Merge branch 'dev'
@ -5,15 +5,11 @@
|
||||
.vs
|
||||
.vscode
|
||||
docker-compose*.yml
|
||||
docker-compose.dcproj
|
||||
*.sln
|
||||
!eShopOnContainers-ServicesAndWebApps.sln
|
||||
*.md
|
||||
hosts
|
||||
LICENSE
|
||||
*.testsettings
|
||||
vsts-docs
|
||||
test
|
||||
ServiceFabric
|
||||
readme
|
||||
k8s
|
||||
@ -31,4 +27,13 @@ cli-linux
|
||||
**/wwwroot/lib/*
|
||||
global.json
|
||||
**/appsettings.localhost.json
|
||||
src/Web/WebSPA/wwwroot/
|
||||
src/Web/WebSPA/wwwroot/
|
||||
packages/
|
||||
csproj-files/
|
||||
test-results/
|
||||
TestResults/
|
||||
src/Mobile/
|
||||
src/Web/Catalog.WebForms/
|
||||
src/Web/WebMonolithic/
|
||||
src/BuildingBlocks/CommandBus/
|
||||
src/Services/Marketing/Infrastructure/
|
||||
12
.gitignore
vendored
@ -26,6 +26,9 @@ bld/
|
||||
# Visual Studio 2015 cache/options directory
|
||||
.vs/
|
||||
|
||||
# Dockerfile projects folder for restore-packages script
|
||||
csproj-files/
|
||||
|
||||
# .js files created on build:
|
||||
src/Web/WebMVC/wwwroot/js/site*
|
||||
|
||||
@ -42,6 +45,8 @@ src/Web/WebMVC/wwwroot/js/site*
|
||||
*.VisualState.xml
|
||||
TestResult.xml
|
||||
|
||||
tests-results/
|
||||
|
||||
# Build Results of an ATL Project
|
||||
[Dd]ebugPS/
|
||||
[Rr]eleasePS/
|
||||
@ -269,4 +274,9 @@ pub/
|
||||
.mfractor
|
||||
|
||||
# Ignore HealthCheckdb
|
||||
*healthchecksdb*
|
||||
*healthchecksdb*
|
||||
|
||||
# Ignores all extra inf.yaml and app.yaml that are copied by prepare-devspaces.ps1
|
||||
src/**/app.yaml
|
||||
src/**/inf.yaml
|
||||
|
||||
|
||||
111
README.md
@ -1,72 +1,28 @@
|
||||
# eShopOnContainers - Microservices Architecture and Containers based Reference Application (**BETA state** - Visual Studio 2017 and CLI environments compatible)
|
||||
# eShopOnContainers - Microservices Architecture and Containers based Reference Application (**BETA state** - Visual Studio and CLI environments compatible)
|
||||
Sample .NET Core reference application, powered by Microsoft, based on a simplified microservices architecture and Docker containers.
|
||||
|
||||
## Linux Build Status for 'dev' branch
|
||||
|
||||
Dev branch contains the latest "stable" code, and their images are tagged with `:dev` in our [Docker Hub](https://cloud.docker.com/u/eshop/repository/list):
|
||||
|
||||
Api Gateways base image
|
||||
| Basket API | Catalog API | Identity API | Location API |
|
||||
| ------------- | ------------- | ------------- | ------------- |
|
||||
| [](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=199&branchName=dev) | [](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=197&branchName=dev) | [](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=200&branchName=dev) | [](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=202&branchName=dev) |
|
||||
|
||||
[](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=201&branchName=dev)
|
||||
| Marketing API | Ordering API | Payment API | Api Gateways base image |
|
||||
| ------------- | ------------- | ------------- | ------------- |
|
||||
| [](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=203&branchName=dev) | [](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=198&branchName=dev) | [](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=205&branchName=dev) | [](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=201&branchName=dev)
|
||||
|
||||
Basket API
|
||||
|
||||
[](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=199&branchName=dev)
|
||||
|
||||
Catalog API
|
||||
|
||||
[](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=197&branchName=dev)
|
||||
|
||||
Identity API
|
||||
|
||||
[](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=200&branchName=dev)
|
||||
|
||||
Location API
|
||||
|
||||
[](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=202&branchName=dev)
|
||||
|
||||
Marketing API
|
||||
|
||||
[](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=203&branchName=dev)
|
||||
|
||||
Ordering API
|
||||
|
||||
[](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=198&branchName=dev)
|
||||
|
||||
Payment API
|
||||
|
||||
[](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=205&branchName=dev)
|
||||
|
||||
Webhooks API
|
||||
|
||||
[](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=207&branchName=dev)
|
||||
|
||||
Web Shopping Aggregator
|
||||
|
||||
[](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=206&branchName=dev)
|
||||
|
||||
Mobile Shopping Aggregator
|
||||
|
||||
[](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=204&branchName=dev)
|
||||
|
||||
Webbhooks demo client
|
||||
|
||||
[](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=208&branchName=dev)
|
||||
|
||||
WebMVC Client
|
||||
|
||||
[](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=209&branchName=dev)
|
||||
|
||||
WebSPA Client
|
||||
|
||||
[](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=210&branchName=dev)
|
||||
|
||||
Web Status
|
||||
|
||||
[](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=211&branchName=dev)
|
||||
| Web Shopping Aggregator | Mobile Shopping Aggregator | WebMVC Client | WebSPA Client |
|
||||
| ------------- | ------------- | ------------- | ------------- |
|
||||
| [](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=206&branchName=dev) | [](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=204&branchName=dev) | [](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=209&branchName=dev) | [](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=210&branchName=dev) |
|
||||
|
||||
| Web Status | Webhooks API | Webbhooks demo client |
|
||||
| ------------- | ------------- | ------------- |
|
||||
[](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=211&branchName=dev) | [](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=207&branchName=dev) | [](https://msftdevtools.visualstudio.com/eShopOnContainers/_build/latest?definitionId=208&branchName=dev) |
|
||||
|
||||
## IMPORTANT NOTES!
|
||||
|
||||
**You can use either the latest version of Visual Studio or simply Docker CLI and .NET CLI for Windows, Mac and Linux**.
|
||||
|
||||
**Note for Pull Requests (PRs)**: We accept pull request from the community. When doing it, please do it onto the **DEV branch** which is the consolidated work-in-progress branch. Do not request it onto Master branch, if possible.
|
||||
@ -74,7 +30,14 @@ Web Status
|
||||
**NEWS / ANNOUNCEMENTS**
|
||||
Do you want to be up-to-date on .NET Architecture guidance and reference apps like eShopOnContainers? --> Subscribe by "WATCHING" this new GitHub repo: https://github.com/dotnet-architecture/News
|
||||
|
||||
## Update to .NET Core 3
|
||||
|
||||
> There's currently an update to .NET Core 3 going on in the branch [features/migration-dotnet3](https://github.com/dotnet-architecture/eShopOnContainers/tree/features/migration-dotnet3).
|
||||
>
|
||||
> You can monitor this branch, but it's being changed frequently, community contributions will be accepted once it's officially released.
|
||||
|
||||
## Updated for .NET Core 2.2 "wave" of technologies
|
||||
|
||||
eShopOnContainers is updated to .NET Core 2.x (currently updated to 2.2) "wave" of technologies. Not just compilation but also new recommended code in EF Core, ASP.NET Core, and other new related versions.
|
||||
|
||||
The **dockerfiles** in the solution have also been updated and now support [**Docker Multi-Stage**](https://blogs.msdn.microsoft.com/stevelasker/2017/09/11/net-and-multistage-dockerfiles/) since mid-December 2017.
|
||||
@ -82,6 +45,7 @@ The **dockerfiles** in the solution have also been updated and now support [**Do
|
||||
>**PLEASE** Read our [branch guide](./branch-guide.md) to know about our branching policy
|
||||
|
||||
> ### DISCLAIMER
|
||||
>
|
||||
> **IMPORTANT:** The current state of this sample application is **BETA**, because we are constantly evolving towards newly released technologies. Therefore, many areas could be improved and change significantly while refactoring the current code and implementing new features. Feedback with improvements and pull requests from the community will be highly appreciated and accepted.
|
||||
>
|
||||
> This reference application proposes a simplified microservice oriented architecture implementation to introduce technologies like .NET Core with Docker containers through a comprehensive application. The chosen domain is eShop/eCommerce but simply because it is a well-known domain by most people/developers.
|
||||
@ -91,11 +55,11 @@ However, this sample application should not be considered as an "eCommerce refer
|
||||
|
||||
|
||||
|
||||
> Read the planned <a href='https://github.com/dotnet/eShopOnContainers/wiki/01.-Roadmap-and-Milestones-for-future-releases'>Roadmap and Milestones for future releases of eShopOnContainers</a> within the Wiki for further info about possible new implementations and provide feedback at the <a href='https://github.com/dotnet/eShopOnContainers/issues'>ISSUES section</a> if you'd like to see any specific scenario implemented or improved. Also, feel free to discuss on any current issue.
|
||||
> Read the planned <a href='https://github.com/dotnet-architecture/eShopOnContainers/wiki/Roadmap'>Roadmap</a> within the Wiki for further info about possible new implementations and provide feedback at the <a href='https://github.com/dotnet/eShopOnContainers/issues'>ISSUES section</a> if you'd like to see any specific scenario implemented or improved. Also, feel free to discuss on any current issue.
|
||||
|
||||
### Architecture overview
|
||||
This reference application is cross-platform at the server and client side, thanks to .NET Core services capable of running on Linux or Windows containers depending on your Docker host, and to Xamarin for mobile apps running on Android, iOS or Windows/UWP plus any browser for the client web apps.
|
||||
The architecture proposes a microservice oriented architecture implementation with multiple autonomous microservices (each one owning its own data/db) and implementing different approaches within each microservice (simple CRUD vs. DDD/CQRS patterns) using Http as the communication protocol between the client apps and the microservices and supports asynchronous communication for data updates propagation across multiple services based on Integration Events and an Event Bus (a light message broker, to choose between RabbitMQ or Azure Service Bus, underneath) plus other features defined at the <a href='https://github.com/dotnet/eShopOnContainers/wiki/01.-Roadmap-and-Milestones-for-future-releases'>roadmap</a>.
|
||||
The architecture proposes a microservice oriented architecture implementation with multiple autonomous microservices (each one owning its own data/db) and implementing different approaches within each microservice (simple CRUD vs. DDD/CQRS patterns) using Http as the communication protocol between the client apps and the microservices and supports asynchronous communication for data updates propagation across multiple services based on Integration Events and an Event Bus (a light message broker, to choose between RabbitMQ or Azure Service Bus, underneath) plus other features defined at the <a href='https://github.com/dotnet-architecture/eShopOnContainers/wiki/Roadmap'>roadmap</a>.
|
||||
<p>
|
||||
<img src="img/eshop_logo.png">
|
||||
<img src="https://user-images.githubusercontent.com/1712635/38758862-d4b42498-3f27-11e8-8dad-db60b0fa05d3.png">
|
||||
@ -125,6 +89,12 @@ The architecture proposes a microservice oriented architecture implementation wi
|
||||
> <p> A similar case is defined in regard to Redis cache running as a container for the development environment. Or a No-SQL database (MongoDB) running as a container.
|
||||
> <p> However, in a real production environment it is recommended to have your databases (SQL Server, Redis, and the NO-SQL database, in this case) in HA (High Available) services like Azure SQL Database, Redis as a service and Azure CosmosDB instead the MongoDB container (as both systems share the same access protocol). If you want to change to a production configuration, you'll just need to change the connection strings once you have set up the servers in an HA cloud or on-premises.
|
||||
|
||||
> ### Important Note on EventBus
|
||||
> In this solution's current EventBus is a simplified implementation, mainly used for learning purposes (development and testing), so it doesn't handle all production scenarios, most notably on error handling. <p>
|
||||
> The following forks provide production environment level implementation examples with eShopOnContainers :
|
||||
> * Implementation with [NServiceBus](https://github.com/Particular/NServiceBus) : https://github.com/Particular/eShopOnContainers
|
||||
> * Implementation with [CAP](https://github.com/dotnetcore/CAP) : https://github.com/yang-xiaodong/eShopOnContainers
|
||||
|
||||
## Related documentation and guidance
|
||||
While developing this reference application, we've been creating a reference <b>Guide/eBook</b> focusing on <b>architecting and developing containerized and microservice based .NET Applications</b> (download link available below) which explains in detail how to develop this kind of architectural style (microservices, Docker containers, Domain-Driven Design for certain microservices) plus other simpler architectural styles, like monolithic apps that can also live as Docker containers.
|
||||
<p>
|
||||
@ -168,25 +138,20 @@ Finally, those microservices are consumed by multiple client web and mobile apps
|
||||
<img src="img/xamarin-mobile-App.png">
|
||||
|
||||
## Setting up your development environment for eShopOnContainers
|
||||
### Visual Studio 2017 and Windows based
|
||||
This is the more straightforward way to get started:
|
||||
https://github.com/dotnet-architecture/eShopOnContainers/wiki/02.-Setting-eShopOnContainers-in-a-Visual-Studio-2017-environment
|
||||
|
||||
### CLI and Windows based
|
||||
For those who prefer the CLI on Windows, using dotnet CLI, docker CLI and VS Code for Windows:
|
||||
https://github.com/dotnet/eShopOnContainers/wiki/03.-Setting-the-eShopOnContainers-solution-up-in-a-Windows-CLI-environment-(dotnet-CLI,-Docker-CLI-and-VS-Code)
|
||||
### Windows based (CLI and Visual Studio)
|
||||
|
||||
### CLI and Mac based
|
||||
For those who prefer the CLI on a Mac, using dotnet CLI, docker CLI and VS Code for Mac:
|
||||
https://github.com/dotnet-architecture/eShopOnContainers/wiki/04.-Setting-eShopOnContainer-solution-up-in-a-Mac,-VS-for-Mac-or-with-CLI-environment--(dotnet-CLI,-Docker-CLI-and-VS-Code)
|
||||
<https://github.com/dotnet-architecture/eShopOnContainers/wiki/Windows-setup>
|
||||
|
||||
### Mac based (CLI ans Visual Studio for Mac)
|
||||
|
||||
<https://github.com/dotnet-architecture/eShopOnContainers/wiki/Mac-setup>
|
||||
|
||||
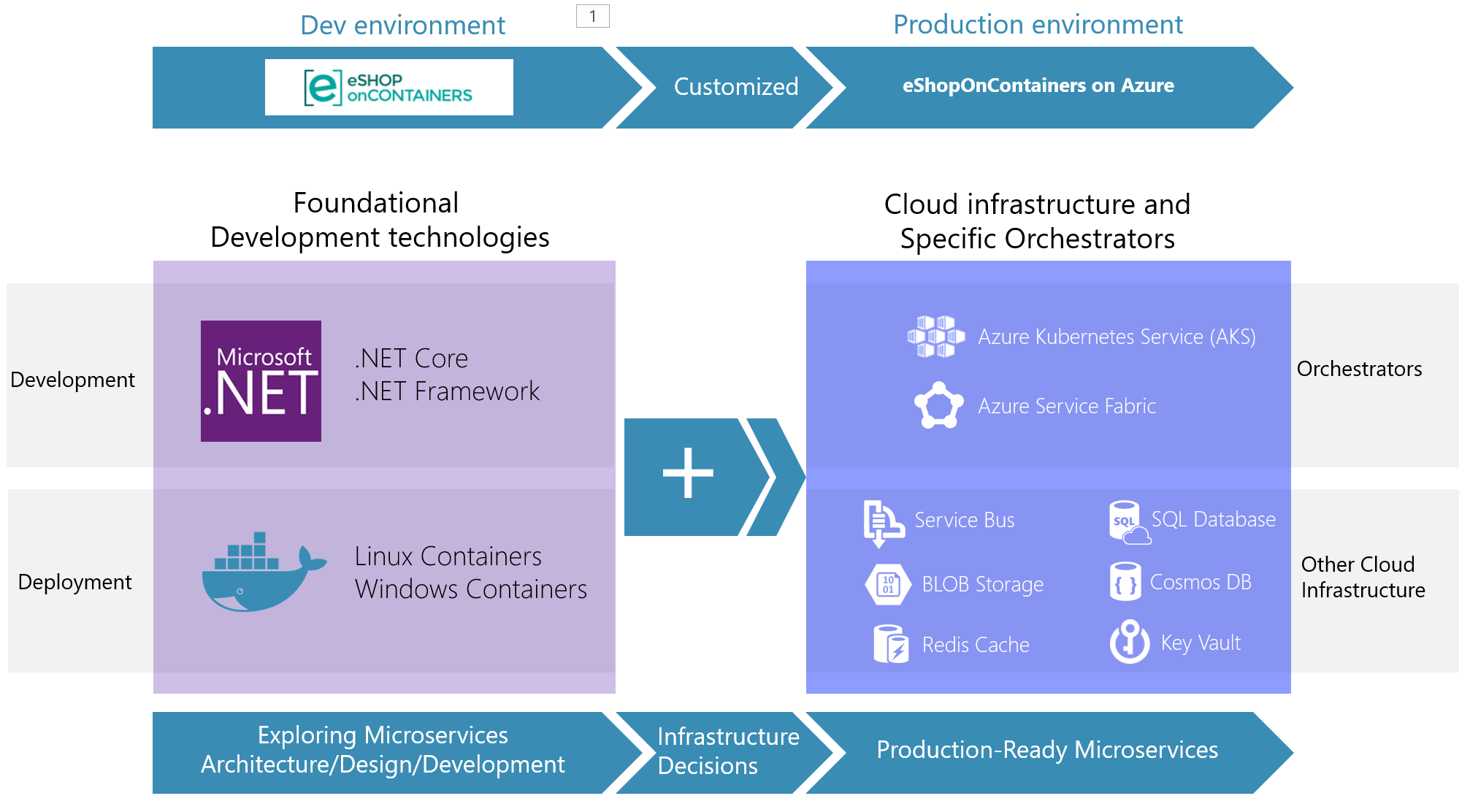
## Orchestrators: Kubernetes and Service Fabric
|
||||
|
||||
See at the [Wiki](https://github.com/dotnet-architecture/eShopOnContainers/wiki) the posts on setup/instructions about how to deploy to Kubernetes or Service Fabric in Azure (although you could also deploy to any other cloud or on-premises).
|
||||
|
||||
## Sending feedback and pull requests
|
||||
|
||||
As mentioned, we'd appreciate your feedback, improvements and ideas.
