriptionId,'/resourceGroups/',resourceGroup().name ,'/providers/','Microsoft.Compute/virtualMachineScaleSets/', parameters('vmNodeType0Name'))]"
|
||||
},
|
||||
"resources": [
|
||||
{
|
||||
"apiVersion": "[variables('storageApiVersion')]",
|
||||
"type": "Microsoft.Storage/storageAccounts",
|
||||
"name": "[parameters('supportLogStorageAccountName')]",
|
||||
"location": "[parameters('computeLocation')]",
|
||||
"dependsOn": [],
|
||||
"properties": {},
|
||||
"kind": "Storage",
|
||||
"sku": {
|
||||
"name": "[parameters('supportLogStorageAccountType')]"
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[parameters('clusterName')]"
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "[variables('storageApiVersion')]",
|
||||
"type": "Microsoft.Storage/storageAccounts",
|
||||
"name": "[parameters('applicationDiagnosticsStorageAccountName')]",
|
||||
"location": "[parameters('computeLocation')]",
|
||||
"dependsOn": [],
|
||||
"properties": {},
|
||||
"kind": "Storage",
|
||||
"sku": {
|
||||
"name": "[parameters('applicationDiagnosticsStorageAccountType')]"
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[parameters('clusterName')]"
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "[variables('vNetApiVersion')]",
|
||||
"type": "Microsoft.Network/virtualNetworks",
|
||||
"name": "[parameters('virtualNetworkName')]",
|
||||
"location": "[parameters('computeLocation')]",
|
||||
"dependsOn": [],
|
||||
"properties": {
|
||||
"addressSpace": {
|
||||
"addressPrefixes": [
|
||||
"[parameters('addressPrefix')]"
|
||||
]
|
||||
},
|
||||
"subnets": [
|
||||
{
|
||||
"name": "[parameters('subnet0Name')]",
|
||||
"properties": {
|
||||
"addressPrefix": "[parameters('subnet0Prefix')]"
|
||||
}
|
||||
}
|
||||
]
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[parameters('clusterName')]"
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "[variables('publicIPApiVersion')]",
|
||||
"type": "Microsoft.Network/publicIPAddresses",
|
||||
"name": "[concat(parameters('lbIPName'),'-','0')]",
|
||||
"location": "[parameters('computeLocation')]",
|
||||
"properties": {
|
||||
"dnsSettings": {
|
||||
"domainNameLabel": "[parameters('dnsName')]"
|
||||
},
|
||||
"publicIPAllocationMethod": "Dynamic"
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[parameters('clusterName')]"
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "[variables('lbApiVersion')]",
|
||||
"type": "Microsoft.Network/loadBalancers",
|
||||
"name": "[concat('LB','-', parameters('clusterName'),'-',parameters('vmNodeType0Name'))]",
|
||||
"location": "[parameters('computeLocation')]",
|
||||
"dependsOn": [
|
||||
"[concat('Microsoft.Network/publicIPAddresses/',concat(parameters('lbIPName'),'-','0'))]"
|
||||
],
|
||||
"properties": {
|
||||
"frontendIPConfigurations": [
|
||||
{
|
||||
"name": "LoadBalancerIPConfig",
|
||||
"properties": {
|
||||
"publicIPAddress": {
|
||||
"id": "[resourceId('Microsoft.Network/publicIPAddresses',concat(parameters('lbIPName'),'-','0'))]"
|
||||
}
|
||||
}
|
||||
}
|
||||
],
|
||||
"backendAddressPools": [
|
||||
{
|
||||
"name": "LoadBalancerBEAddressPool",
|
||||
"properties": {}
|
||||
}
|
||||
],
|
||||
"loadBalancingRules": [
|
||||
{
|
||||
"name": "LBRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('nt0fabricTcpGatewayPort')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('nt0fabricTcpGatewayPort')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"probe": {
|
||||
"id": "[variables('lbProbeID0')]"
|
||||
},
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "LBHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('nt0fabricHttpGatewayPort')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('nt0fabricHttpGatewayPort')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"probe": {
|
||||
"id": "[variables('lbHttpProbeID0')]"
|
||||
},
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "WebMVCHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('webMvcHttpPort')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('webMvcHttpPort')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "WebSPAHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('webSpaHttpPort')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('webSpaHttpPort')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "WebStatusHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('webStatusHttpPort')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('webStatusHttpPort')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "IdSrvHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('IdSrvHttpRule')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('IdSrvHttpRule')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "BasketApiHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('BasketApiHttpRule')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('BasketApiHttpRule')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "CatalogApiHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('CatalogApiHttpRule')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('CatalogApiHttpRule')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "OrderingApiHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('OrderingApiHttpRule')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('OrderingApiHttpRule')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "MarketingApiHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('MarketingApiHttpRule')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('MarketingApiHttpRule')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "LocationsApiHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('LocationsApiHttpRule')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('LocationsApiHttpRule')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
}
|
||||
],
|
||||
"probes": [
|
||||
{
|
||||
"name": "FabricGatewayProbe",
|
||||
"properties": {
|
||||
"intervalInSeconds": 5,
|
||||
"numberOfProbes": 2,
|
||||
"port": "[parameters('nt0fabricTcpGatewayPort')]",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "FabricHttpGatewayProbe",
|
||||
"properties": {
|
||||
"intervalInSeconds": 5,
|
||||
"numberOfProbes": 2,
|
||||
"port": "[parameters('nt0fabricHttpGatewayPort')]",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
}
|
||||
],
|
||||
"inboundNatPools": [
|
||||
{
|
||||
"name": "LoadBalancerBEAddressNatPool",
|
||||
"properties": {
|
||||
"backendPort": "22",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPortRangeEnd": "4500",
|
||||
"frontendPortRangeStart": "3389",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
}
|
||||
]
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[parameters('clusterName')]"
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "[variables('vmssApiVersion')]",
|
||||
"type": "Microsoft.Compute/virtualMachineScaleSets",
|
||||
"name": "[parameters('vmNodeType0Name')]",
|
||||
"location": "[parameters('computeLocation')]",
|
||||
"dependsOn": [
|
||||
"[concat('Microsoft.Network/virtualNetworks/', parameters('virtualNetworkName'))]",
|
||||
"[concat('Microsoft.Network/loadBalancers/', concat('LB','-', parameters('clusterName'),'-',parameters('vmNodeType0Name')))]",
|
||||
"[concat('Microsoft.Storage/storageAccounts/', parameters('supportLogStorageAccountName'))]",
|
||||
"[concat('Microsoft.Storage/storageAccounts/', parameters('applicationDiagnosticsStorageAccountName'))]"
|
||||
],
|
||||
"properties": {
|
||||
"overprovision": "[parameters('overProvision')]",
|
||||
"upgradePolicy": {
|
||||
"mode": "Automatic"
|
||||
},
|
||||
"virtualMachineProfile": {
|
||||
"extensionProfile": {
|
||||
"extensions": [
|
||||
{
|
||||
"name": "[concat(parameters('vmNodeType0Name'),'_ServiceFabricLinuxNode')]",
|
||||
"properties": {
|
||||
"type": "ServiceFabricLinuxNode",
|
||||
"autoUpgradeMinorVersion": true,
|
||||
"protectedSettings": {
|
||||
"StorageAccountKey1": "[listKeys(resourceId('Microsoft.Storage/storageAccounts', parameters('supportLogStorageAccountName')),'2015-05-01-preview').key1]",
|
||||
"StorageAccountKey2": "[listKeys(resourceId('Microsoft.Storage/storageAccounts', parameters('supportLogStorageAccountName')),'2015-05-01-preview').key2]"
|
||||
},
|
||||
"publisher": "Microsoft.Azure.ServiceFabric",
|
||||
"settings": {
|
||||
"clusterEndpoint": "[reference(parameters('clusterName')).clusterEndpoint]",
|
||||
"nodeTypeRef": "[parameters('vmNodeType0Name')]",
|
||||
"durabilityLevel": "Bronze",
|
||||
"enableParallelJobs": true,
|
||||
"nicPrefixOverride": "[parameters('subnet0Prefix')]"
|
||||
},
|
||||
"typeHandlerVersion": "1.0"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "[concat('VMDiagnosticsVmExt','_vmNodeType0Name')]",
|
||||
"properties": {
|
||||
"type": "LinuxDiagnostic",
|
||||
"autoUpgradeMinorVersion": true,
|
||||
"protectedSettings": {
|
||||
"storageAccountName": "[parameters('applicationDiagnosticsStorageAccountName')]",
|
||||
"storageAccountKey": "[listKeys(resourceId('Microsoft.Storage/storageAccounts', parameters('applicationDiagnosticsStorageAccountName')),'2015-05-01-preview').key1]",
|
||||
"storageAccountEndPoint": "https://core.windows.net/"
|
||||
},
|
||||
"publisher": "Microsoft.OSTCExtensions",
|
||||
"settings": {
|
||||
"xmlCfg": "[base64(concat(variables('wadcfgxstart'),variables('wadmetricsresourceid0'),variables('wadcfgxend')))]",
|
||||
"StorageAccount": "[parameters('applicationDiagnosticsStorageAccountName')]"
|
||||
},
|
||||
"typeHandlerVersion": "2.3"
|
||||
}
|
||||
}
|
||||
]
|
||||
},
|
||||
"networkProfile": {
|
||||
"networkInterfaceConfigurations": [
|
||||
{
|
||||
"name": "[concat(parameters('nicName'), '-0')]",
|
||||
"properties": {
|
||||
"ipConfigurations": [
|
||||
{
|
||||
"name": "[concat(parameters('nicName'),'-',0)]",
|
||||
"properties": {
|
||||
"loadBalancerBackendAddressPools": [
|
||||
{
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
}
|
||||
],
|
||||
"loadBalancerInboundNatPools": [
|
||||
{
|
||||
"id": "[variables('lbNatPoolID0')]"
|
||||
}
|
||||
],
|
||||
"subnet": {
|
||||
"id": "[variables('subnet0Ref')]"
|
||||
}
|
||||
}
|
||||
}
|
||||
],
|
||||
"primary": true
|
||||
}
|
||||
}
|
||||
]
|
||||
},
|
||||
"osProfile": {
|
||||
"adminPassword": "[parameters('adminPassword')]",
|
||||
"adminUsername": "[parameters('adminUsername')]",
|
||||
"computernamePrefix": "[parameters('vmNodeType0Name')]"
|
||||
},
|
||||
"storageProfile": {
|
||||
"imageReference": {
|
||||
"publisher": "[parameters('vmImagePublisher')]",
|
||||
"offer": "[parameters('vmImageOffer')]",
|
||||
"sku": "[parameters('vmImageSku')]",
|
||||
"version": "[parameters('vmImageVersion')]"
|
||||
},
|
||||
"osDisk": {
|
||||
"caching": "ReadOnly",
|
||||
"createOption": "FromImage",
|
||||
"managedDisk": {
|
||||
"storageAccountType": "[parameters('storageAccountType')]"
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
},
|
||||
"sku": {
|
||||
"name": "[parameters('vmNodeType0Size')]",
|
||||
"capacity": "[parameters('nt0InstanceCount')]",
|
||||
"tier": "Standard"
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[parameters('clusterName')]"
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "2017-07-01-preview",
|
||||
"type": "Microsoft.ServiceFabric/clusters",
|
||||
"name": "[parameters('clusterName')]",
|
||||
"location": "[parameters('clusterLocation')]",
|
||||
"dependsOn": [
|
||||
"[concat('Microsoft.Storage/storageAccounts/', parameters('supportLogStorageAccountName'))]"
|
||||
],
|
||||
"properties": {
|
||||
"addonFeatures": [
|
||||
"DnsService"
|
||||
],
|
||||
"clientCertificateCommonNames": [],
|
||||
"clientCertificateThumbprints": [],
|
||||
"clusterCodeVersion": "6.0.120.1",
|
||||
"clusterState": "Default",
|
||||
"diagnosticsStorageAccountConfig": {
|
||||
"blobEndpoint": "[reference(concat('Microsoft.Storage/storageAccounts/', parameters('supportLogStorageAccountName')), variables('storageApiVersion')).primaryEndpoints.blob]",
|
||||
"protectedAccountKeyName": "StorageAccountKey1",
|
||||
"queueEndpoint": "[reference(concat('Microsoft.Storage/storageAccounts/', parameters('supportLogStorageAccountName')), variables('storageApiVersion')).primaryEndpoints.queue]",
|
||||
"storageAccountName": "[parameters('supportLogStorageAccountName')]",
|
||||
"tableEndpoint": "[reference(concat('Microsoft.Storage/storageAccounts/', parameters('supportLogStorageAccountName')), variables('storageApiVersion')).primaryEndpoints.table]"
|
||||
},
|
||||
"fabricSettings": [],
|
||||
"managementEndpoint": "[concat('http://',reference(concat(parameters('lbIPName'),'-','0')).dnsSettings.fqdn,':',parameters('nt0fabricHttpGatewayPort'))]",
|
||||
"nodeTypes": [
|
||||
{
|
||||
"name": "[parameters('vmNodeType0Name')]",
|
||||
"applicationPorts": {
|
||||
"endPort": "[parameters('nt0applicationEndPort')]",
|
||||
"startPort": "[parameters('nt0applicationStartPort')]"
|
||||
},
|
||||
"clientConnectionEndpointPort": "[parameters('nt0fabricTcpGatewayPort')]",
|
||||
"durabilityLevel": "Bronze",
|
||||
"ephemeralPorts": {
|
||||
"endPort": "[parameters('nt0ephemeralEndPort')]",
|
||||
"startPort": "[parameters('nt0ephemeralStartPort')]"
|
||||
},
|
||||
"httpGatewayEndpointPort": "[parameters('nt0fabricHttpGatewayPort')]",
|
||||
"isPrimary": true,
|
||||
"vmInstanceCount": "[parameters('nt0InstanceCount')]"
|
||||
}
|
||||
],
|
||||
"provisioningState": "Default",
|
||||
"reliabilityLevel": "None",
|
||||
"upgradeMode": "Manual",
|
||||
"vmImage": "Linux"
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[parameters('clusterName')]"
|
||||
}
|
||||
}
|
||||
],
|
||||
"outputs": {
|
||||
"clusterProperties": {
|
||||
"value": "[reference(parameters('clusterName'))]",
|
||||
"type": "object"
|
||||
}
|
||||
}
|
||||
}
|
||||
@ -1,93 +0,0 @@
|
||||
{
|
||||
"$schema": "https://schema.management.azure.com/schemas/2015-01-01/deploymentParameters.json#",
|
||||
"contentVersion": "1.0.0.0",
|
||||
"parameters": {
|
||||
"clusterName": {
|
||||
"value": "qa-eshop-sflinux-cluster"
|
||||
},
|
||||
"clusterLocation": {
|
||||
"value": "westus"
|
||||
},
|
||||
"computeLocation": {
|
||||
"value": "westus"
|
||||
},
|
||||
"adminUserName": {
|
||||
"value": "eshop"
|
||||
},
|
||||
"adminPassword": {
|
||||
"value": "Your_complex_Pass@word1"
|
||||
},
|
||||
"nicName": {
|
||||
"value": "NIC-eshoponsflin"
|
||||
},
|
||||
"publicIPAddressName": {
|
||||
"value": "eshoponsflin-PubIP"
|
||||
},
|
||||
"dnsName": {
|
||||
"value": "qa-eshop-sflinux-cluster"
|
||||
},
|
||||
"virtualNetworkName": {
|
||||
"value": "VNet-eshoponsflin"
|
||||
},
|
||||
"lbName": {
|
||||
"value": "LB-eshoponsflin"
|
||||
},
|
||||
"lbIPName": {
|
||||
"value": "LBIP-eshoponsflin"
|
||||
},
|
||||
"vmImageSku": {
|
||||
"value": "16.04-LTS"
|
||||
},
|
||||
"vmImageVersion": {
|
||||
"value": "latest"
|
||||
},
|
||||
"vmImagePublisher": {
|
||||
"value": "Canonical"
|
||||
},
|
||||
"nt0ephemeralStartPort": {
|
||||
"value": 49152
|
||||
},
|
||||
"nt0ephemeralEndPort": {
|
||||
"value": 65534
|
||||
},
|
||||
"nt0applicationStartPort": {
|
||||
"value": 20000
|
||||
},
|
||||
"nt0applicationEndPort": {
|
||||
"value": 30000
|
||||
},
|
||||
"nt0fabricTcpGatewayPort": {
|
||||
"value": 19000
|
||||
},
|
||||
"nt0fabricHttpGatewayPort": {
|
||||
"value": 19080
|
||||
},
|
||||
"webMvcHttpPort": {
|
||||
"value": 5100
|
||||
},
|
||||
"webSpaHttpPort": {
|
||||
"value": 5104
|
||||
},
|
||||
"webStatusHttpPort": {
|
||||
"value": 5107
|
||||
},
|
||||
"IdSrvHttpRule": {
|
||||
"value": 5105
|
||||
},
|
||||
"BasketApiHttpRule": {
|
||||
"value": 5103
|
||||
},
|
||||
"CatalogApiHttpRule": {
|
||||
"value": 5101
|
||||
},
|
||||
"OrderingApiHttpRule": {
|
||||
"value": 5102
|
||||
},
|
||||
"MarketingApiHttpRule": {
|
||||
"value": 5110
|
||||
},
|
||||
"LocationsApiHttpRule": {
|
||||
"value": 5109
|
||||
}
|
||||
}
|
||||
}
|
||||
@ -1,821 +0,0 @@
|
||||
{
|
||||
"$schema": "http://schema.management.azure.com/schemas/2015-01-01/deploymentTemplate.json",
|
||||
"contentVersion": "1.0.0.0",
|
||||
"parameters": {
|
||||
"clusterLocation": {
|
||||
"type": "string",
|
||||
"metadata": {
|
||||
"description": "Location of the Cluster"
|
||||
}
|
||||
},
|
||||
"clusterName": {
|
||||
"type": "string",
|
||||
"defaultValue": "Cluster",
|
||||
"metadata": {
|
||||
"description": "Name of your cluster - Between 3 and 23 characters. Letters and numbers only"
|
||||
}
|
||||
},
|
||||
"nt0applicationStartPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 20000
|
||||
},
|
||||
"nt0applicationEndPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 30000
|
||||
},
|
||||
"nt0ephemeralStartPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 49152
|
||||
},
|
||||
"nt0ephemeralEndPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 65534
|
||||
},
|
||||
"nt0fabricTcpGatewayPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 19000
|
||||
},
|
||||
"nt0fabricHttpGatewayPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 19080
|
||||
},
|
||||
"webMvcHttpPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 5100
|
||||
},
|
||||
"webSpaHttpPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 5104
|
||||
},
|
||||
"webStatusHttpPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 5107
|
||||
},
|
||||
"IdSrvHttpRule": {
|
||||
"type": "int",
|
||||
"defaultValue": 5105
|
||||
},
|
||||
"BasketApiHttpRule": {
|
||||
"type": "int",
|
||||
"defaultValue": 5103
|
||||
},
|
||||
"CatalogApiHttpRule": {
|
||||
"type": "int",
|
||||
"defaultValue": 5101
|
||||
},
|
||||
"OrderingApiHttpRule": {
|
||||
"type": "int",
|
||||
"defaultValue": 5102
|
||||
},
|
||||
"MarketingApiHttpRule": {
|
||||
"type": "int",
|
||||
"defaultValue": 5110
|
||||
},
|
||||
"LocationsApiHttpRule": {
|
||||
"type": "int",
|
||||
"defaultValue": 5109
|
||||
},
|
||||
"subnet0Name": {
|
||||
"type": "string",
|
||||
"defaultValue": "Subnet-0"
|
||||
},
|
||||
"subnet0Prefix": {
|
||||
"type": "string",
|
||||
"defaultValue": "10.0.0.0/24"
|
||||
},
|
||||
"computeLocation": {
|
||||
"type": "string"
|
||||
},
|
||||
"publicIPAddressName": {
|
||||
"type": "string",
|
||||
"defaultValue": "PublicIP-VM"
|
||||
},
|
||||
"publicIPAddressType": {
|
||||
"type": "string",
|
||||
"allowedValues": [
|
||||
"Dynamic"
|
||||
],
|
||||
"defaultValue": "Dynamic"
|
||||
},
|
||||
"vmStorageAccountContainerName": {
|
||||
"type": "string",
|
||||
"defaultValue": "vhds"
|
||||
},
|
||||
"adminUserName": {
|
||||
"type": "string",
|
||||
"defaultValue": "testadm",
|
||||
"metadata": {
|
||||
"description": "Remote desktop user Id"
|
||||
}
|
||||
},
|
||||
"adminPassword": {
|
||||
"type": "securestring",
|
||||
"metadata": {
|
||||
"description": "Remote desktop user password. Must be a strong password"
|
||||
}
|
||||
},
|
||||
"virtualNetworkName": {
|
||||
"type": "string",
|
||||
"defaultValue": "VNet"
|
||||
},
|
||||
"addressPrefix": {
|
||||
"type": "string",
|
||||
"defaultValue": "10.0.0.0/16"
|
||||
},
|
||||
"dnsName": {
|
||||
"type": "string"
|
||||
},
|
||||
"nicName": {
|
||||
"type": "string",
|
||||
"defaultValue": "NIC"
|
||||
},
|
||||
"lbName": {
|
||||
"type": "string",
|
||||
"defaultValue": "LoadBalancer"
|
||||
},
|
||||
"lbIPName": {
|
||||
"type": "string",
|
||||
"defaultValue": "PublicIP-LB-FE"
|
||||
},
|
||||
"overProvision": {
|
||||
"type": "string",
|
||||
"defaultValue": "false"
|
||||
},
|
||||
"vmImagePublisher": {
|
||||
"type": "string",
|
||||
"defaultValue": "Microsoft.Azure.ServiceFabric"
|
||||
},
|
||||
"vmImageOffer": {
|
||||
"type": "string",
|
||||
"defaultValue": "UbuntuServer"
|
||||
},
|
||||
"vmImageSku": {
|
||||
"type": "string",
|
||||
"defaultValue": "16.04"
|
||||
},
|
||||
"vmImageVersion": {
|
||||
"type": "string",
|
||||
"defaultValue": "6.0.12"
|
||||
},
|
||||
"clusterProtectionLevel": {
|
||||
"type": "string",
|
||||
"allowedValues": [
|
||||
"None",
|
||||
"Sign",
|
||||
"EncryptAndSign"
|
||||
],
|
||||
"defaultValue": "EncryptAndSign",
|
||||
"metadata": {
|
||||
"description": "Protection level.Three values are allowed - EncryptAndSign, Sign, None. It is best to keep the default of EncryptAndSign, unless you have a need not to"
|
||||
}
|
||||
},
|
||||
"certificateStoreValue": {
|
||||
"type": "string",
|
||||
"allowedValues": [
|
||||
"My"
|
||||
],
|
||||
"defaultValue": "My",
|
||||
"metadata": {
|
||||
"description": "The store name where the cert will be deployed in the virtual machine"
|
||||
}
|
||||
},
|
||||
"certificateThumbprint": {
|
||||
"type": "string",
|
||||
"metadata": {
|
||||
"description": "Certificate Thumbprint"
|
||||
}
|
||||
},
|
||||
"sourceVaultValue": {
|
||||
"type": "string",
|
||||
"metadata": {
|
||||
"description": "Resource Id of the key vault, is should be in the format of /subscriptions/<Sub ID>/resourceGroups/<Resource group name>/providers/Microsoft.KeyVault/vaults/<vault name>"
|
||||
}
|
||||
},
|
||||
"certificateUrlValue": {
|
||||
"type": "string",
|
||||
"metadata": {
|
||||
"description": "Refers to the location URL in your key vault where the certificate was uploaded, it is should be in the format of https://<name of the vault>.vault.azure.net:443/secrets/<exact location>"
|
||||
}
|
||||
},
|
||||
"storageAccountType": {
|
||||
"type": "string",
|
||||
"allowedValues": [
|
||||
"Standard_LRS",
|
||||
"Standard_GRS"
|
||||
],
|
||||
"defaultValue": "Standard_LRS",
|
||||
"metadata": {
|
||||
"description": "Replication option for the VM image storage account"
|
||||
}
|
||||
},
|
||||
"supportLogStorageAccountType": {
|
||||
"type": "string",
|
||||
"allowedValues": [
|
||||
"Standard_LRS",
|
||||
"Standard_GRS"
|
||||
],
|
||||
"defaultValue": "Standard_LRS",
|
||||
"metadata": {
|
||||
"description": "Replication option for the support log storage account"
|
||||
}
|
||||
},
|
||||
"supportLogStorageAccountName": {
|
||||
"type": "string",
|
||||
"defaultValue": "[toLower( concat('sflogs', uniqueString(resourceGroup().id),'2'))]",
|
||||
"metadata": {
|
||||
"description": "Name for the storage account that contains support logs from the cluster"
|
||||
}
|
||||
},
|
||||
"applicationDiagnosticsStorageAccountType": {
|
||||
"type": "string",
|
||||
"allowedValues": [
|
||||
"Standard_LRS",
|
||||
"Standard_GRS"
|
||||
],
|
||||
"defaultValue": "Standard_LRS",
|
||||
"metadata": {
|
||||
"description": "Replication option for the application diagnostics storage account"
|
||||
}
|
||||
},
|
||||
"applicationDiagnosticsStorageAccountName": {
|
||||
"type": "string",
|
||||
"defaultValue": "[toLower(concat(uniqueString(resourceGroup().id), '3' ))]",
|
||||
"metadata": {
|
||||
"description": "Name for the storage account that contains application diagnostics data from the cluster"
|
||||
}
|
||||
},
|
||||
"nt0InstanceCount": {
|
||||
"type": "int",
|
||||
"defaultValue": 5,
|
||||
"metadata": {
|
||||
"description": "Instance count for node type"
|
||||
}
|
||||
},
|
||||
"vmNodeType0Name": {
|
||||
"type": "string",
|
||||
"defaultValue": "primary",
|
||||
"maxLength": 9
|
||||
},
|
||||
"vmNodeType0Size": {
|
||||
"type": "string",
|
||||
"defaultValue": "Standard_D1_v2"
|
||||
}
|
||||
},
|
||||
"variables": {
|
||||
"vmssApiVersion": "2017-03-30",
|
||||
"lbApiVersion": "2015-06-15",
|
||||
"vNetApiVersion": "2015-06-15",
|
||||
"storageApiVersion": "2016-01-01",
|
||||
"publicIPApiVersion": "2015-06-15",
|
||||
"vnetID": "[resourceId('Microsoft.Network/virtualNetworks',parameters('virtualNetworkName'))]",
|
||||
"subnet0Ref": "[concat(variables('vnetID'),'/subnets/',parameters('subnet0Name'))]",
|
||||
"wadlogs": "<WadCfg><DiagnosticMonitorConfiguration>",
|
||||
"wadperfcounters1": "<PerformanceCounters scheduledTransferPeriod=\"PT1M\"><PerformanceCounterConfiguration counterSpecifier=\"\\Memory\\AvailableMemory\" sampleRate=\"PT15S\" unit=\"Bytes\"><annotation displayName=\"Memory available\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\Memory\\PercentAvailableMemory\" sampleRate=\"PT15S\" unit=\"Percent\"><annotation displayName=\"Mem. percent available\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\Memory\\UsedMemory\" sampleRate=\"PT15S\" unit=\"Bytes\"><annotation displayName=\"Memory used\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\Memory\\PercentUsedMemory\" sampleRate=\"PT15S\" unit=\"Percent\"><annotation displayName=\"Memory percentage\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\Memory\\PercentUsedByCache\" sampleRate=\"PT15S\" unit=\"Percent\"><annotation displayName=\"Mem. used by cache\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\Processor\\PercentIdleTime\" sampleRate=\"PT15S\" unit=\"Percent\"><annotation displayName=\"CPU idle time\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\Processor\\PercentUserTime\" sampleRate=\"PT15S\" unit=\"Percent\"><annotation displayName=\"CPU user time\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\Processor\\PercentProcessorTime\" sampleRate=\"PT15S\" unit=\"Percent\"><annotation displayName=\"CPU percentage guest OS\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\Processor\\PercentIOWaitTime\" sampleRate=\"PT15S\" unit=\"Percent\"><annotation displayName=\"CPU IO wait time\" locale=\"en-us\"/></PerformanceCounterConfiguration>",
|
||||