|
||||
You can create new issues at the issues section, do pull requests and/or send emails to **eshop_feedback@service.microsoft.com**
|
||||
|
||||
## Questions
|
||||
[QUESTION] Answer +1 if the solution is working for you (Through VS2017 or CLI environment):
|
||||
https://github.com/dotnet/eShopOnContainers/issues/107
|
||||
|
||||
@ -1,5 +1,3 @@
|
||||
pool:
|
||||
vmImage: 'ubuntu-16.04'
|
||||
variables:
|
||||
registryEndpoint: eshop-registry
|
||||
trigger:
|
||||
@ -17,34 +15,15 @@ trigger:
|
||||
exclude:
|
||||
- src/ApiGateways/Mobile.Bff.Shopping/aggregator/*
|
||||
- src/ApiGateways/Web.Bff.Shopping/aggregator/*
|
||||
steps:
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose build apigws
|
||||
inputs:
|
||||
dockerComposeCommand: 'build mobileshoppingapigw mobilemarketingapigw webshoppingapigw webmarketingapigw'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose push apigws
|
||||
inputs:
|
||||
dockerComposeCommand: 'push mobileshoppingapigw mobilemarketingapigw webshoppingapigw webmarketingapigw'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: CopyFiles@2
|
||||
inputs:
|
||||
sourceFolder: $(Build.SourcesDirectory)/k8s/helm
|
||||
targetFolder: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- task: PublishBuildArtifacts@1
|
||||
inputs:
|
||||
pathtoPublish: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
artifactName: helm
|
||||
jobs:
|
||||
- template: ../buildimages.yaml
|
||||
parameters:
|
||||
services: mobileshoppingapigw mobilemarketingapigw webshoppingapigw webmarketingapigw
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
helmfrom: $(Build.SourcesDirectory)/k8s/helm
|
||||
helmto: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- template: ../multiarch.yaml
|
||||
parameters:
|
||||
image: ocelotapigw
|
||||
branch: $(Build.SourceBranchName)
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
|
||||
@ -1,5 +1,3 @@
|
||||
pool:
|
||||
vmImage: 'ubuntu-16.04'
|
||||
variables:
|
||||
registryEndpoint: eshop-registry
|
||||
trigger:
|
||||
@ -12,34 +10,15 @@ trigger:
|
||||
- src/BuildingBlocks/*
|
||||
- src/Services/Basket/*
|
||||
- k8s/helm/basket-api/*
|
||||
steps:
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose build basket
|
||||
inputs:
|
||||
dockerComposeCommand: 'build basket.api'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose push basket
|
||||
inputs:
|
||||
dockerComposeCommand: 'push basket.api'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: CopyFiles@2
|
||||
inputs:
|
||||
sourceFolder: $(Build.SourcesDirectory)/k8s/helm
|
||||
targetFolder: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- task: PublishBuildArtifacts@1
|
||||
inputs:
|
||||
pathtoPublish: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
artifactName: helm
|
||||
jobs:
|
||||
- template: ../buildimages.yaml
|
||||
parameters:
|
||||
services: basket.api
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
helmfrom: $(Build.SourcesDirectory)/k8s/helm
|
||||
helmto: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- template: ../multiarch.yaml
|
||||
parameters:
|
||||
image: basket.api
|
||||
branch: $(Build.SourceBranchName)
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
|
||||
92
build/azure-devops/buildimages.yaml
Normal file
@ -0,0 +1,92 @@
|
||||
parameters:
|
||||
services: ''
|
||||
registryEndpoint: ''
|
||||
helmfrom: ''
|
||||
helmto: ''
|
||||
|
||||
jobs:
|
||||
- job: BuildContainersForPR_Linux
|
||||
condition: eq('${{ variables['Build.Reason'] }}', 'PullRequest')
|
||||
pool:
|
||||
vmImage: 'ubuntu-16.04'
|
||||
steps:
|
||||
- bash: docker-compose build ${{ parameters.services }}
|
||||
displayName: Create multiarch manifest
|
||||
env:
|
||||
TAG: ${{ variables['Build.SourceBranchName'] }}
|
||||
- job: BuildContainersForPR_Windows
|
||||
condition: eq('${{ variables['Build.Reason'] }}', 'PullRequest')
|
||||
pool:
|
||||
vmImage: 'windows-2019'
|
||||
steps:
|
||||
- bash: docker-compose build ${{ parameters.services }}
|
||||
displayName: Create multiarch manifest
|
||||
env:
|
||||
TAG: ${{ variables['Build.SourceBranchName'] }}
|
||||
PLATFORM: win
|
||||
NODE_IMAGE: stefanscherer/node-windows:10
|
||||
- job: BuildLinux
|
||||
condition: ne('${{ variables['Build.Reason'] }}', 'PullRequest')
|
||||
pool:
|
||||
vmImage: 'ubuntu-16.04'
|
||||
steps:
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose build ${{ parameters.services }}
|
||||
inputs:
|
||||
dockerComposeCommand: 'build ${{ parameters.services }}'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: ${{ parameters.registryEndpoint }}
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=${{ variables['Build.SourceBranchName'] }}
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose push ${{ parameters.images }}
|
||||
inputs:
|
||||
dockerComposeCommand: 'push ${{ parameters.services }}'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: ${{ parameters.registryEndpoint }}
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=${{ variables['Build.SourceBranchName'] }}
|
||||
- task: CopyFiles@2
|
||||
inputs:
|
||||
sourceFolder: ${{ parameters.helmfrom }}
|
||||
targetFolder: ${{ parameters.helmto }}
|
||||
- task: PublishBuildArtifacts@1
|
||||
inputs:
|
||||
pathtoPublish: ${{ parameters.helmto }}
|
||||
artifactName: helm
|
||||
- job: BuildWindows
|
||||
condition: ne('${{ variables['Build.Reason'] }}', 'PullRequest')
|
||||
pool:
|
||||
vmImage: 'windows-2019'
|
||||
steps:
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose build ${{ parameters.services }}
|
||||
inputs:
|
||||
dockerComposeCommand: 'build ${{ parameters.services }}'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: ${{ parameters.registryEndpoint }}
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=${{ variables['Build.SourceBranchName'] }}
|
||||
PLATFORM=win
|
||||
NODE_IMAGE=stefanscherer/node-windows:10
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose push ${{ parameters.services }}
|
||||
inputs:
|
||||
dockerComposeCommand: 'push ${{ parameters.services }}'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: ${{ parameters.registryEndpoint }}
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=${{ variables['Build.SourceBranchName'] }}
|
||||
PLATFORM=win
|
||||
@ -1,5 +1,3 @@
|
||||
pool:
|
||||
vmImage: 'ubuntu-16.04'
|
||||
variables:
|
||||
registryEndpoint: eshop-registry
|
||||
trigger:
|
||||
@ -12,34 +10,15 @@ trigger:
|
||||
- src/BuildingBlocks/*
|
||||
- src/Services/Catalog/*
|
||||
- k8s/helm/catalog-api/*
|
||||
steps:
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose build catalog
|
||||
inputs:
|
||||
dockerComposeCommand: 'build catalog.api'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose push catalog
|
||||
inputs:
|
||||
dockerComposeCommand: 'push catalog.api'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: CopyFiles@2
|
||||
inputs:
|
||||
sourceFolder: $(Build.SourcesDirectory)/k8s/helm
|
||||
targetFolder: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- task: PublishBuildArtifacts@1
|
||||
inputs:
|
||||
pathtoPublish: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
artifactName: helm
|
||||
jobs:
|
||||
- template: ../buildimages.yaml
|
||||
parameters:
|
||||
services: catalog.api
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
helmfrom: $(Build.SourcesDirectory)/k8s/helm
|
||||
helmto: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- template: ../multiarch.yaml
|
||||
parameters:
|
||||
image: catalog.api
|
||||
branch: $(Build.SourceBranchName)
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
|
||||
@ -1,5 +1,3 @@
|
||||
pool:
|
||||
vmImage: 'ubuntu-16.04'
|
||||
variables:
|
||||
registryEndpoint: eshop-registry
|
||||
trigger:
|
||||
@ -12,34 +10,15 @@ trigger:
|
||||
- src/BuildingBlocks/*
|
||||
- src/Services/Identity/*
|
||||
- k8s/helm/identity-api/*
|
||||
steps:
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose build identity
|
||||
inputs:
|
||||
dockerComposeCommand: 'build identity.api'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose push identity
|
||||
inputs:
|
||||
dockerComposeCommand: 'push identity.api'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: CopyFiles@2
|
||||
inputs:
|
||||
sourceFolder: $(Build.SourcesDirectory)/k8s/helm
|
||||
targetFolder: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- task: PublishBuildArtifacts@1
|
||||
inputs:
|
||||
pathtoPublish: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
artifactName: helm
|
||||
jobs:
|
||||
- template: ../buildimages.yaml
|
||||
parameters:
|
||||
services: identity.api
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
helmfrom: $(Build.SourcesDirectory)/k8s/helm
|
||||
helmto: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- template: ../multiarch.yaml
|
||||
parameters:
|
||||
image: identity.api
|
||||
branch: $(Build.SourceBranchName)
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
|
||||
25
build/azure-devops/infrastructure/azure-pipelines.yml
Normal file
@ -0,0 +1,25 @@
|
||||
pool:
|
||||
vmImage: 'ubuntu-16.04'
|
||||
variables:
|
||||
registryEndpoint: eshop-registry
|
||||
trigger:
|
||||
branches:
|
||||
include:
|
||||
- master
|
||||
- dev
|
||||
paths:
|
||||
include:
|
||||
- k8s/helm/basket-data/*
|
||||
- k8s/helm/keystore-data/*
|
||||
- k8s/helm/nosql-data/*
|
||||
- k8s/helm/rabbitmq/*
|
||||
- k8s/helm/sql-data/*
|
||||
steps:
|
||||
- task: CopyFiles@2
|
||||
inputs:
|
||||
sourceFolder: $(Build.SourcesDirectory)/k8s/helm
|
||||
targetFolder: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- task: PublishBuildArtifacts@1
|
||||
inputs:
|
||||
pathtoPublish: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
artifactName: helm
|
||||
@ -1,5 +1,3 @@
|
||||
pool:
|
||||
vmImage: 'ubuntu-16.04'
|
||||
variables:
|
||||
registryEndpoint: eshop-registry
|
||||
trigger:
|
||||
@ -11,35 +9,16 @@ trigger:
|
||||
include:
|
||||
- src/BuildingBlocks/*
|
||||
- src/Services/Location/*
|
||||
- k8s/helm/locations-api/*
|
||||
steps:
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose build locations
|
||||
inputs:
|
||||
dockerComposeCommand: 'build locations.api'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose push locations
|
||||
inputs:
|
||||
dockerComposeCommand: 'push locations.api'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: CopyFiles@2
|
||||
inputs:
|
||||
sourceFolder: $(Build.SourcesDirectory)/k8s/helm
|
||||
targetFolder: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- task: PublishBuildArtifacts@1
|
||||
inputs:
|
||||
pathtoPublish: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
artifactName: helm
|
||||
- k8s/helm/locations-api/*
|
||||
jobs:
|
||||
- template: ../buildimages.yaml
|
||||
parameters:
|
||||
services: locations.api
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
helmfrom: $(Build.SourcesDirectory)/k8s/helm
|
||||
helmto: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- template: ../multiarch.yaml
|
||||
parameters:
|
||||
image: locations.api
|
||||
branch: $(Build.SourceBranchName)
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
|
||||
@ -1,5 +1,3 @@
|
||||
pool:
|
||||
vmImage: 'ubuntu-16.04'
|
||||
variables:
|
||||
registryEndpoint: eshop-registry
|
||||
trigger:
|
||||
@ -11,35 +9,16 @@ trigger:
|
||||
include:
|
||||
- src/BuildingBlocks/*
|
||||
- src/Services/Marketing/*
|
||||
- k8s/helm/marketing-api/*
|
||||
steps:
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose build marketing
|
||||
inputs:
|
||||
dockerComposeCommand: 'build marketing.api'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose push marketing
|
||||
inputs:
|
||||
dockerComposeCommand: 'push marketing.api'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: CopyFiles@2
|
||||
inputs:
|
||||
sourceFolder: $(Build.SourcesDirectory)/k8s/helm
|
||||
targetFolder: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- task: PublishBuildArtifacts@1
|
||||
inputs:
|
||||
pathtoPublish: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
artifactName: helm
|
||||
- k8s/helm/marketing-api/*
|
||||
jobs:
|
||||
- template: ../buildimages.yaml
|
||||
parameters:
|
||||
services: marketing.api
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
helmfrom: $(Build.SourcesDirectory)/k8s/helm
|
||||
helmto: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- template: ../multiarch.yaml
|
||||
parameters:
|
||||
image: marketing.api
|
||||
branch: $(Build.SourceBranchName)
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
|
||||
@ -1,5 +1,3 @@
|
||||
pool:
|
||||
vmImage: 'ubuntu-16.04'
|
||||
variables:
|
||||
registryEndpoint: eshop-registry
|
||||
trigger:
|
||||
@ -10,35 +8,17 @@ trigger:
|
||||
paths:
|
||||
include:
|
||||
- src/ApiGateways/Mobile.Bff.Shopping/aggregator/*
|
||||
- k8s/helm/mobileshoppingagg/*
|
||||
steps:
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose build mobileshoppingagg
|
||||
inputs:
|
||||
dockerComposeCommand: 'build mobileshoppingagg'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose push mobileshoppingagg
|
||||
inputs:
|
||||
dockerComposeCommand: 'push mobileshoppingagg'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: CopyFiles@2
|
||||
inputs:
|
||||
sourceFolder: $(Build.SourcesDirectory)/k8s/helm
|
||||
targetFolder: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- task: PublishBuildArtifacts@1
|
||||
inputs:
|
||||
pathtoPublish: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
artifactName: helm
|
||||
- k8s/helm/mobileshoppingagg/*
|
||||
jobs:
|
||||
- template: ../buildimages.yaml
|
||||
parameters:
|
||||
services: mobileshoppingagg
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
helmfrom: $(Build.SourcesDirectory)/k8s/helm
|
||||
helmto: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- template: ../multiarch.yaml
|
||||
parameters:
|
||||
image: mobileshoppingagg
|
||||
branch: $(Build.SourceBranchName)
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
|
||||
|
||||
30
build/azure-devops/multiarch.yaml
Normal file
@ -0,0 +1,30 @@
|
||||
parameters:
|
||||
image: ''
|
||||
branch: ''
|
||||
registry: 'eshop'
|
||||
registryEndpoint: ''
|
||||
|
||||
jobs:
|
||||
- job: manifest
|
||||
condition: and(succeeded(),ne('${{ variables['Build.Reason'] }}', 'PullRequest'))
|
||||
dependsOn:
|
||||
- BuildWindows
|
||||
- BuildLinux
|
||||
pool:
|
||||
vmImage: 'Ubuntu 16.04'
|
||||
steps:
|
||||
- task: Docker@1
|
||||
displayName: Docker Login
|
||||
inputs:
|
||||
command: login
|
||||
containerregistrytype: 'Container Registry'
|
||||
dockerRegistryEndpoint: ${{ parameters.registryEndpoint }}
|
||||
- bash: |
|
||||
mkdir -p ~/.docker
|
||||
sed '$ s/.$//' $DOCKER_CONFIG/config.json > ~/.docker/config.json
|
||||
echo ',"experimental": "enabled" }' >> ~/.docker/config.json
|
||||
docker --config ~/.docker manifest create ${{ parameters.registry }}/${{ parameters.image }}:${{ parameters.branch }} ${{ parameters.registry }}/${{ parameters.image }}:linux-${{ parameters.branch }} ${{ parameters.registry }}/${{ parameters.image }}:win-${{ parameters.branch }}
|
||||
docker --config ~/.docker manifest create ${{ parameters.registry }}/${{ parameters.image }}:latest ${{ parameters.registry }}/${{ parameters.image }}:linux-latest ${{ parameters.registry }}/${{ parameters.image }}:win-latest
|
||||
docker --config ~/.docker manifest push ${{ parameters.registry }}/${{ parameters.image }}:${{ parameters.branch }}
|
||||
docker --config ~/.docker manifest push ${{ parameters.registry }}/${{ parameters.image }}:latest
|
||||
displayName: Create multiarch manifest
|
||||
@ -1,5 +1,3 @@
|
||||
pool:
|
||||
vmImage: 'ubuntu-16.04'
|
||||
variables:
|
||||
registryEndpoint: eshop-registry
|
||||
trigger:
|
||||
@ -14,34 +12,15 @@ trigger:
|
||||
- k8s/helm/ordering-api/*
|
||||
- k8s/helm/ordering-backgroundtasks/*
|
||||
- k8s/helm/ordering-signalrhub/*
|
||||
steps:
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose build ordering
|
||||
inputs:
|
||||
dockerComposeCommand: 'build ordering.api ordering.backgroundtasks ordering.signalrhub'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose push ordering
|
||||
inputs:
|
||||
dockerComposeCommand: 'push ordering.api ordering.backgroundtasks ordering.signalrhub'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: CopyFiles@2
|
||||
inputs:
|
||||
sourceFolder: $(Build.SourcesDirectory)/k8s/helm
|
||||
targetFolder: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- task: PublishBuildArtifacts@1
|
||||
inputs:
|
||||
pathtoPublish: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
artifactName: helm
|
||||
jobs:
|
||||
- template: ../buildimages.yaml
|
||||
parameters:
|
||||
services: ordering.api
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
helmfrom: $(Build.SourcesDirectory)/k8s/helm
|
||||
helmto: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- template: ../multiarch.yaml
|
||||
parameters:
|
||||
image: ordering.api
|
||||
branch: $(Build.SourceBranchName)
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
@ -1,5 +1,3 @@
|
||||
pool:
|
||||
vmImage: 'ubuntu-16.04'
|
||||
variables:
|
||||
registryEndpoint: eshop-registry
|
||||
trigger:
|
||||
@ -12,34 +10,15 @@ trigger:
|
||||
- src/BuildingBlocks/*
|
||||
- src/Services/Payment/*
|
||||
- k8s/helm/payment-api/*
|
||||
steps:
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose build payment
|
||||
inputs:
|
||||
dockerComposeCommand: 'build payment.api'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose push payment
|
||||
inputs:
|
||||
dockerComposeCommand: 'push payment.api'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: CopyFiles@2
|
||||
inputs:
|
||||
sourceFolder: $(Build.SourcesDirectory)/k8s/helm
|
||||
targetFolder: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- task: PublishBuildArtifacts@1
|
||||
inputs:
|
||||
pathtoPublish: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
artifactName: helm
|
||||
jobs:
|
||||
- template: ../buildimages.yaml
|
||||
parameters:
|
||||
services: payment.api
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
helmfrom: $(Build.SourcesDirectory)/k8s/helm
|
||||
helmto: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- template: ../multiarch.yaml
|
||||
parameters:
|
||||
image: payment.api
|
||||
branch: $(Build.SourceBranchName)
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
@ -1,5 +1,3 @@
|
||||
pool:
|
||||
vmImage: 'ubuntu-16.04'
|
||||
variables:
|
||||
registryEndpoint: eshop-registry
|
||||
trigger:
|
||||
@ -10,35 +8,16 @@ trigger:
|
||||
paths:
|
||||
include:
|
||||
- src/ApiGateways/Web.Bff.Shopping/aggregator/*
|
||||
- k8s/helm/webshoppingagg/*
|
||||
steps:
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose build webshoppingagg
|
||||
inputs:
|
||||
dockerComposeCommand: 'build webshoppingagg'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose push webshoppingagg
|
||||
inputs:
|
||||
dockerComposeCommand: 'push webshoppingagg'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: CopyFiles@2
|
||||
inputs:
|
||||
sourceFolder: $(Build.SourcesDirectory)/k8s/helm
|
||||
targetFolder: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- task: PublishBuildArtifacts@1
|
||||
inputs:
|
||||
pathtoPublish: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
artifactName: helm
|
||||
- k8s/helm/webshoppingagg/*
|
||||
jobs:
|
||||
- template: ../buildimages.yaml
|
||||
parameters:
|
||||
services: webshoppingagg
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
helmfrom: $(Build.SourcesDirectory)/k8s/helm
|
||||
helmto: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- template: ../multiarch.yaml
|
||||
parameters:
|
||||
image: webshoppingagg
|
||||
branch: $(Build.SourceBranchName)
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
@ -1,5 +1,3 @@
|
||||
pool:
|
||||
vmImage: 'ubuntu-16.04'
|
||||
variables:
|
||||
registryEndpoint: eshop-registry
|
||||
trigger:
|
||||
@ -11,35 +9,16 @@ trigger:
|
||||
include:
|
||||
- src/BuildingBlocks/*
|
||||
- src/Services/Webhooks/*
|
||||
- k8s/helm/webhooks-api/*
|
||||
steps:
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose build webhooks
|
||||
inputs:
|
||||
dockerComposeCommand: 'build webhooks.api'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose push webhooks
|
||||
inputs:
|
||||
dockerComposeCommand: 'push webhooks.api'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: CopyFiles@2
|
||||
inputs:
|
||||
sourceFolder: $(Build.SourcesDirectory)/k8s/helm
|
||||
targetFolder: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- task: PublishBuildArtifacts@1
|
||||
inputs:
|
||||
pathtoPublish: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
artifactName: helm
|
||||
- k8s/helm/webhooks-api/*
|
||||
jobs:
|
||||
- template: ../buildimages.yaml
|
||||
parameters:
|
||||
services: webhooks.api
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
helmfrom: $(Build.SourcesDirectory)/k8s/helm
|
||||
helmto: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- template: ../multiarch.yaml
|
||||
parameters:
|
||||
image: webhooks.api
|
||||
branch: $(Build.SourceBranchName)
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
@ -1,5 +1,3 @@
|
||||
pool:
|
||||
vmImage: 'ubuntu-16.04'
|
||||
variables:
|
||||
registryEndpoint: eshop-registry
|
||||
trigger:
|
||||
@ -11,35 +9,16 @@ trigger:
|
||||
include:
|
||||
- src/BuildingBlocks/*
|
||||
- src/Web/WebhookClient/*
|
||||
- k8s/helm/webhooks-web/*
|
||||
steps:
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose build webhooks.client
|
||||
inputs:
|
||||
dockerComposeCommand: 'build webhooks.client'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose push webhooks.client
|
||||
inputs:
|
||||
dockerComposeCommand: 'push webhooks.client'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: CopyFiles@2
|
||||
inputs:
|
||||
sourceFolder: $(Build.SourcesDirectory)/k8s/helm
|
||||
targetFolder: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- task: PublishBuildArtifacts@1
|
||||
inputs:
|
||||
pathtoPublish: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
artifactName: helm
|
||||
- k8s/helm/webhooks-web/*
|
||||
jobs:
|
||||
- template: ../buildimages.yaml
|
||||
parameters:
|
||||
services: webhooks.client
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
helmfrom: $(Build.SourcesDirectory)/k8s/helm
|
||||
helmto: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- template: ../multiarch.yaml
|
||||
parameters:
|
||||
image: webhooks.client
|
||||
branch: $(Build.SourceBranchName)
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
@ -1,5 +1,3 @@
|
||||
pool:
|
||||
vmImage: 'ubuntu-16.04'
|
||||
variables:
|
||||
registryEndpoint: eshop-registry
|
||||
trigger:
|
||||
@ -11,35 +9,16 @@ trigger:
|
||||
include:
|
||||
- src/BuildingBlocks/*
|
||||
- src/Web/WebMVC/*
|
||||
- k8s/helm/webmvc/*
|
||||
steps:
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose build webmvc
|
||||
inputs:
|
||||
dockerComposeCommand: 'build webmvc'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose push webmvc
|
||||
inputs:
|
||||
dockerComposeCommand: 'push webmvc'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: CopyFiles@2
|
||||
inputs:
|
||||
sourceFolder: $(Build.SourcesDirectory)/k8s/helm
|
||||
targetFolder: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- task: PublishBuildArtifacts@1
|
||||
inputs:
|
||||
pathtoPublish: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
artifactName: helm
|
||||
- k8s/helm/webmvc/*
|
||||
jobs:
|
||||
- template: ../buildimages.yaml
|
||||
parameters:
|
||||
services: webmvc
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
helmfrom: $(Build.SourcesDirectory)/k8s/helm
|
||||
helmto: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- template: ../multiarch.yaml
|
||||
parameters:
|
||||
image: webmvc
|
||||
branch: $(Build.SourceBranchName)
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
@ -1,5 +1,3 @@
|
||||
pool:
|
||||
vmImage: 'ubuntu-16.04'
|
||||
variables:
|
||||
registryEndpoint: eshop-registry
|
||||
trigger:
|
||||
@ -12,34 +10,15 @@ trigger:
|
||||
- src/BuildingBlocks/*
|
||||
- src/Web/WebSPA/*
|
||||
- k8s/helm/webspa/*
|
||||
steps:
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose build webspa
|
||||
inputs:
|
||||
dockerComposeCommand: 'build webspa'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose push webspa
|
||||
inputs:
|
||||
dockerComposeCommand: 'push webspa'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: CopyFiles@2
|
||||
inputs:
|
||||
sourceFolder: $(Build.SourcesDirectory)/k8s/helm
|
||||
targetFolder: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- task: PublishBuildArtifacts@1
|
||||
inputs:
|
||||
pathtoPublish: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
artifactName: helm
|
||||
jobs:
|
||||
- template: ../buildimages.yaml
|
||||
parameters:
|
||||
services: webspa
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
helmfrom: $(Build.SourcesDirectory)/k8s/helm
|
||||
helmto: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- template: ../multiarch.yaml
|
||||
parameters:
|
||||
image: webspa
|
||||
branch: $(Build.SourceBranchName)
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
@ -1,5 +1,3 @@
|
||||
pool:
|
||||
vmImage: 'ubuntu-16.04'
|
||||
variables:
|
||||
registryEndpoint: eshop-registry
|
||||
trigger:
|
||||
@ -11,35 +9,16 @@ trigger:
|
||||
include:
|
||||
- src/BuildingBlocks/*
|
||||
- src/Web/WebStatus/*
|
||||
- k8s/helm/webstatus/*
|
||||
steps:
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose build webstatus
|
||||
inputs:
|
||||
dockerComposeCommand: 'build webstatus'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: DockerCompose@0
|
||||
displayName: Compose push webstatus
|
||||
inputs:
|
||||
dockerComposeCommand: 'push webstatus'
|
||||
containerregistrytype: Container Registry
|
||||
dockerRegistryEndpoint: $(registryEndpoint)
|
||||
dockerComposeFile: docker-compose.yml
|
||||
qualifyImageNames: true
|
||||
projectName: ""
|
||||
dockerComposeFileArgs: |
|
||||
TAG=$(Build.SourceBranchName)
|
||||
- task: CopyFiles@2
|
||||
inputs:
|
||||
sourceFolder: $(Build.SourcesDirectory)/k8s/helm
|
||||
targetFolder: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- task: PublishBuildArtifacts@1
|
||||
inputs:
|
||||
pathtoPublish: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
artifactName: helm
|
||||
- k8s/helm/webstatus/*
|
||||
jobs:
|
||||
- template: ../buildimages.yaml
|
||||
parameters:
|
||||
services: webstatus
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
helmfrom: $(Build.SourcesDirectory)/k8s/helm
|
||||
helmto: $(Build.ArtifactStagingDirectory)/k8s/helm
|
||||
- template: ../multiarch.yaml
|
||||
parameters:
|
||||
image: webstatus
|
||||
branch: $(Build.SourceBranchName)
|
||||
registryEndpoint: $(registryEndpoint)
|
||||
26
build/multiarch-manifests/create-manifests.ps1
Normal file
@ -0,0 +1,26 @@
|
||||
Param(
|
||||
[parameter(Mandatory=$true)][string]$registry
|
||||
)
|
||||
|
||||
if ([String]::IsNullOrEmpty($registry)) {
|
||||
Write-Host "Registry must be set to docker registry to use" -ForegroundColor Red
|
||||
exit 1
|
||||
}
|
||||
|
||||
Write-Host "This script creates the local manifests, for pushing the multi-arch manifests" -ForegroundColor Yellow
|
||||
Write-Host "Tags used are linux-master, win-master, linux-dev, win-dev, linux-latest, win-latest" -ForegroundColor Yellow
|
||||
Write-Host "Multiarch images tags will be master, dev, latest" -ForegroundColor Yellow
|
||||
|
||||
|
||||
$services = "identity.api", "basket.api", "catalog.api", "ordering.api", "ordering.backgroundtasks", "marketing.api", "payment.api", "locations.api", "webhooks.api", "ocelotapigw", "mobileshoppingagg", "webshoppingagg", "ordering.signalrhub", "webstatus", "webspa", "webmvc", "webhooks.client"
|
||||
|
||||
foreach ($svc in $services) {
|
||||
Write-Host "Creating manifest for $svc and tags :latest, :master, and :dev"
|
||||
docker manifest create $registry/${svc}:master $registry/${svc}:linux-master $registry/${svc}:win-master
|
||||
docker manifest create $registry/${svc}:dev $registry/${svc}:linux-dev $registry/${svc}:win-dev
|
||||
docker manifest create $registry/${svc}:latest $registry/${svc}:linux-latest $registry/${svc}:win-latest
|
||||
Write-Host "Pushing manifest for $svc and tags :latest, :master, and :dev"
|
||||
docker manifest push $registry/${svc}:latest
|
||||
docker manifest push $registry/${svc}:dev
|
||||
docker manifest push $registry/${svc}:master
|
||||
}
|
||||
2
cli-windows/set-dockernat-networkategory-to-private.ps1
Normal file
@ -0,0 +1,2 @@
|
||||
#Requires -RunAsAdministrator
|
||||
Get-NetConnectionProfile | Where-Object { $_.InterfaceAlias -match "(DockerNAT)" } | ForEach-Object { Set-NetConnectionProfile -InterfaceIndex $_.InterfaceIndex -NetworkCategory Private }
|
||||
37
docker-compose.elk.yml
Normal file
@ -0,0 +1,37 @@
|
||||
version: '3.4'
|
||||
|
||||
services:
|
||||
|
||||
elasticsearch:
|
||||
build:
|
||||
context: elk/elasticsearch/
|
||||
volumes:
|
||||
- ./elk/elasticsearch/config/elasticsearch.yml:/usr/share/elasticsearch/config/elasticsearch.yml:ro
|
||||
ports:
|
||||
- "9200:9200"
|
||||
- "9300:9300"
|
||||
environment:
|
||||
ES_JAVA_OPTS: "-Xmx256m -Xms256m"
|
||||
|
||||
logstash:
|
||||
build:
|
||||
context: elk/logstash/
|
||||
volumes:
|
||||
- ./elk/logstash/config/logstash.yml:/usr/share/logstash/config/logstash.yml:ro
|
||||
- ./elk/logstash/pipeline:/usr/share/logstash/pipeline:ro
|
||||
ports:
|
||||
- "8080:8080"
|
||||
environment:
|
||||
LS_JAVA_OPTS: "-Xmx256m -Xms256m"
|
||||
depends_on:
|
||||
- elasticsearch
|
||||
|
||||
kibana:
|
||||
build:
|
||||
context: elk/kibana/
|
||||
volumes:
|
||||
- ./elk/kibana/config/:/usr/share/kibana/config:ro
|
||||
ports:
|
||||
- "5601:5601"
|
||||
depends_on:
|
||||
- elasticsearch
|
||||
@ -110,6 +110,8 @@ services:
|
||||
- ApplicationInsights__InstrumentationKey=${INSTRUMENTATION_KEY}
|
||||
- OrchestratorType=${ORCHESTRATOR_TYPE}
|
||||
- UseLoadTest=${USE_LOADTEST:-False}
|
||||
- Serilog__MinimumLevel__Override__Microsoft.eShopOnContainers.BuildingBlocks.EventBusRabbitMQ=Verbose
|
||||
- Serilog__MinimumLevel__Override__Ordering.API=Verbose
|
||||
ports:
|
||||
- "5102:80" # Important: In a production environment your should remove the external port (5102) kept here for microservice debugging purposes.
|
||||
# The API Gateway redirects and access through the internal port (80).
|
||||
@ -130,6 +132,7 @@ services:
|
||||
- ApplicationInsights__InstrumentationKey=${INSTRUMENTATION_KEY}
|
||||
- OrchestratorType=${ORCHESTRATOR_TYPE}
|
||||
- UseLoadTest=${USE_LOADTEST:-False}
|
||||
- Serilog__MinimumLevel__Override__Microsoft.eShopOnContainers.BuildingBlocks.EventBusRabbitMQ=Verbose
|
||||
ports:
|
||||
- "5111:80"
|
||||
|
||||
@ -168,6 +171,8 @@ services:
|
||||
- AzureServiceBusEnabled=False
|
||||
- ApplicationInsights__InstrumentationKey=${INSTRUMENTATION_KEY}
|
||||
- OrchestratorType=${ORCHESTRATOR_TYPE}
|
||||
- Serilog__MinimumLevel__Override__Payment.API.IntegrationEvents.EventHandling=Verbose
|
||||
- Serilog__MinimumLevel__Override__Microsoft.eShopOnContainers.BuildingBlocks.EventBusRabbitMQ=Verbose
|
||||
ports:
|
||||
- "5108:80" # Important: In a production environment your should remove the external port (5108) kept here for microservice debugging purposes.
|
||||
# The API Gateway redirects and access through the internal port (80).
|
||||
@ -326,40 +331,40 @@ services:
|
||||
environment:
|
||||
- ASPNETCORE_ENVIRONMENT=Production
|
||||
- ASPNETCORE_URLS=http://0.0.0.0:80
|
||||
- HealthChecks-UI__HealthChecks__1__Name=WebMVC HTTP Check
|
||||
- HealthChecks-UI__HealthChecks__1__Uri=http://webmvc/hc
|
||||
- HealthChecks-UI__HealthChecks__2__Name=WebSPA HTTP Check
|
||||
- HealthChecks-UI__HealthChecks__2__Uri=http://webspa/hc
|
||||
- HealthChecks-UI__HealthChecks__3__Name=Web Shopping Aggregator GW HTTP Check
|
||||
- HealthChecks-UI__HealthChecks__3__Uri=http://webshoppingagg/hc
|
||||
- HealthChecks-UI__HealthChecks__4__Name=Mobile Shopping Aggregator HTTP Check
|
||||
- HealthChecks-UI__HealthChecks__4__Uri=http://mobileshoppingagg/hc
|
||||
- HealthChecks-UI__HealthChecks__5__Name=Mobile Shopping API GW HTTP Check
|
||||
- HealthChecks-UI__HealthChecks__5__Uri=http://mobileshoppingapigw/hc
|
||||
- HealthChecks-UI__HealthChecks__6__Name=Mobile Marketing API GW HTTP Check
|
||||
- HealthChecks-UI__HealthChecks__6__Uri=http://mobilemarketingapigw/hc
|
||||
- HealthChecks-UI__HealthChecks__7__Name=Web Shopping API GW HTTP Check
|
||||
- HealthChecks-UI__HealthChecks__7__Uri=http://webshoppingapigw/hc
|
||||
- HealthChecks-UI__HealthChecks__8__Name=Web Marketing API GW HTTP Check
|
||||
- HealthChecks-UI__HealthChecks__8__Uri=http://webmarketingapigw/hc
|
||||
- HealthChecks-UI__HealthChecks__9__Name=Ordering HTTP Check
|
||||
- HealthChecks-UI__HealthChecks__9__Uri=http://ordering.api/hc
|
||||
- HealthChecks-UI__HealthChecks__10__Name=Ordering HTTP Background Check
|
||||
- HealthChecks-UI__HealthChecks__10__Uri=http://ordering.backgroundtasks/hc
|
||||
- HealthChecks-UI__HealthChecks__11__Name=Basket HTTP Check
|
||||
- HealthChecks-UI__HealthChecks__11__Uri=http://basket.api/hc
|
||||
- HealthChecks-UI__HealthChecks__12__Name=Catalog HTTP Check
|
||||
- HealthChecks-UI__HealthChecks__12__Uri=http://catalog.api/hc
|
||||
- HealthChecks-UI__HealthChecks__13__Name=Identity HTTP Check
|
||||
- HealthChecks-UI__HealthChecks__13__Uri=http://identity.api/hc
|
||||
- HealthChecks-UI__HealthChecks__14__Name=Marketing HTTP Check
|
||||
- HealthChecks-UI__HealthChecks__14__Uri=http://marketing.api/hc
|
||||
- HealthChecks-UI__HealthChecks__15__Name=Locations HTTP Check
|
||||
- HealthChecks-UI__HealthChecks__15__Uri=http://locations.api/hc
|
||||
- HealthChecks-UI__HealthChecks__16__Name=Payments HTTP Check
|
||||
- HealthChecks-UI__HealthChecks__16__Uri=http://payment.api/hc
|
||||
- HealthChecks-UI__HealthChecks__17__Name=Ordering SignalRHub HTTP Check
|
||||
- HealthChecks-UI__HealthChecks__17__Uri=http://ordering.signalrhub/hc
|
||||
- HealthChecksUI__HealthChecks__0__Name=WebMVC HTTP Check
|
||||
- HealthChecksUI__HealthChecks__0__Uri=http://webmvc/hc
|
||||
- HealthChecksUI__HealthChecks__1__Name=WebSPA HTTP Check
|
||||
- HealthChecksUI__HealthChecks__1__Uri=http://webspa/hc
|
||||
- HealthChecksUI__HealthChecks__2__Name=Web Shopping Aggregator GW HTTP Check
|
||||
- HealthChecksUI__HealthChecks__2__Uri=http://webshoppingagg/hc
|
||||
- HealthChecksUI__HealthChecks__3__Name=Mobile Shopping Aggregator HTTP Check
|
||||
- HealthChecksUI__HealthChecks__3__Uri=http://mobileshoppingagg/hc
|
||||
- HealthChecksUI__HealthChecks__4__Name=Mobile Shopping API GW HTTP Check
|
||||
- HealthChecksUI__HealthChecks__4__Uri=http://mobileshoppingapigw/hc
|
||||
- HealthChecksUI__HealthChecks__5__Name=Mobile Marketing API GW HTTP Check
|
||||
- HealthChecksUI__HealthChecks__5__Uri=http://mobilemarketingapigw/hc
|
||||
- HealthChecksUI__HealthChecks__6__Name=Web Shopping API GW HTTP Check
|
||||
- HealthChecksUI__HealthChecks__6__Uri=http://webshoppingapigw/hc
|
||||
- HealthChecksUI__HealthChecks__7__Name=Web Marketing API GW HTTP Check
|
||||
- HealthChecksUI__HealthChecks__7__Uri=http://webmarketingapigw/hc
|
||||
- HealthChecksUI__HealthChecks__8__Name=Ordering HTTP Check
|
||||
- HealthChecksUI__HealthChecks__8__Uri=http://ordering.api/hc
|
||||
- HealthChecksUI__HealthChecks__9__Name=Ordering HTTP Background Check
|
||||
- HealthChecksUI__HealthChecks__9__Uri=http://ordering.backgroundtasks/hc
|
||||
- HealthChecksUI__HealthChecks__10__Name=Basket HTTP Check
|
||||
- HealthChecksUI__HealthChecks__10__Uri=http://basket.api/hc
|
||||
- HealthChecksUI__HealthChecks__11__Name=Catalog HTTP Check
|
||||
- HealthChecksUI__HealthChecks__11__Uri=http://catalog.api/hc
|
||||
- HealthChecksUI__HealthChecks__12__Name=Identity HTTP Check
|
||||
- HealthChecksUI__HealthChecks__12__Uri=http://identity.api/hc
|
||||
- HealthChecksUI__HealthChecks__13__Name=Marketing HTTP Check
|
||||
- HealthChecksUI__HealthChecks__13__Uri=http://marketing.api/hc
|
||||
- HealthChecksUI__HealthChecks__14__Name=Locations HTTP Check
|
||||
- HealthChecksUI__HealthChecks__14__Uri=http://locations.api/hc
|
||||
- HealthChecksUI__HealthChecks__15__Name=Payments HTTP Check
|
||||
- HealthChecksUI__HealthChecks__15__Uri=http://payment.api/hc
|
||||
- HealthChecksUI__HealthChecks__16__Name=Ordering SignalRHub HTTP Check
|
||||
- HealthChecksUI__HealthChecks__16__Uri=http://ordering.signalrhub/hc
|
||||
- OrderingBackgroundTasksUrl=http://ordering.backgroundtasks/hc
|
||||
- ApplicationInsights__InstrumentationKey=${INSTRUMENTATION_KEY}
|
||||
- OrchestratorType=${ORCHESTRATOR_TYPE}
|
||||
|
||||
@ -20,17 +20,17 @@ services:
|
||||
identity.api:
|
||||
build:
|
||||
args:
|
||||
NODE_IMAGE: stefanscherer/node-windows:8.11
|
||||
NODE_IMAGE: stefanscherer/node-windows:10
|
||||
|
||||
webspa:
|
||||
build:
|
||||
args:
|
||||
NODE_IMAGE: stefanscherer/node-windows:8.11
|
||||
NODE_IMAGE: stefanscherer/node-windows:10
|
||||
|
||||
webmvc:
|
||||
build:
|
||||
args:
|
||||
NODE_IMAGE: stefanscherer/node-windows:8.11
|
||||
NODE_IMAGE: stefanscherer/node-windows:10
|
||||
|
||||
|
||||
networks:
|
||||
|
||||
@ -1,11 +1,12 @@
|
||||
version: '3.4'
|
||||
|
||||
services:
|
||||
|
||||
seq:
|
||||
image: datalust/seq:latest
|
||||
|
||||
sql.data:
|
||||
image: microsoft/mssql-server-linux:2017-latest
|
||||
image: mcr.microsoft.com/mssql/server:2017-latest
|
||||
|
||||
nosql.data:
|
||||
image: mongo
|
||||
@ -17,7 +18,7 @@ services:
|
||||
image: rabbitmq:3-management-alpine
|
||||
|
||||
identity.api:
|
||||
image: ${REGISTRY:-eshop}/identity.api:${TAG:-latest}
|
||||
image: ${REGISTRY:-eshop}/identity.api:${PLATFORM:-linux}-${TAG:-latest}
|
||||
build:
|
||||
context: .
|
||||
dockerfile: src/Services/Identity/Identity.API/Dockerfile
|
||||
@ -25,7 +26,7 @@ services:
|
||||
- sql.data
|
||||
|
||||
basket.api:
|
||||
image: ${REGISTRY:-eshop}/basket.api:${TAG:-latest}
|
||||
image: ${REGISTRY:-eshop}/basket.api:${PLATFORM:-linux}-${TAG:-latest}
|
||||
build:
|
||||
context: .