"wadperfcounters2": "<PerformanceCounterConfiguration counterSpecifier=\"\\PhysicalDisk\\BytesPerSecond\" sampleRate=\"PT15S\" unit=\"BytesPerSecond\"><annotation displayName=\"Disk total bytes\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\PhysicalDisk\\ReadBytesPerSecond\" sampleRate=\"PT15S\" unit=\"BytesPerSecond\"><annotation displayName=\"Disk read guest OS\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\PhysicalDisk\\WriteBytesPerSecond\" sampleRate=\"PT15S\" unit=\"BytesPerSecond\"><annotation displayName=\"Disk write guest OS\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\PhysicalDisk\\TransfersPerSecond\" sampleRate=\"PT15S\" unit=\"CountPerSecond\"><annotation displayName=\"Disk transfers\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\PhysicalDisk\\ReadsPerSecond\" sampleRate=\"PT15S\" unit=\"CountPerSecond\"><annotation displayName=\"Disk reads\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\PhysicalDisk\\WritesPerSecond\" sampleRate=\"PT15S\" unit=\"CountPerSecond\"><annotation displayName=\"Disk writes\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\PhysicalDisk\\AverageReadTime\" sampleRate=\"PT15S\" unit=\"Seconds\"><annotation displayName=\"Disk read time\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\PhysicalDisk\\AverageWriteTime\" sampleRate=\"PT15S\" unit=\"Seconds\"><annotation displayName=\"Disk write time\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\PhysicalDisk\\AverageTransferTime\" sampleRate=\"PT15S\" unit=\"Seconds\"><annotation displayName=\"Disk transfer time\" locale=\"en-us\"/></PerformanceCounterConfiguration><PerformanceCounterConfiguration counterSpecifier=\"\\PhysicalDisk\\AverageDiskQueueLength\" sampleRate=\"PT15S\" unit=\"Count\"><annotation displayName=\"Disk queue length\" locale=\"en-us\"/></PerformanceCounterConfiguration></PerformanceCounters>",
|
||||
"wadcfgxstart": "[concat(variables('wadlogs'),variables('wadperfcounters1'),variables('wadperfcounters2'),'<Metrics resourceId=\"')]",
|
||||
"wadcfgxend": "[concat('\"><MetricAggregation scheduledTransferPeriod=\"PT1H\"/><MetricAggregation scheduledTransferPeriod=\"PT1M\"/></Metrics></DiagnosticMonitorConfiguration></WadCfg>')]",
|
||||
"lbID0": "[resourceId('Microsoft.Network/loadBalancers', concat('LB','-', parameters('clusterName'),'-',parameters('vmNodeType0Name')))]",
|
||||
"lbIPConfig0": "[concat(variables('lbID0'),'/frontendIPConfigurations/LoadBalancerIPConfig')]",
|
||||
"lbPoolID0": "[concat(variables('lbID0'),'/backendAddressPools/LoadBalancerBEAddressPool')]",
|
||||
"lbProbeID0": "[concat(variables('lbID0'),'/probes/FabricGatewayProbe')]",
|
||||
"lbHttpProbeID0": "[concat(variables('lbID0'),'/probes/FabricHttpGatewayProbe')]",
|
||||
"lbNatPoolID0": "[concat(variables('lbID0'),'/inboundNatPools/LoadBalancerBEAddressNatPool')]",
|
||||
"vmStorageAccountName0": "[toLower(concat(uniqueString(resourceGroup().id), '1', '0' ))]",
|
||||
"wadmetricsresourceid0": "[concat('/subscriptions/',subscription().subscriptionId,'/resourceGroups/',resourceGroup().name ,'/providers/','Microsoft.Compute/virtualMachineScaleSets/', parameters('vmNodeType0Name'))]"
|
||||
},
|
||||
"resources": [
|
||||
{
|
||||
"apiVersion": "[variables('storageApiVersion')]",
|
||||
"type": "Microsoft.Storage/storageAccounts",
|
||||
"name": "[parameters('supportLogStorageAccountName')]",
|
||||
"location": "[parameters('computeLocation')]",
|
||||
"dependsOn": [],
|
||||
"properties": {},
|
||||
"kind": "Storage",
|
||||
"sku": {
|
||||
"name": "[parameters('supportLogStorageAccountType')]"
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[parameters('clusterName')]"
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "[variables('storageApiVersion')]",
|
||||
"type": "Microsoft.Storage/storageAccounts",
|
||||
"name": "[parameters('applicationDiagnosticsStorageAccountName')]",
|
||||
"location": "[parameters('computeLocation')]",
|
||||
"dependsOn": [],
|
||||
"properties": {},
|
||||
"kind": "Storage",
|
||||
"sku": {
|
||||
"name": "[parameters('applicationDiagnosticsStorageAccountType')]"
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[parameters('clusterName')]"
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "[variables('vNetApiVersion')]",
|
||||
"type": "Microsoft.Network/virtualNetworks",
|
||||
"name": "[parameters('virtualNetworkName')]",
|
||||
"location": "[parameters('computeLocation')]",
|
||||
"dependsOn": [],
|
||||
"properties": {
|
||||
"addressSpace": {
|
||||
"addressPrefixes": [
|
||||
"[parameters('addressPrefix')]"
|
||||
]
|
||||
},
|
||||
"subnets": [
|
||||
{
|
||||
"name": "[parameters('subnet0Name')]",
|
||||
"properties": {
|
||||
"addressPrefix": "[parameters('subnet0Prefix')]"
|
||||
}
|
||||
}
|
||||
]
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[parameters('clusterName')]"
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "[variables('publicIPApiVersion')]",
|
||||
"type": "Microsoft.Network/publicIPAddresses",
|
||||
"name": "[concat(parameters('lbIPName'),'-','0')]",
|
||||
"location": "[parameters('computeLocation')]",
|
||||
"properties": {
|
||||
"dnsSettings": {
|
||||
"domainNameLabel": "[parameters('dnsName')]"
|
||||
},
|
||||
"publicIPAllocationMethod": "Dynamic"
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[parameters('clusterName')]"
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "[variables('lbApiVersion')]",
|
||||
"type": "Microsoft.Network/loadBalancers",
|
||||
"name": "[concat('LB','-', parameters('clusterName'),'-',parameters('vmNodeType0Name'))]",
|
||||
"location": "[parameters('computeLocation')]",
|
||||
"dependsOn": [
|
||||
"[concat('Microsoft.Network/publicIPAddresses/',concat(parameters('lbIPName'),'-','0'))]"
|
||||
],
|
||||
"properties": {
|
||||
"frontendIPConfigurations": [
|
||||
{
|
||||
"name": "LoadBalancerIPConfig",
|
||||
"properties": {
|
||||
"publicIPAddress": {
|
||||
"id": "[resourceId('Microsoft.Network/publicIPAddresses',concat(parameters('lbIPName'),'-','0'))]"
|
||||
}
|
||||
}
|
||||
}
|
||||
],
|
||||
"backendAddressPools": [
|
||||
{
|
||||
"name": "LoadBalancerBEAddressPool",
|
||||
"properties": {}
|
||||
}
|
||||
],
|
||||
"loadBalancingRules": [
|
||||
{
|
||||
"name": "LBRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('nt0fabricTcpGatewayPort')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('nt0fabricTcpGatewayPort')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"probe": {
|
||||
"id": "[variables('lbProbeID0')]"
|
||||
},
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "LBHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('nt0fabricHttpGatewayPort')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('nt0fabricHttpGatewayPort')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"probe": {
|
||||
"id": "[variables('lbHttpProbeID0')]"
|
||||
},
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "WebMVCHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('webMvcHttpPort')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('webMvcHttpPort')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "WebSPAHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('webSpaHttpPort')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('webSpaHttpPort')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "WebStatusHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('webStatusHttpPort')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('webStatusHttpPort')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "IdSrvHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('IdSrvHttpRule')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('IdSrvHttpRule')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "BasketApiHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('BasketApiHttpRule')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('BasketApiHttpRule')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "CatalogApiHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('CatalogApiHttpRule')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('CatalogApiHttpRule')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "OrderingApiHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('OrderingApiHttpRule')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('OrderingApiHttpRule')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "MarketingApiHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('MarketingApiHttpRule')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('MarketingApiHttpRule')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "LocationsApiHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('LocationsApiHttpRule')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('LocationsApiHttpRule')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
}
|
||||
],
|
||||
"probes": [
|
||||
{
|
||||
"name": "FabricGatewayProbe",
|
||||
"properties": {
|
||||
"intervalInSeconds": 5,
|
||||
"numberOfProbes": 2,
|
||||
"port": "[parameters('nt0fabricTcpGatewayPort')]",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "FabricHttpGatewayProbe",
|
||||
"properties": {
|
||||
"intervalInSeconds": 5,
|
||||
"numberOfProbes": 2,
|
||||
"port": "[parameters('nt0fabricHttpGatewayPort')]",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
}
|
||||
],
|
||||
"inboundNatPools": [
|
||||
{
|
||||
"name": "LoadBalancerBEAddressNatPool",
|
||||
"properties": {
|
||||
"backendPort": "22",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPortRangeEnd": "4500",
|
||||
"frontendPortRangeStart": "3389",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
}
|
||||
]
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[parameters('clusterName')]"
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "[variables('vmssApiVersion')]",
|
||||
"type": "Microsoft.Compute/virtualMachineScaleSets",
|
||||
"name": "[parameters('vmNodeType0Name')]",
|
||||
"location": "[parameters('computeLocation')]",
|
||||
"dependsOn": [
|
||||
"[concat('Microsoft.Network/virtualNetworks/', parameters('virtualNetworkName'))]",
|
||||
"[concat('Microsoft.Network/loadBalancers/', concat('LB','-', parameters('clusterName'),'-',parameters('vmNodeType0Name')))]",
|
||||
"[concat('Microsoft.Storage/storageAccounts/', parameters('supportLogStorageAccountName'))]",
|
||||
"[concat('Microsoft.Storage/storageAccounts/', parameters('applicationDiagnosticsStorageAccountName'))]"
|
||||
],
|
||||
"properties": {
|
||||
"overprovision": "[parameters('overProvision')]",
|
||||
"upgradePolicy": {
|
||||
"mode": "Automatic"
|
||||
},
|
||||
"virtualMachineProfile": {
|
||||
"extensionProfile": {
|
||||
"extensions": [
|
||||
{
|
||||
"name": "[concat(parameters('vmNodeType0Name'),'_ServiceFabricLinuxNode')]",
|
||||
"properties": {
|
||||
"type": "ServiceFabricLinuxNode",
|
||||
"autoUpgradeMinorVersion": true,
|
||||
"protectedSettings": {
|
||||
"StorageAccountKey1": "[listKeys(resourceId('Microsoft.Storage/storageAccounts', parameters('supportLogStorageAccountName')),'2015-05-01-preview').key1]",
|
||||
"StorageAccountKey2": "[listKeys(resourceId('Microsoft.Storage/storageAccounts', parameters('supportLogStorageAccountName')),'2015-05-01-preview').key2]"
|
||||
},
|
||||
"publisher": "Microsoft.Azure.ServiceFabric",
|
||||
"settings": {
|
||||
"clusterEndpoint": "[reference(parameters('clusterName')).clusterEndpoint]",
|
||||
"nodeTypeRef": "[parameters('vmNodeType0Name')]",
|
||||
"durabilityLevel": "Bronze",
|
||||
"enableParallelJobs": true,
|
||||
"nicPrefixOverride": "[parameters('subnet0Prefix')]",
|
||||
"certificate": {
|
||||
"thumbprint": "[parameters('certificateThumbprint')]",
|
||||
"x509StoreName": "[parameters('certificateStoreValue')]"
|
||||
}
|
||||
},
|
||||
"typeHandlerVersion": "1.0"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "[concat('VMDiagnosticsVmExt','_vmNodeType0Name')]",
|
||||
"properties": {
|
||||
"type": "LinuxDiagnostic",
|
||||
"autoUpgradeMinorVersion": true,
|
||||
"protectedSettings": {
|
||||
"storageAccountName": "[parameters('applicationDiagnosticsStorageAccountName')]",
|
||||
"storageAccountKey": "[listKeys(resourceId('Microsoft.Storage/storageAccounts', parameters('applicationDiagnosticsStorageAccountName')),'2015-05-01-preview').key1]",
|
||||
"storageAccountEndPoint": "https://core.windows.net/"
|
||||
},
|
||||
"publisher": "Microsoft.OSTCExtensions",
|
||||
"settings": {
|
||||
"xmlCfg": "[base64(concat(variables('wadcfgxstart'),variables('wadmetricsresourceid0'),variables('wadcfgxend')))]",
|
||||
"StorageAccount": "[parameters('applicationDiagnosticsStorageAccountName')]"
|
||||
},
|
||||
"typeHandlerVersion": "2.3"
|
||||
}
|
||||
}
|
||||
]
|
||||
},
|
||||
"networkProfile": {
|
||||
"networkInterfaceConfigurations": [
|
||||
{
|
||||
"name": "[concat(parameters('nicName'), '-0')]",
|
||||
"properties": {
|
||||
"ipConfigurations": [
|
||||
{
|
||||
"name": "[concat(parameters('nicName'),'-',0)]",
|
||||
"properties": {
|
||||
"loadBalancerBackendAddressPools": [
|
||||
{
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
}
|
||||
],
|
||||
"loadBalancerInboundNatPools": [
|
||||
{
|
||||
"id": "[variables('lbNatPoolID0')]"
|
||||
}
|
||||
],
|
||||
"subnet": {
|
||||
"id": "[variables('subnet0Ref')]"
|
||||
}
|
||||
}
|
||||
}
|
||||
],
|
||||
"primary": true
|
||||
}
|
||||
}
|
||||
]
|
||||
},
|
||||
"osProfile": {
|
||||
"adminPassword": "[parameters('adminPassword')]",
|
||||
"adminUsername": "[parameters('adminUsername')]",
|
||||
"computernamePrefix": "[parameters('vmNodeType0Name')]",
|
||||
"secrets": [
|
||||
{
|
||||
"sourceVault": {
|
||||
"id": "[parameters('sourceVaultValue')]"
|
||||
},
|
||||
"vaultCertificates": [
|
||||
{
|
||||
"certificateUrl": "[parameters('certificateUrlValue')]"
|
||||
}
|
||||
]
|
||||
}
|
||||
]
|
||||
},
|
||||
"storageProfile": {
|
||||
"imageReference": {
|
||||
"publisher": "[parameters('vmImagePublisher')]",
|
||||
"offer": "[parameters('vmImageOffer')]",
|
||||
"sku": "[parameters('vmImageSku')]",
|
||||
"version": "[parameters('vmImageVersion')]"
|
||||
},
|
||||
"osDisk": {
|
||||
"caching": "ReadOnly",
|
||||
"createOption": "FromImage",
|
||||
"managedDisk": {
|
||||
"storageAccountType": "[parameters('storageAccountType')]"
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
},
|
||||
"sku": {
|
||||
"name": "[parameters('vmNodeType0Size')]",
|
||||
"capacity": "[parameters('nt0InstanceCount')]",
|
||||
"tier": "Standard"
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[parameters('clusterName')]"
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "2017-07-01-preview",
|
||||
"type": "Microsoft.ServiceFabric/clusters",
|
||||
"name": "[parameters('clusterName')]",
|
||||
"location": "[parameters('clusterLocation')]",
|
||||
"dependsOn": [
|
||||
"[concat('Microsoft.Storage/storageAccounts/', parameters('supportLogStorageAccountName'))]"
|
||||
],
|
||||
"properties": {
|
||||
"addonFeatures": [
|
||||
"DnsService"
|
||||
],
|
||||
"certificate": {
|
||||
"thumbprint": "[parameters('certificateThumbprint')]",
|
||||
"x509StoreName": "[parameters('certificateStoreValue')]"
|
||||
},
|
||||
"clientCertificateCommonNames": [],
|
||||
"clientCertificateThumbprints": [],
|
||||
"clusterCodeVersion": "6.0.120.1",
|
||||
"clusterState": "Default",
|
||||
"diagnosticsStorageAccountConfig": {
|
||||
"blobEndpoint": "[reference(concat('Microsoft.Storage/storageAccounts/', parameters('supportLogStorageAccountName')), variables('storageApiVersion')).primaryEndpoints.blob]",
|
||||
"protectedAccountKeyName": "StorageAccountKey1",
|
||||
"queueEndpoint": "[reference(concat('Microsoft.Storage/storageAccounts/', parameters('supportLogStorageAccountName')), variables('storageApiVersion')).primaryEndpoints.queue]",
|
||||
"storageAccountName": "[parameters('supportLogStorageAccountName')]",
|
||||
"tableEndpoint": "[reference(concat('Microsoft.Storage/storageAccounts/', parameters('supportLogStorageAccountName')), variables('storageApiVersion')).primaryEndpoints.table]"
|
||||
},
|
||||
"fabricSettings": [
|
||||
{
|
||||
"parameters": [
|
||||
{
|
||||
"name": "ClusterProtectionLevel",
|
||||
"value": "[parameters('clusterProtectionLevel')]"
|
||||
}
|
||||
],
|
||||
"name": "Security"
|
||||
}
|
||||
],
|
||||
"managementEndpoint": "[concat('https://',reference(concat(parameters('lbIPName'),'-','0')).dnsSettings.fqdn,':',parameters('nt0fabricHttpGatewayPort'))]",
|
||||
"nodeTypes": [
|
||||
{
|
||||
"name": "[parameters('vmNodeType0Name')]",
|
||||
"applicationPorts": {
|
||||
"endPort": "[parameters('nt0applicationEndPort')]",
|
||||
"startPort": "[parameters('nt0applicationStartPort')]"
|
||||
},
|
||||
"clientConnectionEndpointPort": "[parameters('nt0fabricTcpGatewayPort')]",
|
||||
"durabilityLevel": "Bronze",
|
||||
"ephemeralPorts": {
|
||||
"endPort": "[parameters('nt0ephemeralEndPort')]",
|
||||
"startPort": "[parameters('nt0ephemeralStartPort')]"
|
||||
},
|
||||
"httpGatewayEndpointPort": "[parameters('nt0fabricHttpGatewayPort')]",
|
||||
"isPrimary": true,
|
||||
"vmInstanceCount": "[parameters('nt0InstanceCount')]"
|
||||
}
|
||||
],
|
||||
"provisioningState": "Default",
|
||||
"reliabilityLevel": "Silver",
|
||||
"upgradeMode": "Manual",
|
||||
"vmImage": "Linux"
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[parameters('clusterName')]"
|
||||
}
|
||||
}
|
||||
],
|
||||
"outputs": {
|
||||
"clusterProperties": {
|
||||
"value": "[reference(parameters('clusterName'))]",
|
||||
"type": "object"
|
||||
}
|
||||
}
|
||||
}
|
||||
@ -1,102 +0,0 @@
|
||||
{
|
||||
"$schema": "https://schema.management.azure.com/schemas/2015-01-01/deploymentParameters.json#",
|
||||
"contentVersion": "1.0.0.0",
|
||||
"parameters": {
|
||||
"clusterName": {
|
||||
"value": "pro-eshop-sflinux-cluster"
|
||||
},
|
||||
"clusterLocation": {
|
||||
"value": "westus"
|
||||
},
|
||||
"computeLocation": {
|
||||
"value": "westus"
|
||||
},
|
||||
"adminUserName": {
|
||||
"value": "eshop"
|
||||
},
|
||||
"adminPassword": {
|
||||
"value": "Pass@word1"
|
||||
},
|
||||
"nicName": {
|
||||
"value": "NIC-eshopsflinsec"
|
||||
},
|
||||
"publicIPAddressName": {
|
||||
"value": "eshopsflinsec-PubIP"
|
||||
},
|
||||
"dnsName": {
|
||||
"value": "pro-eshop-sflinux-cluster"
|
||||
},
|
||||
"virtualNetworkName": {
|
||||
"value": "VNet-eshopsflin"
|
||||
},
|
||||
"lbName": {
|
||||
"value": "LB-eshopsflin"
|
||||
},
|
||||
"lbIPName": {
|
||||
"value": "LBIP-eshopsflin"
|
||||
},
|
||||
"sourceVaultValue": {
|
||||
"value": "your-value-check-keyvault-at-azure"
|
||||
},
|
||||
"certificateUrlValue": {
|
||||
"value": "your-value-check-keyvault-at-azure"
|
||||
},
|
||||
"certificateThumbprint": {
|
||||
"value": "your-value-check-keyvault-at-azure"
|
||||
},
|
||||
"vmImageSku": {
|
||||
"value": "16.04-LTS"
|
||||
},
|
||||
"vmImageVersion": {
|
||||
"value": "latest"
|
||||
},
|
||||
"vmImagePublisher": {
|
||||
"value": "Canonical"
|
||||
},
|
||||
"nt0ephemeralStartPort": {
|
||||
"value": 49152
|
||||
},
|
||||
"nt0ephemeralEndPort": {
|
||||
"value": 65534
|
||||
},
|
||||
"nt0applicationStartPort": {
|
||||
"value": 20000
|
||||
},
|
||||
"nt0applicationEndPort": {
|
||||
"value": 30000
|
||||
},
|
||||
"nt0fabricTcpGatewayPort": {
|
||||
"value": 19000
|
||||
},
|
||||
"nt0fabricHttpGatewayPort": {
|
||||
"value": 19080
|
||||
},
|
||||
"webMvcHttpPort": {
|
||||
"value": 5100
|
||||
},
|
||||
"webSpaHttpPort": {
|
||||
"value": 5104
|
||||
},
|
||||
"webStatusHttpPort": {
|
||||
"value": 5107
|
||||
},
|
||||
"IdSrvHttpRule": {
|
||||
"value": 5105
|
||||
},
|
||||
"BasketApiHttpRule": {
|
||||
"value": 5103
|
||||
},
|
||||
"CatalogApiHttpRule": {
|
||||
"value": 5101
|
||||
},
|
||||
"OrderingApiHttpRule": {
|
||||
"value": 5102
|
||||
},
|
||||
"MarketingApiHttpRule": {
|
||||
"value": 5110
|
||||
},
|
||||
"LocationsApiHttpRule": {
|
||||
"value": 5109
|
||||
}
|
||||
}
|
||||
}
|
||||
@ -1,53 +0,0 @@
|
||||
Param(
|
||||
[parameter(Mandatory=$true)][string]$vaultName,
|
||||
[parameter(Mandatory=$true)][string]$certName,
|
||||
[parameter(Mandatory=$true)][string]$certPwd,
|
||||
[parameter(Mandatory=$true)][string]$subjectName,
|
||||
[parameter(Mandatory=$false)][string]$ValidityInMonths=12,
|
||||
[parameter(Mandatory=$true)][string]$saveDir
|
||||
)
|
||||
|
||||
|
||||
#Log in Azure Account
|
||||
Login-AzureRmAccount
|
||||
|
||||
|
||||
# Create Cert in KeyVault
|
||||
Write-Host "Creating certificate in Azure KeyVault..." -ForegroundColor Yellow
|
||||
$policy = New-AzureKeyVaultCertificatePolicy -SubjectName $subjectName -IssuerName Self -ValidityInMonths $ValidityInMonths
|
||||
Add-AzureKeyVaultCertificate -VaultName $vaultName -Name $certName -CertificatePolicy $policy
|
||||
|
||||
# Downloading Certificate
|
||||
Write-Host "Downloading Certificate from KeyVault..." -ForegroundColor Yellow
|
||||
|
||||
$Stoploop = $false
|
||||
$Retrycount = 0
|
||||
|
||||
do {
|
||||
try {
|
||||
|
||||
$kvSecret = Get-AzureKeyVaultSecret -VaultName $vaultName -Name $certName -ErrorAction SilentlyContinue
|
||||
$kvSecretBytes = [System.Convert]::FromBase64String($kvSecret.SecretValueText)
|
||||
$certCollection = New-Object System.Security.Cryptography.X509Certificates.X509Certificate2Collection
|
||||
$certCollection.Import($kvSecretBytes,$null,[System.Security.Cryptography.X509Certificates.X509KeyStorageFlags]::Exportable)
|
||||
$protectedCertificateBytes = $certCollection.Export([System.Security.Cryptography.X509Certificates.X509ContentType]::Pkcs12, $certPwd)
|
||||
[System.IO.File]::WriteAllBytes($saveDir + "\" + $certName + ".pfx", $protectedCertificateBytes)
|
||||
|
||||
$Stoploop = $true
|
||||
Write-Host "Finished!" -ForegroundColor Yellow
|
||||
}
|
||||
catch {
|
||||
if ($Retrycount -gt 5){
|
||||
$Stoploop = $true
|
||||
Write-Host "Not possible to retrieve the certificate!" -ForegroundColor Yellow
|
||||
}
|
||||
else {
|
||||
Start-Sleep -Seconds 20
|
||||
$Retrycount = $Retrycount + 1
|
||||
}
|
||||
}
|
||||
}
|
||||
While ($Stoploop -eq $false)
|
||||
|
||||
# Show Certificate Values
|
||||
Get-AzureKeyVaultCertificate -VaultName $vaultName -Name $certName
|
||||
@ -1,138 +0,0 @@
|
||||
# Deploying a Service Fabric cluster based on Windows nodes
|
||||
|
||||
## A. Unsecured cluster (SF Windows cluster)
|
||||
For a secured cluster, see option B. below.
|
||||
|
||||
You can always deploy a SF cluster through the Azure portal, as explained in this article: https://docs.microsoft.com/en-us/azure/service-fabric/service-fabric-get-started-azure-cluster
|
||||
|
||||
However, when creating a cluster, there are quite a few configurations to take into account, like enabling the internal DNS service or Reverse Proxy service, choosing between Linux/Windows, open/publish your application ports in the load-balancer and most of all (the most complex setup) how to create a secure cluster.
|
||||
|
||||
Because of those reasons, we have created a set of ARM templates and scripts so you can create, re-create and configure the SF clusters much faster, as explained below:
|
||||
|
||||
Within eShopOnContainers root folder, at the folder [..\deploy\az\servicefabric\WindowsContainers](https://github.com/dotnet-architecture/eShopOnContainers/tree/dev/deploy/az/servicefabric/WindowsContainers), you can find the ARM template `servicefabricdeploy.json` and its parameters file (`servicefabricdeploy.parameters.json`) to create a Service Fabric cluster environment for Windows Containers (NOT SECURED CLUSTER).
|
||||
|
||||
## Edit the servicefabricdeploy.parameters.json file
|
||||
|
||||
Edit the following params in `servicefabricdeploy.parameters.json` file to set your values:
|
||||
|
||||
- clusterName: Name of your SF cluster
|
||||
- clusterLocation: Datacenter location, like westus or westeurope
|
||||
- computeLocation: Datacenter location, like westus or westeurope
|
||||
- adminUserName: user-name for VMs administration
|
||||
- adminPassword: user-password for VMs administration
|
||||
- dnsName: Name assigned to your SF dns
|
||||
|
||||
Optionally, you could modify which ports are opened in the LoadBalancer for the multiple eShopOnContainer apps and API services.
|
||||
By default, they are setup as:
|
||||
- webMvcHttpPort: 5100
|
||||
- webSpaHttpPort: 5104
|
||||
- webStatusHttpPort: 5107
|
||||
- IdSrvHttpRule: 5105
|
||||
- BasketApiHttpRule: 5103
|
||||
- CatalogApiHttpRule: 5101
|
||||
- OrderingApiHttpRule: 5102
|
||||
- MarketingApiHttpRule: 5110
|
||||
- LocationsApiHttpRule: 5109
|
||||
|
||||
## Deploy the Service Fabric cluster using the script and ARM templates
|
||||
|
||||
Once parameter file is edited you can deploy it using [create-resources script](../readme.md).
|
||||
|
||||
For example, to deploy the cluster to a new resourcegroup located in westus, using the Command Prompt, go to `deploy\az` folder and type:
|
||||
```
|
||||
create-resources.cmd servicefabric\WindowsContainers\servicefabricdeploy qa-eshop-sfwin-resgrp -c westus
|
||||
```
|
||||
|
||||
You should see a similar execution to the following:
|
||||
|
||||
|
||||
Now, if you go to your subscription in Azure, you should be able to see the SF cluster already created and available, like in the following image:
|
||||
|
||||
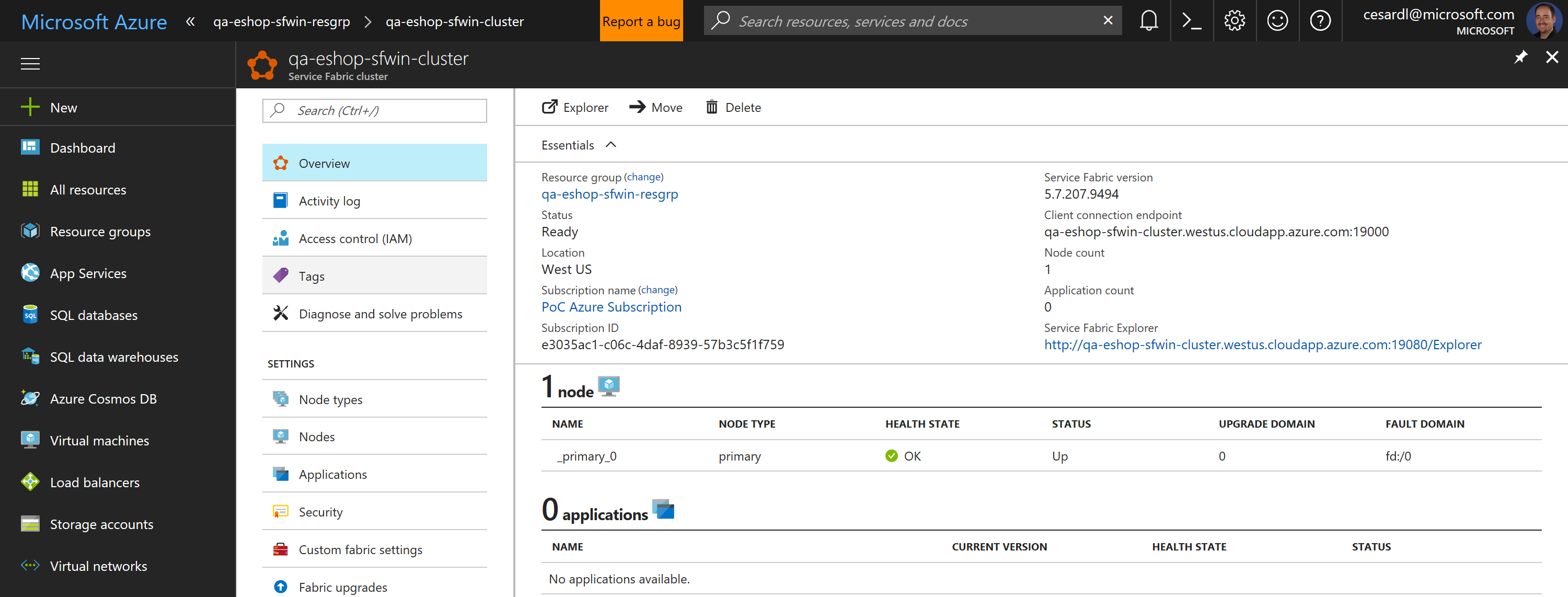
|
||||
|
||||
In this case, this is an unsecured SF cluster with a single Windows node, good for initial tests and getting started with SF.
|
||||
|
||||
|
||||
## B. Secured cluster (SF Windows cluster)
|
||||
|
||||
Within eShopOnContainers root folder, at the folder [..\deploy\az\servicefabric\WindowsContainers](https://github.com/dotnet-architecture/eShopOnContainers/tree/dev/deploy/az/servicefabric/WindowsContainers), you can find the ARM template `servicefabricdeploysecured.json` and its parameter file (`servicefabricdeploysecured.parameters.json`) to create a secured Service Fabric cluster environment for Windows Containers (IN THIS CASE, IT IS A SECURED CLUSTER USING A CERTIFICATE).
|
||||
|
||||
## Create Azure Keyvault service
|
||||
Go to PortalAzure and create a Keyvault service. Make sure Enable access for deployment checkboxes are selected.
|
||||
|
||||

|
||||
|
||||
## Generate a certificate in Azure Keyvault
|
||||
In a POWER-SHELL window, move to the folder [..\deploy\az\servicefabric\WindowsContainers](https://github.com/dotnet-architecture/eShopOnContainers/tree/dev/deploy/az/servicefabric/WindowsContainers).
|
||||
|
||||
**Select your Azure subscription** You might have [several Azure subscriptions](https://docs.microsoft.com/en-us/cli/azure/account#set) as shown if you type the following.