|
||||
dockerfile: src/Services/Basket/Basket.API/Dockerfile
|
||||
@ -35,7 +36,7 @@ services:
|
||||
- rabbitmq
|
||||
|
||||
catalog.api:
|
||||
image: ${REGISTRY:-eshop}/catalog.api:${TAG:-latest}
|
||||
image: ${REGISTRY:-eshop}/catalog.api:${PLATFORM:-linux}-${TAG:-latest}
|
||||
build:
|
||||
context: .
|
||||
dockerfile: src/Services/Catalog/Catalog.API/Dockerfile
|
||||
@ -44,7 +45,7 @@ services:
|
||||
- rabbitmq
|
||||
|
||||
ordering.api:
|
||||
image: ${REGISTRY:-eshop}/ordering.api:${TAG:-latest}
|
||||
image: ${REGISTRY:-eshop}/ordering.api:${PLATFORM:-linux}-${TAG:-latest}
|
||||
build:
|
||||
context: .
|
||||
dockerfile: src/Services/Ordering/Ordering.API/Dockerfile
|
||||
@ -53,7 +54,7 @@ services:
|
||||
- rabbitmq
|
||||
|
||||
ordering.backgroundtasks:
|
||||
image: ${REGISTRY:-eshop}/ordering.backgroundtasks:${TAG:-latest}
|
||||
image: ${REGISTRY:-eshop}/ordering.backgroundtasks:${PLATFORM:-linux}-${TAG:-latest}
|
||||
build:
|
||||
context: .
|
||||
dockerfile: src/Services/Ordering/Ordering.BackgroundTasks/Dockerfile
|
||||
@ -62,7 +63,7 @@ services:
|
||||
- rabbitmq
|
||||
|
||||
marketing.api:
|
||||
image: ${REGISTRY:-eshop}/marketing.api:${TAG:-latest}
|
||||
image: ${REGISTRY:-eshop}/marketing.api:${PLATFORM:-linux}-${TAG:-latest}
|
||||
build:
|
||||
context: .
|
||||
dockerfile: src/Services/Marketing/Marketing.API/Dockerfile
|
||||
@ -73,7 +74,7 @@ services:
|
||||
- rabbitmq
|
||||
|
||||
payment.api:
|
||||
image: ${REGISTRY:-eshop}/payment.api:${TAG:-latest}
|
||||
image: ${REGISTRY:-eshop}/payment.api:${PLATFORM:-linux}-${TAG:-latest}
|
||||
build:
|
||||
context: .
|
||||
dockerfile: src/Services/Payment/Payment.API/Dockerfile
|
||||
@ -81,7 +82,7 @@ services:
|
||||
- rabbitmq
|
||||
|
||||
locations.api:
|
||||
image: ${REGISTRY:-eshop}/locations.api:${TAG:-latest}
|
||||
image: ${REGISTRY:-eshop}/locations.api:${PLATFORM:-linux}-${TAG:-latest}
|
||||
build:
|
||||
context: .
|
||||
dockerfile: src/Services/Location/Locations.API/Dockerfile
|
||||
@ -90,7 +91,7 @@ services:
|
||||
- rabbitmq
|
||||
|
||||
webhooks.api:
|
||||
image: ${REGISTRY:-eshop}/webhooks.api:${TAG:-latest}
|
||||
image: ${REGISTRY:-eshop}/webhooks.api:${PLATFORM:-linux}-${TAG:-latest}
|
||||
build:
|
||||
context: .
|
||||
dockerfile: src/Services/Webhooks/Webhooks.API/Dockerfile
|
||||
@ -98,7 +99,7 @@ services:
|
||||
- sql.data
|
||||
|
||||
mobileshoppingapigw:
|
||||
image: ${REGISTRY:-eshop}/ocelotapigw:${TAG:-latest}
|
||||
image: ${REGISTRY:-eshop}/ocelotapigw:${PLATFORM:-linux}-${TAG:-latest}
|
||||
build:
|
||||
context: .
|
||||
dockerfile: src/ApiGateways/ApiGw-Base/Dockerfile
|
||||
@ -113,7 +114,7 @@ services:
|
||||
- basket.api
|
||||
|
||||
mobilemarketingapigw:
|
||||
image: ${REGISTRY:-eshop}/ocelotapigw:${TAG:-latest}
|
||||
image: ${REGISTRY:-eshop}/ocelotapigw:${PLATFORM:-linux}-${TAG:-latest}
|
||||
build:
|
||||
context: .
|
||||
dockerfile: src/ApiGateways/ApiGw-Base/Dockerfile
|
||||
@ -128,7 +129,7 @@ services:
|
||||
- basket.api
|
||||
|
||||
webshoppingapigw:
|
||||
image: ${REGISTRY:-eshop}/ocelotapigw:${TAG:-latest}
|
||||
image: ${REGISTRY:-eshop}/ocelotapigw:${PLATFORM:-linux}-${TAG:-latest}
|
||||
build:
|
||||
context: .
|
||||
dockerfile: src/ApiGateways/ApiGw-Base/Dockerfile
|
||||
@ -143,7 +144,7 @@ services:
|
||||
- basket.api
|
||||
|
||||
webmarketingapigw:
|
||||
image: ${REGISTRY:-eshop}/ocelotapigw:${TAG:-latest}
|
||||
image: ${REGISTRY:-eshop}/ocelotapigw:${PLATFORM:-linux}-${TAG:-latest}
|
||||
build:
|
||||
context: .
|
||||
dockerfile: src/ApiGateways/ApiGw-Base/Dockerfile
|
||||
@ -158,7 +159,7 @@ services:
|
||||
- basket.api
|
||||
|
||||
mobileshoppingagg:
|
||||
image: ${REGISTRY:-eshop}/mobileshoppingagg:${TAG:-latest}
|
||||
image: ${REGISTRY:-eshop}/mobileshoppingagg:${PLATFORM:-linux}-${TAG:-latest}
|
||||
build:
|
||||
context: .
|
||||
dockerfile: src/ApiGateways/Mobile.Bff.Shopping/aggregator/Dockerfile
|
||||
@ -173,7 +174,7 @@ services:
|
||||
- basket.api
|
||||
|
||||
webshoppingagg:
|
||||
image: ${REGISTRY:-eshop}/webshoppingagg:${TAG:-latest}
|
||||
image: ${REGISTRY:-eshop}/webshoppingagg:${PLATFORM:-linux}-${TAG:-latest}
|
||||
build:
|
||||
context: .
|
||||
dockerfile: src/ApiGateways/Web.Bff.Shopping/aggregator/Dockerfile
|
||||
@ -188,7 +189,7 @@ services:
|
||||
- basket.api
|
||||
|
||||
ordering.signalrhub:
|
||||
image: ${REGISTRY:-eshop}/ordering.signalrhub:${TAG:-latest}
|
||||
image: ${REGISTRY:-eshop}/ordering.signalrhub:${PLATFORM:-linux}-${TAG:-latest}
|
||||
build:
|
||||
context: .
|
||||
dockerfile: src/Services/Ordering/Ordering.SignalrHub/Dockerfile
|
||||
@ -203,23 +204,25 @@ services:
|
||||
- basket.api
|
||||
|
||||
webstatus:
|
||||
image: ${REGISTRY:-eshop}/webstatus:${TAG:-latest}
|
||||
image: ${REGISTRY:-eshop}/webstatus:${PLATFORM:-linux}-${TAG:-latest}
|
||||
build:
|
||||
context: .
|
||||
dockerfile: src/Web/WebStatus/Dockerfile
|
||||
|
||||
webspa:
|
||||
image: ${REGISTRY:-eshop}/webspa:${TAG:-latest}
|
||||
image: ${REGISTRY:-eshop}/webspa:${PLATFORM:-linux}-${TAG:-latest}
|
||||
build:
|
||||
context: .
|
||||
dockerfile: src/Web/WebSPA/Dockerfile
|
||||
args:
|
||||
NODE_IMAGE: ${NODE_IMAGE:-node:8.11}
|
||||
# depends_on:
|
||||
# - webshoppingagg
|
||||
# - webshoppingapigw
|
||||
# - webmarketingapigw
|
||||
|
||||
webmvc:
|
||||
image: ${REGISTRY:-eshop}/webmvc:${TAG:-latest}
|
||||
image: ${REGISTRY:-eshop}/webmvc:${PLATFORM:-linux}-${TAG:-latest}
|
||||
build:
|
||||
context: .
|
||||
dockerfile: src/Web/WebMVC/Dockerfile
|
||||
@ -229,7 +232,7 @@ services:
|
||||
- webmarketingapigw
|
||||
|
||||
webhooks.client:
|
||||
image: ${REGISTRY:-eshop}/webhooks.client:${TAG:-latest}
|
||||
image: ${REGISTRY:-eshop}/webhooks.client:${PLATFORM:-linux}-${TAG:-latest}
|
||||
build:
|
||||
context: .
|
||||
dockerfile: src/Web/WebhookClient/Dockerfile
|
||||
|
||||
@ -1,8 +0,0 @@
|
||||
#!/bin/sh
|
||||
|
||||
export NODE_DOWNLOAD_SHA 0e20787e2eda4cc31336d8327556ebc7417e8ee0a6ba0de96a09b0ec2b841f60
|
||||
curl -SL "https://nodejs.org/dist/v${NODE_VERSION}/node-v${NODE_VERSION}-linux-x64.tar.gz" --output nodejs.tar.gz \
|
||||
&& echo "$NODE_DOWNLOAD_SHA nodejs.tar.gz" | sha256sum -c - \
|
||||
&& tar -xzf "nodejs.tar.gz" -C /usr/local --strip-components=1 \
|
||||
&& rm nodejs.tar.gz \
|
||||
&& ln -s /usr/local/bin/node /usr/local/bin/nodejs
|
||||
@ -1,4 +0,0 @@
|
||||
set NODE_VERSION=8.11.1
|
||||
curl -SL "https://nodejs.org/dist/v%NODE_VERSION%/node-v%NODE_VERSION%-win-x64.zip" --output nodejs.zip
|
||||
tar -xf nodejs.zip -C c:\
|
||||
setx PATH "%PATH%;c:\node-v%NODE_VERSION%-win-x64"
|
||||
@ -142,9 +142,13 @@ Project("{9A19103F-16F7-4668-BE54-9A1E7A4F7556}") = "Payment.API", "src\Services
|
||||
EndProject
|
||||
Project("{2150E333-8FDC-42A3-9474-1A3956D46DE8}") = "Webhooks", "Webhooks", "{E0AA11C4-2873-461D-8F82-53392530FB7A}"
|
||||
EndProject
|
||||
Project("{FAE04EC0-301F-11D3-BF4B-00C04F79EFBC}") = "Webhooks.API", "src\Services\Webhooks\Webhooks.API\Webhooks.API.csproj", "{84E2016E-0435-44C6-8020-3D288AA38B2C}"
|
||||
Project("{9A19103F-16F7-4668-BE54-9A1E7A4F7556}") = "Webhooks.API", "src\Services\Webhooks\Webhooks.API\Webhooks.API.csproj", "{84E2016E-0435-44C6-8020-3D288AA38B2C}"
|
||||
EndProject
|
||||
Project("{FAE04EC0-301F-11D3-BF4B-00C04F79EFBC}") = "WebhookClient", "src\Web\WebhookClient\WebhookClient.csproj", "{766D7E92-6AF0-476C-ADD5-282BF4D8C576}"
|
||||
Project("{9A19103F-16F7-4668-BE54-9A1E7A4F7556}") = "WebhookClient", "src\Web\WebhookClient\WebhookClient.csproj", "{766D7E92-6AF0-476C-ADD5-282BF4D8C576}"
|
||||
EndProject
|
||||
Project("{2150E333-8FDC-42A3-9474-1A3956D46DE8}") = "Devspace.Support", "Devspace.Support", "{68F5041D-51F2-4630-94B6-B49789F5E51A}"
|
||||
EndProject
|
||||
Project("{FAE04EC0-301F-11D3-BF4B-00C04F79EFBC}") = "Devspaces.Support", "src\BuildingBlocks\Devspaces.Support\Devspaces.Support.csproj", "{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}"
|
||||
EndProject
|
||||
Global
|
||||
GlobalSection(SolutionConfigurationPlatforms) = preSolution
|
||||
@ -1744,6 +1748,54 @@ Global
|
||||
{766D7E92-6AF0-476C-ADD5-282BF4D8C576}.Release|x64.Build.0 = Release|Any CPU
|
||||
{766D7E92-6AF0-476C-ADD5-282BF4D8C576}.Release|x86.ActiveCfg = Release|Any CPU
|
||||
{766D7E92-6AF0-476C-ADD5-282BF4D8C576}.Release|x86.Build.0 = Release|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Ad-Hoc|Any CPU.ActiveCfg = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Ad-Hoc|Any CPU.Build.0 = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Ad-Hoc|ARM.ActiveCfg = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Ad-Hoc|ARM.Build.0 = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Ad-Hoc|iPhone.ActiveCfg = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Ad-Hoc|iPhone.Build.0 = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Ad-Hoc|iPhoneSimulator.ActiveCfg = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Ad-Hoc|iPhoneSimulator.Build.0 = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Ad-Hoc|x64.ActiveCfg = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Ad-Hoc|x64.Build.0 = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Ad-Hoc|x86.ActiveCfg = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Ad-Hoc|x86.Build.0 = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.AppStore|Any CPU.ActiveCfg = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.AppStore|Any CPU.Build.0 = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.AppStore|ARM.ActiveCfg = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.AppStore|ARM.Build.0 = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.AppStore|iPhone.ActiveCfg = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.AppStore|iPhone.Build.0 = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.AppStore|iPhoneSimulator.ActiveCfg = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.AppStore|iPhoneSimulator.Build.0 = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.AppStore|x64.ActiveCfg = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.AppStore|x64.Build.0 = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.AppStore|x86.ActiveCfg = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.AppStore|x86.Build.0 = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Debug|Any CPU.ActiveCfg = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Debug|Any CPU.Build.0 = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Debug|ARM.ActiveCfg = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Debug|ARM.Build.0 = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Debug|iPhone.ActiveCfg = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Debug|iPhone.Build.0 = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Debug|iPhoneSimulator.ActiveCfg = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Debug|iPhoneSimulator.Build.0 = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Debug|x64.ActiveCfg = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Debug|x64.Build.0 = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Debug|x86.ActiveCfg = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Debug|x86.Build.0 = Debug|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Release|Any CPU.ActiveCfg = Release|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Release|Any CPU.Build.0 = Release|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Release|ARM.ActiveCfg = Release|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Release|ARM.Build.0 = Release|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Release|iPhone.ActiveCfg = Release|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Release|iPhone.Build.0 = Release|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Release|iPhoneSimulator.ActiveCfg = Release|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Release|iPhoneSimulator.Build.0 = Release|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Release|x64.ActiveCfg = Release|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Release|x64.Build.0 = Release|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Release|x86.ActiveCfg = Release|Any CPU
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35}.Release|x86.Build.0 = Release|Any CPU
|
||||
EndGlobalSection
|
||||
GlobalSection(SolutionProperties) = preSolution
|
||||
HideSolutionNode = FALSE
|
||||
@ -1808,6 +1860,8 @@ Global
|
||||
{E0AA11C4-2873-461D-8F82-53392530FB7A} = {91CF7717-08AB-4E65-B10E-0B426F01E2E8}
|
||||
{84E2016E-0435-44C6-8020-3D288AA38B2C} = {E0AA11C4-2873-461D-8F82-53392530FB7A}
|
||||
{766D7E92-6AF0-476C-ADD5-282BF4D8C576} = {E279BF0F-7F66-4F3A-A3AB-2CDA66C1CD04}
|
||||
{68F5041D-51F2-4630-94B6-B49789F5E51A} = {DB0EFB20-B024-4E5E-A75C-52143C131D25}
|
||||
{56C2EF0B-6BF2-41D9-BE07-6E6D08D06B35} = {68F5041D-51F2-4630-94B6-B49789F5E51A}
|
||||
EndGlobalSection
|
||||
GlobalSection(ExtensibilityGlobals) = postSolution
|
||||
SolutionGuid = {25728519-5F0F-4973-8A64-0A81EB4EA8D9}
|
||||
|
||||
@ -161,6 +161,10 @@ Project("{9A19103F-16F7-4668-BE54-9A1E7A4F7556}") = "Mobile.Shopping.HttpAggrega
|
||||
EndProject
|
||||
Project("{9A19103F-16F7-4668-BE54-9A1E7A4F7556}") = "Web.Shopping.HttpAggregator", "src\ApiGateways\Web.Bff.Shopping\aggregator\Web.Shopping.HttpAggregator.csproj", "{E39BD762-BC86-459D-B818-B6BF2D9F1352}"
|
||||
EndProject
|
||||
Project("{2150E333-8FDC-42A3-9474-1A3956D46DE8}") = "Devspaces.Support", "Devspaces.Support", "{ABBA561B-499B-48C0-8299-85D41E6E9E98}"
|
||||
EndProject
|
||||
Project("{9A19103F-16F7-4668-BE54-9A1E7A4F7556}") = "Devspaces.Support", "src\BuildingBlocks\Devspaces.Support\Devspaces.Support.csproj", "{CB6D01A4-E597-4348-9570-FC8DB03B4267}"
|
||||
EndProject
|
||||
Global
|
||||
GlobalSection(SolutionConfigurationPlatforms) = preSolution
|
||||
Ad-Hoc|Any CPU = Ad-Hoc|Any CPU
|
||||
@ -2039,6 +2043,54 @@ Global
|
||||
{E39BD762-BC86-459D-B818-B6BF2D9F1352}.Release|x64.Build.0 = Release|Any CPU
|
||||
{E39BD762-BC86-459D-B818-B6BF2D9F1352}.Release|x86.ActiveCfg = Release|Any CPU
|
||||
{E39BD762-BC86-459D-B818-B6BF2D9F1352}.Release|x86.Build.0 = Release|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Ad-Hoc|Any CPU.ActiveCfg = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Ad-Hoc|Any CPU.Build.0 = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Ad-Hoc|ARM.ActiveCfg = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Ad-Hoc|ARM.Build.0 = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Ad-Hoc|iPhone.ActiveCfg = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Ad-Hoc|iPhone.Build.0 = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Ad-Hoc|iPhoneSimulator.ActiveCfg = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Ad-Hoc|iPhoneSimulator.Build.0 = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Ad-Hoc|x64.ActiveCfg = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Ad-Hoc|x64.Build.0 = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Ad-Hoc|x86.ActiveCfg = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Ad-Hoc|x86.Build.0 = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.AppStore|Any CPU.ActiveCfg = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.AppStore|Any CPU.Build.0 = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.AppStore|ARM.ActiveCfg = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.AppStore|ARM.Build.0 = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.AppStore|iPhone.ActiveCfg = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.AppStore|iPhone.Build.0 = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.AppStore|iPhoneSimulator.ActiveCfg = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.AppStore|iPhoneSimulator.Build.0 = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.AppStore|x64.ActiveCfg = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.AppStore|x64.Build.0 = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.AppStore|x86.ActiveCfg = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.AppStore|x86.Build.0 = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Debug|Any CPU.ActiveCfg = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Debug|Any CPU.Build.0 = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Debug|ARM.ActiveCfg = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Debug|ARM.Build.0 = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Debug|iPhone.ActiveCfg = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Debug|iPhone.Build.0 = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Debug|iPhoneSimulator.ActiveCfg = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Debug|iPhoneSimulator.Build.0 = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Debug|x64.ActiveCfg = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Debug|x64.Build.0 = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Debug|x86.ActiveCfg = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Debug|x86.Build.0 = Debug|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Release|Any CPU.ActiveCfg = Release|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Release|Any CPU.Build.0 = Release|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Release|ARM.ActiveCfg = Release|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Release|ARM.Build.0 = Release|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Release|iPhone.ActiveCfg = Release|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Release|iPhone.Build.0 = Release|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Release|iPhoneSimulator.ActiveCfg = Release|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Release|iPhoneSimulator.Build.0 = Release|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Release|x64.ActiveCfg = Release|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Release|x64.Build.0 = Release|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Release|x86.ActiveCfg = Release|Any CPU
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267}.Release|x86.Build.0 = Release|Any CPU
|
||||
EndGlobalSection
|
||||
GlobalSection(SolutionProperties) = preSolution
|
||||
HideSolutionNode = FALSE
|
||||
@ -2111,6 +2163,8 @@ Global
|
||||
{0A328C44-4C4E-49BE-9FB4-9D851CEC28AC} = {56AD1FCA-6E16-4798-BF29-941C5B3277D2}
|
||||
{98E0B3BA-6601-4C59-A9AA-24A00A17D835} = {A32A5254-BA36-46FC-8C75-F7B8FFE8FCD0}
|
||||
{E39BD762-BC86-459D-B818-B6BF2D9F1352} = {424BC53E-17EA-4E12-BC07-64BAA927ABCB}
|
||||
{ABBA561B-499B-48C0-8299-85D41E6E9E98} = {DB0EFB20-B024-4E5E-A75C-52143C131D25}
|
||||
{CB6D01A4-E597-4348-9570-FC8DB03B4267} = {ABBA561B-499B-48C0-8299-85D41E6E9E98}
|
||||
EndGlobalSection
|
||||
GlobalSection(ExtensibilityGlobals) = postSolution
|
||||
SolutionGuid = {25728519-5F0F-4973-8A64-0A81EB4EA8D9}
|
||||
|
||||
88
elk/Readme.md
Normal file
@ -0,0 +1,88 @@
|
||||
This article contains a brief introduction to centralized structured logging with [Serilog](https://serilog.net/) and event viewing with [ELK](https://www.elastic.co/elk-stack) in eShopOnContainers. ELK is an acronym of ElasticSearch, LogStash and Kibana. This is one of the most used tools in the industry standards.
|
||||
|
||||

|
||||
|
||||
## Wiring eshopOnContainers with ELK in Localhost
|
||||
|
||||
eshopOnContainers is ready for work with ELK, you only need to setup the configuration parameter **LogstashUrl**, in **Serilog** Section, for achieve this, you can do it modifing this parameter in every appsettings.json of every service, or via Environment Variable **Serilog:LogstashUrl**.
|
||||
|
||||
There is another option, a zero-configuration environment for testing the integration launching via ```docker-compose``` command, on the root directory of eshopOnContainers:
|
||||
|
||||
```sh
|
||||
docker-compose -f docker-compose.yml -f docker-compose.override.yml -f docker-compose.elk.yml build
|
||||
|
||||
docker-compose -f docker-compose.yml -f docker-compose.override.yml -f docker-compose.elk.yml up
|
||||
```
|
||||
|
||||
### Configuring Logstash index on Kibana
|
||||
|
||||
Once time you have started and configured your application, you only need to configure the logstash index on kibana.
|
||||
You can address to Kibana, with docker-compose setup is at [http://localhost:5601](http://localhost:5601)
|
||||
|
||||
If you have accessed to kibana too early, you can see this error. It's normal, depending of your machine the kibana stack needs a bit of time to startup.
|
||||

|
||||
|
||||
You can wait a bit and refresh the page, the first time you enter, you need to configure and index pattern, in the ```docker-compose``` configuration, the index pattern name is **eshops-\***.
|
||||

|
||||
|
||||
With the index pattern configured, you can enter in the discover section and start viewing how the tool is recollecting the logging information.
|
||||
|
||||

|
||||
|
||||
## Configuring ELK on Azure VM
|
||||
Another option is to use a preconfigured virtual machine with Logstash, ElasticSearch and Kibana and point the configuration parameter **LogstashUrl**. For doing this you can address to Microsoft Azure, and start searching a Certified ELK Virtual Machine
|
||||
|
||||

|
||||
|
||||
This options it have a certified preconfigured options (Network, VirtualMachine type, OS, RAM, Disks) for having a good starting point of ELK with good performance.
|
||||
|
||||

|
||||
|
||||
When you have configured the main aspects of your virtual machine, you will have a "review & create" last step like this:
|
||||

|
||||
|
||||
### Configuring the bitnami environment
|
||||
|
||||
This virtual machine has a lot of configuration pipeing done. If you want to change something of the default configuration you can address this documentation:
|
||||
[https://docs.bitnami.com/virtual-machine/apps/elk/get-started/](https://docs.bitnami.com/virtual-machine/apps/elk/get-started/)
|
||||
|
||||
The only thing you have to change is the logstash configuration inside the machine. This configuration is at the file ```/opt/bitnami/logstash/conf/logstash.conf```
|
||||
You must edit the file and overwrite with this configuration:
|
||||
```conf
|
||||
input {
|
||||
http {
|
||||
#default host 0.0.0.0:8080
|
||||
codec => json
|
||||
}
|
||||
}
|
||||
|
||||
## Add your filters / logstash plugins configuration here
|
||||
filter {
|
||||
split {
|
||||
field => "events"
|
||||
target => "e"
|
||||
remove_field => "events"
|
||||
}
|
||||
}
|
||||
|
||||
output {
|
||||
elasticsearch {
|
||||
hosts => "elasticsearch:9200"
|
||||
index=>"eshops-%{+xxxx.ww}"
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
For doing this you can connect via ssh to the vm and edit the file using the vi editor for example.
|
||||
When the file will be edited, check there are Inbound Port Rules created for the logstash service. You can do it going to Networking Menu on your ELK Virtual Machine Resource in Azure.
|
||||
|
||||

|
||||
|
||||
The only thing that remains is to connect to your vm vía browser. And check the bitnami splash page is showing.
|
||||
|
||||

|
||||
|
||||
You can get the password for accessing going to your virtual machine in azure and check the boot diagnostics, theres a message that shows to you which is your password.
|
||||
|
||||
When you have the user and password you can access to the kibana tool, and create the ```eshops-*``` index pattern that is well documented at the beggining of this documentation and then start to discover.
|
||||

|
||||
5
elk/elasticsearch/Dockerfile
Normal file
@ -0,0 +1,5 @@
|
||||
# https://github.com/elastic/elasticsearch-docker
|
||||
FROM docker.elastic.co/elasticsearch/elasticsearch-oss:6.0.0
|
||||
|
||||
# Add your elasticsearch plugins setup here
|
||||
# Example: RUN elasticsearch-plugin install analysis-icu
|
||||
16
elk/elasticsearch/config/elasticsearch.yml
Normal file
@ -0,0 +1,16 @@
|
||||
---
|
||||
## Default Elasticsearch configuration from elasticsearch-docker.
|
||||
## from https://github.com/elastic/elasticsearch-docker/blob/master/build/elasticsearch/elasticsearch.yml
|
||||
#
|
||||
cluster.name: "docker-cluster"
|
||||
network.host: 0.0.0.0
|
||||
|
||||
# minimum_master_nodes need to be explicitly set when bound on a public IP
|
||||
# set to 1 to allow single node clusters
|
||||
# Details: https://github.com/elastic/elasticsearch/pull/17288
|
||||
discovery.zen.minimum_master_nodes: 1
|
||||
|
||||
## Use single node discovery in order to disable production mode and avoid bootstrap checks
|
||||
## see https://www.elastic.co/guide/en/elasticsearch/reference/current/bootstrap-checks.html
|
||||
#
|
||||
discovery.type: single-node
|
||||
5
elk/kibana/Dockerfile
Normal file
@ -0,0 +1,5 @@
|
||||
# https://github.com/elastic/kibana-docker
|
||||
FROM docker.elastic.co/kibana/kibana-oss:6.0.0
|
||||
|
||||
# Add your kibana plugins setup here
|
||||
# Example: RUN kibana-plugin install <name|url>
|
||||
7
elk/kibana/config/kibana.yml
Normal file
@ -0,0 +1,7 @@
|
||||
---
|
||||
## Default Kibana configuration from kibana-docker.
|
||||
## from https://github.com/elastic/kibana-docker/blob/master/build/kibana/config/kibana.yml
|
||||
#
|
||||
server.name: kibana
|
||||
server.host: "0"
|
||||
elasticsearch.url: http://elasticsearch:9200
|
||||
6
elk/logstash/Dockerfile
Normal file
@ -0,0 +1,6 @@
|
||||
# https://github.com/elastic/logstash-docker
|
||||
FROM docker.elastic.co/logstash/logstash-oss:6.0.0
|
||||
|
||||
# Add your logstash plugins setup here
|
||||
# Example: RUN logstash-plugin install logstash-filter-json
|
||||
RUN logstash-plugin install logstash-input-http
|
||||
6
elk/logstash/config/logstash.yml
Normal file
@ -0,0 +1,6 @@
|
||||
---
|
||||
## Default Logstash configuration from logstash-docker.
|
||||
## from https://github.com/elastic/logstash-docker/blob/master/build/logstash/config/logstash-oss.yml
|
||||
#
|
||||
http.host: "0.0.0.0"
|
||||
path.config: /usr/share/logstash/pipeline
|
||||
22
elk/logstash/pipeline/logstash.conf
Normal file
@ -0,0 +1,22 @@
|
||||
input {
|
||||
http {
|
||||
#default host 0.0.0.0:8080
|
||||
codec => json
|
||||
}
|
||||
}
|
||||
|
||||
## Add your filters / logstash plugins configuration here
|
||||
filter {
|
||||
split {
|
||||
field => "events"
|
||||
target => "e"
|
||||
remove_field => "events"
|
||||
}
|
||||
}
|
||||
|
||||
output {
|
||||
elasticsearch {
|
||||
hosts => "elasticsearch:9200"
|
||||
index=>"eshops-%{+xxxx.ww}"
|
||||
}
|
||||
}
|
||||
BIN
img/eShopScreen.png
Normal file
|
After Width: | Height: | Size: 334 KiB |
BIN
img/elk/azure-nsg-inboundportsConfig.png
Normal file
|
After Width: | Height: | Size: 17 KiB |
BIN
img/elk/bitnami_splash.png
Normal file
|
After Width: | Height: | Size: 43 KiB |
BIN
img/elk/create-vm-elk-azure-last-step.png
Normal file
|
After Width: | Height: | Size: 60 KiB |
BIN
img/elk/create-vm-elk-azure-summary.png
Normal file
|
After Width: | Height: | Size: 80 KiB |
BIN
img/elk/create-vm-elk-azure.png
Normal file
|
After Width: | Height: | Size: 54 KiB |
BIN
img/elk/discover-kibana.png
Normal file
|
After Width: | Height: | Size: 62 KiB |
BIN
img/elk/kibana_eshops_index.png
Normal file
|
After Width: | Height: | Size: 37 KiB |
BIN
img/elk/kibana_result.png
Normal file
|
After Width: | Height: | Size: 71 KiB |
BIN
img/elk/kibana_startup.png
Normal file
|
After Width: | Height: | Size: 57 KiB |
BIN
img/elk/kibana_working.png
Normal file
|
After Width: | Height: | Size: 78 KiB |
@ -20,7 +20,7 @@ For AKS:
|
||||
For ACS:
|
||||
|
||||
>```
|
||||
>./gen-k8s-env -resourceGroupName k8sGroup -location westeurope -registryName k8sregistry -createAcr true -orchestratorName k8s-cluster -dnsName k8s-dns
|
||||
>./gen-k8s-env-aks -resourceGroupName k8sGroup -location westeurope -registryName k8sregistry -serviceName k8s-cluster -createAcr true -nodeCount 3 -nodeVMSize Standard_D2_v2
|
||||
>```
|
||||
|
||||
* A Docker development environment with `docker` and `docker-compose`.
|
||||
|
||||
2
k8s/deploy-nodeports.ps1
Normal file
@ -0,0 +1,2 @@
|
||||
kubectl apply -f .\nodeports\rabbitmq-admin.yaml
|
||||
kubectl apply -f .\nodeports\sql-services.yaml
|
||||
@ -33,14 +33,13 @@
|
||||
{{- end -}}
|
||||
|
||||
|
||||
|
||||
{{- define "pathBase" -}}
|
||||
{{- $name := first .}}
|
||||
{{- $ctx := last .}}
|
||||
{{- if $ctx.Values.inf.k8s.suffix -}}
|
||||
{{- $suffix := include "suffix-name" $ctx -}}
|
||||
{{- printf "/%s-%s" $name $suffix -}}
|
||||
{{- if .Values.inf.k8s.suffix -}}
|
||||
{{- $suffix := include "suffix-name" . -}}
|
||||
{{- printf "%s-%s" .Values.pathBase $suffix -}}
|
||||
{{- else -}}
|
||||
{{- printf "/%s" $name -}}
|
||||
{{- .Values.pathBase -}}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
||||
|
||||
@ -61,10 +61,10 @@ spec:
|
||||
imagePullPolicy: {{ .Values.image.pullPolicy }}
|
||||
volumeMounts:
|
||||
- name: config
|
||||
mountPath: /app/configuration
|
||||
mountPath: {{ .Values.ocelot.configPath }}
|
||||
env:
|
||||
- name: PATH_BASE
|
||||
value: {{ include "pathBase" (list .Values.app.ingress.entries.mobilemarketingapigw .) }}
|
||||
value: {{ include "pathBase" . }}
|
||||
- name: k8sname
|
||||
value: {{ .Values.clusterName }}
|
||||
{{- if .Values.env.values -}}
|
||||
|
||||
@ -1,5 +1,6 @@
|
||||
{{- if .Values.ingress.enabled -}}
|
||||
{{- $ingressPath := include "pathBase" (list .Values.app.ingress.entries.mobilemarketingapigw .) -}}
|
||||
{{- $ingressPath := include "pathBase" . -}}
|
||||
{{- $serviceName := .Values.app.svc.mobilemarketingapigw -}}
|
||||
apiVersion: extensions/v1beta1
|
||||
kind: Ingress
|
||||
metadata:
|
||||
@ -23,11 +24,13 @@ spec:
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
rules:
|
||||
- host: {{ .Values.inf.k8s.dns }}
|
||||
{{- range .Values.ingress.hosts }}
|
||||
- host: {{ . }}
|
||||
http:
|
||||
paths:
|
||||
- path: {{ $ingressPath }}
|
||||
backend:
|
||||
serviceName: {{ .Values.app.svc.mobilemarketingapigw }}
|
||||
serviceName: {{ $serviceName }}
|
||||
servicePort: http
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
||||
@ -62,3 +62,5 @@ probes:
|
||||
initialDelaySeconds: 90
|
||||
periodSeconds: 60
|
||||
port: 80
|
||||
ocelot:
|
||||
configPath: /app/configuration
|
||||
|
||||
@ -35,13 +35,11 @@
|
||||
|
||||
|
||||
{{- define "pathBase" -}}
|
||||
{{- $name := first .}}
|
||||
{{- $ctx := last .}}
|
||||
{{- if $ctx.Values.inf.k8s.suffix -}}
|
||||
{{- $suffix := include "suffix-name" $ctx -}}
|
||||
{{- printf "/%s-%s" $name $suffix -}}
|
||||
{{- if .Values.inf.k8s.suffix -}}
|
||||
{{- $suffix := include "suffix-name" . -}}
|
||||
{{- printf "%s-%s" .Values.pathBase $suffix -}}
|
||||
{{- else -}}
|
||||
{{- printf "/%s" $name -}}
|
||||
{{- .Values.pathBase -}}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
||||
|
||||
@ -61,10 +61,10 @@ spec:
|
||||
imagePullPolicy: {{ .Values.image.pullPolicy }}
|
||||
volumeMounts:
|
||||
- name: config
|
||||
mountPath: /app/configuration
|
||||
mountPath: {{ .Values.ocelot.configPath }}
|
||||
env:
|
||||
- name: PATH_BASE
|
||||
value: {{ include "pathBase" (list .Values.app.ingress.entries.mobileshoppingapigw .) }}
|
||||
value: {{ include "pathBase" . }}
|
||||
- name: k8sname
|
||||
value: {{ .Values.clusterName }}
|
||||
{{- if .Values.env.values -}}
|
||||
|
||||
@ -1,5 +1,7 @@
|
||||
{{- if .Values.ingress.enabled -}}
|
||||
{{- $ingressPath := include "pathBase" (list .Values.app.ingress.entries.mobileshoppingapigw .) -}}
|
||||
{{- $ingressPath := include "pathBase" . -}}
|
||||
{{- $serviceName := .Values.app.svc.mobileshoppingapigw -}}
|
||||
|
||||
apiVersion: extensions/v1beta1
|
||||
kind: Ingress
|
||||
metadata:
|
||||
@ -23,11 +25,13 @@ spec:
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
rules:
|
||||
- host: {{ .Values.inf.k8s.dns }}
|
||||
{{- range .Values.ingress.hosts }}
|
||||
- host: {{ . }}
|
||||
http:
|
||||
paths:
|
||||
- path: {{ $ingressPath }}
|
||||
backend:
|
||||
serviceName: {{ .Values.app.svc.mobileshoppingapigw }}
|
||||
serviceName: {{ $serviceName }}
|
||||
servicePort: http
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
||||
@ -61,4 +61,6 @@ probes:
|
||||
timeoutSeconds: 5
|
||||
initialDelaySeconds: 90
|
||||
periodSeconds: 60
|
||||
port: 80
|
||||
port: 80
|
||||
ocelot:
|
||||
configPath: /app/configuration
|
||||
@ -35,13 +35,11 @@
|
||||
|
||||
|
||||
{{- define "pathBase" -}}
|
||||
{{- $name := first .}}
|
||||
{{- $ctx := last .}}
|
||||
{{- if $ctx.Values.inf.k8s.suffix -}}
|
||||
{{- $suffix := include "suffix-name" $ctx -}}
|
||||
{{- printf "/%s-%s" $name $suffix -}}
|
||||
{{- if .Values.inf.k8s.suffix -}}
|
||||
{{- $suffix := include "suffix-name" . -}}
|
||||
{{- printf "%s-%s" .Values.pathBase $suffix -}}
|
||||
{{- else -}}
|
||||
{{- printf "/%s" $name -}}
|
||||
{{- .Values.pathBase -}}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
||||
|
||||
@ -61,10 +61,10 @@ spec:
|
||||
imagePullPolicy: {{ .Values.image.pullPolicy }}
|
||||
volumeMounts:
|
||||
- name: config
|
||||
mountPath: /app/configuration
|
||||
mountPath: {{ .Values.ocelot.configPath }}
|
||||
env:
|
||||
- name: PATH_BASE
|
||||
value: {{ include "pathBase" (list .Values.app.ingress.entries.webmarketingapigw .) }}
|
||||
value: {{ include "pathBase" . }}
|
||||
- name: k8sname
|
||||
value: {{ .Values.clusterName }}
|
||||
{{- if .Values.env.values -}}
|
||||
|
||||
@ -1,5 +1,7 @@
|
||||
{{- if .Values.ingress.enabled -}}
|
||||
{{- $ingressPath := include "pathBase" (list .Values.app.ingress.entries.webmarketingapigw .) -}}
|
||||
{{- $ingressPath := include "pathBase" . -}}
|
||||
{{- $serviceName := .Values.app.svc.webmarketingapigw -}}
|
||||
|
||||
apiVersion: extensions/v1beta1
|
||||
kind: Ingress
|
||||
metadata:
|
||||
@ -23,11 +25,13 @@ spec:
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
rules:
|
||||
- host: {{ .Values.inf.k8s.dns }}
|
||||
{{- range .Values.ingress.hosts }}
|
||||
- host: {{ . }}
|
||||
http:
|
||||
paths:
|
||||
- path: {{ $ingressPath }}
|
||||
backend:
|
||||
serviceName: {{ .Values.app.svc.webmarketingapigw }}
|
||||
serviceName: {{ $serviceName }}
|
||||
servicePort: http
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
||||
@ -61,4 +61,6 @@ probes:
|
||||
timeoutSeconds: 5
|
||||
initialDelaySeconds: 90
|
||||
periodSeconds: 60
|
||||
port: 80
|
||||
port: 80
|
||||
ocelot:
|
||||
configPath: /app/configuration
|
||||
@ -33,14 +33,13 @@
|
||||
{{- end -}}
|
||||
|
||||
|
||||
|
||||
{{- define "pathBase" -}}
|
||||
{{- $name := first .}}
|
||||
{{- $ctx := last .}}
|
||||
{{- if $ctx.Values.inf.k8s.suffix -}}
|
||||
{{- $suffix := include "suffix-name" $ctx -}}
|
||||
{{- printf "/%s-%s" $name $suffix -}}
|
||||
{{- if .Values.inf.k8s.suffix -}}
|
||||
{{- $suffix := include "suffix-name" . -}}
|
||||
{{- printf "%s-%s" .Values.pathBase $suffix -}}
|
||||
{{- else -}}
|
||||
{{- printf "/%s" $name -}}
|
||||
{{- .Values.pathBase -}}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
||||
|
||||
@ -60,10 +60,10 @@ spec:
|
||||
imagePullPolicy: {{ .Values.image.pullPolicy }}
|
||||
volumeMounts:
|
||||
- name: config
|
||||
mountPath: /app/configuration
|
||||
mountPath: {{ .Values.ocelot.configPath }}
|
||||
env:
|
||||
- name: PATH_BASE
|
||||
value: {{ include "pathBase" (list .Values.app.ingress.entries.webshoppingapigw .) }}
|
||||
value: {{ include "pathBase" . }}
|
||||
- name: k8sname
|
||||
value: {{ .Values.clusterName }}