|
||||
|
||||
>```
|
||||
>az account list
|
||||
>```
|
||||
If you have multiple subscription accounts, you first need to select the Azure subscription account you want to target. Type the following:
|
||||
>```
|
||||
>az account set --subscription "Your Azure Subscription Name or ID"
|
||||
>```
|
||||
|
||||
**Execute the gen-keyvaultcert.ps1 script** to generate and download a certificate from Keyvault.
|
||||
Make sure you're going to run it against the Azure subscription you mean it.
|
||||
|
||||
You might need to authenticate from the browser when running this PowerShell script.
|
||||
|
||||
```
|
||||
.\gen-keyvaultcert.ps1 -vaultName <your_keyvault_service> -certName <your_cert_name> -certPwd <your_cert_pwd> -subjectName CN=<your_sf_dns_name>.westus.cloudapp.azure.com -saveDir C:\Users\<your-user>\Downloads
|
||||
|
||||
```
|
||||
You should see a similar execution to the following:
|
||||

|
||||
|
||||
IMPORTANT: At this point, copy/cut the .PFX certificate file saved in the downloads forlder and save it in a secure place.
|
||||
|
||||
## Install the certificate
|
||||
Install the certificate (by double-clicking on the .PFX file) under 'Current User' store location (by default location) and check it as exportable.
|
||||
|
||||
<img src="../../../../img/sf/install-cert.PNG">
|
||||
|
||||
Also, install the same certificate as CA (Certificate Authority) under Current User, too.
|
||||
|
||||

|
||||
|
||||
## Editing servicefabricdeploysecured.parameters.json file
|
||||
|
||||
Edit the parameters in `servicefabricdeploysecured.parameters.json` in a similar way you can do with the unsecured .json file shown above (clusterName, dnsName, etc.), plus edit the following values:
|
||||
|
||||
- sourceVaultValue: Your Azure Keyvault's RESOURCE ID (check Azure keyvault properties, similar to: /subscriptions/e1234ac1-c09c-3jaf-6767-98b3c5f1f246/resourceGroups/eshop-global-resgrp/providers/Microsoft.KeyVault/vaults/eshopkeyvault")
|
||||
|
||||
- certificateUrlValue: Your certificate Secret Identifier (check Azure Keyvault secret certificate properties, should be in the format of https://<name of the vault>.vault.azure.net:443/secrets/<exact location>, similar to:
|
||||
https://eshopkeyvault.vault.azure.net/secrets/pro-eshop-sfwin-cluster-cert/w647684642cGE2sj83b3hfe4h8e08963)
|
||||
|
||||
- certificateThumbprint: certificate thumbprint (check azure Keyvault certificate thumbprint, something like 88JK453486D55A6818573G0DW9100365HDK70HDK)
|
||||
|
||||
## Deploy the secured SF cluster (Windows nodes)
|
||||
|
||||
Once parameters file is edited you can deploy it using [create-resources script](../readme.md).
|
||||
|
||||
Use a command prompt window positioned into the deploy\az folder.
|
||||
|
||||
```
|
||||
create-resources.cmd servicefabric\WindowsContainers\servicefabricdeploysecured pro-eshop-sfwin-resgrp -c westus
|
||||
```
|
||||
The execution should be something like the following:
|
||||
|
||||
|
||||
|
||||
Once the cluster is created you can explore it with Azure's portal, like in the following image:
|
||||
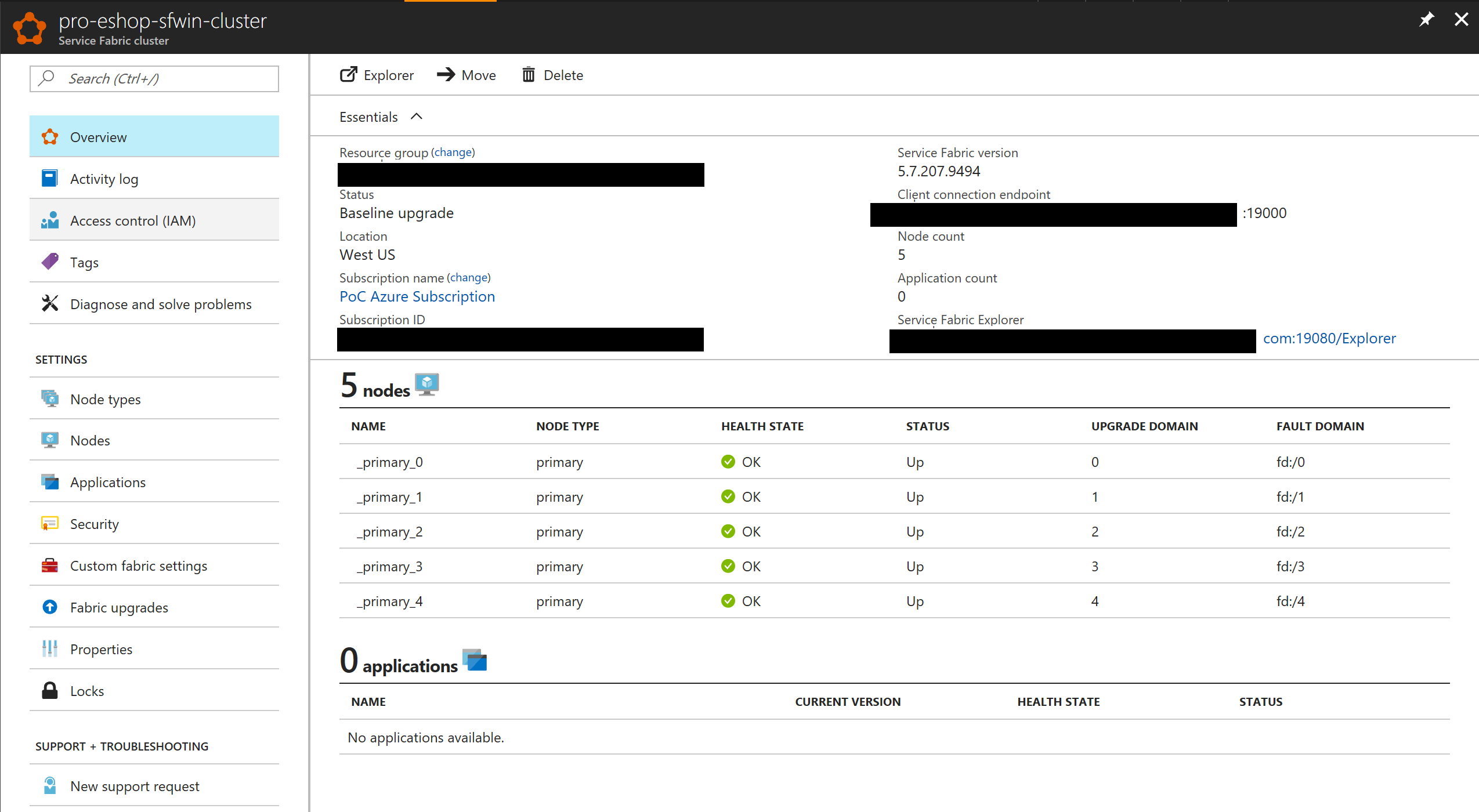
|
||||
|
||||
In this case, the ARM template is creating a 5 node cluster when creating a SECURE cluster for "production".
|
||||
|
||||
|
||||
# Deploy eShopOnServiceFabric with Visual Studio.
|
||||
|
||||
Modify the cloud.xml file of each Service Fabric application in PublishProfile directory and set your certificate settings to be able to deploy eshopOnContainers in the secured cluster:
|
||||
|
||||
<img src="../../../../img/sf/cloud_publishProfile.PNG">
|
||||
|
||||
|
||||
|
||||
@ -1,859 +0,0 @@
|
||||
{
|
||||
"$schema": "http://schema.management.azure.com/schemas/2015-01-01/deploymentTemplate.json",
|
||||
"contentVersion": "1.0.0.0",
|
||||
"parameters": {
|
||||
"prefix": {
|
||||
"type": "string"
|
||||
},
|
||||
"clusterLocation": {
|
||||
"type": "string",
|
||||
"metadata": {
|
||||
"description": "Location of the Cluster"
|
||||
}
|
||||
},
|
||||
"clusterName": {
|
||||
"type": "string",
|
||||
"defaultValue": "Cluster",
|
||||
"metadata": {
|
||||
"description": "Name of your cluster - Between 3 and 23 characters. Letters and numbers only"
|
||||
}
|
||||
},
|
||||
"nt0applicationStartPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 20000
|
||||
},
|
||||
"nt0applicationEndPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 30000
|
||||
},
|
||||
"nt0ephemeralStartPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 49152
|
||||
},
|
||||
"nt0ephemeralEndPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 65534
|
||||
},
|
||||
"nt0fabricTcpGatewayPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 19000
|
||||
},
|
||||
"nt0fabricHttpGatewayPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 19080
|
||||
},
|
||||
"nt0reverseProxyEndpointPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 19081
|
||||
},
|
||||
"webMvcHttpPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 5100
|
||||
},
|
||||
"webSpaHttpPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 5104
|
||||
},
|
||||
"webStatusHttpPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 5107
|
||||
},
|
||||
"IdSrvHttpRule": {
|
||||
"type": "int",
|
||||
"defaultValue": 5105
|
||||
},
|
||||
"BasketApiHttpRule": {
|
||||
"type": "int",
|
||||
"defaultValue": 5103
|
||||
},
|
||||
"CatalogApiHttpRule": {
|
||||
"type": "int",
|
||||
"defaultValue": 5101
|
||||
},
|
||||
"OrderingApiHttpRule": {
|
||||
"type": "int",
|
||||
"defaultValue": 5102
|
||||
},
|
||||
"MarketingApiHttpRule": {
|
||||
"type": "int",
|
||||
"defaultValue": 5110
|
||||
},
|
||||
"LocationsApiHttpRule": {
|
||||
"type": "int",
|
||||
"defaultValue": 5109
|
||||
},
|
||||
"subnet0Name": {
|
||||
"type": "string",
|
||||
"defaultValue": "Subnet-0"
|
||||
},
|
||||
"subnet0Prefix": {
|
||||
"type": "string",
|
||||
"defaultValue": "10.0.0.0/24"
|
||||
},
|
||||
"computeLocation": {
|
||||
"type": "string"
|
||||
},
|
||||
"publicIPAddressName": {
|
||||
"type": "string",
|
||||
"defaultValue": "PublicIP-VM"
|
||||
},
|
||||
"publicIPAddressType": {
|
||||
"type": "string",
|
||||
"allowedValues": [
|
||||
"Dynamic"
|
||||
],
|
||||
"defaultValue": "Dynamic"
|
||||
},
|
||||
"vmStorageAccountContainerName": {
|
||||
"type": "string",
|
||||
"defaultValue": "vhds"
|
||||
},
|
||||
"adminUserName": {
|
||||
"type": "string",
|
||||
"defaultValue": "testadm",
|
||||
"metadata": {
|
||||
"description": "Remote desktop user Id"
|
||||
}
|
||||
},
|
||||
"adminPassword": {
|
||||
"type": "securestring",
|
||||
"metadata": {
|
||||
"description": "Remote desktop user password. Must be a strong password"
|
||||
}
|
||||
},
|
||||
"virtualNetworkName": {
|
||||
"type": "string",
|
||||
"defaultValue": "VNet"
|
||||
},
|
||||
"addressPrefix": {
|
||||
"type": "string",
|
||||
"defaultValue": "10.0.0.0/16"
|
||||
},
|
||||
"dnsName": {
|
||||
"type": "string"
|
||||
},
|
||||
"nicName": {
|
||||
"type": "string",
|
||||
"defaultValue": "NIC"
|
||||
},
|
||||
"lbName": {
|
||||
"type": "string",
|
||||
"defaultValue": "LoadBalancer"
|
||||
},
|
||||
"lbIPName": {
|
||||
"type": "string",
|
||||
"defaultValue": "PublicIP-LB-FE"
|
||||
},
|
||||
"overProvision": {
|
||||
"type": "string",
|
||||
"defaultValue": "false"
|
||||
},
|
||||
"vmImagePublisher": {
|
||||
"type": "string",
|
||||
"defaultValue": "MicrosoftWindowsServer"
|
||||
},
|
||||
"vmImageOffer": {
|
||||
"type": "string",
|
||||
"defaultValue": "WindowsServer"
|
||||
},
|
||||
"vmImageSku": {
|
||||
"type": "string",
|
||||
"defaultValue": "2012-R2-Datacenter"
|
||||
},
|
||||
"vmImageVersion": {
|
||||
"type": "string",
|
||||
"defaultValue": "latest"
|
||||
},
|
||||
"storageAccountType": {
|
||||
"type": "string",
|
||||
"allowedValues": [
|
||||
"Standard_LRS",
|
||||
"Standard_GRS"
|
||||
],
|
||||
"defaultValue": "Standard_LRS",
|
||||
"metadata": {
|
||||
"description": "Replication option for the VM image storage account"
|
||||
}
|
||||
},
|
||||
"supportLogStorageAccountType": {
|
||||
"type": "string",
|
||||
"allowedValues": [
|
||||
"Standard_LRS",
|
||||
"Standard_GRS"
|
||||
],
|
||||
"defaultValue": "Standard_LRS",
|
||||
"metadata": {
|
||||
"description": "Replication option for the support log storage account"
|
||||
}
|
||||
},
|
||||
"supportLogStorageAccountName": {
|
||||
"type": "string",
|
||||
"defaultValue": "[toLower( concat('sflogs', uniqueString(resourceGroup().id),'2'))]",
|
||||
"metadata": {
|
||||
"description": "Name for the storage account that contains support logs from the cluster"
|
||||
}
|
||||
},
|
||||
"applicationDiagnosticsStorageAccountType": {
|
||||
"type": "string",
|
||||
"allowedValues": [
|
||||
"Standard_LRS",
|
||||
"Standard_GRS"
|
||||
],
|
||||
"defaultValue": "Standard_LRS",
|
||||
"metadata": {
|
||||
"description": "Replication option for the application diagnostics storage account"
|
||||
}
|
||||
},
|
||||
"applicationDiagnosticsStorageAccountName": {
|
||||
"type": "string",
|
||||
"defaultValue": "[toLower(concat(uniqueString(resourceGroup().id), '3' ))]",
|
||||
"metadata": {
|
||||
"description": "Name for the storage account that contains application diagnostics data from the cluster"
|
||||
}
|
||||
},
|
||||
"nt0InstanceCount": {
|
||||
"type": "int",
|
||||
"defaultValue": 1,
|
||||
"metadata": {
|
||||
"description": "Instance count for node type"
|
||||
}
|
||||
},
|
||||
"vmNodeType0Name": {
|
||||
"type": "string",
|
||||
"defaultValue": "primary",
|
||||
"maxLength": 9
|
||||
},
|
||||
"vmNodeType0Size": {
|
||||
"type": "string",
|
||||
"defaultValue": "Standard_D2_v2"
|
||||
}
|
||||
},
|
||||
"variables": {
|
||||
"vmssApiVersion": "2017-03-30",
|
||||
"lbApiVersion": "2015-06-15",
|
||||
"vNetApiVersion": "2015-06-15",
|
||||
"storageApiVersion": "2016-01-01",
|
||||
"publicIPApiVersion": "2015-06-15",
|
||||
"vnetID": "[resourceId('Microsoft.Network/virtualNetworks',parameters('virtualNetworkName'))]",
|
||||
"subnet0Ref": "[concat(variables('vnetID'),'/subnets/',parameters('subnet0Name'))]",
|
||||
"lbID0": "[resourceId('Microsoft.Network/loadBalancers', concat('LB','-', variables('clusterName'),'-',parameters('vmNodeType0Name')))]",
|
||||
"lbIPConfig0": "[concat(variables('lbID0'),'/frontendIPConfigurations/LoadBalancerIPConfig')]",
|
||||
"lbPoolID0": "[concat(variables('lbID0'),'/backendAddressPools/LoadBalancerBEAddressPool')]",
|
||||
"lbProbeID0": "[concat(variables('lbID0'),'/probes/FabricGatewayProbe')]",
|
||||
"lbHttpProbeID0": "[concat(variables('lbID0'),'/probes/FabricHttpGatewayProbe')]",
|
||||
"lbNatPoolID0": "[concat(variables('lbID0'),'/inboundNatPools/LoadBalancerBEAddressNatPool')]",
|
||||
"vmStorageAccountName0": "[toLower(concat(uniqueString(resourceGroup().id), '1', '0' ))]",
|
||||
"supportLogStorageAccountName": "[take(concat(parameters('prefix'), parameters('supportLogStorageAccountName')),22)]",
|
||||
"applicationDiagnosticsStorageAccountName" : "[take(concat(parameters('prefix'), parameters('applicationDiagnosticsStorageAccountName')),22)]",
|
||||
"clusterName": "[concat(parameters('prefix'), parameters('clusterName'))]",
|
||||
"uniqueStringArray0": [
|
||||
"[concat(variables('vmStorageAccountName0'), '0')]",
|
||||
"[concat(variables('vmStorageAccountName0'), '1')]",
|
||||
"[concat(variables('vmStorageAccountName0'), '2')]",
|
||||
"[concat(variables('vmStorageAccountName0'), '3')]",
|
||||
"[concat(variables('vmStorageAccountName0'), '4')]"
|
||||
]
|
||||
},
|
||||
"resources": [
|
||||
{
|
||||
"apiVersion": "[variables('storageApiVersion')]",
|
||||
"type": "Microsoft.Storage/storageAccounts",
|
||||
"name": "[variables('supportLogStorageAccountName')]",
|
||||
"location": "[parameters('computeLocation')]",
|
||||
"dependsOn": [],
|
||||
"properties": {},
|
||||
"kind": "Storage",
|
||||
"sku": {
|
||||
"name": "[parameters('supportLogStorageAccountType')]"
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[variables('clusterName')]"
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "[variables('storageApiVersion')]",
|
||||
"type": "Microsoft.Storage/storageAccounts",
|
||||
"name": "[variables('applicationDiagnosticsStorageAccountName')]",
|
||||
"location": "[parameters('computeLocation')]",
|
||||
"dependsOn": [],
|
||||
"properties": {},
|
||||
"kind": "Storage",
|
||||
"sku": {
|
||||
"name": "[parameters('applicationDiagnosticsStorageAccountType')]"
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[variables('clusterName')]"
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "[variables('vNetApiVersion')]",
|
||||
"type": "Microsoft.Network/virtualNetworks",
|
||||
"name": "[parameters('virtualNetworkName')]",
|
||||
"location": "[parameters('computeLocation')]",
|
||||
"dependsOn": [],
|
||||
"properties": {
|
||||
"addressSpace": {
|
||||
"addressPrefixes": [
|
||||
"[parameters('addressPrefix')]"
|
||||
]
|
||||
},
|
||||
"subnets": [
|
||||
{
|
||||
"name": "[parameters('subnet0Name')]",
|
||||
"properties": {
|
||||
"addressPrefix": "[parameters('subnet0Prefix')]"
|
||||
}
|
||||
}
|
||||
]
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[variables('clusterName')]"
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "[variables('publicIPApiVersion')]",
|
||||
"type": "Microsoft.Network/publicIPAddresses",
|
||||
"name": "[concat(parameters('lbIPName'),'-','0')]",
|
||||
"location": "[parameters('computeLocation')]",
|
||||
"properties": {
|
||||
"dnsSettings": {
|
||||
"domainNameLabel": "[parameters('dnsName')]"
|
||||
},
|
||||
"publicIPAllocationMethod": "Dynamic"
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[variables('clusterName')]"
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "[variables('lbApiVersion')]",
|
||||
"type": "Microsoft.Network/loadBalancers",
|
||||
"name": "[concat('LB','-', variables('clusterName'),'-',parameters('vmNodeType0Name'))]",
|
||||
"location": "[parameters('computeLocation')]",
|
||||
"dependsOn": [
|
||||
"[concat('Microsoft.Network/publicIPAddresses/',concat(parameters('lbIPName'),'-','0'))]"
|
||||
],
|
||||
"properties": {
|
||||
"frontendIPConfigurations": [
|
||||
{
|
||||
"name": "LoadBalancerIPConfig",
|
||||
"properties": {
|
||||
"publicIPAddress": {
|
||||
"id": "[resourceId('Microsoft.Network/publicIPAddresses',concat(parameters('lbIPName'),'-','0'))]"
|
||||
}
|
||||
}
|
||||
}
|
||||
],
|
||||
"backendAddressPools": [
|
||||
{
|
||||
"name": "LoadBalancerBEAddressPool",
|
||||
"properties": {}
|
||||
}
|
||||
],
|
||||
"loadBalancingRules": [
|
||||
{
|
||||
"name": "LBRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('nt0fabricTcpGatewayPort')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('nt0fabricTcpGatewayPort')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"probe": {
|
||||
"id": "[variables('lbProbeID0')]"
|
||||
},
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "LBHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('nt0fabricHttpGatewayPort')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('nt0fabricHttpGatewayPort')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"probe": {
|
||||
"id": "[variables('lbHttpProbeID0')]"
|
||||
},
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "ReverseProxyHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('nt0reverseProxyEndpointPort')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('nt0reverseProxyEndpointPort')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"probe": {
|
||||
"id": "[variables('lbHttpProbeID0')]"
|
||||
},
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "WebMVCHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('webMvcHttpPort')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('webMvcHttpPort')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"probe": {
|
||||
"id": "[variables('lbHttpProbeID0')]"
|
||||
},
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "WebSPAHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('webSpaHttpPort')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('webSpaHttpPort')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"probe": {
|
||||
"id": "[variables('lbHttpProbeID0')]"
|
||||
},
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "WebStatusHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('webStatusHttpPort')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('webStatusHttpPort')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"probe": {
|
||||
"id": "[variables('lbHttpProbeID0')]"
|
||||
},
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "IdSrvHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('IdSrvHttpRule')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('IdSrvHttpRule')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"probe": {
|
||||
"id": "[variables('lbHttpProbeID0')]"
|
||||
},
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "BasketApiHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('BasketApiHttpRule')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('BasketApiHttpRule')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "CatalogApiHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('CatalogApiHttpRule')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('CatalogApiHttpRule')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "OrderingApiHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('OrderingApiHttpRule')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('OrderingApiHttpRule')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "MarketingApiHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('MarketingApiHttpRule')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('MarketingApiHttpRule')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "LocationsApiHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('LocationsApiHttpRule')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('LocationsApiHttpRule')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
}
|
||||
],
|
||||
"probes": [
|
||||
{
|
||||
"name": "FabricGatewayProbe",
|
||||
"properties": {
|
||||
"intervalInSeconds": 5,
|
||||
"numberOfProbes": 2,
|
||||
"port": "[parameters('nt0fabricTcpGatewayPort')]",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "FabricHttpGatewayProbe",
|
||||
"properties": {
|
||||
"intervalInSeconds": 5,
|
||||
"numberOfProbes": 2,
|
||||
"port": "[parameters('nt0fabricHttpGatewayPort')]",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
}
|
||||
],
|
||||
"inboundNatPools": [
|
||||
{
|
||||
"name": "LoadBalancerBEAddressNatPool",
|
||||
"properties": {
|
||||
"backendPort": "3389",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPortRangeEnd": "4500",
|
||||
"frontendPortRangeStart": "3389",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
}
|
||||
]
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[variables('clusterName')]"
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "[variables('storageApiVersion')]",
|
||||
"type": "Microsoft.Storage/storageAccounts",
|
||||
"name": "[variables('uniqueStringArray0')[copyIndex()]]",
|
||||
"location": "[parameters('computeLocation')]",
|
||||
"dependsOn": [],
|
||||
"properties": {},
|
||||
"copy": {
|
||||
"name": "storageLoop",
|
||||
"count": 5
|
||||
},
|
||||
"kind": "Storage",
|
||||
"sku": {
|
||||
"name": "[parameters('storageAccountType')]"
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[variables('clusterName')]"
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "[variables('vmssApiVersion')]",
|
||||
"type": "Microsoft.Compute/virtualMachineScaleSets",
|
||||
"name": "[parameters('vmNodeType0Name')]",
|
||||
"location": "[parameters('computeLocation')]",
|
||||
"dependsOn": [
|
||||
"[concat('Microsoft.Network/virtualNetworks/', parameters('virtualNetworkName'))]",
|
||||
"[concat('Microsoft.Storage/storageAccounts/', variables('uniqueStringArray0')[0])]",
|
||||
"[concat('Microsoft.Storage/storageAccounts/', variables('uniqueStringArray0')[1])]",
|
||||
"[concat('Microsoft.Storage/storageAccounts/', variables('uniqueStringArray0')[2])]",
|
||||
"[concat('Microsoft.Storage/storageAccounts/', variables('uniqueStringArray0')[3])]",
|
||||
"[concat('Microsoft.Storage/storageAccounts/', variables('uniqueStringArray0')[4])]",
|
||||
"[concat('Microsoft.Network/loadBalancers/', concat('LB','-', variables('clusterName'),'-',parameters('vmNodeType0Name')))]",
|
||||
"[concat('Microsoft.Storage/storageAccounts/', variables('supportLogStorageAccountName'))]",
|
||||
"[concat('Microsoft.Storage/storageAccounts/', variables('applicationDiagnosticsStorageAccountName'))]"
|
||||
],
|
||||
"properties": {
|
||||
"overprovision": "[parameters('overProvision')]",
|
||||
"upgradePolicy": {
|
||||
"mode": "Automatic"
|
||||
},
|
||||
"virtualMachineProfile": {
|
||||
"extensionProfile": {
|
||||
"extensions": [
|
||||
{
|
||||
"name": "[concat(parameters('vmNodeType0Name'),'_ServiceFabricNode')]",
|
||||
"properties": {
|
||||
"type": "ServiceFabricNode",
|
||||
"autoUpgradeMinorVersion": true,
|
||||
"protectedSettings": {
|
||||
"StorageAccountKey1": "[listKeys(resourceId('Microsoft.Storage/storageAccounts', variables('supportLogStorageAccountName')),'2015-05-01-preview').key1]",
|
||||
"StorageAccountKey2": "[listKeys(resourceId('Microsoft.Storage/storageAccounts', variables('supportLogStorageAccountName')),'2015-05-01-preview').key2]"
|
||||
},
|
||||
"publisher": "Microsoft.Azure.ServiceFabric",
|
||||
"settings": {
|
||||
"clusterEndpoint": "[reference(variables('clusterName')).clusterEndpoint]",
|
||||
"nodeTypeRef": "[parameters('vmNodeType0Name')]",
|
||||
"dataPath": "D:\\\\SvcFab",
|
||||
"durabilityLevel": "Bronze",
|
||||
"enableParallelJobs": true,
|
||||
"nicPrefixOverride": "[parameters('subnet0Prefix')]"
|
||||
},
|
||||
"typeHandlerVersion": "1.0"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "[concat('VMDiagnosticsVmExt','_vmNodeType0Name')]",
|
||||
"properties": {
|
||||
"type": "IaaSDiagnostics",
|
||||
"autoUpgradeMinorVersion": true,
|
||||
"protectedSettings": {
|
||||
"storageAccountName": "[variables('applicationDiagnosticsStorageAccountName')]",
|
||||
"storageAccountKey": "[listKeys(resourceId('Microsoft.Storage/storageAccounts', variables('applicationDiagnosticsStorageAccountName')),'2015-05-01-preview').key1]",
|
||||
"storageAccountEndPoint": "https://core.windows.net/"
|
||||
},
|
||||
"publisher": "Microsoft.Azure.Diagnostics",
|
||||
"settings": {
|
||||
"WadCfg": {
|
||||
"DiagnosticMonitorConfiguration": {
|
||||
"overallQuotaInMB": "50000",
|
||||
"EtwProviders": {
|
||||
"EtwEventSourceProviderConfiguration": [
|
||||
{
|
||||
"provider": "Microsoft-ServiceFabric-Actors",
|
||||
"scheduledTransferKeywordFilter": "1",
|
||||
"scheduledTransferPeriod": "PT5M",
|
||||
"DefaultEvents": {
|
||||
"eventDestination": "ServiceFabricReliableActorEventTable"
|
||||
}
|
||||
},
|
||||
{
|
||||
"provider": "Microsoft-ServiceFabric-Services",
|
||||
"scheduledTransferPeriod": "PT5M",
|
||||
"DefaultEvents": {
|
||||
"eventDestination": "ServiceFabricReliableServiceEventTable"
|
||||
}
|
||||
}
|
||||
],
|
||||
"EtwManifestProviderConfiguration": [
|
||||
{
|
||||
"provider": "cbd93bc2-71e5-4566-b3a7-595d8eeca6e8",
|
||||
"scheduledTransferLogLevelFilter": "Information",
|
||||
"scheduledTransferKeywordFilter": "4611686018427387904",
|
||||
"scheduledTransferPeriod": "PT5M",
|
||||
"DefaultEvents": {
|
||||
"eventDestination": "ServiceFabricSystemEventTable"
|
||||
}
|
||||
}
|
||||
]
|
||||
}
|
||||
}
|
||||
},
|
||||
"StorageAccount": "[variables('applicationDiagnosticsStorageAccountName')]"
|
||||
},
|
||||
"typeHandlerVersion": "1.5"
|
||||
}
|
||||
}
|
||||
]
|
||||
},
|
||||
"networkProfile": {
|
||||
"networkInterfaceConfigurations": [
|
||||
{
|
||||
"name": "[concat(parameters('nicName'), '-0')]",
|
||||
"properties": {
|
||||
"ipConfigurations": [
|
||||
{
|
||||
"name": "[concat(parameters('nicName'),'-',0)]",
|
||||
"properties": {
|
||||
"loadBalancerBackendAddressPools": [
|
||||
{
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
}
|
||||
],
|
||||
"loadBalancerInboundNatPools": [
|
||||
{
|
||||
"id": "[variables('lbNatPoolID0')]"
|
||||
}
|
||||
],
|
||||
"subnet": {
|
||||
"id": "[variables('subnet0Ref')]"
|
||||
}
|
||||
}
|
||||
}
|
||||
],
|
||||
"primary": true
|
||||
}
|
||||
}
|
||||
]
|
||||
},
|
||||
"osProfile": {
|
||||
"adminPassword": "[parameters('adminPassword')]",
|
||||
"adminUsername": "[parameters('adminUsername')]",
|
||||
"computernamePrefix": "[parameters('vmNodeType0Name')]"
|
||||
},
|
||||
"storageProfile": {
|
||||
"imageReference": {
|
||||
"publisher": "[parameters('vmImagePublisher')]",
|
||||
"offer": "[parameters('vmImageOffer')]",
|
||||
"sku": "[parameters('vmImageSku')]",
|
||||
"version": "[parameters('vmImageVersion')]"
|
||||
},
|
||||
"osDisk": {
|
||||
"caching": "ReadOnly",
|
||||
"createOption": "FromImage",
|
||||
"vhdContainers": [
|
||||
"[concat(reference(concat('Microsoft.Storage/storageAccounts/', variables('uniqueStringArray0')[0]), variables('storageApiVersion')).primaryEndpoints.blob, parameters('vmStorageAccountContainerName'))]",
|
||||
"[concat(reference(concat('Microsoft.Storage/storageAccounts/', variables('uniqueStringArray0')[1]), variables('storageApiVersion')).primaryEndpoints.blob, parameters('vmStorageAccountContainerName'))]",
|
||||
"[concat(reference(concat('Microsoft.Storage/storageAccounts/', variables('uniqueStringArray0')[2]), variables('storageApiVersion')).primaryEndpoints.blob, parameters('vmStorageAccountContainerName'))]",
|
||||
"[concat(reference(concat('Microsoft.Storage/storageAccounts/', variables('uniqueStringArray0')[3]), variables('storageApiVersion')).primaryEndpoints.blob, parameters('vmStorageAccountContainerName'))]",
|
||||
"[concat(reference(concat('Microsoft.Storage/storageAccounts/', variables('uniqueStringArray0')[4]), variables('storageApiVersion')).primaryEndpoints.blob, parameters('vmStorageAccountContainerName'))]"
|
||||
],
|
||||
"name": "vmssosdisk"
|
||||
}
|
||||
}
|
||||
}
|
||||
},
|
||||
"sku": {
|
||||
"name": "[parameters('vmNodeType0Size')]",
|
||||
"capacity": "[parameters('nt0InstanceCount')]",
|
||||
"tier": "Standard"
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[variables('clusterName')]"
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "2017-07-01-preview",
|
||||
"type": "Microsoft.ServiceFabric/clusters",
|
||||
"name": "[variables('clusterName')]",
|
||||
"location": "[parameters('clusterLocation')]",
|
||||
"dependsOn": [
|
||||
"[concat('Microsoft.Storage/storageAccounts/', variables('supportLogStorageAccountName'))]"
|
||||
],
|
||||
"properties": {
|
||||
"addonFeatures": [
|
||||
"DnsService"
|
||||
],
|
||||
"clientCertificateCommonNames": [],
|
||||
"clientCertificateThumbprints": [],
|
||||
"clusterCodeVersion": "6.0.232.9494",
|
||||
"clusterState": "Default",
|
||||
"diagnosticsStorageAccountConfig": {
|
||||
"blobEndpoint": "[reference(concat('Microsoft.Storage/storageAccounts/', variables('supportLogStorageAccountName')), variables('storageApiVersion')).primaryEndpoints.blob]",
|
||||
"protectedAccountKeyName": "StorageAccountKey1",
|
||||
"queueEndpoint": "[reference(concat('Microsoft.Storage/storageAccounts/', variables('supportLogStorageAccountName')), variables('storageApiVersion')).primaryEndpoints.queue]",
|
||||
"storageAccountName": "[variables('supportLogStorageAccountName')]",
|
||||
"tableEndpoint": "[reference(concat('Microsoft.Storage/storageAccounts/', variables('supportLogStorageAccountName')), variables('storageApiVersion')).primaryEndpoints.table]"
|
||||
},
|
||||
"fabricSettings": [],
|
||||
"managementEndpoint": "[concat('http://',reference(concat(parameters('lbIPName'),'-','0')).dnsSettings.fqdn,':',parameters('nt0fabricHttpGatewayPort'))]",
|
||||
"nodeTypes": [
|
||||
{
|
||||
"name": "[parameters('vmNodeType0Name')]",
|
||||
"applicationPorts": {
|
||||
"endPort": "[parameters('nt0applicationEndPort')]",
|
||||
"startPort": "[parameters('nt0applicationStartPort')]"
|
||||
},
|
||||
"clientConnectionEndpointPort": "[parameters('nt0fabricTcpGatewayPort')]",
|
||||
"durabilityLevel": "Bronze",
|
||||
"ephemeralPorts": {
|
||||
"endPort": "[parameters('nt0ephemeralEndPort')]",
|
||||
"startPort": "[parameters('nt0ephemeralStartPort')]"
|
||||
},
|
||||
"httpGatewayEndpointPort": "[parameters('nt0fabricHttpGatewayPort')]",
|
||||
"isPrimary": true,
|
||||
"reverseProxyEndpointPort": "[parameters('nt0reverseProxyEndpointPort')]",
|
||||
"vmInstanceCount": "[parameters('nt0InstanceCount')]"
|
||||
}
|
||||
],
|
||||
"provisioningState": "Default",
|
||||
"reliabilityLevel": "None",
|
||||
"upgradeMode": "Manual",
|
||||
"vmImage": "Windows"
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[variables('clusterName')]"
|
||||
}
|
||||
}
|
||||
],
|
||||
"outputs": {
|
||||
"clusterProperties": {
|
||||
"value": "[reference(variables('clusterName'))]",
|
||||
"type": "object"
|
||||
}
|
||||
}
|
||||
}
|
||||
@ -1,100 +0,0 @@
|
||||
{
|
||||
"$schema": "https://schema.management.azure.com/schemas/2015-01-01/deploymentParameters.json#",
|
||||
"contentVersion": "1.0.0.0",
|
||||
"parameters": {
|
||||
"prefix": {
|
||||
"value": "qa"
|
||||
},
|
||||
"clusterName": {
|
||||
"value": "-eshop-sfwin-cluster"
|
||||
},
|
||||
"clusterLocation": {
|
||||
"value": "westus"
|
||||
},
|
||||
"computeLocation": {
|
||||
"value": "westus"
|
||||
},
|
||||
"adminUserName": {
|
||||
"value": "testedu"
|
||||
},
|
||||
"adminPassword": {
|
||||
"value": "testedu1234!"
|
||||
},
|
||||
"nicName": {
|
||||
"value": "NIC-eshopsfwin"
|
||||
},
|
||||
"publicIPAddressName": {
|
||||
"value": "eshopsfwin-PubIP"
|
||||
},
|
||||
"dnsName": {
|
||||
"value": "testedu-eshop-sfwin-cluster"
|
||||
},
|
||||
"virtualNetworkName": {
|
||||
"value": "VNet-eshopsfwin"
|
||||
},
|
||||
"lbName": {
|
||||
"value": "LB-eshopsfwin"
|
||||
},
|
||||
"lbIPName": {
|
||||
"value": "LBIP-eshopsfwin"
|
||||
},
|
||||
"applicationDiagnosticsStorageAccountName": {
|
||||
"value": "sfdiageshopw"
|
||||
},
|
||||
"supportLogStorageAccountName": {
|
||||
"value": "sflogeshopw"
|
||||
},
|
||||
"vmImageSku": {
|
||||
"value": "2016-Datacenter-with-Containers"
|
||||
},
|
||||
"nt0ephemeralStartPort": {
|
||||
"value": 49152
|
||||
},
|
||||
"nt0ephemeralEndPort": {
|
||||
"value": 65534
|
||||
},
|
||||
"nt0applicationStartPort": {
|
||||
"value": 20000
|
||||
},
|
||||
"nt0applicationEndPort": {
|
||||
"value": 30000
|
||||
},
|
||||
"nt0fabricTcpGatewayPort": {
|
||||
"value": 19000
|
||||
},
|
||||
"nt0fabricHttpGatewayPort": {
|
||||
"value": 19080
|
||||
},
|
||||
"nt0reverseProxyEndpointPort": {
|
||||
"value": 19081
|
||||
},
|
||||
"webMvcHttpPort": {
|
||||
"value": 5100
|
||||
},
|
||||
"webSpaHttpPort": {
|
||||
"value": 5104
|
||||
},
|
||||
"webStatusHttpPort": {
|
||||
"value": 5107
|
||||
},
|
||||
"IdSrvHttpRule": {
|
||||
"value": 5105
|
||||
},
|
||||
"BasketApiHttpRule": {
|
||||
"value": 5103
|
||||
},
|
||||
"CatalogApiHttpRule": {
|
||||
"value": 5101
|
||||
},
|
||||
"OrderingApiHttpRule": {
|
||||
"value": 5102
|
||||
},
|
||||
"MarketingApiHttpRule": {
|
||||
"value": 5110
|
||||
},
|
||||
"LocationsApiHttpRule": {
|
||||
"value": 5109
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
@ -1,924 +0,0 @@
|
||||
{
|
||||
"$schema": "http://schema.management.azure.com/schemas/2015-01-01/deploymentTemplate.json",
|
||||
"contentVersion": "1.0.0.0",
|
||||
"parameters": {
|
||||
"clusterLocation": {
|
||||
"type": "string",
|
||||
"metadata": {
|
||||
"description": "Location of the Cluster"
|
||||
}
|
||||
},
|
||||
"clusterName": {
|
||||
"type": "string",
|
||||
"defaultValue": "Cluster",
|
||||
"metadata": {
|
||||
"description": "Name of your cluster - Between 3 and 23 characters. Letters and numbers only"
|
||||
}
|
||||
},
|
||||
"nt0applicationStartPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 20000
|
||||
},
|
||||
"nt0applicationEndPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 30000
|
||||
},
|
||||
"nt0ephemeralStartPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 49152
|
||||
},
|
||||
"nt0ephemeralEndPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 65534
|
||||
},
|
||||
"nt0fabricTcpGatewayPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 19000
|
||||
},
|
||||
"nt0fabricHttpGatewayPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 19080
|
||||
},
|
||||
"nt0reverseProxyEndpointPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 19081
|
||||
},
|
||||
"webMvcHttpPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 5100
|
||||
},
|
||||
"webSpaHttpPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 5104
|
||||
},
|
||||
"webStatusHttpPort": {
|
||||
"type": "int",
|
||||
"defaultValue": 5107
|
||||
},
|
||||
"IdSrvHttpRule": {
|
||||
"type": "int",
|
||||
"defaultValue": 5105
|
||||
},
|
||||
"BasketApiHttpRule": {
|
||||
"type": "int",
|
||||
"defaultValue": 5103
|
||||
},
|
||||
"CatalogApiHttpRule": {
|
||||
"type": "int",
|
||||
"defaultValue": 5101
|
||||
},
|
||||
"OrderingApiHttpRule": {
|
||||
"type": "int",
|
||||
"defaultValue": 5102
|
||||
},
|
||||
"MarketingApiHttpRule": {
|
||||
"type": "int",
|
||||
"defaultValue": 5110
|
||||
},
|
||||
"LocationsApiHttpRule": {
|
||||
"type": "int",
|
||||
"defaultValue": 5109
|
||||
},
|
||||
"subnet0Name": {
|
||||
"type": "string",
|
||||
"defaultValue": "Subnet-0"
|
||||
},
|
||||
"subnet0Prefix": {
|
||||
"type": "string",
|
||||
"defaultValue": "10.0.0.0/24"
|
||||
},
|
||||
"computeLocation": {
|
||||
"type": "string"
|
||||
},
|
||||
"publicIPAddressName": {
|
||||
"type": "string",
|
||||
"defaultValue": "PublicIP-VM"
|
||||
},
|
||||
"publicIPAddressType": {
|
||||
"type": "string",
|
||||
"allowedValues": [
|
||||
"Dynamic"
|
||||
],
|
||||
"defaultValue": "Dynamic"
|
||||
},
|
||||
"vmStorageAccountContainerName": {
|
||||
"type": "string",
|
||||
"defaultValue": "vhds"
|
||||
},
|
||||
"adminUserName": {
|
||||
"type": "string",
|
||||
"defaultValue": "testadm",
|
||||
"metadata": {
|
||||
"description": "Remote desktop user Id"
|
||||
}
|
||||
},
|
||||
"adminPassword": {
|
||||
"type": "securestring",
|
||||
"metadata": {
|
||||
"description": "Remote desktop user password. Must be a strong password"
|
||||
}
|
||||
},
|
||||
"virtualNetworkName": {
|
||||
"type": "string",
|
||||
"defaultValue": "VNet"
|
||||
},
|
||||
"addressPrefix": {
|
||||
"type": "string",
|
||||
"defaultValue": "10.0.0.0/16"
|
||||
},
|
||||
"dnsName": {
|
||||
"type": "string"
|
||||
},
|
||||
"nicName": {
|
||||
"type": "string",
|
||||
"defaultValue": "NIC"
|
||||
},
|
||||
"lbName": {
|
||||
"type": "string",
|
||||
"defaultValue": "LoadBalancer"
|
||||
},
|
||||
"lbIPName": {
|
||||
"type": "string",
|
||||
"defaultValue": "PublicIP-LB-FE"
|
||||
},
|
||||
"overProvision": {
|
||||
"type": "string",
|
||||
"defaultValue": "false"
|
||||
},
|
||||
"vmImagePublisher": {
|
||||
"type": "string",
|
||||
"defaultValue": "MicrosoftWindowsServer"
|
||||
},
|
||||
"vmImageOffer": {
|
||||
"type": "string",
|
||||
"defaultValue": "WindowsServer"
|
||||
},
|
||||
"vmImageSku": {
|
||||
"type": "string",
|
||||
"defaultValue": "2012-R2-Datacenter"
|
||||
},
|
||||
"vmImageVersion": {
|
||||
"type": "string",
|
||||
"defaultValue": "latest"
|
||||
},
|
||||
"clusterProtectionLevel": {
|
||||
"type": "string",
|
||||
"allowedValues": [
|
||||
"None",
|
||||
"Sign",
|
||||
"EncryptAndSign"
|
||||
],
|
||||
"defaultValue": "EncryptAndSign",
|
||||
"metadata": {
|
||||
"description": "Protection level.Three values are allowed - EncryptAndSign, Sign, None. It is best to keep the default of EncryptAndSign, unless you have a need not to"
|
||||
}
|
||||
},
|
||||
"certificateStoreValue": {
|
||||
"type": "string",
|
||||
"allowedValues": [
|
||||
"My"
|
||||
],
|
||||
"defaultValue": "My",
|
||||
"metadata": {
|
||||
"description": "The store name where the cert will be deployed in the virtual machine"
|
||||
}
|
||||
},
|
||||
"certificateThumbprint": {
|
||||
"type": "string",
|
||||
"metadata": {
|
||||
"description": "Certificate Thumbprint"
|
||||
}
|
||||
},
|
||||
"sourceVaultValue": {
|
||||
"type": "string",
|
||||
"metadata": {
|
||||
"description": "Resource Id of the key vault, is should be in the format of /subscriptions/<Sub ID>/resourceGroups/<Resource group name>/providers/Microsoft.KeyVault/vaults/<vault name>"
|
||||
}
|
||||
},
|
||||
"certificateUrlValue": {
|
||||
"type": "string",
|
||||
"metadata": {
|
||||
"description": "Refers to the location URL in your key vault where the certificate was uploaded, it is should be in the format of https://<name of the vault>.vault.azure.net:443/secrets/<exact location>"
|
||||
}
|
||||
},
|
||||
"storageAccountType": {
|
||||
"type": "string",
|
||||
"allowedValues": [
|
||||
"Standard_LRS",
|
||||
"Standard_GRS"
|
||||
],
|
||||
"defaultValue": "Standard_LRS",
|
||||
"metadata": {
|
||||
"description": "Replication option for the VM image storage account"
|
||||
}
|
||||
},
|
||||
"supportLogStorageAccountType": {
|
||||
"type": "string",
|
||||
"allowedValues": [
|
||||
"Standard_LRS",
|
||||
"Standard_GRS"
|
||||
],
|
||||
"defaultValue": "Standard_LRS",
|
||||
"metadata": {
|
||||
"description": "Replication option for the support log storage account"
|
||||
}
|
||||
},
|
||||
"supportLogStorageAccountName": {
|
||||
"type": "string",
|
||||
"defaultValue": "[toLower( concat('sflogs', uniqueString(resourceGroup().id),'2'))]",
|
||||
"metadata": {
|
||||
"description": "Name for the storage account that contains support logs from the cluster"
|
||||
}
|
||||
},
|
||||
"applicationDiagnosticsStorageAccountType": {
|
||||
"type": "string",
|
||||
"allowedValues": [
|
||||
"Standard_LRS",
|
||||
"Standard_GRS"
|
||||
],
|
||||
"defaultValue": "Standard_LRS",
|
||||
"metadata": {
|
||||
"description": "Replication option for the application diagnostics storage account"
|
||||
}
|
||||
},
|
||||
"applicationDiagnosticsStorageAccountName": {
|
||||
"type": "string",
|
||||
"defaultValue": "[toLower(concat(uniqueString(resourceGroup().id), '3' ))]",
|
||||
"metadata": {
|
||||
"description": "Name for the storage account that contains application diagnostics data from the cluster"
|
||||
}
|
||||
},
|
||||
"nt0InstanceCount": {
|
||||
"type": "int",
|
||||
"defaultValue": 5,
|
||||
"metadata": {
|
||||
"description": "Instance count for node type"
|
||||
}
|
||||
},
|
||||
"vmNodeType0Name": {
|
||||
"type": "string",
|
||||
"defaultValue": "primary",
|
||||
"maxLength": 9
|
||||
},
|
||||
"vmNodeType0Size": {
|
||||
"type": "string",
|
||||
"defaultValue": "Standard_D2_v2"
|
||||
}
|
||||
},
|
||||
"variables": {
|
||||
"vmssApiVersion": "2017-03-30",
|
||||
"lbApiVersion": "2015-06-15",
|
||||
"vNetApiVersion": "2015-06-15",
|
||||
"storageApiVersion": "2016-01-01",
|
||||
"publicIPApiVersion": "2015-06-15",
|
||||
"vnetID": "[resourceId('Microsoft.Network/virtualNetworks',parameters('virtualNetworkName'))]",
|
||||
"subnet0Ref": "[concat(variables('vnetID'),'/subnets/',parameters('subnet0Name'))]",
|
||||
"lbID0": "[resourceId('Microsoft.Network/loadBalancers', concat('LB','-', parameters('clusterName'),'-',parameters('vmNodeType0Name')))]",
|
||||
"lbIPConfig0": "[concat(variables('lbID0'),'/frontendIPConfigurations/LoadBalancerIPConfig')]",
|
||||
"lbPoolID0": "[concat(variables('lbID0'),'/backendAddressPools/LoadBalancerBEAddressPool')]",
|
||||
"lbProbeID0": "[concat(variables('lbID0'),'/probes/FabricGatewayProbe')]",
|
||||
"lbHttpProbeID0": "[concat(variables('lbID0'),'/probes/FabricHttpGatewayProbe')]",
|
||||
"lbNatPoolID0": "[concat(variables('lbID0'),'/inboundNatPools/LoadBalancerBEAddressNatPool')]",
|
||||
"vmStorageAccountName0": "[toLower(concat(uniqueString(resourceGroup().id), '1', '0' ))]",
|
||||
"uniqueStringArray0": [
|
||||
"[concat(variables('vmStorageAccountName0'), '0')]",
|
||||
"[concat(variables('vmStorageAccountName0'), '1')]",
|
||||
"[concat(variables('vmStorageAccountName0'), '2')]",
|
||||
"[concat(variables('vmStorageAccountName0'), '3')]",
|
||||
"[concat(variables('vmStorageAccountName0'), '4')]"
|
||||
]
|
||||
},
|
||||
"resources": [
|
||||
{
|
||||
"apiVersion": "[variables('storageApiVersion')]",
|
||||
"type": "Microsoft.Storage/storageAccounts",
|
||||
"name": "[parameters('supportLogStorageAccountName')]",
|
||||
"location": "[parameters('computeLocation')]",
|
||||
"dependsOn": [],
|
||||
"properties": {},
|
||||
"kind": "Storage",
|
||||
"sku": {
|
||||
"name": "[parameters('supportLogStorageAccountType')]"
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[parameters('clusterName')]"
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "[variables('storageApiVersion')]",
|
||||
"type": "Microsoft.Storage/storageAccounts",
|
||||
"name": "[parameters('applicationDiagnosticsStorageAccountName')]",
|
||||
"location": "[parameters('computeLocation')]",
|
||||
"dependsOn": [],
|
||||
"properties": {},
|
||||
"kind": "Storage",
|
||||
"sku": {
|
||||
"name": "[parameters('applicationDiagnosticsStorageAccountType')]"
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[parameters('clusterName')]"
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "[variables('vNetApiVersion')]",
|
||||
"type": "Microsoft.Network/virtualNetworks",
|
||||
"name": "[parameters('virtualNetworkName')]",
|
||||
"location": "[parameters('computeLocation')]",
|
||||
"dependsOn": [],
|
||||
"properties": {
|
||||
"addressSpace": {
|
||||
"addressPrefixes": [
|
||||
"[parameters('addressPrefix')]"
|
||||
]
|
||||
},
|
||||
"subnets": [
|
||||
{
|
||||
"name": "[parameters('subnet0Name')]",
|
||||
"properties": {
|
||||
"addressPrefix": "[parameters('subnet0Prefix')]"
|
||||
}
|
||||
}
|
||||
]
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[parameters('clusterName')]"
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "[variables('publicIPApiVersion')]",
|
||||
"type": "Microsoft.Network/publicIPAddresses",
|
||||
"name": "[concat(parameters('lbIPName'),'-','0')]",
|
||||
"location": "[parameters('computeLocation')]",
|
||||
"properties": {
|
||||
"dnsSettings": {
|
||||
"domainNameLabel": "[parameters('dnsName')]"
|
||||
},
|
||||
"publicIPAllocationMethod": "Dynamic"
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[parameters('clusterName')]"
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "[variables('lbApiVersion')]",
|
||||
"type": "Microsoft.Network/loadBalancers",
|
||||
"name": "[concat('LB','-', parameters('clusterName'),'-',parameters('vmNodeType0Name'))]",
|
||||
"location": "[parameters('computeLocation')]",
|
||||
"dependsOn": [
|
||||
"[concat('Microsoft.Network/publicIPAddresses/',concat(parameters('lbIPName'),'-','0'))]"
|
||||
],
|
||||
"properties": {
|
||||
"frontendIPConfigurations": [
|
||||
{
|
||||
"name": "LoadBalancerIPConfig",
|
||||
"properties": {
|
||||
"publicIPAddress": {
|
||||
"id": "[resourceId('Microsoft.Network/publicIPAddresses',concat(parameters('lbIPName'),'-','0'))]"
|
||||
}
|
||||
}
|
||||
}
|
||||
],
|
||||
"backendAddressPools": [
|
||||
{
|
||||
"name": "LoadBalancerBEAddressPool",
|
||||
"properties": {}
|
||||
}
|
||||
],
|
||||
"loadBalancingRules": [
|
||||
{
|
||||
"name": "LBRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('nt0fabricTcpGatewayPort')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('nt0fabricTcpGatewayPort')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"probe": {
|
||||
"id": "[variables('lbProbeID0')]"
|
||||
},
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "LBHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('nt0fabricHttpGatewayPort')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('nt0fabricHttpGatewayPort')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"probe": {
|
||||
"id": "[variables('lbHttpProbeID0')]"
|
||||
},
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "ReverseProxyHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('nt0reverseProxyEndpointPort')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('nt0reverseProxyEndpointPort')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"probe": {
|
||||
"id": "[variables('lbHttpProbeID0')]"
|
||||
},
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "WebMVCHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('webMvcHttpPort')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('webMvcHttpPort')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"probe": {
|
||||
"id": "[variables('lbHttpProbeID0')]"
|
||||
},
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "WebSPAHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('webSpaHttpPort')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('webSpaHttpPort')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"probe": {
|
||||
"id": "[variables('lbHttpProbeID0')]"
|
||||
},
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "WebStatusHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('webStatusHttpPort')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('webStatusHttpPort')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"probe": {
|
||||
"id": "[variables('lbHttpProbeID0')]"
|
||||
},
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "IdSrvHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('IdSrvHttpRule')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('IdSrvHttpRule')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"probe": {
|
||||
"id": "[variables('lbHttpProbeID0')]"
|
||||
},
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "BasketApiHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('BasketApiHttpRule')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('BasketApiHttpRule')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "CatalogApiHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('CatalogApiHttpRule')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('CatalogApiHttpRule')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "OrderingApiHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('OrderingApiHttpRule')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('OrderingApiHttpRule')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "MarketingApiHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('MarketingApiHttpRule')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('MarketingApiHttpRule')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "LocationsApiHttpRule",
|
||||
"properties": {
|
||||
"backendAddressPool": {
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
},
|
||||
"backendPort": "[parameters('LocationsApiHttpRule')]",
|
||||
"enableFloatingIP": "false",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPort": "[parameters('LocationsApiHttpRule')]",
|
||||
"idleTimeoutInMinutes": "5",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
}
|
||||
],
|
||||
"probes": [
|
||||
{
|
||||
"name": "FabricGatewayProbe",
|
||||
"properties": {
|
||||
"intervalInSeconds": 5,
|
||||
"numberOfProbes": 2,
|
||||
"port": "[parameters('nt0fabricTcpGatewayPort')]",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "FabricHttpGatewayProbe",
|
||||
"properties": {
|
||||
"intervalInSeconds": 5,
|
||||
"numberOfProbes": 2,
|
||||
"port": "[parameters('nt0fabricHttpGatewayPort')]",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
}
|
||||
],
|
||||
"inboundNatPools": [
|
||||
{
|
||||
"name": "LoadBalancerBEAddressNatPool",
|
||||
"properties": {
|
||||
"backendPort": "3389",
|
||||
"frontendIPConfiguration": {
|
||||
"id": "[variables('lbIPConfig0')]"
|
||||
},
|
||||
"frontendPortRangeEnd": "4500",
|
||||
"frontendPortRangeStart": "3389",
|
||||
"protocol": "tcp"
|
||||
}
|
||||
}
|
||||
]
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[parameters('clusterName')]"
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "[variables('storageApiVersion')]",
|
||||
"type": "Microsoft.Storage/storageAccounts",
|
||||
"name": "[variables('uniqueStringArray0')[copyIndex()]]",
|
||||
"location": "[parameters('computeLocation')]",
|
||||
"dependsOn": [],
|
||||
"properties": {},
|
||||
"copy": {
|
||||
"name": "storageLoop",
|
||||
"count": 5
|
||||
},
|
||||
"kind": "Storage",
|
||||
"sku": {
|
||||
"name": "[parameters('storageAccountType')]"
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[parameters('clusterName')]"
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "[variables('vmssApiVersion')]",
|
||||
"type": "Microsoft.Compute/virtualMachineScaleSets",
|
||||
"name": "[parameters('vmNodeType0Name')]",
|
||||
"location": "[parameters('computeLocation')]",
|
||||
"dependsOn": [
|
||||
"[concat('Microsoft.Network/virtualNetworks/', parameters('virtualNetworkName'))]",
|
||||
"[concat('Microsoft.Storage/storageAccounts/', variables('uniqueStringArray0')[0])]",
|
||||
"[concat('Microsoft.Storage/storageAccounts/', variables('uniqueStringArray0')[1])]",
|
||||
"[concat('Microsoft.Storage/storageAccounts/', variables('uniqueStringArray0')[2])]",
|
||||
"[concat('Microsoft.Storage/storageAccounts/', variables('uniqueStringArray0')[3])]",
|
||||
"[concat('Microsoft.Storage/storageAccounts/', variables('uniqueStringArray0')[4])]",
|
||||
"[concat('Microsoft.Network/loadBalancers/', concat('LB','-', parameters('clusterName'),'-',parameters('vmNodeType0Name')))]",
|
||||
"[concat('Microsoft.Storage/storageAccounts/', parameters('supportLogStorageAccountName'))]",
|
||||
"[concat('Microsoft.Storage/storageAccounts/', parameters('applicationDiagnosticsStorageAccountName'))]"
|
||||
],
|
||||
"properties": {
|
||||
"overprovision": "[parameters('overProvision')]",
|
||||
"upgradePolicy": {
|
||||
"mode": "Automatic"
|
||||
},
|
||||
"virtualMachineProfile": {
|
||||
"extensionProfile": {
|
||||
"extensions": [
|
||||
{
|
||||
"name": "[concat(parameters('vmNodeType0Name'),'_ServiceFabricNode')]",
|
||||
"properties": {
|
||||
"type": "ServiceFabricNode",
|
||||
"autoUpgradeMinorVersion": true,
|
||||
"protectedSettings": {
|
||||
"StorageAccountKey1": "[listKeys(resourceId('Microsoft.Storage/storageAccounts', parameters('supportLogStorageAccountName')),'2015-05-01-preview').key1]",
|
||||
"StorageAccountKey2": "[listKeys(resourceId('Microsoft.Storage/storageAccounts', parameters('supportLogStorageAccountName')),'2015-05-01-preview').key2]"
|
||||
},
|
||||
"publisher": "Microsoft.Azure.ServiceFabric",
|
||||
"settings": {
|
||||
"clusterEndpoint": "[reference(parameters('clusterName')).clusterEndpoint]",
|
||||
"nodeTypeRef": "[parameters('vmNodeType0Name')]",
|
||||
"dataPath": "D:\\\\SvcFab",
|
||||
"durabilityLevel": "Bronze",
|
||||
"enableParallelJobs": true,
|
||||
"nicPrefixOverride": "[parameters('subnet0Prefix')]",
|
||||
"certificate": {
|
||||
"thumbprint": "[parameters('certificateThumbprint')]",
|
||||
"x509StoreName": "[parameters('certificateStoreValue')]"
|
||||
}
|
||||
},
|
||||
"typeHandlerVersion": "1.0"
|
||||
}
|
||||
},
|
||||
{
|
||||
"name": "[concat('VMDiagnosticsVmExt','_vmNodeType0Name')]",
|
||||
"properties": {
|
||||
"type": "IaaSDiagnostics",
|
||||
"autoUpgradeMinorVersion": true,
|
||||
"protectedSettings": {
|
||||
"storageAccountName": "[parameters('applicationDiagnosticsStorageAccountName')]",
|
||||
"storageAccountKey": "[listKeys(resourceId('Microsoft.Storage/storageAccounts', parameters('applicationDiagnosticsStorageAccountName')),'2015-05-01-preview').key1]",
|
||||
"storageAccountEndPoint": "https://core.windows.net/"
|
||||
},
|
||||
"publisher": "Microsoft.Azure.Diagnostics",
|
||||
"settings": {
|
||||
"WadCfg": {
|
||||
"DiagnosticMonitorConfiguration": {
|
||||
"overallQuotaInMB": "50000",
|
||||
"EtwProviders": {
|
||||
"EtwEventSourceProviderConfiguration": [
|
||||
{
|
||||
"provider": "Microsoft-ServiceFabric-Actors",
|
||||
"scheduledTransferKeywordFilter": "1",
|
||||
"scheduledTransferPeriod": "PT5M",
|
||||
"DefaultEvents": {
|
||||
"eventDestination": "ServiceFabricReliableActorEventTable"
|
||||
}
|
||||
},
|
||||
{
|
||||
"provider": "Microsoft-ServiceFabric-Services",
|
||||
"scheduledTransferPeriod": "PT5M",
|
||||
"DefaultEvents": {
|
||||
"eventDestination": "ServiceFabricReliableServiceEventTable"
|
||||
}
|
||||
}
|
||||
],
|
||||
"EtwManifestProviderConfiguration": [
|
||||
{
|
||||
"provider": "cbd93bc2-71e5-4566-b3a7-595d8eeca6e8",
|
||||