|
||||
{{- if .Values.env.values -}}
|
||||
|
||||
@ -1,5 +1,6 @@
|
||||
{{- if .Values.ingress.enabled -}}
|
||||
{{- $ingressPath := include "pathBase" (list .Values.app.ingress.entries.webshoppingapigw .) -}}
|
||||
{{- $ingressPath := include "pathBase" . -}}
|
||||
{{- $serviceName := .Values.app.svc.webshoppingapigw -}}
|
||||
apiVersion: extensions/v1beta1
|
||||
kind: Ingress
|
||||
metadata:
|
||||
@ -23,11 +24,13 @@ spec:
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
rules:
|
||||
- host: {{ .Values.inf.k8s.dns }}
|
||||
{{- range .Values.ingress.hosts }}
|
||||
- host: {{ . }}
|
||||
http:
|
||||
paths:
|
||||
- path: {{ $ingressPath }}
|
||||
backend:
|
||||
serviceName: {{ .Values.app.svc.webshoppingapigw }}
|
||||
serviceName: {{ $serviceName }}
|
||||
servicePort: http
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
||||
@ -62,3 +62,5 @@ probes:
|
||||
initialDelaySeconds: 90
|
||||
periodSeconds: 60
|
||||
port: 80
|
||||
ocelot:
|
||||
configPath: /app/configuration
|
||||
@ -29,7 +29,7 @@ app: # app global settings
|
||||
catalog: catalog # service name for catalog api
|
||||
ordering: ordering # service name for ordering api
|
||||
orderingbackgroundtasks: orderingbackgroundtasks # service name for orderingbackgroundtasks
|
||||
orderingsignalrhub: ordering-signalrhub # service name for orderingsignalrhub
|
||||
orderingsignalrhub: ordering-signalrhub # service name for orderingsignalrhub
|
||||
identity: identity # service name for identity api
|
||||
mvc: webmvc # service name for web mvc
|
||||
spa: webspa # service name for web spa
|
||||
|
||||
@ -15,5 +15,5 @@ data:
|
||||
urls__IdentityUrl: http://{{ $identity }}
|
||||
basket__EnableLoadTest: "{{ .Values.inf.misc.useLoadTest }}"
|
||||
all__EventBusConnection: {{ .Values.inf.eventbus.constr }}
|
||||
all__InstrumentationKey: {{ .Values.inf.appinsights.key }}
|
||||
all__InstrumentationKey: "{{ .Values.inf.appinsights.key }}"
|
||||
all__UseAzureServiceBus: "{{ .Values.inf.eventbus.useAzure }}"
|
||||
37
k8s/helm/basket-api/templates/ingress.yaml
Normal file
@ -0,0 +1,37 @@
|
||||
{{- if .Values.ingress.enabled -}}
|
||||
{{- $ingressPath := include "pathBase" . -}}
|
||||
{{- $serviceName := .Values.app.svc.basket -}}
|
||||
|
||||
apiVersion: extensions/v1beta1
|
||||
kind: Ingress
|
||||
metadata:
|
||||
name: {{ template "basket-api.fullname" . }}
|
||||
labels:
|
||||
app: {{ template "basket-api.name" . }}
|
||||
chart: {{ template "basket-api.chart" . }}
|
||||
release: {{ .Release.Name }}
|
||||
heritage: {{ .Release.Service }}
|
||||
{{- with .Values.ingress.annotations }}
|
||||
annotations:
|
||||
{{ toYaml . | indent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
{{- if .Values.ingress.tls }}
|
||||
tls:
|
||||
{{- range .Values.ingress.tls }}
|
||||
- hosts:
|
||||
- {{ .Values.inf.k8s.dns }}
|
||||
secretName: {{ .secretName }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
rules:
|
||||
{{- range .Values.ingress.hosts }}
|
||||
- host: {{ . }}
|
||||
http:
|
||||
paths:
|
||||
- path: {{ $ingressPath }}
|
||||
backend:
|
||||
serviceName: {{ $serviceName }}
|
||||
servicePort: http
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
@ -53,3 +53,6 @@ probes:
|
||||
initialDelaySeconds: 90
|
||||
periodSeconds: 60
|
||||
port: 80
|
||||
|
||||
ingress:
|
||||
enabled: false
|
||||
@ -16,5 +16,5 @@ data:
|
||||
catalog__PicBaseUrl: http://{{ $webshoppingapigw }}/api/v1/c/catalog/items/[0]/pic/
|
||||
catalog__AzureStorageEnabled: "{{ .Values.inf.misc.useAzureStorage }}"
|
||||
all__EventBusConnection: {{ .Values.inf.eventbus.constr }}
|
||||
all__InstrumentationKey: {{ .Values.inf.appinsights.key }}
|
||||
all__InstrumentationKey: "{{ .Values.inf.appinsights.key }}"
|
||||
all__UseAzureServiceBus: "{{ .Values.inf.eventbus.useAzure }}"
|
||||
37
k8s/helm/catalog-api/templates/ingress.yaml
Normal file
@ -0,0 +1,37 @@
|
||||
{{- if .Values.ingress.enabled -}}
|
||||
{{- $ingressPath := include "pathBase" . -}}
|
||||
{{- $serviceName := .Values.app.svc.catalog -}}
|
||||
|
||||
apiVersion: extensions/v1beta1
|
||||
kind: Ingress
|
||||
metadata:
|
||||
name: {{ template "catalog-api.fullname" . }}
|
||||
labels:
|
||||
app: {{ template "catalog-api.name" . }}
|
||||
chart: {{ template "catalog-api.chart" . }}
|
||||
release: {{ .Release.Name }}
|
||||
heritage: {{ .Release.Service }}
|
||||
{{- with .Values.ingress.annotations }}
|
||||
annotations:
|
||||
{{ toYaml . | indent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
{{- if .Values.ingress.tls }}
|
||||
tls:
|
||||
{{- range .Values.ingress.tls }}
|
||||
- hosts:
|
||||
- {{ .Values.inf.k8s.dns }}
|
||||
secretName: {{ .secretName }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
rules:
|
||||
{{- range .Values.ingress.hosts }}
|
||||
- host: {{ . }}
|
||||
http:
|
||||
paths:
|
||||
- path: {{ $ingressPath }}
|
||||
backend:
|
||||
serviceName: {{ $serviceName }}
|
||||
servicePort: http
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
116
k8s/helm/deploy-all-istio.ps1
Normal file
@ -0,0 +1,116 @@
|
||||
Param(
|
||||
[parameter(Mandatory=$false)][string]$registry,
|
||||
[parameter(Mandatory=$false)][bool]$installIstioOnSystem=$false,
|
||||
[parameter(Mandatory=$false)][string]$dockerUser,
|
||||
[parameter(Mandatory=$false)][string]$dockerPassword,
|
||||
[parameter(Mandatory=$false)][string]$externalDns="aks",
|
||||
[parameter(Mandatory=$false)][string]$dnsname="eshoptestistio",
|
||||
[parameter(Mandatory=$false)][string]$appName="eshop",
|
||||
[parameter(Mandatory=$false)][bool]$deployInfrastructure=$true,
|
||||
[parameter(Mandatory=$false)][string]$kialiuser="admin",
|
||||
[parameter(Mandatory=$false)][string]$kialipasswrd="admin",
|
||||
[parameter(Mandatory=$false)][bool]$clean=$true,
|
||||
[parameter(Mandatory=$false)][string]$aksName="",
|
||||
[parameter(Mandatory=$false)][string]$aksRg="",
|
||||
[parameter(Mandatory=$false)][string]$imageTag="latest",
|
||||
[parameter(Mandatory=$false)][bool]$useLocalk8s=$false
|
||||
)
|
||||
|
||||
$dns = $externalDns
|
||||
|
||||
# Instalamos Istio
|
||||
# Specify the Istio version that will be leveraged throughout these instructions
|
||||
$ISTIO_VERSION="1.0.6"
|
||||
|
||||
# Windows
|
||||
$ProgressPreference = 'SilentlyContinue';
|
||||
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12
|
||||
Invoke-WebRequest -URI "https://github.com/istio/istio/releases/download/$ISTIO_VERSION/istio-$ISTIO_VERSION-win.zip" -OutFile "istio-$ISTIO_VERSION.zip"
|
||||
Remove-Item istio-$ISTIO_VERSION -Recurse -ErrorAction Ignore
|
||||
Expand-Archive -Path "istio-$ISTIO_VERSION.zip" -DestinationPath .
|
||||
|
||||
if($installIstioOnSystem -eq $true) {
|
||||
New-Item -ItemType Directory -Force -Path "C:\Program Files\Istio"
|
||||
mv ./istio-$ISTIO_VERSION/bin/istioctl.exe "C:\Program Files/Istio/"
|
||||
$PATH = [environment]::GetEnvironmentVariable("PATH", "User")
|
||||
[environment]::SetEnvironmentVariable("PATH", $PATH + "; C:\Program Files\Istio", "User")
|
||||
}
|
||||
# Primero Desinstalamos cualquier cosa que haya en el cluster
|
||||
if ($clean -eq $true) {
|
||||
Write-Host "Cleaning previous helm releases..." -ForegroundColor Green
|
||||
helm delete --purge $(helm ls -q)
|
||||
kubectl delete -f istio-$ISTIO_VERSION/install/kubernetes/helm/istio/templates/crds.yaml -n istio-system
|
||||
Write-Host "Previous releases deleted" -ForegroundColor Green
|
||||
}
|
||||
|
||||
Write-Host "Generating Kiali Credentials" -ForegroundColor Green
|
||||
#generamos la credenciales para que kiali arranque sin problemas
|
||||
kubectl -n istio-system create secret generic kiali --from-literal=username=$kialiuser --from-literal=passphrase=$kialipasswrd
|
||||
|
||||
|
||||
Write-Host "Deploying Istio in the cluster" -ForegroundColor Green
|
||||
helm install istio-$ISTIO_VERSION/install/kubernetes/helm/istio --wait --name istio --namespace istio-system --set global.controlPlaneSecurityEnabled=true --set grafana.enabled=true --set tracing.enabled=true --set kiali.enabled=true
|
||||
|
||||
Write-Host "Setting Up Gateway"
|
||||
kubectl delete gateway istio-autogenerated-k8s-ingress -n istio-system
|
||||
kubectl apply -f ./istio/gateway.yml
|
||||
|
||||
if ($useLocalk8s -eq $true) {
|
||||
$dns="localhost"
|
||||
$externalDns="localhost"
|
||||
}
|
||||
else {
|
||||
Write-Host "Resolving DNS to Gateway public IP" -ForegroundColor Green
|
||||
$ipaddress = $(kubectl get service istio-ingressgateway -n istio-system)[1] | %{ $_.Split(' ')[9];}
|
||||
$query = "[?ipAddress!=null]|[?contains([ipAddress], '$ipaddress')].[id]"
|
||||
$resid = az network public-ip list --query $query --output tsv
|
||||
$jsonresponse = az network public-ip update --ids $resid --dns-name $dnsname
|
||||
$externalDns = ($jsonresponse | ConvertFrom-Json).dnsSettings.fqdn
|
||||
Write-Host "$externalDns is pointing to Cluster public ip $ipaddress"
|
||||
}
|
||||
|
||||
$useCustomRegistry=$false
|
||||
if (-not [string]::IsNullOrEmpty($registry)) {
|
||||
$useCustomRegistry=$true
|
||||
if ([string]::IsNullOrEmpty($dockerUser) -or [string]::IsNullOrEmpty($dockerPassword)) {
|
||||
Write-Host "Error: Must use -dockerUser AND -dockerPassword if specifying custom registry" -ForegroundColor Red
|
||||
exit 1
|
||||
}
|
||||
}
|
||||
Write-Host "Begin eShopOnContainers installation using Helm" -ForegroundColor Green
|
||||
|
||||
$infras = ("sql-data", "nosql-data", "rabbitmq", "keystore-data", "basket-data")
|
||||
$charts = ("eshop-common", "apigwmm", "apigwms", "apigwwm", "apigwws", "basket-api","catalog-api", "identity-api", "locations-api", "marketing-api", "mobileshoppingagg","ordering-api","ordering-backgroundtasks","ordering-signalrhub", "payment-api", "webmvc", "webshoppingagg", "webspa", "webstatus", "webhooks-api", "webhooks-web")
|
||||
|
||||
if ($deployInfrastructure) {
|
||||
foreach ($infra in $infras) {
|
||||
Write-Host "Installing infrastructure: $infra" -ForegroundColor Green
|
||||
helm install --values app.yaml --values inf.yaml --set app.name=$appName --set inf.k8s.dns=$externalDns --name="$appName-$infra" $infra
|
||||
}
|
||||
}
|
||||
|
||||
foreach ($chart in $charts) {
|
||||
Write-Host "Installing: $chart" -ForegroundColor Green
|
||||
if ($useCustomRegistry) {
|
||||
helm install --set inf.registry.server=$registry --set inf.registry.login=$dockerUser --set inf.registry.pwd=$dockerPassword --set inf.registry.secretName=eshop-docker-scret --values app.yaml --values inf.yaml --values $ingressValuesFile --set app.name=$appName --set inf.k8s.dns=$dns --set image.tag=$imageTag --set image.pullPolicy=Always --name="$appName-$chart" $chart
|
||||
}
|
||||
else {
|
||||
if ($chart -ne "eshop-common") { # eshop-common is ignored when no secret must be deployed
|
||||
helm install --values app.yaml --values inf.yaml --set app.name=$appName --set inf.k8s.dns=$externalDns --set image.tag=$imageTag --set image.pullPolicy=Always --name="$appName-$chart" $chart
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
Write-Host "helm charts installed." -ForegroundColor Green
|
||||
Write-Host "Appling Virtual Services for routing." -ForegroundColor Green
|
||||
kubectl apply -f ./istio/virtualservices.yml
|
||||
|
||||
Remove-Item istio-$ISTIO_VERSION -Recurse -ErrorAction Ignore
|
||||
Remove-Item istio-$ISTIO_VERSION.zip -Recurse -ErrorAction Ignore
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
@ -5,11 +5,13 @@ Param(
|
||||
[parameter(Mandatory=$false)][string]$externalDns,
|
||||
[parameter(Mandatory=$false)][string]$appName="eshop",
|
||||
[parameter(Mandatory=$false)][bool]$deployInfrastructure=$true,
|
||||
[parameter(Mandatory=$false)][bool]$deployCharts=$true,
|
||||
[parameter(Mandatory=$false)][bool]$clean=$true,
|
||||
[parameter(Mandatory=$false)][string]$aksName="",
|
||||
[parameter(Mandatory=$false)][string]$aksRg="",
|
||||
[parameter(Mandatory=$false)][string]$imageTag="latest",
|
||||
[parameter(Mandatory=$false)][bool]$useLocalk8s=$false
|
||||
[parameter(Mandatory=$false)][bool]$useLocalk8s=$false,
|
||||
[parameter(Mandatory=$false)][bool]$useLocalImages=$false
|
||||
)
|
||||
|
||||
$dns = $externalDns
|
||||
@ -21,6 +23,12 @@ if ($useLocalk8s -eq $true) {
|
||||
$dns="localhost"
|
||||
}
|
||||
|
||||
$pullPolicy = "Always"
|
||||
|
||||
if ($useLocalImages -eq $true) {
|
||||
$pullPolicy = "IfNotPresent"
|
||||
}
|
||||
|
||||
if ($externalDns -eq "aks") {
|
||||
if ([string]::IsNullOrEmpty($aksName) -or [string]::IsNullOrEmpty($aksRg)) {
|
||||
Write-Host "Error: When using -dns aks, MUST set -aksName and -aksRg too." -ForegroundColor Red
|
||||
@ -44,7 +52,7 @@ if ([string]::IsNullOrEmpty($dns)) {
|
||||
|
||||
if ($clean) {
|
||||
Write-Host "Cleaning previous helm releases..." -ForegroundColor Green
|
||||
helm delete --purge $(helm ls -q)
|
||||
helm delete --purge $(helm ls -q eshop)
|
||||
Write-Host "Previous releases deleted" -ForegroundColor Green
|
||||
}
|
||||
|
||||
@ -66,24 +74,28 @@ $charts = ("eshop-common", "apigwmm", "apigwms", "apigwwm", "apigwws", "basket-a
|
||||
if ($deployInfrastructure) {
|
||||
foreach ($infra in $infras) {
|
||||
Write-Host "Installing infrastructure: $infra" -ForegroundColor Green
|
||||
helm install --values app.yaml --values inf.yaml --values $ingressValuesFile --set app.name=$appName --set inf.k8s.dns=$dns --name="$appName-$infra" $infra
|
||||
helm install --values app.yaml --values inf.yaml --values $ingressValuesFile --set app.name=$appName --set inf.k8s.dns=$dns --set "ingress.hosts={$dns}" --name="$appName-$infra" $infra
|
||||
}
|
||||
}
|
||||
else {
|
||||
Write-Host "eShopOnContainers infrastructure (bbdd, redis, ...) charts aren't installed (-deployCharts is false)" -ForegroundColor Yellow
|
||||
}
|
||||
|
||||
foreach ($chart in $charts) {
|
||||
Write-Host "Installing: $chart" -ForegroundColor Green
|
||||
if ($useCustomRegistry) {
|
||||
helm install --set inf.registry.server=$registry --set inf.registry.login=$dockerUser --set inf.registry.pwd=$dockerPassword --set inf.registry.secretName=eshop-docker-scret --values app.yaml --values inf.yaml --values $ingressValuesFile --set app.name=$appName --set inf.k8s.dns=$dns --set image.tag=$imageTag --set image.pullPolicy=Always --name="$appName-$chart" $chart
|
||||
}
|
||||
else {
|
||||
if ($chart -ne "eshop-common") { # eshop-common is ignored when no secret must be deployed
|
||||
helm install --values app.yaml --values inf.yaml --values $ingressValuesFile --set app.name=$appName --set inf.k8s.dns=$dns --set image.tag=$imageTag --set image.pullPolicy=Always --name="$appName-$chart" $chart
|
||||
if ($deployCharts) {
|
||||
foreach ($chart in $charts) {
|
||||
Write-Host "Installing: $chart" -ForegroundColor Green
|
||||
if ($useCustomRegistry) {
|
||||
helm install --set inf.registry.server=$registry --set inf.registry.login=$dockerUser --set inf.registry.pwd=$dockerPassword --set inf.registry.secretName=eshop-docker-scret --values app.yaml --values inf.yaml --values $ingressValuesFile --set app.name=$appName --set inf.k8s.dns=$dns --set "ingress.hosts={$dns}" --set image.tag=$imageTag --set image.pullPolicy=Always --name="$appName-$chart" $chart
|
||||
}
|
||||
else {
|
||||
if ($chart -ne "eshop-common") { # eshop-common is ignored when no secret must be deployed
|
||||
helm install --values app.yaml --values inf.yaml --values $ingressValuesFile --set app.name=$appName --set inf.k8s.dns=$dns --set "ingress.hosts={$dns}" --set image.tag=$imageTag --set image.pullPolicy=$pullPolicy --name="$appName-$chart" $chart
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
else {
|
||||
Write-Host "eShopOnContainers non-infrastructure charts aren't installed (-deployCharts is false)" -ForegroundColor Yellow
|
||||
}
|
||||
|
||||
Write-Host "helm charts installed." -ForegroundColor Green
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
232
k8s/helm/deploy-all.sh
Executable file
@ -0,0 +1,232 @@
|
||||
#!/usr/bin/env bash
|
||||
|
||||
# http://redsymbol.net/articles/unofficial-bash-strict-mode
|
||||
set -euo pipefail
|
||||
|
||||
usage()
|
||||
{
|
||||
cat <<END
|
||||
deploy.sh: deploys the $app_name application to a Kubernetes cluster using Helm.