"scheduledTransferLogLevelFilter": "Information",
|
||||
"scheduledTransferKeywordFilter": "4611686018427387904",
|
||||
"scheduledTransferPeriod": "PT5M",
|
||||
"DefaultEvents": {
|
||||
"eventDestination": "ServiceFabricSystemEventTable"
|
||||
}
|
||||
}
|
||||
]
|
||||
}
|
||||
}
|
||||
},
|
||||
"StorageAccount": "[parameters('applicationDiagnosticsStorageAccountName')]"
|
||||
},
|
||||
"typeHandlerVersion": "1.5"
|
||||
}
|
||||
}
|
||||
]
|
||||
},
|
||||
"networkProfile": {
|
||||
"networkInterfaceConfigurations": [
|
||||
{
|
||||
"name": "[concat(parameters('nicName'), '-0')]",
|
||||
"properties": {
|
||||
"ipConfigurations": [
|
||||
{
|
||||
"name": "[concat(parameters('nicName'),'-',0)]",
|
||||
"properties": {
|
||||
"loadBalancerBackendAddressPools": [
|
||||
{
|
||||
"id": "[variables('lbPoolID0')]"
|
||||
}
|
||||
],
|
||||
"loadBalancerInboundNatPools": [
|
||||
{
|
||||
"id": "[variables('lbNatPoolID0')]"
|
||||
}
|
||||
],
|
||||
"subnet": {
|
||||
"id": "[variables('subnet0Ref')]"
|
||||
}
|
||||
}
|
||||
}
|
||||
],
|
||||
"primary": true
|
||||
}
|
||||
}
|
||||
]
|
||||
},
|
||||
"osProfile": {
|
||||
"adminPassword": "[parameters('adminPassword')]",
|
||||
"adminUsername": "[parameters('adminUsername')]",
|
||||
"computernamePrefix": "[parameters('vmNodeType0Name')]",
|
||||
"secrets": [
|
||||
{
|
||||
"sourceVault": {
|
||||
"id": "[parameters('sourceVaultValue')]"
|
||||
},
|
||||
"vaultCertificates": [
|
||||
{
|
||||
"certificateStore": "[parameters('certificateStoreValue')]",
|
||||
"certificateUrl": "[parameters('certificateUrlValue')]"
|
||||
}
|
||||
]
|
||||
}
|
||||
]
|
||||
},
|
||||
"storageProfile": {
|
||||
"imageReference": {
|
||||
"publisher": "[parameters('vmImagePublisher')]",
|
||||
"offer": "[parameters('vmImageOffer')]",
|
||||
"sku": "[parameters('vmImageSku')]",
|
||||
"version": "[parameters('vmImageVersion')]"
|
||||
},
|
||||
"osDisk": {
|
||||
"caching": "ReadOnly",
|
||||
"createOption": "FromImage",
|
||||
"vhdContainers": [
|
||||
"[concat(reference(concat('Microsoft.Storage/storageAccounts/', variables('uniqueStringArray0')[0]), variables('storageApiVersion')).primaryEndpoints.blob, parameters('vmStorageAccountContainerName'))]",
|
||||
"[concat(reference(concat('Microsoft.Storage/storageAccounts/', variables('uniqueStringArray0')[1]), variables('storageApiVersion')).primaryEndpoints.blob, parameters('vmStorageAccountContainerName'))]",
|
||||
"[concat(reference(concat('Microsoft.Storage/storageAccounts/', variables('uniqueStringArray0')[2]), variables('storageApiVersion')).primaryEndpoints.blob, parameters('vmStorageAccountContainerName'))]",
|
||||
"[concat(reference(concat('Microsoft.Storage/storageAccounts/', variables('uniqueStringArray0')[3]), variables('storageApiVersion')).primaryEndpoints.blob, parameters('vmStorageAccountContainerName'))]",
|
||||
"[concat(reference(concat('Microsoft.Storage/storageAccounts/', variables('uniqueStringArray0')[4]), variables('storageApiVersion')).primaryEndpoints.blob, parameters('vmStorageAccountContainerName'))]"
|
||||
],
|
||||
"name": "vmssosdisk"
|
||||
}
|
||||
}
|
||||
}
|
||||
},
|
||||
"sku": {
|
||||
"name": "[parameters('vmNodeType0Size')]",
|
||||
"capacity": "[parameters('nt0InstanceCount')]",
|
||||
"tier": "Standard"
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[parameters('clusterName')]"
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "2017-07-01-preview",
|
||||
"type": "Microsoft.ServiceFabric/clusters",
|
||||
"name": "[parameters('clusterName')]",
|
||||
"location": "[parameters('clusterLocation')]",
|
||||
"dependsOn": [
|
||||
"[concat('Microsoft.Storage/storageAccounts/', parameters('supportLogStorageAccountName'))]"
|
||||
],
|
||||
"properties": {
|
||||
"addonFeatures": [
|
||||
"DnsService"
|
||||
],
|
||||
"certificate": {
|
||||
"thumbprint": "[parameters('certificateThumbprint')]",
|
||||
"x509StoreName": "[parameters('certificateStoreValue')]"
|
||||
},
|
||||
"clientCertificateCommonNames": [],
|
||||
"clientCertificateThumbprints": [],
|
||||
"clusterCodeVersion": "5.7.207.9494",
|
||||
"clusterState": "Default",
|
||||
"diagnosticsStorageAccountConfig": {
|
||||
"blobEndpoint": "[reference(concat('Microsoft.Storage/storageAccounts/', parameters('supportLogStorageAccountName')), variables('storageApiVersion')).primaryEndpoints.blob]",
|
||||
"protectedAccountKeyName": "StorageAccountKey1",
|
||||
"queueEndpoint": "[reference(concat('Microsoft.Storage/storageAccounts/', parameters('supportLogStorageAccountName')), variables('storageApiVersion')).primaryEndpoints.queue]",
|
||||
"storageAccountName": "[parameters('supportLogStorageAccountName')]",
|
||||
"tableEndpoint": "[reference(concat('Microsoft.Storage/storageAccounts/', parameters('supportLogStorageAccountName')), variables('storageApiVersion')).primaryEndpoints.table]"
|
||||
},
|
||||
"fabricSettings": [
|
||||
{
|
||||
"parameters": [
|
||||
{
|
||||
"name": "ClusterProtectionLevel",
|
||||
"value": "[parameters('clusterProtectionLevel')]"
|
||||
}
|
||||
],
|
||||
"name": "Security"
|
||||
}
|
||||
],
|
||||
"managementEndpoint": "[concat('https://',reference(concat(parameters('lbIPName'),'-','0')).dnsSettings.fqdn,':',parameters('nt0fabricHttpGatewayPort'))]",
|
||||
"nodeTypes": [
|
||||
{
|
||||
"name": "[parameters('vmNodeType0Name')]",
|
||||
"applicationPorts": {
|
||||
"endPort": "[parameters('nt0applicationEndPort')]",
|
||||
"startPort": "[parameters('nt0applicationStartPort')]"
|
||||
},
|
||||
"clientConnectionEndpointPort": "[parameters('nt0fabricTcpGatewayPort')]",
|
||||
"durabilityLevel": "Bronze",
|
||||
"ephemeralPorts": {
|
||||
"endPort": "[parameters('nt0ephemeralEndPort')]",
|
||||
"startPort": "[parameters('nt0ephemeralStartPort')]"
|
||||
},
|
||||
"httpGatewayEndpointPort": "[parameters('nt0fabricHttpGatewayPort')]",
|
||||
"isPrimary": true,
|
||||
"reverseProxyEndpointPort": "[parameters('nt0reverseProxyEndpointPort')]",
|
||||
"vmInstanceCount": "[parameters('nt0InstanceCount')]"
|
||||
}
|
||||
],
|
||||
"provisioningState": "Default",
|
||||
"reliabilityLevel": "Silver",
|
||||
"upgradeMode": "Manual",
|
||||
"vmImage": "Windows"
|
||||
},
|
||||
"tags": {
|
||||
"resourceType": "Service Fabric",
|
||||
"clusterName": "[parameters('clusterName')]"
|
||||
}
|
||||
}
|
||||
],
|
||||
"outputs": {
|
||||
"clusterProperties": {
|
||||
"value": "[reference(parameters('clusterName'))]",
|
||||
"type": "object"
|
||||
}
|
||||
}
|
||||
}
|
||||
@ -1,106 +0,0 @@
|
||||
{
|
||||
"$schema": "https://schema.management.azure.com/schemas/2015-01-01/deploymentParameters.json#",
|
||||
"contentVersion": "1.0.0.0",
|
||||
"parameters": {
|
||||
"clusterName": {
|
||||
"value": "pro-eshop-sfwin-cluster"
|
||||
},
|
||||
"clusterLocation": {
|
||||
"value": "westus"
|
||||
},
|
||||
"computeLocation": {
|
||||
"value": "westus"
|
||||
},
|
||||
"adminUserName": {
|
||||
"value": "eshop"
|
||||
},
|
||||
"adminPassword": {
|
||||
"value": "Your_complex_Pass@word1"
|
||||
},
|
||||
"nicName": {
|
||||
"value": "NIC-eshopsfwin"
|
||||
},
|
||||
"publicIPAddressName": {
|
||||
"value": "eshopsfwin-PubIP"
|
||||
},
|
||||
"dnsName": {
|
||||
"value": "pro-eshop-sfwin-cluster"
|
||||
},
|
||||
"virtualNetworkName": {
|
||||
"value": "VNet-eshopsfwin"
|
||||
},
|
||||
"lbName": {
|
||||
"value": "LB-eshopsfwin"
|
||||
},
|
||||
"lbIPName": {
|
||||
"value": "LBIP-eshopsfwin"
|
||||
},
|
||||
"applicationDiagnosticsStorageAccountName": {
|
||||
"value": "sfdgqaeshopsfwinsec"
|
||||
},
|
||||
"supportLogStorageAccountName": {
|
||||
"value": "sflogsqaeshopsfwinsec"
|
||||
},
|
||||
"sourceVaultValue": {
|
||||
"value": "your-value-check-keyvault-at-azure"
|
||||
},
|
||||
"certificateUrlValue": {
|
||||
"value": "your-value-check-keyvault-at-azure"
|
||||
},
|
||||
"certificateThumbprint": {
|
||||
"value": "your-value-check-keyvault-at-azure"
|
||||
},
|
||||
"vmImageSku": {
|
||||
"value": "2016-Datacenter-with-Containers"
|
||||
},
|
||||
"nt0ephemeralStartPort": {
|
||||
"value": 49152
|
||||
},
|
||||
"nt0ephemeralEndPort": {
|
||||
"value": 65534
|
||||
},
|
||||
"nt0applicationStartPort": {
|
||||
"value": 20000
|
||||
},
|
||||
"nt0applicationEndPort": {
|
||||
"value": 30000
|
||||
},
|
||||
"nt0fabricTcpGatewayPort": {
|
||||
"value": 19000
|
||||
},
|
||||
"nt0fabricHttpGatewayPort": {
|
||||
"value": 19080
|
||||
},
|
||||
"nt0reverseProxyEndpointPort": {
|
||||
"value": 19081
|
||||
},
|
||||
"webMvcHttpPort": {
|
||||
"value": 5100
|
||||
},
|
||||
"webSpaHttpPort": {
|
||||
"value": 5104
|
||||
},
|
||||
"webStatusHttpPort": {
|
||||
"value": 5107
|
||||
},
|
||||
"IdSrvHttpRule": {
|
||||
"value": 5105
|
||||
},
|
||||
"BasketApiHttpRule": {
|
||||
"value": 5103
|
||||
},
|
||||
"CatalogApiHttpRule": {
|
||||
"value": 5101
|
||||
},
|
||||
"OrderingApiHttpRule": {
|
||||
"value": 5102
|
||||
},
|
||||
"MarketingApiHttpRule": {
|
||||
"value": 5110
|
||||
},
|
||||
"LocationsApiHttpRule": {
|
||||
"value": 5109
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
@ -1,48 +0,0 @@
|
||||
# Create a VM using docker-machine
|
||||
|
||||
Ensure you are logged in the desired subscription Refer to [this article](https://docs.microsoft.com/en-us/cli/azure/authenticate-azure-cli) for more details.
|
||||
|
||||
1. Use `az account show` to find your subscription id.
|
||||
2. Use `docker-machine create --driver azure --azure-subscription-id <subs_id> --azure-resource-group <resource_group> --azure-ssh-user <login_name> <machine_name>`
|
||||
|
||||
After use `docker-machine create` you'll need to authenticate in Azure (even thought if you are logged using `az`, because this is not an Azure CLI 2.0 command). This command will fully create the VM with all the needed settings to run Docker.
|
||||
|
||||
**Note** Refer to this article with all the [parameters that docker-machine accepts when creating Azure VMs](https://docs.docker.com/machine/drivers/azure/#options) for finding more parameters.
|
||||
|
||||
## Connecting your local environment with docker host running on the VM
|
||||
|
||||
Using docker-machine you control the remote VM from your local development environment (you don't need to use ssh to login to remote VM).
|
||||
|
||||
Connecting your local environment to a remote host is using by setting some environment variables, but the easiest way is to use again the docker-machine command. Just type `docker-machine env machine_name` (where machine_name is the name you gave when you created the VM). That command **do not change anything**, so do'nt do really nothing, but **outputs the environment variables you have to set**. This is the output of the command (running on a windows workstation):
|
||||
|
||||
```
|
||||
SET DOCKER_TLS_VERIFY=1
|
||||
SET DOCKER_HOST=tcp://104.42.236.237:2376
|
||||
SET DOCKER_CERT_PATH=C:\Users\etoma\.docker\machine\machines\ufohost
|
||||
SET DOCKER_MACHINE_NAME=ufohost
|
||||
SET COMPOSE_CONVERT_WINDOWS_PATHS=true
|
||||
REM Run this command to configure your shell:
|
||||
REM @FOR /f "tokens=*" %i IN ('docker-machine env ufohost') DO @%i
|
||||
```
|
||||
|
||||
You have to set all these environment variables, or (as the command suggest) just copy and paste the last line in your terminal.
|
||||
|
||||
Once you did this, your local development machine is connected to VM running Docker on Azure: all docker and docker-compose commands will run in the VM instead of your local Docker machine!
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
@ -1,199 +0,0 @@
|
||||
{
|
||||
"$schema": "https://schema.management.azure.com/schemas/2015-01-01/deploymentTemplate.json#",
|
||||
"contentVersion": "1.0.0.0",
|
||||
"parameters": {
|
||||
"newStorageAccountName": {
|
||||
"type": "string",
|
||||
"metadata": {
|
||||
"description": "Unique DNS Name for the Storage Account where the Virtual Machine's disks will be placed."
|
||||
}
|
||||
},
|
||||
"adminUsername": {
|
||||
"type": "string",
|
||||
"metadata": {
|
||||
"description": "Username for the Virtual Machine."
|
||||
}
|
||||
},
|
||||
"adminPassword": {
|
||||
"type": "securestring",
|
||||
"metadata": {
|
||||
"description": "Password for the Virtual Machine."
|
||||
}
|
||||
},
|
||||
"dnsNameForPublicIP": {
|
||||
"type": "string",
|
||||
"metadata": {
|
||||
"description": "Unique DNS Name for the Public IP used to access the Virtual Machine."
|
||||
}
|
||||
},
|
||||
"ubuntuOSVersion": {
|
||||
"type": "string",
|
||||
"defaultValue": "14.04.4-LTS",
|
||||
"metadata": {
|
||||
"description": "The Ubuntu version for deploying the Docker containers. This will pick a fully patched image of this given Ubuntu version. Allowed values: 14.04.4-LTS, 15.10, 16.04.0-LTS"
|
||||
},
|
||||
"allowedValues": [
|
||||
"14.04.4-LTS",
|
||||
"15.10",
|
||||
"16.04.0-LTS"
|
||||
]
|
||||
},
|
||||
"VMName": {
|
||||
"type": "string",
|
||||
"metadata": {
|
||||
"description": "Name of VM in Azure"
|
||||
}
|
||||
}
|
||||
},
|
||||
"variables": {
|
||||
"newStorageAccountName": "[take(concat(parameters('newStorageAccountName'), uniqueString(resourceGroup().id)), 23)]",
|
||||
"dnsNameForPublicIP": "[concat(parameters('dnsNameForPublicIP'), uniqueString(resourceGroup().id))]",
|
||||
"imagePublisher": "Canonical",
|
||||
"imageOffer": "UbuntuServer",
|
||||
"OSDiskName": "osdiskfordockersimple",
|
||||
"nicName": "myVMNicD",
|
||||
"extensionName": "DockerExtension",
|
||||
"addressPrefix": "10.0.0.0/16",
|
||||
"subnetName": "Subnet",
|
||||
"subnetPrefix": "10.0.0.0/24",
|
||||
"storageAccountType": "Standard_LRS",
|
||||
"publicIPAddressName": "myPublicIPD",
|
||||
"publicIPAddressType": "Dynamic",
|
||||
"vmStorageAccountContainerName": "vhds",
|
||||
"vmName": "[parameters('VMName')]",
|
||||
"vmSize": "Standard_F1",
|
||||
"virtualNetworkName": "MyVNETD",
|
||||
"vnetID": "[resourceId('Microsoft.Network/virtualNetworks',variables('virtualNetworkName'))]",
|
||||
"subnetRef": "[concat(variables('vnetID'),'/subnets/',variables('subnetName'))]"
|
||||
},
|
||||
"resources": [
|
||||
{
|
||||
"type": "Microsoft.Storage/storageAccounts",
|
||||
"name": "[variables('newStorageAccountName')]",
|
||||
"apiVersion": "2015-05-01-preview",
|
||||
"location": "[resourceGroup().location]",
|
||||
"properties": {
|
||||
"accountType": "[variables('storageAccountType')]"
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "2015-05-01-preview",
|
||||
"type": "Microsoft.Network/publicIPAddresses",
|
||||
"name": "[variables('publicIPAddressName')]",
|
||||
"location": "[resourceGroup().location]",
|
||||
"properties": {
|
||||
"publicIPAllocationMethod": "[variables('publicIPAddressType')]",
|
||||
"dnsSettings": {
|
||||
"domainNameLabel": "[variables('dnsNameForPublicIP')]"
|
||||
}
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "2015-05-01-preview",
|
||||
"type": "Microsoft.Network/virtualNetworks",
|
||||
"name": "[variables('virtualNetworkName')]",
|
||||
"location": "[resourceGroup().location]",
|
||||
"properties": {
|
||||
"addressSpace": {
|
||||
"addressPrefixes": [
|
||||
"[variables('addressPrefix')]"
|
||||
]
|
||||
},
|
||||
"subnets": [
|
||||
{
|
||||
"name": "[variables('subnetName')]",
|
||||
"properties": {
|
||||
"addressPrefix": "[variables('subnetPrefix')]"
|
||||
}
|
||||
}
|
||||
]
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "2015-05-01-preview",
|
||||
"type": "Microsoft.Network/networkInterfaces",
|
||||
"name": "[variables('nicName')]",
|
||||
"location": "[resourceGroup().location]",
|
||||
"dependsOn": [
|
||||
"[concat('Microsoft.Network/publicIPAddresses/', variables('publicIPAddressName'))]",
|
||||
"[concat('Microsoft.Network/virtualNetworks/', variables('virtualNetworkName'))]"
|
||||
],
|
||||
"properties": {
|
||||
"ipConfigurations": [
|
||||
{
|
||||
"name": "ipconfig1",
|
||||
"properties": {
|
||||
"privateIPAllocationMethod": "Dynamic",
|
||||
"publicIPAddress": {
|
||||
"id": "[resourceId('Microsoft.Network/publicIPAddresses',variables('publicIPAddressName'))]"
|
||||
},
|
||||
"subnet": {
|
||||
"id": "[variables('subnetRef')]"
|
||||
}
|
||||
}
|
||||
}
|
||||
]
|
||||
}
|
||||
},
|
||||
{
|
||||
"apiVersion": "2015-05-01-preview",
|
||||
"type": "Microsoft.Compute/virtualMachines",
|
||||
"name": "[variables('vmName')]",
|
||||
"location": "[resourceGroup().location]",
|
||||
"dependsOn": [
|
||||
"[concat('Microsoft.Storage/storageAccounts/', variables('newStorageAccountName'))]",
|
||||
"[concat('Microsoft.Network/networkInterfaces/', variables('nicName'))]"
|
||||
],
|
||||
"properties": {
|
||||
"hardwareProfile": {
|
||||
"vmSize": "[variables('vmSize')]"
|
||||
},
|
||||
"osProfile": {
|
||||
"computerName": "[variables('vmName')]",
|
||||
"adminUsername": "[parameters('adminUsername')]",
|
||||
"adminPassword": "[parameters('adminPassword')]"
|
||||
},
|
||||
"storageProfile": {
|
||||
"imageReference": {
|
||||
"publisher": "[variables('imagePublisher')]",
|
||||
"offer": "[variables('imageOffer')]",
|
||||
"sku": "[parameters('ubuntuOSVersion')]",
|
||||
"version": "latest"
|
||||
},
|
||||
"osDisk": {
|
||||
"name": "osdisk1",
|
||||
"vhd": {
|
||||
"uri": "[concat('http://',variables('newStorageAccountName'),'.blob.core.windows.net/',variables('vmStorageAccountContainerName'),'/',variables('OSDiskName'),'.vhd')]"
|
||||
},
|
||||
"caching": "ReadWrite",
|
||||
"createOption": "FromImage"
|
||||
}
|
||||
},
|
||||
"networkProfile": {
|
||||
"networkInterfaces": [
|
||||
{
|
||||
"id": "[resourceId('Microsoft.Network/networkInterfaces',variables('nicName'))]"
|
||||
}
|
||||
]
|
||||
}
|
||||
}
|
||||
},
|
||||
{
|
||||
"type": "Microsoft.Compute/virtualMachines/extensions",
|
||||
"name": "[concat(variables('vmName'),'/', variables('extensionName'))]",
|
||||
"apiVersion": "2015-05-01-preview",
|
||||
"location": "[resourceGroup().location]",
|
||||
"dependsOn": [
|
||||
"[concat('Microsoft.Compute/virtualMachines/', variables('vmName'))]"
|
||||
],
|
||||
"properties": {
|
||||
"publisher": "Microsoft.Azure.Extensions",
|
||||
"type": "DockerExtension",
|
||||
"typeHandlerVersion": "1.0",
|
||||
"autoUpgradeMinorVersion": true,
|
||||
"settings": { }
|
||||
}
|
||||
}
|
||||
]
|
||||
}
|
||||
|
||||
@ -1,7 +0,0 @@
|
||||
{
|
||||
"newStorageAccountName": { "value": "eshopsrvmvstorage" },
|
||||
"adminUsername": { "value": "eshop" },
|
||||
"adminPassword": { "value": "Pass@word" },
|
||||
"dnsNameForPublicIP": { "value": "eshop-srv" },
|
||||
"VMName": {"value": "MyDockerVM2"}
|
||||
}
|
||||
@ -1,77 +0,0 @@
|
||||
# Deploy a VM to run the services
|
||||
|
||||
Follow these instructions to deploy a Linux-based VM with the Docker Host installed, or a VM with Windows Server 2016 plus
|
||||
windows containers and Docker Daemon.
|
||||
|
||||
**Note**: Use this option, only if you want to provide an environment using images pulled from DockerHub (for example, to create a test environment). If you want to
|
||||
be able to deploy images built by yourself (but not pushed to DockerHub) follow the [instructions about using docker-machine](./docker-machine.md).
|
||||
|
||||
You can use this machine to install the microservices and having a "development" environment (useful to develop and test the client apps).
|
||||
|
||||
Please note that this deployment is not a production deployment. In a production-based scenario, you should deploy all containers in ACS.
|
||||
|
||||
## Create the VM
|
||||
|
||||
Ensure you are logged in the desired subscription (use `az login` and `az account set` if needed. Refer to [this article](https://docs.microsoft.com/en-us/cli/azure/authenticate-azure-cli) for more details.
|
||||
|
||||
Go to `linux-vm` or `win-vm` folder (based on if you want a Linux or Windows VM). Then:
|
||||
|
||||
1. Edit the file `linuxvm.parameters.json` or `windowsvm.parameters.json` (based on what VM do you want to create) with your desired values
|
||||
2. Run the [create-resources script](../readme.md) to deploy the desired template (`linux-vm/linuxvm.json` or `win-vm/windowsvm.json`).
|
||||
|
||||
I. e. if you are in Windows and want to deploy a linux based VM, in a new resourcegroup located in westus, go to `deploy\az` folder and type:
|
||||
|
||||
```
|
||||
create-resources.cmd vms\linux-vm\linuxvm newResourceGroup -c westus
|
||||
```
|
||||
|
||||
**Note:** To avoid errors, ARM template used generates unique names for:
|
||||
|
||||
1. VM used storage
|
||||
2. Public DNS
|
||||
|
||||
Those public names are based on the parameters set in the parameters file.
|
||||
|
||||
### The parameters file (linuxvm.parameters.json or winsowsvm.parameters.json)
|
||||
|
||||
Both files are identical and contains the minimum set of parameters needed by the ARM template to deploy the VM. ARM template accepts some other parameters (set with default values). Look the template for more info.
|
||||
|
||||
The parameters defined are:
|
||||
|
||||
1. `newStorageAccountName`: Name of the storage created for the VM. To ensure uniqueness a unique suffix will be added to this value.
|
||||
2. `adminUsername`: Admin login
|
||||
3. `adminPassword`: Admin password
|
||||
4. `dnsNameForPublicIP`: DNS of the VM. To ensure uniqueness a unique suffix will be added to this value.
|
||||
5. `VMName`: Name of the VM inside Azure
|
||||
|
||||
## Finding the IP and DNS of the VM
|
||||
|
||||
To find the IP and FQDN of the VM you can type `az vm list --resource-group <resourcegroup> --output table --show-details` (where resourcegroup is the
|
||||
name of the resourcegroup where you created the VM). This command will generate output like:
|
||||
|
||||
```
|
||||
Name ResourceGroup PowerState PublicIps Fqdns Location
|
||||
---------- --------------- ------------ ------------- ------------------------------------------------ ----------
|
||||
MyDockerVM MyResourceGroup VM running xx.xx.xxx.xxx eshop-srvxxxxxxxxxxxxx.westus.cloudapp.azure.com westus
|
||||
```
|
||||
|
||||
You can use this information to connect your new VM.
|
||||
|
||||
## Deploy services in the VM
|
||||
|
||||
We are providing public images of the services in DockerHub (https://hub.docker.com/u/eshop/). To use these images, just create a folder in the VM and copy
|
||||
following files to it (those files are in the root of the repo):
|
||||
|
||||
1. `docker-compose.nobuild.yml`
|
||||
2. `docker-compose.prod.yml`
|
||||
|
||||
**Note:** The `docker-compose.nobuild.yml` is just a version of the `docker-compose.yml` without the `build` section. Is neede due [docker-compose bug](https://github.com/docker/compose/issues/2945).
|
||||
|
||||
Then log into the VM and run the command `docker-compose -f docker-compose.nobuild.yml -f docker-compose.prod.yml up --no-build -d` to start all the microservices.
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
@ -1,10 +0,0 @@
|
||||
## Create VM with Docker installed
|
||||
|
||||
There are two options for creating VM machines with Docker installed:
|
||||
|
||||
1. [Deploying a Linux VM to run single-server development environment using docker-machine (**Recommended for development environments**)](./docker-machine.md)
|
||||
2. [Deploying a Linux VM or Windows Server 2016 to run a single-server development environment using ARM template (**Recommended for creating testing environments**)](./plain-vm.md)
|
||||
|
||||
If you want to create a VM for deploying images you build locally, then use the first option.
|
||||
|
||||
If you want to create a VM to run images deployed to DockerHub (to provide some test environment) then use the second option.
|
||||
@ -1,290 +0,0 @@
|
||||
{
|
||||
"$schema": "https://schema.management.azure.com/schemas/2015-01-01/deploymentTemplate.json#",
|
||||
"contentVersion": "1.0.0.0",
|
||||
"parameters": {
|
||||
|
||||
"VMName": {
|
||||
"type": "string",
|
||||
"metadata": {
|
||||
"description": "This name will also be used to prefix the network security group, storage, virtual network, network card, subnet and public IP address name."
|
||||
}
|
||||
},
|
||||
|
||||
"adminUsername": {
|
||||
"type": "string",
|
||||
"metadata": {
|
||||
"description": "Username for the Virtual Machine."
|
||||
}
|
||||
},
|
||||
|
||||
"adminPassword": {
|
||||
"type": "securestring",
|
||||
"metadata": {
|
||||
"description": "Password for the Virtual Machine."
|
||||
}
|
||||
},
|
||||
|
||||
"dnsNameForPublicIP": {
|
||||
"type": "string",
|
||||
"metadata": {
|
||||
"description": "Unique DNS Name for the Public IP used to access the Virtual Machine."
|
||||
}
|
||||
},
|
||||
|
||||
"newStorageAccountName": {
|
||||
"type": "string",
|
||||
"metadata": {
|
||||
"description": "Storage name for the Virtual Machine."
|
||||
}
|
||||
},
|
||||
"vmSize": {
|
||||
"type": "string",
|
||||
"defaultValue": "Standard_D1",
|
||||
"metadata": {
|
||||
"description": "VM Size"
|
||||
}
|
||||
}
|
||||
},
|
||||
|
||||
"variables": {
|
||||
"newStorageAccountName": "[take(concat(parameters('newStorageAccountName'), uniqueString(resourceGroup().id)), 23)]",
|
||||
"dnsNameForPublicIP": "[concat(parameters('dnsNameForPublicIP'), uniqueString(resourceGroup().id))]",
|
||||
"windowsOSVersion": "2016-Datacenter",
|
||||
"imagePublisher": "MicrosoftWindowsServer",
|
||||
"imageOffer": "WindowsServer",
|
||||
"OSDiskName": "[concat(parameters('VMName'),'_osdisk')]",
|
||||
"nicName": "[concat(parameters('VMName'),'_nic')]",
|
||||
"addressPrefix": "10.0.0.0/16",
|
||||
"subnetName": "[concat(parameters('VMName'),'_subnet')]",
|
||||
"subnetPrefix": "10.0.0.0/24",
|
||||
"networkSecurityGroupName": "[concat(parameters('VMName'),'_nsg')]",
|
||||
"storageAccountType": "Standard_LRS",
|
||||
"publicIPAddressName": "[concat(parameters('VMName'),'_pubip')]",
|
||||
"publicIPAddressType": "Dynamic",
|
||||
"vmStorageAccountContainerName": "vhds",
|
||||
"apiVersion": "2015-05-01-preview",
|
||||
"virtualNetworkName": "[concat(parameters('VMName'),'_vnet')]",
|
||||
"vnetID": "[resourceId('Microsoft.Network/virtualNetworks',variables('virtualNetworkName'))]",
|
||||
"subnetRef": "[concat(variables('vnetID'),'/subnets/',variables('subnetName'))]"
|
||||
},
|
||||
"resources": [
|
||||
{
|
||||
"type": "Microsoft.Network/networkSecurityGroups",
|
||||
"name": "[variables('networkSecurityGroupName')]",
|
||||
"apiVersion": "[variables('apiVersion')]",
|
||||
"location": "[resourceGroup().location]",
|
||||
"properties": {
|
||||
"securityRules": [
|
||||
{
|
||||
"name": "HTTP",
|
||||
"properties": {
|
||||
"description": "HTTP",
|
||||
"protocol": "Tcp",
|
||||
"sourcePortRange": "*",
|
||||
"destinationPortRange": "80",
|
||||
"sourceAddressPrefix": "*",
|
||||
"destinationAddressPrefix": "*",
|
||||
"access": "Allow",
|
||||
"priority": 100,
|
||||
"direction": "Inbound"
|
||||
}
|
||||
},
|
||||
|
||||
{
|
||||
"name": "RDP",
|
||||
"properties": {
|
||||
"description": "RDP",
|
||||
"protocol": "Tcp",
|
||||
"sourcePortRange": "*",
|
||||
"destinationPortRange": "3389",
|
||||
"sourceAddressPrefix": "*",
|
||||
"destinationAddressPrefix": "*",
|
||||
"access": "Allow",
|
||||
"priority": 200,
|
||||
"direction": "Inbound"
|
||||
}
|
||||
},
|
||||
|
||||
{
|
||||
"name": "Docker",
|
||||
"properties": {
|
||||
"description": "Docker",
|
||||
"protocol": "Tcp",
|
||||
"sourcePortRange": "*",
|
||||
"destinationPortRange": "2375",
|
||||
"sourceAddressPrefix": "*",
|
||||
"destinationAddressPrefix": "*",
|
||||
"access": "Allow",
|
||||
"priority": 300,
|
||||
"direction": "Inbound"
|
||||
}
|
||||
}
|
||||
|
||||
]
|
||||
}
|
||||
},
|
||||
|
||||
{
|
||||
"type": "Microsoft.Storage/storageAccounts",
|
||||
"name": "[variables('newStorageAccountName')]",
|
||||
"apiVersion": "[variables('apiVersion')]",
|
||||
"location": "[resourceGroup().location]",
|
||||
"tags": {
|
||||
"displayName": "StorageAccount"
|
||||
},
|
||||
"properties": {
|
||||
"accountType": "[variables('storageAccountType')]"
|
||||
}
|
||||
},
|
||||
|
||||
{
|
||||
"apiVersion": "[variables('apiVersion')]",
|
||||
"type": "Microsoft.Network/publicIPAddresses",
|
||||
"name": "[variables('publicIPAddressName')]",
|
||||
"location": "[resourceGroup().location]",
|
||||
"tags": {
|
||||
"displayName": "PublicIPAddress"
|
||||
},
|
||||
"properties": {
|
||||
"publicIPAllocationMethod": "[variables('publicIPAddressType')]",
|
||||
"dnsSettings": {
|
||||
"domainNameLabel": "[tolower(variables('dnsNameForPublicIP'))]"
|
||||
}
|
||||
}
|
||||
},
|
||||
|
||||
{
|
||||
"apiVersion": "[variables('apiVersion')]",
|
||||
"type": "Microsoft.Network/virtualNetworks",
|
||||
"name": "[variables('virtualNetworkName')]",
|
||||
"location": "[resourceGroup().location]",
|
||||
"dependsOn": [
|
||||
"[concat('Microsoft.Network/networkSecurityGroups/', variables('networkSecurityGroupName'))]"
|
||||
],
|
||||
"tags": {
|
||||
"displayName": "VirtualNetwork"
|
||||
},
|
||||
"properties": {
|
||||
"addressSpace": {
|
||||
"addressPrefixes": [
|
||||
"[variables('addressPrefix')]"
|
||||
]
|
||||
},
|
||||
"subnets": [
|
||||
{
|
||||
"name": "[variables('subnetName')]",
|
||||
"properties": {
|
||||
"addressPrefix": "[variables('subnetPrefix')]",
|
||||
"networkSecurityGroup": {
|
||||
"id": "[resourceId('Microsoft.Network/networkSecurityGroups', variables('networkSecurityGroupName'))]"
|
||||
}
|
||||
}
|
||||
}
|
||||
]
|
||||
}
|
||||
},
|
||||
|
||||
{
|
||||
"apiVersion": "[variables('apiVersion')]",
|
||||
"type": "Microsoft.Network/networkInterfaces",
|
||||
"name": "[variables('nicName')]",
|
||||
"location": "[resourceGroup().location]",
|
||||
"tags": {
|
||||
"displayName": "NetworkInterface"
|
||||
},
|
||||
"dependsOn": [
|
||||
"[concat('Microsoft.Network/publicIPAddresses/', variables('publicIPAddressName'))]",
|
||||
"[concat('Microsoft.Network/virtualNetworks/', variables('virtualNetworkName'))]"
|
||||
],
|
||||
"properties": {
|
||||
"ipConfigurations": [
|
||||
{
|
||||
"name": "ipconfig1",
|
||||
"properties": {
|
||||
"privateIPAllocationMethod": "Dynamic",
|
||||
"publicIPAddress": {
|
||||
"id": "[resourceId('Microsoft.Network/publicIPAddresses',variables('publicIPAddressName'))]"
|
||||
},
|
||||
"subnet": {
|
||||
"id": "[variables('subnetRef')]"
|
||||
}
|
||||
}
|
||||
}
|
||||
]
|
||||
}
|
||||
},
|
||||
|
||||
{
|
||||
"apiVersion": "[variables('apiVersion')]",
|
||||
"type": "Microsoft.Compute/virtualMachines",
|
||||
"name": "[parameters('VMName')]",
|
||||
"location": "[resourceGroup().location]",
|
||||
"tags": {
|
||||
"displayName": "VirtualMachine"
|
||||
},
|
||||
"dependsOn": [
|
||||
"[concat('Microsoft.Storage/storageAccounts/', variables('newStorageAccountName'))]",
|
||||
"[concat('Microsoft.Network/networkInterfaces/', variables('nicName'))]"
|
||||
],
|
||||
"properties": {
|
||||
"hardwareProfile": {
|
||||
"vmSize": "[parameters('vmSize')]"
|
||||
},
|
||||
"osProfile": {
|
||||
"computername": "[parameters('VMName')]",
|
||||
"adminUsername": "[parameters('adminUsername')]",
|
||||
"adminPassword": "[parameters('adminPassword')]"
|
||||
},
|
||||
"storageProfile": {
|
||||
"imageReference": {
|
||||
"publisher": "[variables('imagePublisher')]",
|
||||
"offer": "[variables('imageOffer')]",
|
||||
"sku": "[variables('windowsOSVersion')]",
|
||||
"version": "latest"
|
||||
},
|
||||
"osDisk": {
|
||||
"name": "osdisk",
|
||||
"vhd": {
|
||||
"uri": "[concat(reference(concat('Microsoft.Storage/storageAccounts/', variables('newStorageAccountName')), variables('apiVersion')).primaryEndpoints.blob, variables('vmStorageAccountContainerName'),'/',variables('OSDiskName'),'.vhd')]"
|
||||
},
|
||||
"caching": "ReadWrite",
|
||||
"createOption": "FromImage"
|
||||
}
|
||||
},
|
||||
"networkProfile": {
|
||||
"networkInterfaces": [
|
||||
{
|
||||
"id": "[resourceId('Microsoft.Network/networkInterfaces',variables('nicName'))]"
|
||||
}
|
||||
]
|
||||
}
|
||||
},
|
||||
"resources": [
|
||||
{
|
||||
"name": "containerConfiguration",
|
||||
"type": "extensions",
|
||||
"location": "[resourceGroup().location]",
|
||||
"apiVersion": "2015-06-15",
|
||||
"dependsOn": [
|
||||
"[concat('Microsoft.Compute/virtualMachines/', parameters('VMName'))]"
|
||||
],
|
||||
"tags": {
|
||||
"displayName": "containerConfiguration"
|
||||
},
|
||||
"properties": {
|
||||
"publisher": "Microsoft.Compute",
|
||||
"type": "CustomScriptExtension",
|
||||
"typeHandlerVersion": "1.2",
|
||||
"autoUpgradeMinorVersion": true,
|
||||
"settings": {
|
||||
"fileUris": [
|
||||
"https://raw.githubusercontent.com/Azure/azure-quickstart-templates/master/windows-server-containers-preview/azure-containers.ps1"
|
||||
],
|
||||
"commandToExecute": "[concat('powershell.exe -ExecutionPolicy Unrestricted -File azure-containers.ps1 -adminuser ',parameters('adminUsername'))]"
|
||||
}
|
||||
}
|
||||
}
|
||||
]
|
||||
}
|
||||
]
|
||||
}
|
||||
@ -1,7 +0,0 @@
|
||||
{
|
||||
"newStorageAccountName": { "value": "eshopsrvmvstoragewin" },
|
||||
"adminUsername": { "value": "eshop" },
|
||||
"adminPassword": { "value": "Pass@word" },
|
||||
"dnsNameForPublicIP": { "value": "eshop-srv-win" },
|
||||
"VMName": {"value": "eshop-srv-win"}
|
||||
}
|
||||
@ -1,66 +0,0 @@
|
||||
# Kubernetes CI/CD VSTS
|
||||
For k8s CI/CD pipeline delivery a series of tasks must be created in VSTS to deploy k8s in Azure
|
||||
|
||||
## Prerequisites
|
||||
* A Kubernetes cluster. Follow Azure Container Service's [walkthrough](https://docs.microsoft.com/en-us/azure/container-service/container-service-kubernetes-walkthrough) to create one.
|
||||
* A private Docker registry. Follow Azure Container Registry's [guide](https://docs.microsoft.com/en-us/azure/container-registry/container-registry-get-started-portal) to create one.
|
||||
* Optionally, previous steps can be skipped if you run gen-k8s-env.ps1 (or gen-k8s-env-aks.ps1 if you would like to use AKS instead of ACS) script to automatically create the azure environment needed for kubernetes deployment. Azure cli 2.0 must be previously installed [installation guide](https://docs.microsoft.com/en-us/cli/azure/install-azure-cli). For example:
|
||||
|
||||
>```
|
||||
>./gen-k8s-env -resourceGroupName k8sGroup -location westeurope -registryName k8sregistry -orchestratorName k8s-cluster -dnsName k8s-dns
|
||||
>```
|
||||
or using AKS instead of ACS
|
||||
>```
|
||||
>./gen-k8s-env-aks -resourceGroupName k8sGroup -location westeurope -registryName k8sregistry -dnsName k8s-dns -serviceName k8s-cluster -createAcr true -nodeCount 3 -nodeVMSize Standard_D2_v2
|
||||
>```
|
||||
* An `Azure Blob storage`. It is needed for storing the kubernetes config file used by the hosted agent to access to Kubernetes cluster. Example:
|
||||
|
||||
<img src="./img/blob_creation.png">
|
||||
|
||||
* Upload the `kubernetes config file` to the blob storage previously created. Execute the following command which will download the config file into the directory `c:\Users\<User>\.kube\` and then, upload it to your blob storage:
|
||||
|
||||
>```
|
||||
>https://eshopk8s.blob.core.windows.net/k8s-config/config
|
||||
>```
|
||||
|
||||
## Create the VSTS tasks
|
||||
1. Create a `Download File` task to download the kubernetes binary `kubectl` to the hosted agent. For example:
|
||||
|
||||
>```
|
||||
>https://storage.googleapis.com/kubernetes-release/release/v1.8.5/bin/windows/386/kubectl.exe
|
||||
>```
|
||||
|
||||
<img src="./img/get_kubectlbin_task.png">
|
||||
|
||||
2. Create a Download File task to download the kubernetes config file to the hosted agent. For example:
|
||||
|
||||
>```
|
||||
>https://eshopk8s.blob.core.windows.net/k8s-config/config
|
||||
>```
|
||||
<img src="./img/get_kubectlconfig_task.png">
|
||||
|
||||
3. Create a powershell task to execute the k8s deployment script. For example:
|
||||
|
||||
* Deployment script path
|
||||
|
||||
>```
|
||||
>$(System.DefaultWorkingDirectory)/All Microservices/docker-compose/deploy.ps1
|
||||
>```
|
||||
|
||||
* Deployment script path arguments. Use value:
|
||||
|
||||
>```
|
||||
>-deployCI $true -execPath '$(System.DefaultWorkingDirectory)/' -kubeconfigPath '$(System.DefaultWorkingDirectory)/' -deployInfrastructure $true -imageTag dev -configFile '$(System.DefaultWorkingDirectory)/$(Build.DefinitionName)/docker-compose/conf_local.yml'
|
||||
>```
|
||||
|
||||
|
||||
- deployCI: Must be set to `$true`. This avoids create images (always are pulled from registry) and compile bits.
|
||||
- deployInfrastructure: Can be set to `$false` if don't want to deploy infrastructure containers (like Redis, rabbit, SQL,...).
|
||||
- imageTag: Image tag to pull from k8s.
|
||||
- configFile: Configuration file (refer to [README.k8s.md](./README.k8s.md) for more info). This file is part of the VSTS build output.
|
||||
- execPath: path where the k8s binary is stored
|
||||
- kubeconfigPath: path where the k8s config file is stored
|
||||
|
||||
You can use additional parameters (i.e. pass registry and user/password to use custom registry instead of DockerHub. Plase, refer to [README.k8s.md](./README.k8s.md) for more info.
|
||||
|
||||
<img src="./img/deploy_script_task.png">
|
||||
@ -1,98 +0,0 @@
|
||||
# eShopOnContainers on Kubernetes
|
||||
The k8s directory contains Kubernetes configuration for the eShopOnContainers app and a PowerShell script to deploy it to a cluster. Each eShopOnContainers microservice has a deployment configuration in `deployments.yaml`, and is exposed to the cluster by a service in `services.yaml`. The microservices are exposed externally on individual routes (`/basket-api`, `/webmvc`, etc.) by an nginx reverse proxy specified in `frontend.yaml` and `nginx.conf`.
|
||||
|
||||
## Prerequisites
|
||||
* A Kubernetes cluster. Follow Azure Container Service's [walkthrough](https://docs.microsoft.com/en-us/azure/container-service/container-service-kubernetes-walkthrough) to create one.
|
||||
* A private Docker registry. Follow Azure Container Registry's [guide](https://docs.microsoft.com/en-us/azure/container-registry/container-registry-get-started-portal) to create one.
|
||||
* Optionally, previous steps can be skipped if you run the **gen-k8s-env-aks.ps1** script to create an AKS cluster environment or gen-k8s-env.ps1 script to create an ACS for Kuberentes cluster environment including the creation of additional Azure environment needed like an Azure Resource Manager and ACR registry.
|
||||
|
||||
Azure cli 2.0 must be previously installed [installation guide](https://docs.microsoft.com/en-us/cli/azure/install-azure-cli). For example:
|
||||
|
||||
**Important**: Note the parameter "-createAcr true". If you are creating the K8s cluster but you want to re-use and existing ACR, say "-createAcr false".
|
||||
|
||||
|
||||
For AKS:
|
||||
|
||||
>```
|
||||
>./gen-k8s-env-aks -resourceGroupName YoureShopAksResgroup -location centralus -serviceName YoureShopAksCluster -dnsNamePrefix youreshopaks -registryName YoureShopAcrRegistry -createAcr true -nodeCount 3 -nodeVMSize Standard_D2_v2
|
||||
>```
|
||||
|
||||
For ACS:
|
||||
|
||||
>```
|
||||
>./gen-k8s-env-aks -resourceGroupName k8sGroup -location westeurope -registryName k8sregistry -serviceName k8s-cluster -createAcr true -nodeCount 3 -nodeVMSize Standard_D2_v2
|
||||
>```
|
||||
|
||||
* A Docker development environment with `docker` and `docker-compose`.
|
||||
* Visit [docker.com](https://docker.com) to download the tools and set up the environment. Docker's [installation guide](https://docs.docker.com/engine/getstarted/step_one/#step-3-verify-your-installation) covers verifying your Docker installation.
|
||||
* The Kubernetes command line client, `kubectl`.
|
||||
* This can be installed with the `az` tool as described in the Azure Container Service [walkthrough](https://docs.microsoft.com/en-us/azure/container-service/container-service-kubernetes-walkthrough). `az` is also helpful for getting the credentials `kubectl` needs to access your cluster. For other installation options, and information about configuring `kubectl` yourself, see the [Kubernetes documentation](https://kubernetes.io/docs/tasks/kubectl/install/).
|
||||
|
||||
## Deploy the application with the deployment script
|
||||
1. Open a PowerShell command line at the `k8s` directory of your local eShopOnContainers repository.
|
||||
1. Ensure `docker`, `docker-compose`, and `kubectl` are on the path, and configured for your Docker machine and Kubernetes cluster.
|
||||
1. Run `deploy.ps1` with your registry information. The Docker username and password are provided by Azure Container Registry, and can be retrieved from the Azure portal. Optionally, ACR credentials can be obtained by running the following command:
|
||||
|
||||
>```
|
||||
>az acr credential show -n eshopregistry
|
||||
>```
|
||||
|
||||
Once the user and password are retrieved, run the following script for deployment. For example:
|
||||
|
||||
>```
|
||||
>./deploy.ps1 -registry myregistry.azurecr.io -dockerUser User -dockerPassword SecretPassword -configFile file_with_config.yaml
|
||||
>```
|
||||
|
||||
The parameter `configFile` is important (and mandatory) because it contains the configuration used for the Pods in Kubernetes. This allow deploying Pods that use your own resources in Azure or any other cloud provider. A configuration file `conf_local.yaml` is provided which configures Pods to use the infrastructure containers (that is sql server, rabbitmq, redis and mongodb must be deployed also in the k8s).
|
||||
|
||||
The script will build the code and corresponding Docker images, push the later to your registry, and deploy the application to your cluster. You can watch the deployment unfold from the Kubernetes web interface: run `kubectl proxy` and open a browser to [http://localhost:8001/ui](http://localhost:8001/ui)
|
||||
|
||||
### Pods configuration file
|
||||
|
||||
When deploying to k8s the script needs the `configFile` parameter with the location of the YAML configuration file. This file contains the configuration of the pods. The file is a .YAML file. For reference another configuration file (conf_cloud.yaml) is provided but without valid values.
|
||||
|
||||
If you deploy the infrastructure containers use `conf_local.yaml` as a value for `configFile` parameter. If you don't deploy the infrastructure containers use your own configuration file with the correct values.
|
||||
|
||||
### Parameters of the deploy.ps1 script
|
||||
|
||||
The script accepts following parameters:
|
||||
|
||||
+ `registry`: Name of the Docker registry to use. If not passed DockerHub is assumed
|
||||
+ `dockerUser`: Login to use for the Docker registry (if needed)
|
||||
+ `dockerPassword`: Password to use for the Docker registry (if needed)
|
||||
+ `execPath`: Location of `kubectl` (if not in the path). If passed must finish with the path character.
|
||||
+ `kubeconfigPath`: Location of the `kubectl` configuration file. **This parameter is used only in the CI pipeline**, so you don't need to pass it when invoking the script using the CLI.
|
||||
+ `configFile`: Location of the Yaml file with the `externalcfg` configmap to be deployed. This configmap is used to configure the Pod's environment **This parameter is mandatory**
|
||||
+ `imageTag`: Tag of the images to deploy to k8s. If not passed the name of the current branch is used.
|
||||
+ `externalDns`: External DNS name of the k8s. This is only needed if you have configured a DNS that points to your k8s external IP. If you don't have any DNS configured do not pass this parameter.
|
||||
+ `deployCI`: If `true` means that script is running under the context of a VSTS Hosted Build Agent. **You should never use this parameter from CLI**
|
||||
+ `buildBits`: means that the source code of eShopOnContainers will be built. If you have built your code (and have all projects published in `obj/Docker/publish`) do not pass this parameter. Default value is `false`
|
||||
+ `buildImages`: If `true` (default value) Docker images are built and pushed in the Docker registry. If you set this parameter to `false`, Docker images won't be built nor pushed in the Docker registry (but k8s' deployments and services will be redeployed).
|
||||
+ `deployInfrastructure`: If `true` infrastructure containers (rabbitmq, mongo, redis, sql) will be deployed in k8s. If `false` those containers (and its related deployments and services in k8s) won't be deployed.
|
||||
+ `dockerOrg`: Name of the organization in the registry where the images are (or will be pushed). Default value is `eshop` (which has images provided by Microsoft)
|
||||
|
||||
**Important:** If you **don't pass the `-buildBits $true` the script won't build and publish the projects** to their `obj/Docker/publish` folder. If any project is not published, you'll be receiving errors like:
|
||||
|
||||
```
|
||||
ERROR: Service 'xxxxxxx' failed to build: COPY failed: stat /var/lib/docker/tmp/docker-builder123456789/obj/Docker/publish: no such file or directory
|
||||
```
|
||||
|
||||
### Typical usages of the script:
|
||||
|
||||
Build all projects, and deploy all them in k8s including infrastructure containers in a organization called `foo` in Docker Hub. Images will be tagged with my current git branch and containers will use the configuration set in `conf_local.yml` file:
|
||||
|
||||
```
|
||||
./deploy.ps1 -buildBits $true -dockerOrg foo -dockerUser MY_USER -dockerPassword MY_PASSWORD -configFile conf_local.yml
|
||||
```
|
||||
|
||||
Do not build any project and don't rebuild docker images. Create k8s deployments that will pull images from my private repository, in the `foo` organization, using the tag `latest`. Containers will use the configuration set in `conf_cloud` file.
|
||||
|
||||
```
|
||||
./deploy.ps1 -buildImages $false -dockerOrg foo -registry MY_REGISTRY_FQDN -dockerUser MY_USER -dockerPassword MY_PASSWORD -configFile conf_cloud.yml -imageTag master
|
||||
```
|
||||
|
||||
Deploy k8s using public images that Microsoft provides:
|
||||
|
||||
```
|
||||
./deploy.ps1 -buildImages $false -configFile conf_local.yml -imageTag master
|
||||
```
|
||||
@ -1,72 +0,0 @@
|
||||
Param(
|
||||
[parameter(Mandatory=$false)][string]$registry,
|
||||
[parameter(Mandatory=$false)][string]$dockerUser,
|
||||
[parameter(Mandatory=$false)][string]$dockerPassword,
|
||||
[parameter(Mandatory=$false)][string]$imageTag,
|
||||
[parameter(Mandatory=$false)][bool]$buildImages=$true,
|
||||
[parameter(Mandatory=$false)][bool]$pushImages=$true,
|
||||
[parameter(Mandatory=$false)][string]$dockerOrg="eshop"
|
||||
)
|
||||
|
||||
# Initialization
|
||||
|
||||
$useDockerHub = [string]::IsNullOrEmpty($registry)
|
||||
|
||||
# Check required commands (only if not in CI environment)
|
||||
|
||||
$requiredCommands = ("docker", "docker-compose")
|
||||
foreach ($command in $requiredCommands) {
|
||||
if ((Get-Command $command -ErrorAction SilentlyContinue) -eq $null) {
|
||||
Write-Host "$command must be on path" -ForegroundColor Red
|
||||
exit
|
||||
}
|
||||
}
|
||||
|
||||
# Get tag to use from current branch if no tag is passed
|
||||
if ([string]::IsNullOrEmpty($imageTag)) {
|
||||
$imageTag = $(git rev-parse --abbrev-ref HEAD)
|
||||
}
|
||||
Write-Host "Docker image Tag: $imageTag" -ForegroundColor Yellow
|
||||
|
||||
# Build docker images if needed
|
||||
if ($buildImages) {
|
||||
Write-Host "Building Docker images tagged with '$imageTag'" -ForegroundColor Yellow
|
||||
$env:TAG=$imageTag
|
||||
docker-compose -p .. -f ../docker-compose.yml build
|
||||
}
|
||||
|
||||
# Login to Docker registry
|
||||
if (-not [string]::IsNullOrEmpty($dockerUser)) {
|
||||
$registryFDQN = if (-not $useDockerHub) {$registry} else {"index.docker.io/v1/"}
|
||||
|
||||
Write-Host "Logging in to $registryFDQN as user $dockerUser" -ForegroundColor Yellow
|
||||
if ($useDockerHub) {
|
||||
docker login -u $dockerUser -p $dockerPassword
|
||||
}
|
||||
else {
|
||||
docker login -u $dockerUser -p $dockerPassword $registryFDQN
|
||||
}
|
||||
|
||||
if (-not $LastExitCode -eq 0) {
|
||||
Write-Host "Login failed" -ForegroundColor Red
|
||||
exit
|
||||
}
|
||||
|
||||
}
|
||||
|
||||
# Push images to Docker registry
|
||||
if ($pushImages) {
|
||||
Write-Host "Pushing images to $registry/$dockerOrg..." -ForegroundColor Yellow
|
||||
$services = ("basket.api", "catalog.api", "identity.api", "ordering.api", "ordering.backgroundtasks", "marketing.api","payment.api","locations.api", "webmvc", "webspa", "webstatus", "ocelotapigw", "mobileshoppingagg", "webshoppingagg", "ordering.signalrhub")
|
||||
|
||||
foreach ($service in $services) {
|
||||
$imageFqdn = if ($useDockerHub) {"$dockerOrg/${service}"} else {"$registry/$dockerOrg/${service}"}
|
||||
docker tag eshop/${service}:$imageTag ${imageFqdn}:$imageTag
|
||||
docker push ${imageFqdn}:$imageTag
|
||||
}
|
||||
}
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
@ -1,17 +0,0 @@
|
||||
# YAML files used to deploy to k8s
|
||||
|
||||
This is just a brief enumeration of the configuration files used to create the k8s objects. Use as reference to find where specific object is.
|
||||
|
||||
- `deployments.yaml` Contains the definition of all deployments of the eShopOnContainers. Do not contain any infrastructure deployment (so no SQL, Redis, ...).
|
||||
- `services.yaml` Contains the definition of all services of the eShopOnContainers. Do not contain any infrastructure service (so no SQL, Redis, ...).
|
||||
- `basket-data.yaml` Contains the definition of the Redis (used by basket.api) deployment and service
|
||||
- `nosql-data.yaml` Contains the definition of the Mongodb (used by locations and marketing) deployment and service
|
||||
- `sql-data.yaml` Contains the definition of the SQL server deployment and service
|
||||
- `rabbitmq.yaml` Contains the definition of the RabbitMQ deployment and service
|
||||
- `keystore-data.yaml` Contains the deployment and service definition of the Redis used to mantain coherence between all the ASP.NET Identity keystores.
|
||||
- `conf_local.yaml` Contains the configuration map that configures all the Pods to use "local" containers (that is all containers in k8s)
|
||||
- `conf_cloud.yaml` Contains the configuration map that configures all the Pods to use "cloud" resources (that is use Azure resources instead infrastructure containers). This file is provided with no valid values, just for example.
|
||||
- `frontend.yaml` Contains the deployment and service definition of the NGINX frontend used as reverse-proxy
|
||||
|
||||
- For more information what kubernetes deployments are, read [Kubernetes help](https://kubernetes.io/docs/concepts/workloads/controllers/deployment/)
|
||||
- For more information what kubernetes services are, read [Kubernetes help](https://kubernetes.io/docs/concepts/services-networking/service/)
|
||||
@ -1,34 +0,0 @@
|
||||
apiVersion: v1
|
||||
kind: ConfigMap
|
||||
metadata:
|
||||
name: externalcfg
|
||||
labels:
|
||||
app: eshop
|
||||
data:
|
||||
# Basket.API entries
|
||||
basket__ConnectionString: REDIS CONNECTION STRING FOR BASKET
|
||||
# Catalog.API entries
|
||||
catalog__ConnectionString: Catalog SQL SERVER CONNECTION STRING (Server=xxxx;Intial Catalog=yyy;....)
|
||||
# Identity.API entries
|
||||
IdentitySqlDb: Identity SQL SERVER CONNECTION STRING (Server=xxxx;Intial Catalog=yyy;....)
|
||||
# Locations.API entries
|
||||
LocationsBus: CONNECTION_STRING (NAME OF RABBITMQ CONTAINER OR Endpoint=sb://XXXX for topic in case of using Azure)
|
||||
LocationsNoSqlDb: Locations MongoDb ConnectionString
|
||||
LocationsNoSqlDbName: Locations MongoDb database (LocationsDb)
|
||||
# Marketing.API entries
|
||||
MarketingBus: CONNECTION_STRING (NAME OF RABBITMQ CONTAINER OR Endpoint=sb://XXXX for topic in case of using Azure)
|
||||
MarketingNoSqlDb: Marketing MongoDb ConnectionString
|
||||
MarketingNoSqlDbName: Marketing MongoDb database (MarketingDb)
|
||||
MarketingSqlDb: Marketing SQL SERVER CONNECTION STRING (Server=xxxx;Intial Catalog=yyy;....)
|
||||
# Ordering.API entries
|
||||
OrderingBus: CONNECTION_STRING (NAME OF RABBITMQ CONTAINER OR Endpoint=sb://XXXX for topic in case of using Azure)
|
||||
OrderingSqlDb: Ordering SQL SERVER CONNECTION STRING (Server=xxxx;Intial Catalog=yyy;....)