|
||||
Parameters:
|
||||
--aks-name <AKS cluster name>
|
||||
The name of the AKS cluster. Required when the registry (using the -r parameter) is set to "aks".
|
||||
--aks-rg <AKS resource group>
|
||||
The resource group for the AKS cluster. Required when the registry (using the -r parameter) is set to "aks".
|
||||
-b | --build-solution
|
||||
Force a solution build before deployment (default: false).
|
||||
-d | --dns <dns or ip address> | --dns aks
|
||||
Specifies the external DNS/ IP address of the Kubernetes cluster.
|
||||
If 'aks' is set as value, the DNS value is retrieved from the AKS. --aks-name and --aks-rg are needed.
|
||||
When --use-local-k8s is specified the external DNS is automatically set to localhost.
|
||||
-h | --help
|
||||
Displays this help text and exits the script.
|
||||
--image-build
|
||||
Build images (default is to not build all images).
|
||||
--image-push
|
||||
Upload images to the container registry (default is not pushing to the custom registry)
|
||||
-n | --app-name <the name of the app>
|
||||
Specifies the name of the application (default: eshop).
|
||||
--namespace <namespace name>
|
||||
Specifies the namespace name to deploy the app. If it doesn't exists it will be created (default: eshop).
|
||||
-p | --docker-password <docker password>
|
||||
The Docker password used to logon to the custom registry, supplied using the -r parameter.
|
||||
-r | --registry <container registry>
|
||||
Specifies the container registry to use (required), e.g. myregistry.azurecr.io.
|
||||
--skip-clean
|
||||
Do not clean the Kubernetes cluster (default is to clean the cluster).
|
||||
--skip-infrastructure
|
||||
Do not deploy infrastructure resources (like sql-data, no-sql or redis).
|
||||
This is useful for production environments where infrastructure is hosted outside the Kubernetes cluster.
|
||||
-t | --tag <docker image tag>
|
||||
The tag used for the newly created docker images. Default: latest.
|
||||
-u | --docker-username <docker username>
|
||||
The Docker username used to logon to the custom registry, supplied using the -r parameter.
|
||||
--use-local-k8s
|
||||
Deploy to a locally installed Kubernetes (default: false).
|
||||
|
||||
It is assumed that the Kubernetes cluster has been granted access to the container registry.
|
||||
If using AKS and ACR see link for more info:
|
||||
https://docs.microsoft.com/en-us/azure/container-registry/container-registry-auth-aks
|
||||
|
||||
WARNING! THE SCRIPT WILL COMPLETELY DESTROY ALL DEPLOYMENTS AND SERVICES VISIBLE
|
||||
FROM THE CURRENT CONFIGURATION CONTEXT AND NAMESPACE.
|
||||
It is recommended that you check your selected namespace, 'eshop' by default, is already in use.
|
||||
Every deployment and service done in the namespace will be deleted.
|
||||
For more information see https://kubernetes.io/docs/tasks/administer-cluster/namespaces/
|
||||
|
||||
END
|
||||
}
|
||||
|
||||
app_name='eshop'
|
||||
aks_name=''
|
||||
aks_rg=''
|
||||
build_images=''
|
||||
clean='yes'
|
||||
build_solution=''
|
||||
container_registry=''
|
||||
docker_password=''
|
||||
docker_username=''
|
||||
dns=''
|
||||
image_tag='latest'
|
||||
push_images=''
|
||||
skip_infrastructure=''
|
||||
use_local_k8s=''
|
||||
namespace='eshop'
|
||||
|
||||
while [[ $# -gt 0 ]]; do
|
||||
case "$1" in
|
||||
--aks-name )
|
||||
aks_name="$2"; shift 2;;
|
||||
--aks-rg )
|
||||
aks_rg="$2"; shift 2;;
|
||||
-b | --build-solution )
|
||||
build_solution='yes'; shift ;;
|
||||
-d | --dns )
|
||||
dns="$2"; shift 2;;
|
||||
-h | --help )
|
||||
usage; exit 1 ;;
|
||||
-n | --app-name )
|
||||
app_name="$2"; shift 2;;
|
||||
-p | --docker-password )
|
||||
docker_password="$2"; shift 2;;
|
||||
-r | --registry )
|
||||
container_registry="$2"; shift 2;;
|
||||
--skip-clean )
|
||||
clean=''; shift ;;
|
||||
--image-build )
|
||||
build_images='yes'; shift ;;
|
||||
--image-push )
|
||||
push_images='yes'; shift ;;
|
||||
--skip-infrastructure )
|
||||
skip_infrastructure='yes'; shift ;;
|
||||
-t | --tag )
|
||||
image_tag="$2"; shift 2;;
|
||||
-u | --docker-username )
|
||||
docker_username="$2"; shift 2;;
|
||||
--use-local-k8s )
|
||||
use_local_k8s='yes'; shift ;;
|
||||
--namespace )
|
||||
namespace="$2"; shift 2;;
|
||||
*)
|
||||
echo "Unknown option $1"
|
||||
usage; exit 2 ;;
|
||||
esac
|
||||
done
|
||||
|
||||
if [[ $build_solution ]]; then
|
||||
echo "#################### Building $app_name solution ####################"
|
||||
dotnet publish -o obj/Docker/publish ../../eShopOnContainers-ServicesAndWebApps.sln
|
||||
fi
|
||||
|
||||
export TAG=$image_tag
|
||||
|
||||
if [[ $build_images ]]; then
|
||||
echo "#################### Building the $app_name Docker images ####################"
|
||||
docker-compose -p ../.. -f ../../docker-compose.yml build
|
||||
|
||||
# Remove temporary images
|
||||
docker rmi $(docker images -qf "dangling=true")
|
||||
fi
|
||||
|
||||
use_custom_registry=''
|
||||
|
||||
if [[ -n $container_registry ]]; then
|
||||
echo "################ Log into custom registry $container_registry ##################"
|
||||
use_custom_registry='yes'
|
||||
if [[ -z $docker_username ]] || [[ -z $docker_password ]]; then
|
||||
echo "Error: Must use -u (--docker-username) AND -p (--docker-password) if specifying custom registry"
|
||||
exit 1
|
||||
fi
|
||||
docker login -u $docker_username -p $docker_password $container_registry
|
||||
fi
|
||||
|
||||
if [[ $push_images ]]; then
|
||||
echo "#################### Pushing images to the container registry ####################"
|
||||
services=(basket.api catalog.api identity.api ordering.api marketing.api payment.api locations.api webmvc webspa webstatus)
|
||||
|
||||
if [[ -z "$(docker image ls -q --filter=reference=eshop/$service:$image_tag)" ]]; then
|
||||
image_tag=linux-$image_tag
|
||||
fi
|
||||
|
||||
for service in "${services[@]}"
|
||||
do
|
||||
echo "Pushing image for service $service..."
|
||||
docker tag "eshop/$service:$image_tag" "$container_registry/$service:$image_tag"
|
||||
docker push "$container_registry/$service:$image_tag"
|
||||
done
|
||||
fi
|
||||
|
||||
ingress_values_file="ingress_values.yaml"
|
||||
|
||||
if [[ $use_local_k8s ]]; then
|
||||
ingress_values_file="ingress_values_dockerk8s.yaml"
|
||||
dns="localhost"
|
||||
fi
|
||||
|
||||
if [[ $dns == "aks" ]]; then
|
||||
echo "#################### Begin AKS discovery based on the --dns aks setting. ####################"
|
||||
if [[ -z $aks_name ]] || [[ -z $aks_rg ]]; then
|
||||
echo "Error: When using -dns aks, MUST set -aksName and -aksRg too."
|
||||
echo ''
|
||||
usage
|
||||
exit 1
|
||||
fi
|
||||
|
||||
echo "Getting AKS cluster $aks_name AKS (in resource group $aks_rg)"
|
||||
# JMESPath queries are case sensitive and httpapplicationrouting can be lowercase sometimes
|
||||
jmespath_dnsqueries=(\
|
||||
addonProfiles.httpApplicationRouting.config.HTTPApplicationRoutingZoneName \
|
||||
addonProfiles.httpapplicationrouting.config.HTTPApplicationRoutingZoneName \
|
||||
)
|
||||
for q in "${jmespath_dnsqueries[@]}"
|
||||
do
|
||||
dns="$(az aks show -n $aks_name -g $aks_rg --query $q -o tsv)"
|
||||
if [[ -n $dns ]]; then break; fi
|
||||
done
|
||||
if [[ -z $dns ]]; then
|
||||
echo "Error: when getting DNS of AKS $aks_name (in resource group $aks_rg). Please ensure AKS has httpRouting enabled AND Azure CLI is logged in and is of version 2.0.37 or higher."
|
||||
exit 1
|
||||
fi
|
||||
echo "DNS base found is $dns. Will use $aks_name.$dns for the app!"
|
||||
dns="$aks_name.$dns"
|
||||
fi
|
||||
|
||||
# Initialization & check commands
|
||||
if [[ -z $dns ]]; then
|
||||
echo "No DNS specified. Ingress resources will be bound to public IP."
|
||||
fi
|
||||
|
||||
if [[ $clean ]]; then
|
||||
echo "Cleaning previous helm releases..."
|
||||
if [[ -z $(helm ls -q --namespace $namespace) ]]; then
|
||||
echo "No previous releases found"
|
||||
else
|
||||
helm delete --purge $(helm ls -q --namespace $namespace)
|
||||
echo "Previous releases deleted"
|
||||
waitsecs=10; while [ $waitsecs -gt 0 ]; do echo -ne "$waitsecs\033[0K\r"; sleep 1; : $((waitsecs--)); done
|
||||
fi
|
||||
fi
|
||||
|
||||
echo "#################### Begin $app_name installation using Helm ####################"
|
||||
infras=(sql-data nosql-data rabbitmq keystore-data basket-data)
|
||||
charts=(eshop-common apigwmm apigwms apigwwm apigwws basket-api catalog-api identity-api locations-api marketing-api mobileshoppingagg ordering-api ordering-backgroundtasks ordering-signalrhub payment-api webmvc webshoppingagg webspa webstatus webhooks-api webhooks-web)
|
||||
|
||||
if [[ !$skip_infrastructure ]]; then
|
||||
for infra in "${infras[@]}"
|
||||
do
|
||||
echo "Installing infrastructure: $infra"
|
||||
helm install --namespace $namespace --set "ingress.hosts={$dns}" --values app.yaml --values inf.yaml --values $ingress_values_file --set app.name=$app_name --set inf.k8s.dns=$dns --name="$app_name-$infra" $infra
|
||||
done
|
||||
fi
|
||||
|
||||
for chart in "${charts[@]}"
|
||||
do
|
||||
echo "Installing: $chart"
|
||||
if [[ $use_custom_registry ]]; then
|
||||
helm install --namespace $namespace --set "ingress.hosts={$dns}" --set inf.registry.server=$container_registry --set inf.registry.login=$docker_username --set inf.registry.pwd=$docker_password --set inf.registry.secretName=eshop-docker-scret --values app.yaml --values inf.yaml --values $ingress_values_file --set app.name=$app_name --set inf.k8s.dns=$dns --set image.tag=$image_tag --set image.pullPolicy=Always --name="$app_name-$chart" $chart
|
||||
elif [[ $chart != "eshop-common" ]]; then # eshop-common is ignored when no secret must be deployed
|
||||
helm install --namespace $namespace --set "ingress.hosts={$dns}" --values app.yaml --values inf.yaml --values $ingress_values_file --set app.name=$app_name --set inf.k8s.dns=$dns --set image.tag=$image_tag --set image.pullPolicy=Always --name="$app_name-$chart" $chart
|
||||
fi
|
||||
done
|
||||
|
||||
echo "FINISHED: Helm charts installed."
|
||||
@ -24,7 +24,7 @@ metadata:
|
||||
data:
|
||||
identity__ConnectionString: Server={{ $sqlsrv }};Initial Catalog={{ .Values.inf.sql.identity.db }};User Id={{ .Values.inf.sql.common.user }};Password={{ .Values.inf.sql.common.pwd }};
|
||||
identity__keystore: {{ .Values.inf.redis.keystore.constr }}
|
||||
all__InstrumentationKey: {{ .Values.inf.appinsights.key }}
|
||||
all__InstrumentationKey: "{{ .Values.inf.appinsights.key }}"
|
||||
mvc_e: http://{{ $mvc_url }}
|
||||
spa_e: http://{{ $spa_url }}
|
||||
locations_e: http://{{ $locations_url }}
|
||||
@ -36,5 +36,4 @@ data:
|
||||
xamarin_callback_e: http://{{ $xamarincallback }}
|
||||
webhooksapi_e: http://{{ $webhooks_url }}
|
||||
webhooksweb_e: http://{{ $webhooksweb_url }}
|
||||
|
||||
|
||||
enableDevspaces: "{{ .Values.enableDevspaces }}"
|
||||
@ -1,5 +1,6 @@
|
||||
{{- if .Values.ingress.enabled -}}
|
||||
{{- $ingressPath := include "pathBase" . -}}
|
||||
{{- $serviceName := .Values.app.svc.identity }}
|
||||
apiVersion: extensions/v1beta1
|
||||
kind: Ingress
|
||||
metadata:
|
||||
@ -23,11 +24,13 @@ spec:
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
rules:
|
||||
- host: {{ .Values.inf.k8s.dns }}
|
||||
{{- range .Values.ingress.hosts }}
|
||||
- host: {{ . }}
|
||||
http:
|
||||
paths:
|
||||
- path: {{ $ingressPath }}
|
||||
backend:
|
||||
serviceName: {{ .Values.app.svc.identity }}
|
||||
serviceName: {{ $serviceName }}
|
||||
servicePort: http
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
||||
@ -58,6 +58,8 @@ env:
|
||||
key: webhooksapi_e
|
||||
- name: WebhooksWebClient
|
||||
key: webhooksweb_e
|
||||
- name: EnableDevspaces
|
||||
key: enableDevspaces
|
||||
values:
|
||||
- name: ASPNETCORE_ENVIRONMENT
|
||||
value: Development
|
||||
@ -65,6 +67,7 @@ env:
|
||||
value: 'K8S'
|
||||
- name: IsClusterEnv
|
||||
value: 'True'
|
||||
|
||||
probes:
|
||||
liveness:
|
||||
path: /liveness
|
||||
@ -76,4 +79,6 @@ probes:
|
||||
timeoutSeconds: 5
|
||||
initialDelaySeconds: 90
|
||||
periodSeconds: 60
|
||||
port: 80
|
||||
port: 80
|
||||
|
||||
enableDevspaces: "false"
|
||||
@ -1,4 +1,4 @@
|
||||
# This heml values file defines all infrastructure used by eShopOnContainers.
|
||||
# This helm values file defines all infrastructure used by eShopOnContainers.
|
||||
# It is used on all charts, so ** MUST BE INCLUDED ** on every deployment
|
||||
|
||||
inf:
|
||||
@ -15,11 +15,11 @@ inf:
|
||||
identity:
|
||||
db: IdentityDb # Ordering API SQL db name
|
||||
marketing:
|
||||
db: MarketingDb # Marketing API SQL db name
|
||||
db: MarketingDb # Marketing API SQL db name
|
||||
webhooks:
|
||||
db: WebhooksDb # Webhooks DB
|
||||
db: WebhooksDb # Webhooks DB
|
||||
mongo:
|
||||
# host: my-nosql-data # Uncomment to use specify custom mongo host. By default nosql-data is used
|
||||
# host: my-nosql-data # Uncomment to use specify custom mongo host. By default nosql-data is used
|
||||
locations:
|
||||
database: LocationsDb
|
||||
marketing:
|
||||
|
||||
325
k8s/helm/istio/doc.md
Normal file
@ -0,0 +1,325 @@
|
||||
# Using Helm Charts to deploy eShopOnContainers to AKS with ISTIO
|
||||
|
||||
It is possible to deploy eShopOnContainers on a AKS using [Helm](https://helm.sh/) instead of custom scripts (that will be deprecated soon).
|
||||
|
||||
## Create Kubernetes cluster in AKS
|
||||
You can create the AKS cluster by using two ways:
|
||||
|
||||
- A. Use Azure CLI: Follow a procedure suing [Azure CLI like here](https://docs.microsoft.com/en-us/azure/aks/kubernetes-walkthrough), but make sure you **enable RBAC** with `--enable-rbac` in `az aks create` command.
|
||||
|
||||
- B. Use Azure's portal
|
||||
|
||||
The following steps are using the Azure portal to create the AKS cluster:
|
||||
|
||||
- Start the process by providing the general data, like in the following screenshot:
|
||||
|
||||
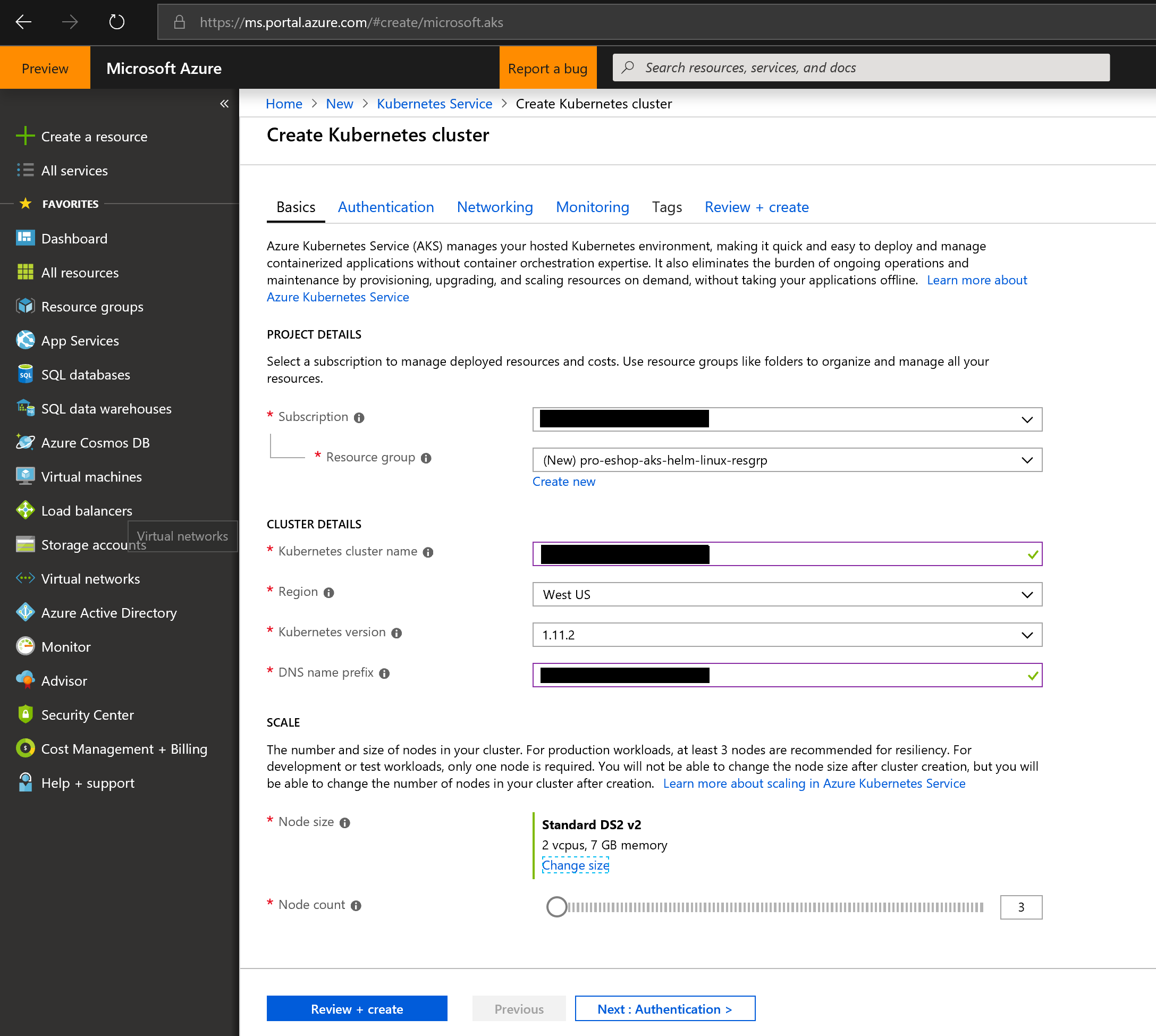
|
||||
|
||||
- Then, very important, in the next step, enable RBAC:
|
||||
|
||||
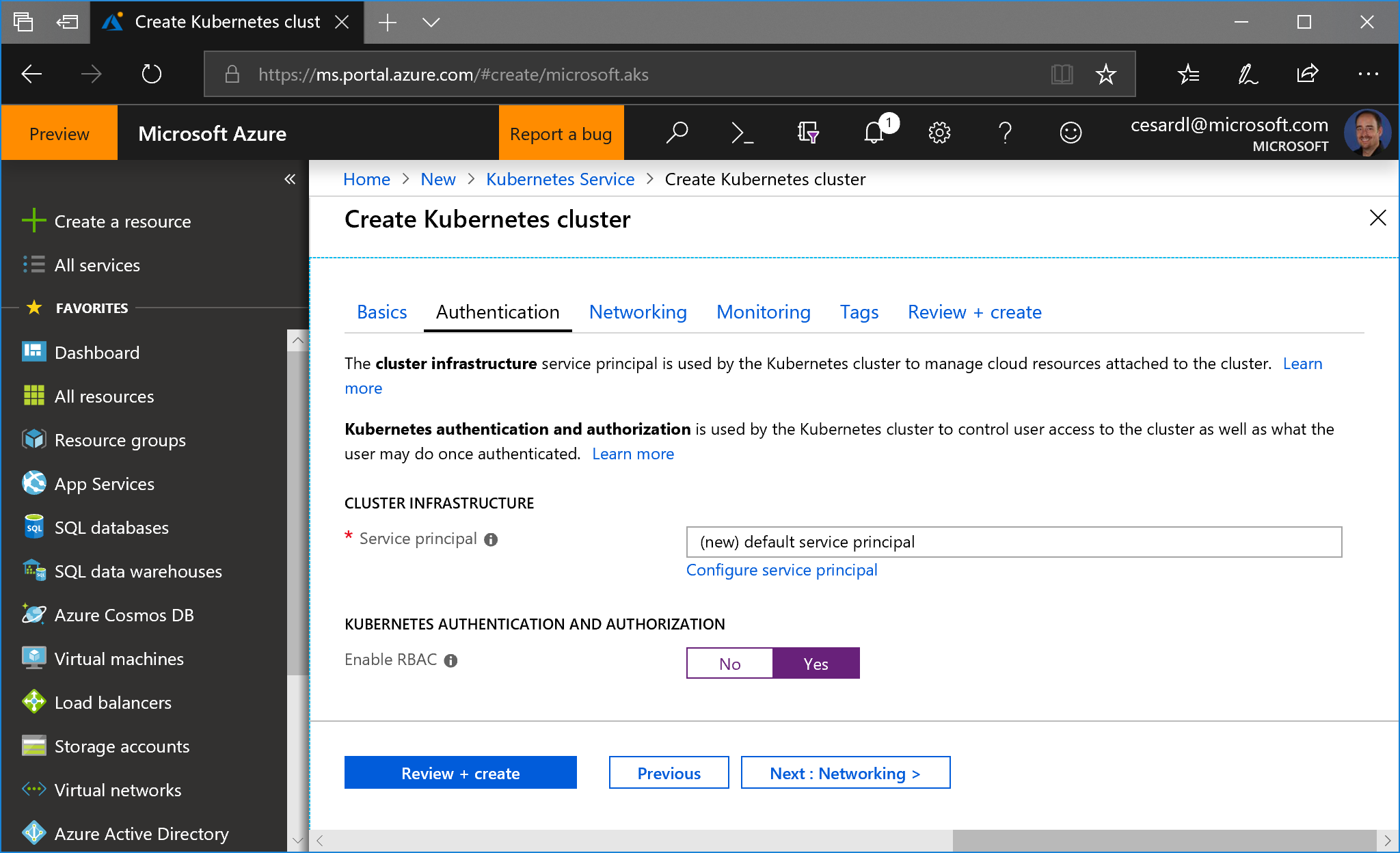
|
||||
|
||||
You can use **basic network** settings since for a test you don't need integration into any existing VNET.