|
||||
GracePeriodManager_GracePeriodTime: "1"
|
||||
GracePeriodManager_CheckUpdateTime: "15000"
|
||||
# Payment.API entries
|
||||
PaymentBus: CONNECTION_STRING (NAME OF RABBITMQ CONTAINER OR Endpoint=sb://XXXX for topic in case of using Azure)
|
||||
# Global entries
|
||||
all_UseAzureServiceBus: "TRUE" IF USE AZURE SB ("FALSE" FOR USING RABBITMQ)
|
||||
keystore: REDIS CONNECTION STRING FOR KEYSTORE
|
||||
all_EventBusConnection: CONNECTION_STRING (NAME OF RABBITMQ CONTAINER OR Endpoint=sb://XXXX in case of using Azure)
|
||||
all_InstrumentationKey: APPINSIGHTS KEY
|
||||
@ -1,27 +0,0 @@
|
||||
apiVersion: v1
|
||||
kind: ConfigMap
|
||||
metadata:
|
||||
name: externalcfg
|
||||
labels:
|
||||
app: eshop
|
||||
data:
|
||||
basket__ConnectionString: basket-data
|
||||
catalog__ConnectionString: Server=sql-data;Initial Catalog=Microsoft.eShopOnContainers.Services.CatalogDb;User Id=sa;Password=Pass@word;
|
||||
catalog__AzureStorageEnabled: "False"
|
||||
identity__ConnectionString: Server=sql-data;Initial Catalog=Microsoft.eShopOnContainers.Services.IdentityDb;User Id=sa;Password=Pass@word;
|
||||
locations__ConnectionString: mongodb://nosql-data
|
||||
locations__Database: LocationsDb
|
||||
marketing__MongoConnectionString: mongodb://nosql-data
|
||||
marketing__MongoDatabase: MarketingDb
|
||||
marketing__ConnectionString: Server=sql-data;Initial Catalog=Microsoft.eShopOnContainers.Services.MarketingDb;User Id=sa;Password=Pass@word;
|
||||
ordering__ConnectionString: Server=sql-data;Initial Catalog=Microsoft.eShopOnContainers.Services.OrderingDb;User Id=sa;Password=Pass@word;
|
||||
keystore: keystore-data
|
||||
GracePeriodManager__GracePeriodTime: "1"
|
||||
GracePeriodManager__CheckUpdateTime: "15000"
|
||||
all__EventBusConnection: rabbitmq
|
||||
all__InstrumentationKey: ""
|
||||
all__EnableLoadTest: "False"
|
||||
all__UseAzureServiceBus: "False"
|
||||
|
||||
|
||||
|
||||
@ -1 +0,0 @@
|
||||
kubectl apply -f nginx-ingress\cloud-generic.yaml
|
||||
@ -1,2 +0,0 @@
|
||||
kubectl apply -f nginx-ingress\cm.yaml
|
||||
kubectl apply -f nginx-ingress\cloud-generic.yaml
|
||||
@ -1,5 +0,0 @@
|
||||
# Deploy nginx-ingress core files
|
||||
kubectl apply -f nginx-ingress\mandatory.yaml
|
||||
|
||||
|
||||
|
||||
@ -1,2 +0,0 @@
|
||||
kubectl apply -f .\nodeports\rabbitmq-admin.yaml
|
||||
kubectl apply -f .\nodeports\sql-services.yaml
|
||||
@ -1,212 +0,0 @@
|
||||
Param(
|
||||
[parameter(Mandatory=$false)][string]$registry,
|
||||
[parameter(Mandatory=$false)][string]$dockerUser,
|
||||
[parameter(Mandatory=$false)][string]$dockerPassword,
|
||||
[parameter(Mandatory=$false)][string]$execPath,
|
||||
[parameter(Mandatory=$false)][string]$kubeconfigPath,
|
||||
[parameter(Mandatory=$true)][string]$configFile,
|
||||
[parameter(Mandatory=$false)][string]$imageTag,
|
||||
[parameter(Mandatory=$false)][bool]$deployCI=$false,
|
||||
[parameter(Mandatory=$false)][bool]$buildImages=$true,
|
||||
[parameter(Mandatory=$false)][bool]$pushImages=$true,
|
||||
[parameter(Mandatory=$false)][bool]$deployInfrastructure=$true,
|
||||
[parameter(Mandatory=$false)][string]$dockerOrg="eshop"
|
||||
)
|
||||
|
||||
function ExecKube($cmd) {
|
||||
if($deployCI) {
|
||||
$kubeconfig = $kubeconfigPath + 'config';
|
||||
$exp = $execPath + 'kubectl ' + $cmd + ' --kubeconfig=' + $kubeconfig
|
||||
Invoke-Expression $exp
|
||||
}
|
||||
else{
|
||||
$exp = $execPath + 'kubectl ' + $cmd
|
||||
Invoke-Expression $exp
|
||||
}
|
||||
}
|
||||
|
||||
# Initialization
|
||||
$debugMode = $PSCmdlet.MyInvocation.BoundParameters["Debug"].IsPresent
|
||||
$useDockerHub = [string]::IsNullOrEmpty($registry)
|
||||
|
||||
$externalDns = & ExecKube -cmd 'get svc ingress-nginx -n ingress-nginx -o=jsonpath="{.status.loadBalancer.ingress[0].ip}"'
|
||||
Write-Host "Ingress ip detected: $externalDns" -ForegroundColor Yellow
|
||||
|
||||
if (-not [bool]($externalDns -as [ipaddress])) {
|
||||
Write-Host "Must install ingress first" -ForegroundColor Red
|
||||
Write-Host "Run deploy-ingress.ps1 and deploy-ingress-azure.ps1" -ForegroundColor Red
|
||||
exit
|
||||
}
|
||||
|
||||
|
||||
# Check required commands (only if not in CI environment)
|
||||
if(-not $deployCI) {
|
||||
$requiredCommands = ("docker", "docker-compose", "kubectl")
|
||||
foreach ($command in $requiredCommands) {
|
||||
if ((Get-Command $command -ErrorAction SilentlyContinue) -eq $null) {
|
||||
Write-Host "$command must be on path" -ForegroundColor Red
|
||||
exit
|
||||
}
|
||||
}
|
||||
}
|
||||
else {
|
||||
$buildImages = false; # Never build images through CI, as they previously built
|
||||
}
|
||||
|
||||
# Get tag to use from current branch if no tag is passed
|
||||
if ([string]::IsNullOrEmpty($imageTag)) {
|
||||
$imageTag = $(git rev-parse --abbrev-ref HEAD)
|
||||
}
|
||||
Write-Host "Docker image Tag: $imageTag" -ForegroundColor Yellow
|
||||
|
||||
# building docker images if needed
|
||||
if ($buildImages) {
|
||||
Write-Host "Building Docker images tagged with '$imageTag'" -ForegroundColor Yellow
|
||||
$env:TAG=$imageTag
|
||||
docker-compose -p .. -f ../docker-compose.yml build
|
||||
}
|
||||
|
||||
if ($pushImages) {
|
||||
Write-Host "Pushing images to $registry/$dockerOrg..." -ForegroundColor Yellow
|
||||
$services = ("basket.api", "catalog.api", "identity.api", "ordering.api", "ordering.backgroundtasks", "marketing.api","payment.api","locations.api", "webmvc", "webspa", "webstatus", "ocelotapigw", "mobileshoppingagg", "webshoppingagg", "ordering.signalrhub")
|
||||
|
||||
foreach ($service in $services) {
|
||||
$imageFqdn = if ($useDockerHub) {"$dockerOrg/${service}"} else {"$registry/$dockerOrg/${service}"}
|
||||
docker tag eshop/${service}:$imageTag ${imageFqdn}:$imageTag
|
||||
docker push ${imageFqdn}:$imageTag
|
||||
}
|
||||
}
|
||||
|
||||
# if we have login/pwd add the secret to k8s
|
||||
if (-not [string]::IsNullOrEmpty($dockerUser)) {
|
||||
$registryFDQN = if (-not $useDockerHub) {$registry} else {"index.docker.io/v1/"}
|
||||
|
||||
Write-Host "Logging in to $registryFDQN as user $dockerUser" -ForegroundColor Yellow
|
||||
if ($useDockerHub) {
|
||||
docker login -u $dockerUser -p $dockerPassword
|
||||
}
|
||||
else {
|
||||
docker login -u $dockerUser -p $dockerPassword $registryFDQN
|
||||
}
|
||||
|
||||
if (-not $LastExitCode -eq 0) {
|
||||
Write-Host "Login failed" -ForegroundColor Red
|
||||
exit
|
||||
}
|
||||
|
||||
# Try to delete the Docker registry key secret
|
||||
ExecKube -cmd 'delete secret docker-registry registry-key'
|
||||
|
||||
# Create the Docker registry key secret
|
||||
ExecKube -cmd 'create secret docker-registry registry-key `
|
||||
--docker-server=$registryFDQN `
|
||||
--docker-username=$dockerUser `
|
||||
--docker-password=$dockerPassword `
|
||||
--docker-email=not@used.com'
|
||||
}
|
||||
|
||||
# Removing previous services & deployments
|
||||
Write-Host "Removing existing services & deployments.." -ForegroundColor Yellow
|
||||
ExecKube -cmd 'delete deployments --all'
|
||||
ExecKube -cmd 'delete services --all'
|
||||
ExecKube -cmd 'delete configmap internalurls'
|
||||
ExecKube -cmd 'delete configmap urls'
|
||||
ExecKube -cmd 'delete configmap externalcfg'
|
||||
ExecKube -cmd 'delete configmap ocelot'
|
||||
ExecKube -cmd 'delete -f ingress.yaml'
|
||||
|
||||
# start sql, rabbitmq, frontend deployments
|
||||
if ($deployInfrastructure) {
|
||||
Write-Host 'Deploying infrastructure deployments (databases, redis, RabbitMQ...)' -ForegroundColor Yellow
|
||||
ExecKube -cmd 'create -f sql-data.yaml -f basket-data.yaml -f keystore-data.yaml -f rabbitmq.yaml -f nosql-data.yaml'
|
||||
}
|
||||
|
||||
|
||||
Write-Host 'Deploying ocelot APIGW' -ForegroundColor Yellow
|
||||
|
||||
ExecKube "create configmap ocelot --from-file=mm=ocelot/configuration-mobile-marketing.json --from-file=ms=ocelot/configuration-mobile-shopping.json --from-file=wm=ocelot/configuration-web-marketing.json --from-file=ws=ocelot/configuration-web-shopping.json "
|
||||
ExecKube -cmd "apply -f ocelot/deployment.yaml"
|
||||
ExecKube -cmd "apply -f ocelot/service.yaml"
|
||||
|
||||
Write-Host 'Deploying code deployments (Web APIs, Web apps, ...)' -ForegroundColor Yellow
|
||||
ExecKube -cmd 'create -f services.yaml'
|
||||
|
||||
ExecKube -cmd 'create -f internalurls.yaml'
|
||||
ExecKube -cmd 'create configmap urls `
|
||||
--from-literal=PicBaseUrl=http://$($externalDns)/webshoppingapigw/c/api/v1/catalog/items/[0]/pic/ `
|
||||
--from-literal=Marketing_PicBaseUrl=http://$($externalDns)/webmarketingapigw/m/api/v1/campaigns/[0]/pic/ `
|
||||
--from-literal=mvc_e=http://$($externalDns)/webmvc `
|
||||
--from-literal=marketingapigw_e=http://$($externalDns)/webmarketingapigw `
|
||||
--from-literal=webshoppingapigw_e=http://$($externalDns)/webshoppingapigw `
|
||||
--from-literal=mobileshoppingagg_e=http://$($externalDns)/mobileshoppingagg `
|
||||
--from-literal=webshoppingagg_e=http://$($externalDns)/webshoppingagg `
|
||||
--from-literal=identity_e=http://$($externalDns)/identity `
|
||||
--from-literal=spa_e=http://$($externalDns) `
|
||||
--from-literal=locations_e=http://$($externalDns)/locations-api `
|
||||
--from-literal=marketing_e=http://$($externalDns)/marketing-api `
|
||||
--from-literal=basket_e=http://$($externalDns)/basket-api `
|
||||
--from-literal=ordering_e=http://$($externalDns)/ordering-api `
|
||||
--from-literal=xamarin_callback_e=http://$($externalDns)/xamarincallback'
|
||||
|
||||
ExecKube -cmd 'label configmap urls app=eshop'
|
||||
|
||||
Write-Host "Deploying configuration from $configFile" -ForegroundColor Yellow
|
||||
ExecKube -cmd "create -f $configFile"
|
||||
|
||||
Write-Host "Creating deployments..." -ForegroundColor Yellow
|
||||
ExecKube -cmd 'create -f deployments.yaml'
|
||||
|
||||
# update deployments with the correct image (with tag and/or registry)
|
||||
$registryPath = ""
|
||||
if (-not [string]::IsNullOrEmpty($registry)) {
|
||||
$registryPath = "$registry/"
|
||||
}
|
||||
|
||||
Write-Host "Update Image containers to use prefix '$registry$dockerOrg' and tag '$imageTag'" -ForegroundColor Yellow
|
||||
|
||||
ExecKube -cmd 'set image deployments/basket basket=${registryPath}${dockerOrg}/basket.api:$imageTag'
|
||||
ExecKube -cmd 'set image deployments/catalog catalog=${registryPath}${dockerOrg}/catalog.api:$imageTag'
|
||||
ExecKube -cmd 'set image deployments/identity identity=${registryPath}${dockerOrg}/identity.api:$imageTag'
|
||||
ExecKube -cmd 'set image deployments/ordering ordering=${registryPath}${dockerOrg}/ordering.api:$imageTag'
|
||||
ExecKube -cmd 'set image deployments/ordering-backgroundtasks ordering-backgroundtasks=${registryPath}${dockerOrg}/ordering.backgroundtasks:$imageTag'
|
||||
ExecKube -cmd 'set image deployments/marketing marketing=${registryPath}${dockerOrg}/marketing.api:$imageTag'
|
||||
ExecKube -cmd 'set image deployments/locations locations=${registryPath}${dockerOrg}/locations.api:$imageTag'
|
||||
ExecKube -cmd 'set image deployments/payment payment=${registryPath}${dockerOrg}/payment.api:$imageTag'
|
||||
ExecKube -cmd 'set image deployments/webmvc webmvc=${registryPath}${dockerOrg}/webmvc:$imageTag'
|
||||
ExecKube -cmd 'set image deployments/webstatus webstatus=${registryPath}${dockerOrg}/webstatus:$imageTag'
|
||||
ExecKube -cmd 'set image deployments/webspa webspa=${registryPath}${dockerOrg}/webspa:$imageTag'
|
||||
ExecKube -cmd 'set image deployments/ordering-signalrhub ordering-signalrhub=${registryPath}${dockerOrg}/ordering.signalrhub:$imageTag'
|
||||
|
||||
ExecKube -cmd 'set image deployments/mobileshoppingagg mobileshoppingagg=${registryPath}${dockerOrg}/mobileshoppingagg:$imageTag'
|
||||
ExecKube -cmd 'set image deployments/webshoppingagg webshoppingagg=${registryPath}${dockerOrg}/webshoppingagg:$imageTag'
|
||||
|
||||
ExecKube -cmd 'set image deployments/apigwmm apigwmm=${registryPath}${dockerOrg}/ocelotapigw:$imageTag'
|
||||
ExecKube -cmd 'set image deployments/apigwms apigwms=${registryPath}${dockerOrg}/ocelotapigw:$imageTag'
|
||||
ExecKube -cmd 'set image deployments/apigwwm apigwwm=${registryPath}${dockerOrg}/ocelotapigw:$imageTag'
|
||||
ExecKube -cmd 'set image deployments/apigwws apigwws=${registryPath}${dockerOrg}/ocelotapigw:$imageTag'
|
||||
|
||||
Write-Host "Execute rollout..." -ForegroundColor Yellow
|
||||
ExecKube -cmd 'rollout resume deployments/basket'
|
||||
ExecKube -cmd 'rollout resume deployments/catalog'
|
||||
ExecKube -cmd 'rollout resume deployments/identity'
|
||||
ExecKube -cmd 'rollout resume deployments/ordering'
|
||||
ExecKube -cmd 'rollout resume deployments/ordering-backgroundtasks'
|
||||
ExecKube -cmd 'rollout resume deployments/marketing'
|
||||
ExecKube -cmd 'rollout resume deployments/locations'
|
||||
ExecKube -cmd 'rollout resume deployments/payment'
|
||||
ExecKube -cmd 'rollout resume deployments/webmvc'
|
||||
ExecKube -cmd 'rollout resume deployments/webstatus'
|
||||
ExecKube -cmd 'rollout resume deployments/webspa'
|
||||
ExecKube -cmd 'rollout resume deployments/mobileshoppingagg'
|
||||
ExecKube -cmd 'rollout resume deployments/webshoppingagg'
|
||||
ExecKube -cmd 'rollout resume deployments/apigwmm'
|
||||
ExecKube -cmd 'rollout resume deployments/apigwms'
|
||||
ExecKube -cmd 'rollout resume deployments/apigwwm'
|
||||
ExecKube -cmd 'rollout resume deployments/apigwws'
|
||||
ExecKube -cmd 'rollout resume deployments/ordering-signalrhub'
|
||||
|
||||
Write-Host "Adding/Updating ingress resource..." -ForegroundColor Yellow
|
||||
ExecKube -cmd 'apply -f ingress.yaml'
|
||||
|
||||
Write-Host "WebSPA is exposed at http://$externalDns, WebMVC at http://$externalDns/webmvc, WebStatus at http://$externalDns/webstatus" -ForegroundColor Yellow
|
||||
|
||||
@ -1,212 +0,0 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# http://redsymbol.net/articles/unofficial-bash-strict-mode/
|
||||
set -euo pipefail
|
||||
|
||||
# This script is comparable to the PowerShell script deploy.ps1 but to be used from a Mac bash environment.
|
||||
# There are, however, the following few differences/limitations:
|
||||
|
||||
# It assumes docker/container registry login was already performed
|
||||
# It assumes K8s was given access to the registry—does not create any K8s secrets
|
||||
# It does not support explicit kubectl config file (relies on kubectl config use-context to point kubectl at the right cluster/namespace)
|
||||
# It always deploys infrastructure bits (redis, SQL Server etc)
|
||||
# The script was tested only with Azure Container Registry (not Docker Hub, although it is expected to work with Docker Hub too)
|
||||
|
||||
# Feel free to submit a PR in order to improve it.
|
||||
|
||||
usage()
|
||||
{
|
||||
cat <<END
|
||||
deploy.sh: deploys eShopOnContainers application to Kubernetes cluster
|
||||
Parameters:
|
||||
-r | --registry <container registry>
|
||||
Specifies container registry (ACR) to use (required), e.g. myregistry.azurecr.io
|
||||
-t | --tag <docker image tag>
|
||||
Default: newly created, date-based timestamp, with 1-minute resolution
|
||||
-b | --build-solution
|
||||
Force solution build before deployment (default: false)
|
||||
--skip-image-build
|
||||
Do not build images (default is to build all images)
|
||||
--skip-image-push
|
||||
Do not upload images to the container registry (just run the Kubernetes deployment portion)
|
||||
Default is to push images to container registry
|
||||
-h | --help
|
||||
Displays this help text and exits the script
|
||||
|
||||
It is assumed that the Kubernetes AKS cluster has been granted access to ACR registry.
|
||||
For more info see
|
||||
https://docs.microsoft.com/en-us/azure/container-registry/container-registry-auth-aks
|
||||
|
||||
WARNING! THE SCRIPT WILL COMPLETELY DESTROY ALL DEPLOYMENTS AND SERVICES VISIBLE
|
||||
FROM THE CURRENT CONFIGURATION CONTEXT.
|
||||
It is recommended that you create a separate namespace and confguration context
|
||||
for the eShopOnContainers application, to isolate it from other applications on the cluster.
|
||||
For more information see https://kubernetes.io/docs/tasks/administer-cluster/namespaces/
|
||||
You can use eshop-namespace.yaml file (in the same directory) to create the namespace.
|
||||
|
||||
END
|
||||
}
|
||||
|
||||
image_tag=$(date '+%Y%m%d%H%M')
|
||||
build_solution=''
|
||||
container_registry=''
|
||||
build_images='yes'
|
||||
push_images='yes'
|
||||
|
||||
while [[ $# -gt 0 ]]; do
|
||||
case "$1" in
|
||||
-r | --registry )
|
||||
container_registry="$2"; shift 2 ;;
|
||||
-t | --tag )
|
||||
image_tag="$2"; shift 2 ;;
|
||||
-b | --build-solution )
|
||||
build_solution='yes'; shift ;;
|
||||
--skip-image-build )
|
||||
build_images=''; shift ;;
|
||||
--skip-image-push )
|
||||
push_images=''; shift ;;
|
||||
-h | --help )
|
||||
usage; exit 1 ;;
|
||||
*)
|
||||
echo "Unknown option $1"
|
||||
usage; exit 2 ;;
|
||||
esac
|
||||
done
|
||||
|
||||
if [[ ! $container_registry ]]; then
|
||||
echo 'Container registry must be specified (e.g. myregistry.azurecr.io)'
|
||||
echo ''
|
||||
usage
|
||||
exit 3
|
||||
fi
|
||||
|
||||
if [[ $build_solution ]]; then
|
||||
echo "#################### Building eShopOnContainers solution ####################"
|
||||
dotnet publish -o obj/Docker/publish ../eShopOnContainers-ServicesAndWebApps.sln
|
||||
fi
|
||||
|
||||
export TAG=$image_tag
|
||||
|
||||
if [[ $build_images ]]; then
|
||||
echo "#################### Building eShopOnContainers Docker images ####################"
|
||||
docker-compose -p .. -f ../docker-compose.yml build
|
||||
|
||||
# Remove temporary images
|
||||
docker rmi $(docker images -qf "dangling=true")
|
||||
fi
|
||||
|
||||
if [[ $push_images ]]; then
|
||||
echo "#################### Pushing images to registry ####################"
|
||||
services=(basket.api catalog.api identity.api ordering.api marketing.api payment.api locations.api webmvc webspa webstatus)
|
||||
|
||||
for service in "${services[@]}"
|
||||
do
|
||||
echo "Pushing image for service $service..."
|
||||
docker tag "eshop/$service:$image_tag" "$container_registry/$service:$image_tag"
|
||||
docker push "$container_registry/$service:$image_tag"
|
||||
done
|
||||
fi
|
||||
|
||||
echo "#################### Cleaning up old deployment ####################"
|
||||
kubectl delete deployments --all
|
||||
kubectl delete services --all
|
||||
kubectl delete configmap config-files || true
|
||||
kubectl delete configmap urls || true
|
||||
kubectl delete configmap externalcfg || true
|
||||
|
||||
echo "#################### Deploying infrastructure components ####################"
|
||||
kubectl create configmap config-files --from-file=nginx-conf=nginx.conf
|
||||
kubectl label configmap config-files app=eshop
|
||||
kubectl create -f sql-data.yaml -f basket-data.yaml -f keystore-data.yaml -f rabbitmq.yaml -f nosql-data.yaml
|
||||
|
||||
echo "#################### Creating application service definitions ####################"
|
||||
kubectl create -f services.yaml -f frontend.yaml
|
||||
|
||||
echo "#################### Waiting for Azure to provision external IP ####################"
|
||||
|
||||
ip_regex='([0-9]{1,3}\.){3}[0-9]{1,3}'
|
||||
while true; do
|
||||
printf "."
|
||||
frontendUrl=$(kubectl get svc frontend -o=jsonpath="{.status.loadBalancer.ingress[0].ip}")
|
||||
if [[ $frontendUrl =~ $ip_regex ]]; then
|
||||
break
|
||||
fi
|
||||
sleep 5s
|
||||
done
|
||||
|
||||
printf "\n"
|
||||
externalDns=$frontendUrl
|
||||
echo "Using $externalDns as the external DNS/IP of the K8s cluster"
|
||||
|
||||
echo "#################### Creating application configuration ####################"
|
||||
|
||||
# urls configmap
|
||||
kubectl create configmap urls \
|
||||
"--from-literal=BasketUrl=http://basket" \
|
||||
"--from-literal=BasketHealthCheckUrl=http://basket/hc" \
|
||||
"--from-literal=CatalogUrl=http://$externalDns/catalog-api" \
|
||||
"--from-literal=CatalogHealthCheckUrl=http://catalog/hc" \
|
||||
"--from-literal=PicBaseUrl=http://$externalDns/catalog-api/api/v1/catalog/items/[0]/pic/" \
|
||||
"--from-literal=Marketing_PicBaseUrl=http://$externalDns/marketing-api/api/v1/campaigns/[0]/pic/" \
|
||||
"--from-literal=IdentityUrl=http://$externalDns/identity" \
|
||||
"--from-literal=IdentityHealthCheckUrl=http://identity/hc" \
|
||||
"--from-literal=OrderingUrl=http://ordering" \
|
||||
"--from-literal=OrderingHealthCheckUrl=http://ordering/hc" \
|
||||
"--from-literal=MvcClientExternalUrl=http://$externalDns/webmvc" \
|
||||
"--from-literal=WebMvcHealthCheckUrl=http://webmvc/hc" \
|
||||
"--from-literal=MvcClientOrderingUrl=http://ordering" \
|
||||
"--from-literal=MvcClientCatalogUrl=http://catalog" \
|
||||
"--from-literal=MvcClientBasketUrl=http://basket" \
|
||||
"--from-literal=MvcClientMarketingUrl=http://marketing" \
|
||||
"--from-literal=MvcClientLocationsUrl=http://locations" \
|
||||
"--from-literal=MarketingHealthCheckUrl=http://marketing/hc" \
|
||||
"--from-literal=WebSpaHealthCheckUrl=http://webspa/hc" \
|
||||
"--from-literal=SpaClientMarketingExternalUrl=http://$externalDns/marketing-api" \
|
||||
"--from-literal=SpaClientOrderingExternalUrl=http://$externalDns/ordering-api" \
|
||||
"--from-literal=SpaClientCatalogExternalUrl=http://$externalDns/catalog-api" \
|
||||
"--from-literal=SpaClientBasketExternalUrl=http://$externalDns/basket-api" \
|
||||
"--from-literal=SpaClientIdentityExternalUrl=http://$externalDns/identity" \
|
||||
"--from-literal=SpaClientLocationsUrl=http://$externalDns/locations-api" \
|
||||
"--from-literal=LocationsHealthCheckUrl=http://locations/hc" \
|
||||
"--from-literal=SpaClientExternalUrl=http://$externalDns" \
|
||||
"--from-literal=LocationApiClient=http://$externalDns/locations-api" \
|
||||
"--from-literal=MarketingApiClient=http://$externalDns/marketing-api" \
|
||||
"--from-literal=BasketApiClient=http://$externalDns/basket-api" \
|
||||
"--from-literal=OrderingApiClient=http://$externalDns/ordering-api" \
|
||||
"--from-literal=PaymentHealthCheckUrl=http://payment/hc"
|
||||
|
||||
kubectl label configmap urls app=eshop
|
||||
|
||||
# externalcfg configmap -- points to local infrastructure components (rabbitmq, SQL Server etc)
|
||||
kubectl create -f conf_local.yml
|
||||
|
||||
# Create application pod deployments
|
||||
kubectl create -f deployments.yaml
|
||||
|
||||
echo "#################### Deploying application pods ####################"
|
||||
|
||||
# update deployments with the correct image (with tag and/or registry)
|
||||
kubectl set image deployments/basket "basket=$container_registry/basket.api:$image_tag"
|
||||
kubectl set image deployments/catalog "catalog=$container_registry/catalog.api:$image_tag"
|
||||
kubectl set image deployments/identity "identity=$container_registry/identity.api:$image_tag"
|
||||
kubectl set image deployments/ordering "ordering=$container_registry/ordering.api:$image_tag"
|
||||
kubectl set image deployments/marketing "marketing=$container_registry/marketing.api:$image_tag"
|
||||
kubectl set image deployments/locations "locations=$container_registry/locations.api:$image_tag"
|
||||
kubectl set image deployments/payment "payment=$container_registry/payment.api:$image_tag"
|
||||
kubectl set image deployments/webmvc "webmvc=$container_registry/webmvc:$image_tag"
|
||||
kubectl set image deployments/webstatus "webstatus=$container_registry/webstatus:$image_tag"
|
||||
kubectl set image deployments/webspa "webspa=$container_registry/webspa:$image_tag"
|
||||
|
||||
kubectl rollout resume deployments/basket
|
||||
kubectl rollout resume deployments/catalog
|
||||
kubectl rollout resume deployments/identity
|
||||
kubectl rollout resume deployments/ordering
|
||||
kubectl rollout resume deployments/marketing
|
||||
kubectl rollout resume deployments/locations
|
||||
kubectl rollout resume deployments/payment
|
||||
kubectl rollout resume deployments/webmvc
|
||||
kubectl rollout resume deployments/webstatus
|
||||
kubectl rollout resume deployments/webspa
|
||||
|
||||
echo "WebSPA is exposed at http://$externalDns, WebMVC at http://$externalDns/webmvc, WebStatus at http://$externalDns/webstatus"
|
||||
echo "eShopOnContainers deployment is DONE"
|
||||
Binary file not shown.
|
Before Width: | Height: | Size: 26 KiB |
Binary file not shown.
|
Before Width: | Height: | Size: 50 KiB |
Binary file not shown.
|
Before Width: | Height: | Size: 31 KiB |
Binary file not shown.
|
Before Width: | Height: | Size: 30 KiB |
@ -1,33 +0,0 @@
|
||||
apiVersion: v1
|
||||
kind: ConfigMap
|
||||
metadata:
|
||||
name: internalurls
|
||||
labels:
|
||||
app: eshop
|
||||
data:
|
||||
# Internal Services & healthchecks
|
||||
basket: http://basket
|
||||
basket__hc: http://basket/hc
|
||||
catalog: http://catalog
|
||||
catalog__hc: http://catalog/hc
|
||||
identity: http://identity
|
||||
identity__hc: http://identity/hc
|
||||
ordering: http://ordering
|
||||
ordering__hc: http://ordering/hc
|
||||
ordering-background: http://ordering-background
|
||||
ordering-background__hc: http://ordering-background/hc
|
||||
marketing: http://marketing
|
||||
marketing__hc: http://marketing/hc
|
||||
locations: http://locations
|
||||
locations__hc: http://locations/hc
|
||||
payment__hc: http://payment/hc
|
||||
mvc__hc: http://webmvc/hc
|
||||
spa__hc: http://webspa/hc
|
||||
# Aggreggators
|
||||
mobileshoppingagg: http://mobileshoppingagg
|
||||
webshoppingagg: http://webshoppingagg
|
||||
# API GWs
|
||||
apigwmm: http://ocelotapigw-mm
|
||||
apigwms: http://ocelotapigw-ms
|
||||
apigwwm: http://ocelotapigw-wm
|
||||
apigwws: http://ocelotapigw-ws
|
||||
@ -1,238 +0,0 @@
|
||||
apiVersion: v1
|
||||
kind: Namespace
|
||||
metadata:
|
||||
name: ingress-nginx
|
||||
|
||||
---
|
||||
|
||||
kind: ConfigMap
|
||||
apiVersion: v1
|
||||
metadata:
|
||||
name: nginx-configuration
|
||||
namespace: ingress-nginx
|
||||
labels:
|
||||
app.kubernetes.io/name: ingress-nginx
|
||||
app.kubernetes.io/part-of: ingress-nginx
|
||||
|
||||
---
|
||||
|
||||
apiVersion: v1
|
||||
kind: ServiceAccount
|
||||
metadata:
|
||||
name: nginx-ingress-serviceaccount
|
||||
namespace: ingress-nginx
|
||||
labels:
|
||||
app.kubernetes.io/name: ingress-nginx
|
||||
app.kubernetes.io/part-of: ingress-nginx
|
||||
|
||||
---
|
||||
apiVersion: rbac.authorization.k8s.io/v1beta1
|
||||
kind: ClusterRole
|
||||
metadata:
|
||||
name: nginx-ingress-clusterrole
|
||||
labels:
|
||||
app.kubernetes.io/name: ingress-nginx
|
||||
app.kubernetes.io/part-of: ingress-nginx
|
||||
rules:
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- configmaps
|
||||
- endpoints
|
||||
- nodes
|
||||
- pods
|
||||
- secrets
|
||||
verbs:
|
||||
- list
|
||||
- watch
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- nodes
|
||||
verbs:
|
||||
- get
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- services
|
||||
verbs:
|
||||
- get
|
||||
- list
|
||||
- watch
|
||||
- apiGroups:
|
||||
- "extensions"
|
||||
resources:
|
||||
- ingresses
|
||||
verbs:
|
||||
- get
|
||||
- list
|
||||
- watch
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- events
|
||||
verbs:
|
||||
- create
|
||||
- patch
|
||||
- apiGroups:
|
||||
- "extensions"
|
||||
resources:
|
||||
- ingresses/status
|
||||
verbs:
|
||||
- update
|
||||
|
||||
---
|
||||
apiVersion: rbac.authorization.k8s.io/v1beta1
|
||||
kind: Role
|
||||
metadata:
|
||||
name: nginx-ingress-role
|
||||
namespace: ingress-nginx
|
||||
labels:
|
||||
app.kubernetes.io/name: ingress-nginx
|
||||
app.kubernetes.io/part-of: ingress-nginx
|
||||
rules:
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- configmaps
|
||||
- pods
|
||||
- secrets
|
||||
- namespaces
|
||||
verbs:
|
||||
- get
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- configmaps
|
||||
resourceNames:
|
||||
# Defaults to "<election-id>-<ingress-class>"
|
||||
# Here: "<ingress-controller-leader>-<nginx>"
|
||||
# This has to be adapted if you change either parameter
|
||||
# when launching the nginx-ingress-controller.
|
||||
- "ingress-controller-leader-nginx"
|
||||
verbs:
|
||||
- get
|
||||
- update
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- configmaps
|
||||
verbs:
|
||||
- create
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- endpoints
|
||||
verbs:
|
||||
- get
|
||||
|
||||
---
|
||||
apiVersion: rbac.authorization.k8s.io/v1beta1
|
||||
kind: RoleBinding
|
||||
metadata:
|
||||
name: nginx-ingress-role-nisa-binding
|
||||
namespace: ingress-nginx
|
||||
labels:
|
||||
app.kubernetes.io/name: ingress-nginx
|
||||
app.kubernetes.io/part-of: ingress-nginx
|
||||
roleRef:
|
||||
apiGroup: rbac.authorization.k8s.io
|
||||
kind: Role
|
||||
name: nginx-ingress-role
|
||||
subjects:
|
||||
- kind: ServiceAccount
|
||||
name: nginx-ingress-serviceaccount
|
||||
namespace: ingress-nginx
|
||||
|
||||
---
|
||||
apiVersion: rbac.authorization.k8s.io/v1beta1
|
||||
kind: ClusterRoleBinding
|
||||
metadata:
|
||||
name: nginx-ingress-clusterrole-nisa-binding
|
||||
labels:
|
||||
app.kubernetes.io/name: ingress-nginx
|
||||
app.kubernetes.io/part-of: ingress-nginx
|
||||
roleRef:
|
||||
apiGroup: rbac.authorization.k8s.io
|
||||
kind: ClusterRole
|
||||
name: nginx-ingress-clusterrole
|
||||
subjects:
|
||||
- kind: ServiceAccount
|
||||
name: nginx-ingress-serviceaccount
|
||||
namespace: ingress-nginx
|
||||
|
||||
---
|
||||
|
||||
apiVersion: extensions/v1beta1
|
||||
kind: Deployment
|
||||
metadata:
|
||||
name: nginx-ingress-controller
|
||||
namespace: ingress-nginx
|
||||
labels:
|
||||
app.kubernetes.io/name: ingress-nginx
|
||||
app.kubernetes.io/part-of: ingress-nginx
|
||||
spec:
|
||||
replicas: 1
|
||||
selector:
|
||||
matchLabels:
|
||||
app.kubernetes.io/name: ingress-nginx
|
||||
app.kubernetes.io/part-of: ingress-nginx
|
||||
template:
|
||||
metadata:
|
||||
labels:
|
||||
app.kubernetes.io/name: ingress-nginx
|
||||
app.kubernetes.io/part-of: ingress-nginx
|
||||
annotations:
|
||||
prometheus.io/port: "10254"
|
||||
prometheus.io/scrape: "true"
|
||||
spec:
|
||||
serviceAccountName: nginx-ingress-serviceaccount
|
||||
containers:
|
||||
- name: nginx-ingress-controller
|
||||
image: quay.io/kubernetes-ingress-controller/nginx-ingress-controller:0.20.0
|
||||
args:
|
||||
- /nginx-ingress-controller
|
||||
- --configmap=$(POD_NAMESPACE)/nginx-configuration
|
||||
- --publish-service=$(POD_NAMESPACE)/ingress-nginx
|
||||
- --annotations-prefix=nginx.ingress.kubernetes.io
|
||||
securityContext:
|
||||
capabilities:
|
||||
drop:
|
||||
- ALL
|
||||
add:
|
||||
- NET_BIND_SERVICE
|
||||
# www-data -> 33
|
||||
runAsUser: 33
|
||||
env:
|
||||
- name: POD_NAME
|
||||
valueFrom:
|
||||
fieldRef:
|
||||
fieldPath: metadata.name
|
||||
- name: POD_NAMESPACE
|
||||
valueFrom:
|
||||
fieldRef:
|
||||
fieldPath: metadata.namespace
|
||||
ports:
|
||||
- name: http
|
||||
containerPort: 80
|
||||
- name: https
|
||||
containerPort: 443
|
||||
livenessProbe:
|
||||
failureThreshold: 3
|
||||
httpGet:
|
||||
path: /healthz
|
||||
port: 10254
|
||||
scheme: HTTP
|
||||
initialDelaySeconds: 10
|
||||
periodSeconds: 10
|
||||
successThreshold: 1
|
||||
timeoutSeconds: 1
|
||||
readinessProbe:
|
||||
failureThreshold: 3
|
||||
httpGet:
|
||||
path: /healthz
|
||||
port: 10254
|
||||
scheme: HTTP
|
||||
periodSeconds: 10
|
||||
successThreshold: 1
|
||||
timeoutSeconds: 1
|
||||
@ -1,12 +0,0 @@
|
||||
kind: Service
|
||||
apiVersion: v1
|
||||
metadata:
|
||||
name: rabbitmq-admin
|
||||
spec:
|
||||
type: NodePort
|
||||
selector:
|
||||
app: rabbitmq
|
||||
ports:
|
||||
- port: 15672
|
||||
nodePort: 31672
|
||||
name: rabbitmq-port
|
||||
@ -1,12 +0,0 @@
|
||||
kind: Service
|
||||
apiVersion: v1
|
||||
metadata:
|
||||
name: sql-service
|
||||
spec:
|
||||
type: NodePort
|
||||
selector:
|
||||
app: sql-data
|
||||
ports:
|
||||
- port: 1433
|
||||
nodePort: 31433
|
||||
name: sql-port
|
||||
@ -1,12 +0,0 @@
|
||||
# Kubernetes (k8s) deploy information
|
||||
|
||||
This folder contains files needed to **create** a ACS with Kubernetes in Azure and to **deploy** eShopServices in a existing Kubernetes:
|
||||
|
||||
- `gen-k8s-env.ps1` Script to create a ACS with Kubernetes in Azure
|
||||
- `deploy.ps1` Script to deploy eShopOnContainers in a existing k8s
|
||||
|
||||
Refer to file [README.k8s.md](./README.k8s.md) for detailed information
|
||||
|
||||
Refer to file [README.CICD.k8s.md](./README.CICD.k8s.md) for information about how to set a VSTS build for deploying on k8s
|
||||
|
||||
Refer to file [conf-files.md](./conf-files.md) for a brief description of every YAML file in this folder
|
||||
@ -1,51 +0,0 @@
|
||||
#!/bin/bash
|
||||
|
||||
declare -x path=$1
|
||||
|
||||
if [ -z "$path" ]; then
|
||||
$path="$(pwd)/../src";
|
||||
echo -e "\e[33mNo path passed. Will use $path"
|
||||
fi
|
||||
|
||||
declare -a projectList=(
|
||||
"$path/Web/WebSPA"
|
||||
"$path/Services/Catalog/Catalog.API"
|
||||
"$path/Services/Basket/Basket.API"
|
||||
"$path/Services/Ordering/Ordering.API"
|
||||
"$path/Services/Identity/Identity.API"
|
||||
"$path/Services/Location/Locations.API"
|
||||
"$path/Services/Marketing/Marketing.API"
|
||||
"$path/Services/Payment/Payment.API"
|
||||
"$path/Web/WebMVC"
|
||||
"$path/Web/WebStatus"
|
||||
)
|
||||
|
||||
# Build SPA app
|
||||
# pushd $(pwd)../src/Web/WebSPA
|
||||
# npm run build:prod
|
||||
|
||||
for project in "${projectList[@]}"
|
||||
do
|
||||
echo -e "\e[33mWorking on $path/$project"
|
||||
echo -e "\e[33m\tRemoving old publish output"
|
||||
pushd $path/$project
|
||||
rm -rf obj/Docker/publish
|
||||
echo -e "\e[33m\tBuilding and publishing $project"
|
||||
dotnet publish -c Release -o obj/Docker/publish --verbosity quiet
|
||||
popd
|
||||
done
|
||||
|
||||
## remove old docker images:
|
||||
#images=$(docker images --filter=reference="eshop/*" -q)
|
||||
#if [ -n "$images" ]; then
|
||||
# docker rm $(docker ps -a -q) -f
|
||||
# echo "Deleting eShop images in local Docker repo"
|
||||
# echo $images
|
||||
# docker rmi $(docker images --filter=reference="eshop/*" -q) -f
|
||||
#fi
|
||||
|
||||
|
||||
# No need to build the images, docker build or docker compose will
|
||||
# do that using the images and containers defined in the docker-compose.yml file.
|
||||
#
|
||||
#
|
||||
@ -1,10 +0,0 @@
|
||||
version: '2'
|
||||
|
||||
services:
|
||||
ci-build:
|
||||
image: microsoft/aspnetcore-build-nightly:1.0-1.1
|
||||
volumes:
|
||||
- .:/src
|
||||
working_dir: /src
|
||||
command: /bin/bash -c "chmod -x ./cli-linux/build-bits-linux.sh && ./cli-linux/build-bits-linux.sh"
|
||||
|
||||
@ -1,4 +0,0 @@
|
||||
# Build SPA app
|
||||
pushd $(pwd)/src/Web/WebSPA
|
||||
npm rebuild node-sass
|
||||
#npm run build:prod
|
||||
@ -1,6 +0,0 @@
|
||||
#!/bin/bash
|
||||
docker stop $(docker ps -a -q)
|
||||
docker rm $(docker ps -a -q)
|
||||
docker images |grep -v REPOSITORY|awk '{print $1}'|xargs -L1 docker pull
|
||||
export ESHOP_PROD_EXTERNAL_DNS_NAME_OR_IP=$(curl ipinfo.io/ip)
|
||||
docker-compose -f docker-compose.images.yml -f docker-compose.prod.yml up -d --force-recreate
|
||||
@ -1,47 +0,0 @@
|
||||
#!/bin/sh
|
||||
|
||||
# List of microservices here needs to be updated to include all the new microservices (Marketing, etc.)
|
||||
|
||||
projectList=(
|
||||
"../src/Web/WebMVC"
|
||||
"../src/Web/WebSPA"
|
||||
"../src/Services/Identity/Identity.API"
|
||||
"../src/Services/Catalog/Catalog.API"
|
||||
"../src/Services/Ordering/Ordering.API"
|
||||
"../src/Services/Basket/Basket.API"
|
||||
"../src/Services/Location/Locations.API"
|
||||
"../src/Services/Marketing/Marketing.API"
|
||||
"../src/Services/Payment/Payment.API"
|
||||
"../src/Web/WebStatus"
|
||||
)
|
||||
|
||||
|
||||
pushd $(pwd)/../src/Web/WebSPA
|
||||
npm install
|
||||
npm rebuild node-sass
|
||||
popd
|
||||
|
||||
for project in "${projectList[@]}"
|
||||
do
|
||||
echo -e "\e[33mWorking on $(pwd)/$project"
|
||||
echo -e "\e[33m\tRemoving old publish output"
|
||||
pushd $(pwd)/$project
|
||||
rm -rf obj/Docker/publish
|
||||
echo -e "\e[33m\tBuilding and publishing projects"
|
||||
dotnet publish -o obj/Docker/publish -c Release
|
||||
popd
|
||||
done
|
||||
|
||||
# remove old docker images:
|
||||
images=$(docker images --filter=reference="eshop/*" -q)
|
||||
if [ -n "$images" ]; then
|
||||
docker rm $(docker ps -a -q) -f
|
||||
echo "Deleting eShop images in local Docker repo"
|
||||
echo $images
|
||||
docker rmi $(docker images --filter=reference="eshop/*" -q) -f
|
||||
fi
|
||||
|
||||
# No need to build the images, docker build or docker compose will
|
||||
# do that using the images and containers defined in the docker-compose.yml file.
|
||||
#
|
||||
#
|
||||
@ -1,17 +0,0 @@
|
||||
# This approach still has issues, but would be the simplest approach for this script
|
||||
# See: https://github.com/dotnet/eShopOnContainers/issues/74
|
||||
|
||||
Param([string] $rootPath)
|
||||
$scriptPath = Split-Path $script:MyInvocation.MyCommand.Path
|
||||
|
||||
Write-Host "Current script directory is $scriptPath" -ForegroundColor Yellow
|
||||
|
||||
if ([string]::IsNullOrEmpty($rootPath)) {
|
||||
$rootPath = "$scriptPath\.."
|
||||
}
|
||||
Write-Host "Root path used is $rootPath" -ForegroundColor Yellow
|
||||
|
||||
$SolutionFilePath = [IO.Path]::Combine($rootPath, "eShopOnContainers-ServicesAndWebApps.sln")
|
||||
|
||||
dotnet publish $SolutionFilePath -c Release -o .\obj\Docker\publish
|
||||
|
||||
@ -1,59 +0,0 @@
|
||||
Param([string] $rootPath)
|
||||
$scriptPath = Split-Path $script:MyInvocation.MyCommand.Path
|
||||
|
||||
Write-Host "Current script directory is $scriptPath" -ForegroundColor Yellow
|
||||
|
||||
if ([string]::IsNullOrEmpty($rootPath)) {
|
||||
$rootPath = "$scriptPath\.."
|
||||
}
|
||||
Write-Host "Root path used is $rootPath" -ForegroundColor Yellow
|
||||
|
||||
workflow BuildAndPublish {
|
||||
param ([string] $rootPath
|
||||
)
|
||||
$projectPaths =
|
||||
@{Path="$rootPath\src\Web\WebMVC";Prj="WebMVC.csproj"},
|
||||
@{Path="$rootPath\src\Web\WebSPA";Prj="WebSPA.csproj"},
|
||||
@{Path="$rootPath\src\Services\Identity\Identity.API";Prj="Identity.API.csproj"},
|
||||
@{Path="$rootPath\src\Services\Catalog\Catalog.API";Prj="Catalog.API.csproj"},
|
||||
@{Path="$rootPath\src\Services\Ordering\Ordering.API";Prj="Ordering.API.csproj"},
|
||||
@{Path="$rootPath\src\Services\Basket\Basket.API";Prj="Basket.API.csproj"},
|
||||
@{Path="$rootPath\src\Services\Location\Locations.API";Prj="Locations.API.csproj"},
|
||||
@{Path="$rootPath\src\Services\Marketing\Marketing.API";Prj="Marketing.API.csproj"},
|
||||
@{Path="$rootPath\src\Services\Payment\Payment.API";Prj="Payment.API.csproj"},
|
||||
@{Path="$rootPath\src\Web\WebStatus";Prj="WebStatus.csproj"}
|
||||
|
||||
foreach -parallel ($item in $projectPaths) {
|
||||
$projectPath = $item.Path
|
||||
$projectFile = $item.Prj
|
||||
$outPath = $item.Path + "\obj\Docker\publish"
|
||||
$projectPathAndFile = "$projectPath\$projectFile"
|
||||
#Write-Host "Deleting old publish files in $outPath" -ForegroundColor Yellow
|
||||
remove-item -path $outPath -Force -Recurse -ErrorAction SilentlyContinue
|
||||
#Write-Host "Publishing $projectPathAndFile to $outPath" -ForegroundColor Yellow
|
||||
dotnet publish $projectPathAndFile -o $outPath -c Release
|
||||
}
|
||||
}
|
||||
|
||||
BuildAndPublish $rootPath
|
||||
|
||||
########################################################################################
|
||||
# Delete old eShop Docker images
|
||||
########################################################################################
|
||||
|
||||
$imagesToDelete = docker images --filter=reference="eshop/*" -q
|
||||
|
||||
If (-Not $imagesToDelete) {Write-Host "Not deleting eShop images as there are no eShop images in the current local Docker repo."}
|
||||
Else
|
||||
{
|
||||
# Delete all containers
|
||||
Write-Host "Deleting all containers in local Docker Host"
|
||||
docker rm $(docker ps -a -q) -f
|
||||
|
||||
# Delete all eshop images
|
||||
Write-Host "Deleting eShop images in local Docker repo"
|
||||
Write-Host $imagesToDelete
|
||||
docker rmi $(docker images --filter=reference="eshop/*" -q) -f
|
||||
}
|
||||
|
||||
# WE DON'T NEED DOCKER BUILD AS WE CAN RUN "DOCKER-COMPOSE BUILD" OR "DOCKER-COMPOSE UP" AND IT WILL BUILD ALL THE IMAGES IN THE .YML FOR US
|
||||
@ -1,11 +0,0 @@
|
||||
Param([string] $imageTag)
|
||||
|
||||
$scriptPath = Split-Path $script:MyInvocation.MyCommand.Path
|
||||
|
||||
if ([string]::IsNullOrEmpty($imageTag)) {
|
||||
$imageTag = $(git rev-parse --abbrev-ref HEAD)
|
||||
}
|
||||
|
||||
Write-Host "Building images with tag $imageTag" -ForegroundColor Yellow
|
||||
$env:TAG=$imageTag
|
||||
docker-compose -f "$scriptPath\..\docker-compose.yml" -f "$scriptPath\..\docker-compose.windows.yml" build
|
||||
@ -1,27 +0,0 @@
|
||||
$imagesToDelete = docker images --filter=reference="eshop/*" -q
|
||||
|
||||
If (-Not $imagesToDelete) {Write-Host "Not deleting eShop images as there are no eShop images in the current local Docker repo."}
|
||||
Else
|
||||
{
|
||||
# Delete all containers
|
||||
Write-Host "Deleting all containers in local Docker Host"
|
||||
docker rm $(docker ps -a -q) -f
|
||||
|
||||
# Delete all eshop images
|
||||
Write-Host "Deleting eShop images in local Docker repo"
|
||||
Write-Host $imagesToDelete
|
||||
docker rmi $(docker images --filter=reference="eshop/*" -q) -f
|
||||
}
|
||||
|
||||
|
||||
# DELETE ALL IMAGES AND CONTAINERS
|
||||
|
||||
# Delete all containers
|
||||
# docker rm $(docker ps -a -q) -f
|
||||
|
||||
# Delete all images
|
||||
# docker rmi $(docker images -q)
|
||||
|
||||
#Filter by image name (Has to be complete, cannot be a wildcard)
|
||||
#docker ps -q --filter=ancestor=eshop/identity.api:dev
|
||||
|
||||
@ -1,46 +0,0 @@
|
||||
# Delete all containers
|
||||
Write-Host "Deleting all running containers in the local Docker Host"
|
||||
docker rm $(docker ps -a -q) -f
|
||||
|
||||
$eShopImagesToDelete = docker images --filter=reference="eshop/*" -q
|
||||
If (-Not $eShopImagesToDelete) {Write-Host "Not deleting eShop images as there are no eShop images in the current local Docker repo."}
|
||||
Else
|
||||
{
|
||||
# Delete all eshop images
|
||||
Write-Host "Deleting eShop images in local Docker repo"
|
||||
Write-Host $eShopImagesToDelete
|
||||
docker rmi $(docker images --filter=reference="eshop/*" -q) -f
|
||||
}
|
||||
|
||||
$VSImagesToDelete = docker images --filter=reference="catalog.api:dev" -q
|
||||
If (-Not $VSImagesToDelete) {Write-Host "Not deleting VS images as there are no VS images in the current local Docker repo."}
|
||||
Else
|
||||
{
|
||||
# Delete all eshop images
|
||||
Write-Host "Deleting images created by VS in local Docker repo"
|
||||
Write-Host $VSImagesToDelete
|
||||
docker rmi $(docker images --filter=reference="*:dev" -q) -f
|
||||
|
||||
#docker rmi $(docker images --filter=reference="eshop/payment.api:dev" -q) -f
|
||||
#docker rmi $(docker images --filter=reference="eshop/webspa:dev" -q) -f
|
||||
#docker rmi $(docker images --filter=reference="eshop/webmvc:dev" -q) -f
|
||||
#docker rmi $(docker images --filter=reference="eshop/catalog.api:dev" -q) -f
|
||||
#docker rmi $(docker images --filter=reference="eshop/marketing.api:dev" -q) -f
|
||||
#docker rmi $(docker images --filter=reference="eshop/ordering.api:dev" -q) -f
|
||||
#docker rmi $(docker images --filter=reference="eshop/basket.api:dev" -q) -f
|
||||
#docker rmi $(docker images --filter=reference="eshop/identity.api:dev" -q) -f
|
||||
#docker rmi $(docker images --filter=reference="eshop/locations.api:dev" -q) -f
|
||||
#docker rmi $(docker images --filter=reference="eshop/webstatus:dev" -q) -f
|
||||
}
|
||||
|
||||
# DELETE ALL IMAGES AND CONTAINERS
|
||||
|
||||
# Delete all containers
|
||||
# docker rm $(docker ps -a -q) -f
|
||||
|
||||
# Delete all images
|
||||
# docker rmi $(docker images -q)
|
||||
|
||||
#Filter by image name (Has to be complete, cannot be a wildcard)
|
||||
#docker ps -q --filter=ancestor=eshop/identity.api:dev
|
||||
|
||||
@ -1,11 +0,0 @@
|
||||
Param([string] $rootPath)
|
||||
$scriptPath = Split-Path $script:MyInvocation.MyCommand.Path
|
||||
|
||||
Write-Host "Current script directory is $scriptPath" -ForegroundColor Yellow
|
||||
|
||||
if ([string]::IsNullOrEmpty($rootPath)) {
|
||||
$rootPath = "$scriptPath\.."
|
||||
}
|
||||
Write-Host "Root path used is $rootPath" -ForegroundColor Yellow
|
||||
|
||||
docker-compose -f "$rootPath\docker-compose-external.yml" -f "$rootPath\docker-compose-external.override.yml" up
|
||||
@ -1,33 +0,0 @@
|
||||
# rootPath: Root path of the repo (where docker-compose*.yml are). If not passed ../cli-windows/ is assumed
|
||||
# buildBits: If the projects must be built before. Default value: $true
|
||||
# customEventBusLoginPassword: If a custom RabbitMQ image is used that do not use the default user login/pwd. Default: $false (means assume use default spring2/rabbitmq image)
|
||||
|
||||
Param(
|
||||
[parameter(Mandatory=$false)][string] $rootPath,
|
||||
[parameter(Mandatory=$false)][bool] $customEventBusLoginPassword=$false,
|
||||
[parameter(Mandatory=$false)][bool]$buildBits=$false
|
||||
)
|
||||
|
||||
$scriptPath = Split-Path $script:MyInvocation.MyCommand.Path
|
||||
if ([string]::IsNullOrEmpty($rootPath)) {
|
||||
$rootPath = "$scriptPath\.."
|
||||
}
|
||||
Write-Host "Root path used is $rootPath" -ForegroundColor Yellow
|
||||
|
||||
|
||||
if ($buildBits) {
|
||||
& $scriptPath\build-bits.ps1 -rootPath $rootPath
|
||||
}
|
||||
|
||||
|
||||
$env:ESHOP_EXTERNAL_DNS_NAME_OR_IP = "10.0.75.1"
|
||||
$env:ESHOP_AZURE_STORAGE_CATALOG_URL ="http://10.0.75.1:5101/api/v1/catalog/items/[0]/pic/"
|
||||
$env:ESHOP_AZURE_STORAGE_MARKETING_URL ="http://10.0.75.1:5110/api/v1/campaigns/[0]/pic/"
|
||||
$env:ESHOP_OCELOT_VOLUME_SPEC ="C:\app\configuration"
|
||||
|
||||
if (-Not $customEventBusLoginPassword) {
|
||||
docker-compose -f "$rootPath\docker-compose.yml" -f "$rootPath\docker-compose.override.yml" -f "$rootPath\docker-compose.windows.yml" -f "$rootPath\docker-compose.override.windows.yml" up
|
||||
}
|
||||
else {
|
||||
docker-compose -f "$rootPath\docker-compose.yml" -f "$rootPath\docker-compose.override.yml" -f "$rootPath\docker-compose.windows.yml" up
|
||||
}
|
||||
@ -1,56 +0,0 @@
|
||||
Param([string] $rootPath)
|
||||
$scriptPath = Split-Path $script:MyInvocation.MyCommand.Path
|
||||
|
||||
Write-Host "Current script directory is $scriptPath" -ForegroundColor Yellow
|
||||
|
||||
if ([string]::IsNullOrEmpty($rootPath)) {
|
||||
$rootPath = "$scriptPath\..\.."
|
||||
}
|
||||
Write-Host "Root path used is $rootPath" -ForegroundColor Yellow
|
||||
|
||||
|
||||
$projectPaths =
|
||||
@{Path="$rootPath\src\Web\WebMVC";Prj="WebMVC.csproj"},
|
||||
@{Path="$rootPath\src\Web\WebSPA";Prj="WebSPA.csproj"},
|
||||
@{Path="$rootPath\src\Services\Identity\Identity.API";Prj="Identity.API.csproj"},
|
||||
@{Path="$rootPath\src\Services\Catalog\Catalog.API";Prj="Catalog.API.csproj"},
|
||||
@{Path="$rootPath\src\Services\Ordering\Ordering.API";Prj="Ordering.API.csproj"},
|
||||
@{Path="$rootPath\src\Services\Basket\Basket.API";Prj="Basket.API.csproj"},
|
||||
@{Path="$rootPath\src\Services\Location\Locations.API";Prj="Locations.API.csproj"},
|
||||
@{Path="$rootPath\src\Services\Marketing\Marketing.API";Prj="Marketing.API.csproj"},
|
||||
@{Path="$rootPath\src\Services\Payment\Payment.API";Prj="Payment.API.csproj"},
|
||||
@{Path="$rootPath\src\Web\WebStatus";Prj="WebStatus.csproj"}
|
||||
|
||||
$projectPaths | foreach {
|
||||
$projectPath = $_.Path
|
||||
$projectFile = $_.Prj
|
||||
$outPath = $_.Path + "\obj\Docker\publish"
|
||||
$projectPathAndFile = "$projectPath\$projectFile"
|
||||
Write-Host "Deleting old publish files in $outPath" -ForegroundColor Yellow
|
||||
remove-item -path $outPath -Force -Recurse -ErrorAction SilentlyContinue
|
||||
Write-Host "Publishing $projectPathAndFile to $outPath" -ForegroundColor Yellow
|
||||
dotnet restore $projectPathAndFile
|
||||
dotnet build $projectPathAndFile
|
||||
dotnet publish $projectPathAndFile -o $outPath
|
||||
}
|
||||
|
||||
########################################################################################
|
||||
# Delete old eShop Docker images
|
||||
########################################################################################
|
||||
|
||||
$imagesToDelete = docker images --filter=reference="eshop/*" -q
|
||||
|
||||
If (-Not $imagesToDelete) {Write-Host "Not deleting eShop images as there are no eShop images in the current local Docker repo."}
|
||||
Else
|
||||
{
|
||||
# Delete all containers
|
||||
Write-Host "Deleting all containers in local Docker Host"
|
||||
docker rm $(docker ps -a -q) -f
|
||||
|
||||
# Delete all eshop images
|
||||
Write-Host "Deleting eShop images in local Docker repo"
|
||||
Write-Host $imagesToDelete
|
||||
docker rmi $(docker images --filter=reference="eshop/*" -q) -f
|
||||
}
|
||||
|
||||
# WE DON'T NEED DOCKER BUILD AS WE CAN RUN "DOCKER-COMPOSE BUILD" OR "DOCKER-COMPOSE UP" AND IT WILL BUILD ALL THE IMAGES IN THE .YML FOR US
|
||||
Loading…
x
Reference in New Issue
Block a user