|
||||
|
||||
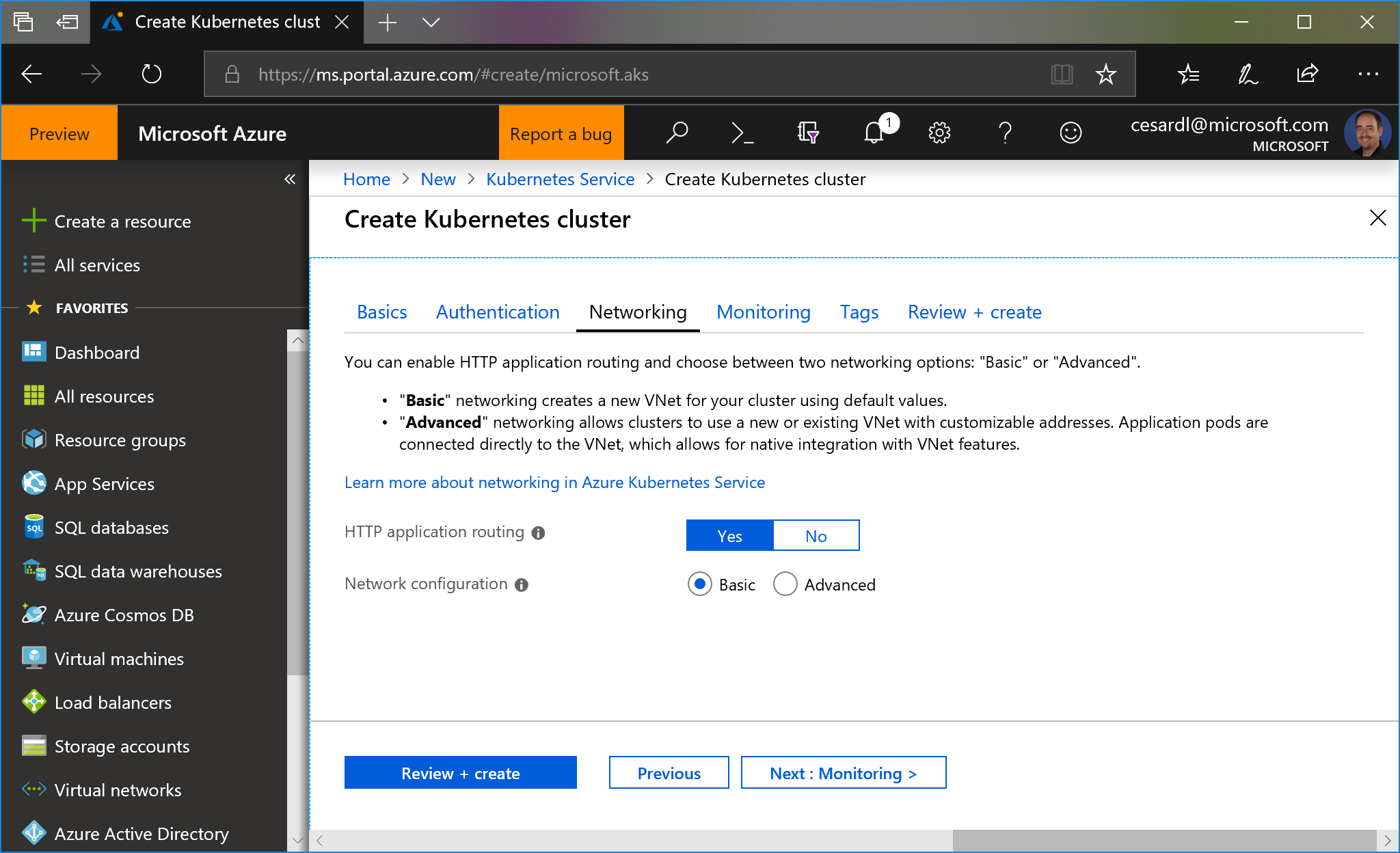
|
||||
|
||||
- You can also enable monitoring:
|
||||
|
||||
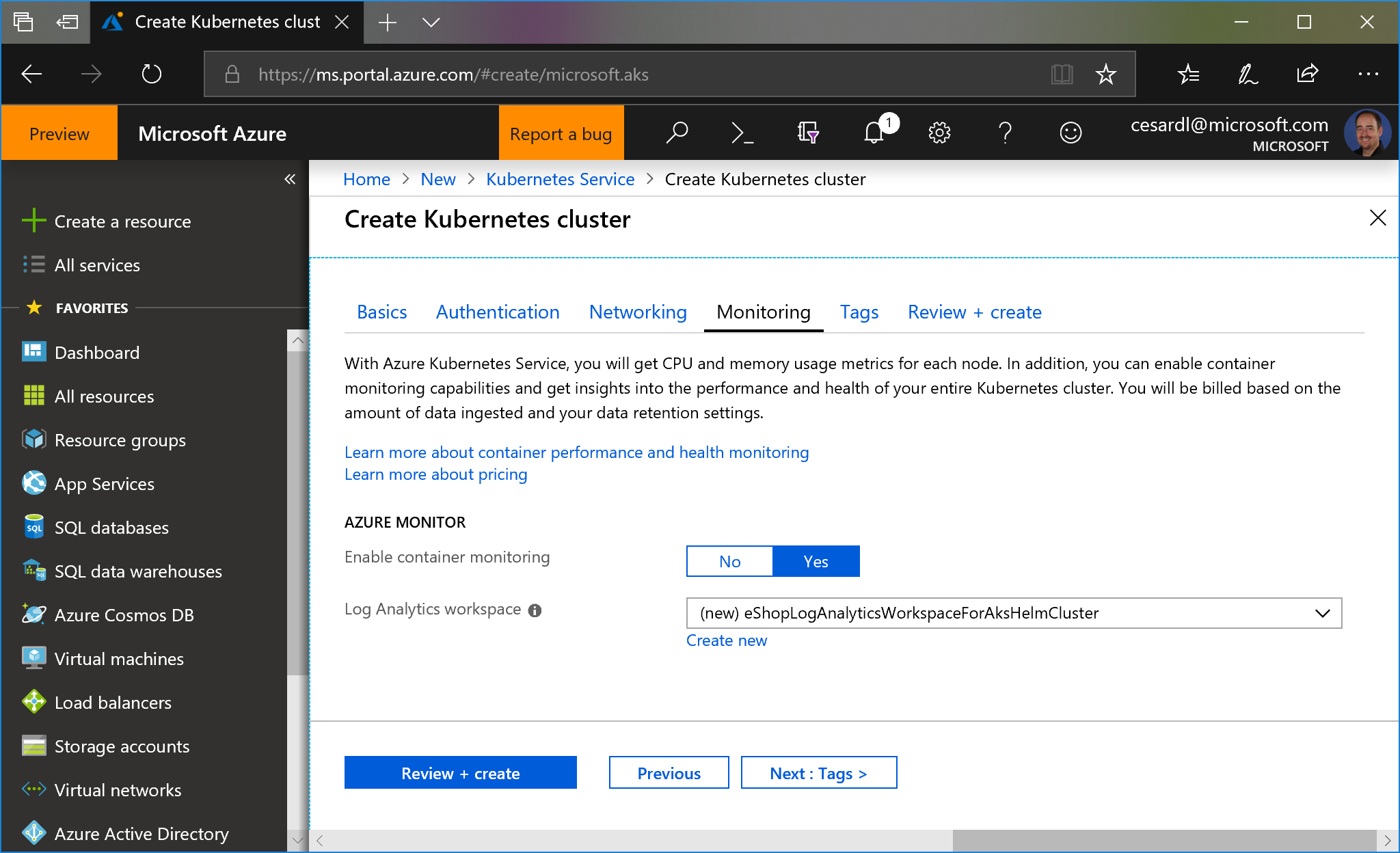
|
||||
|
||||
- Finally, create the cluster. It'll take a few minutes for it to be ready.
|
||||
|
||||
### Configure RBAC security for K8s dashboard service-account
|
||||
|
||||
In order NOT to get errors in the Kubernetes dashboard, you'll need to set the following service-account steps.
|
||||
|
||||
Here you can see the errors you might see:
|
||||
|
||||
|
||||
Now, just run the Azure CLI command to browse the Kubernetes Dashboard:
|
||||
|
||||
`az aks browse --resource-group pro-eshop-aks-helm-linux-resgrp --name pro-eshop-aks-helm-linux`
|
||||
|
||||
|
||||
|
||||
|
||||
## Additional pre-requisites
|
||||
|
||||
In addition to having an AKS cluster created in Azure and having kubectl and Azure CLI installed in your local machine and configured to use your Azure subscription, you also need the following pre-requisites:
|
||||
|
||||
### Install Helm
|
||||
|
||||
You need to have helm installed on your machine, and Tiller must be installed on the AKS. Follow these instructions on how to ['Install applications with Helm in Azure Kubernetes Service (AKS)'](https://docs.microsoft.com/en-us/azure/aks/kubernetes-helm) to setup Helm and Tiller for AKS.
|
||||
|
||||
**Note**: If your ASK cluster is not RBAC-enabled (default option in portal) you may receive following error when running a helm command:
|
||||
|
||||
```
|
||||
Error: Get http://localhost:8080/api/v1/namespaces/kube-system/configmaps?labelSelector=OWNER%!D(MISSING)TILLER: dial tcp [::1]:8080: connect: connection refused
|
||||
```
|
||||
|
||||
If so, type:
|
||||
|
||||
```
|
||||
kubectl --namespace=kube-system edit deployment/tiller-deploy
|
||||
```
|
||||
|
||||
Your default text editor will popup with the YAML definition of the tiller deploy. Search for:
|
||||
|
||||
```
|
||||
automountServiceAccountToken: false
|
||||
```
|
||||
|
||||
And change it to:
|
||||
|
||||
```
|
||||
automountServiceAccountToken: true
|
||||
```
|
||||
|
||||
Save the file and close the editor. This should reapply the deployment in the cluster. Now Helm commands should work.
|
||||
|
||||
## Install eShopOnContainers with Istio using Helm
|
||||
|
||||
All steps need to be performed on `/k8s/helm` folder. The easiest way is to use the `deploy-all-istio.ps1` script from a Powershell window:
|
||||
|
||||
```
|
||||
.\deploy-all-istio.ps1 -dnsname eshoptestistio -externalDns aks -aksName eshoptest -aksRg eshoptest -imageTag dev
|
||||
```
|
||||
|
||||
This will install all the [eShopOnContainers public images](https://hub.docker.com/u/eshop/) with tag `dev` on the AKS named `eshoptest` in the resource group `eshoptest` and with the dns url: http://**eshoptestistio**.westus.cloudapp.azure.com/ . By default all infrastructure (sql, mongo, rabbit and redis) is installed also in the cluster.
|
||||
|
||||
Once the script is run, you should see following output when using `kubectl get deployment`:
|
||||
|
||||
```
|
||||
NAME DESIRED CURRENT UP-TO-DATE AVAILABLE AGE
|
||||
eshop-apigwmm 1 1 1 1 4d
|
||||
eshop-apigwms 1 1 1 1 4d
|
||||
eshop-apigwwm 1 1 1 1 4d
|
||||
eshop-apigwws 1 1 1 1 4d
|
||||
eshop-basket-api 1 1 1 1 4d
|
||||
eshop-basket-data 1 1 1 1 4d
|
||||
eshop-catalog-api 1 1 1 1 4d
|
||||
eshop-identity-api 1 1 1 1 4d
|
||||
eshop-keystore-data 1 1 1 1 4d
|
||||
eshop-locations-api 1 1 1 1 4d
|
||||
eshop-marketing-api 1 1 1 1 4d
|
||||
eshop-mobileshoppingagg 1 1 1 1 4d
|
||||
eshop-nosql-data 1 1 1 1 4d
|
||||
eshop-ordering-api 1 1 1 1 4d
|
||||
eshop-ordering-backgroundtasks 1 1 1 1 4d
|
||||
eshop-ordering-signalrhub 1 1 1 1 4d
|
||||
eshop-payment-api 1 1 1 1 4d
|
||||
eshop-rabbitmq 1 1 1 1 4d
|
||||
eshop-sql-data 1 1 1 1 4d
|
||||
eshop-webmvc 1 1 1 1 4d
|
||||
eshop-webshoppingagg 1 1 1 1 4d
|
||||
eshop-webspa 1 1 1 1 4d
|
||||
eshop-webstatus 1 1 1 1 4d
|
||||
```
|
||||
|
||||
Every public service is exposed through the istio ingress gateway.
|
||||
Yo can see the ingress gateway public ip doing `kubectl get services -n istio-system`
|
||||
```
|
||||
grafana ClusterIP 10.0.204.87 <none> 3000/TCP 1h
|
||||
istio-citadel ClusterIP 10.0.23.86 <none> 8060/TCP,9093/TCP 1h
|
||||
istio-egressgateway ClusterIP 10.0.136.169 <none> 80/TCP,443/TCP 1h
|
||||
istio-galley ClusterIP 10.0.113.51 <none> 443/TCP,9093/TCP 1h
|
||||
istio-ingressgateway LoadBalancer 10.0.76.80 40.118.189.161 80:31380/TCP,443:31390/TCP,31400:31400/TCP,15011:31276/TCP,8060:30519/TCP,853:31698/TCP,15030:31453/TCP,15031:32362/TCP 1h
|
||||
istio-pilot ClusterIP 10.0.164.253 <none> 15010/TCP,15011/TCP,8080/TCP,9093/TCP 1h
|
||||
istio-policy ClusterIP 10.0.170.49 <none> 9091/TCP,15004/TCP,9093/TCP 1h
|
||||
istio-sidecar-injector ClusterIP 10.0.251.12 <none> 443/TCP 1h
|
||||
istio-telemetry ClusterIP 10.0.195.112 <none> 9091/TCP,15004/TCP,9093/TCP,42422/TCP 1h
|
||||
jaeger-agent ClusterIP None <none> 5775/UDP,6831/UDP,6832/UDP 1h
|
||||
jaeger-collector ClusterIP 10.0.123.98 <none> 14267/TCP,14268/TCP 1h
|
||||
jaeger-query ClusterIP 10.0.244.146 <none> 16686/TCP 1h
|
||||
kiali ClusterIP 10.0.182.12 <none> 20001/TCP 1h
|
||||
prometheus ClusterIP 10.0.136.223 <none> 9090/TCP 1h
|
||||
tracing ClusterIP 10.0.57.236 <none> 80/TCP 1h
|
||||
zipkin ClusterIP 10.0.30.57 <none> 9411/TCP 1h
|
||||
```
|
||||
|
||||
You can view the MVC client at http://[dns]/
|
||||
|
||||
## Customizing the deployment
|
||||
|
||||
### Using your own images
|
||||
|
||||
To use your own images instead of the public ones, you have to pass following additional parameters to the `deploy-all-istio.ps1` script:
|
||||
|
||||
* `registry`: Login server for the Docker registry
|
||||
* `dockerUser`: User login for the Docker registry
|
||||
* `dockerPassword`: User password for the Docker registry
|
||||
|
||||
This will deploy a secret on the cluster to connect to the specified server, and all image names deployed will be prepended with `registry/` value.
|
||||
|
||||
### Not deploying infrastructure containers
|
||||
|
||||
If you want to use external resources, use `-deployInfrastructure $false` to not deploy infrastructure containers. However **you still have to manually update the scripts to provide your own configuration** (see next section).
|
||||
|
||||
### Providing your own configuration
|
||||
|
||||
The file `inf.yaml` contains the description of the infrastructure used. File is docummented so take a look on it to understand all of its entries. If using external resources you need to edit this file according to your needs. You'll need to edit:
|
||||
|
||||
* `inf.sql.host` with the host name of the SQL Server
|
||||
* `inf.sql.common` entries to provide your SQL user, password. `Pid` is not used when using external resources (it is used to set specific product id for the SQL Server container).
|
||||
* `inf.sql.catalog`, `inf.sql.ordering`, `inf.sql.identity`: To provide the database names for catalog, ordering and identity services
|
||||
* `mongo.host`: With the host name of the Mongo DB
|
||||
* `mongo.locations`, `mongo.marketing` with the database names for locations and marketing services
|
||||
* `redis.basket.constr` with the connection string to Redis for Basket Service. Note that `redis.basket.svc` is not used when using external services
|
||||
* `redis.keystore.constr` with the connection string to Redis for Keystore Service. Note that `redis.keystore.svc` is not used when using external services
|
||||
* `eventbus.constr` with the connection string to Azure Service Bus and `eventbus.useAzure` to `true` to use Azure service bus. Note that `eventbus.svc` is not used when using external services
|
||||
|
||||
### Using Azure storage for Catalog Photos
|
||||
|
||||
Using Azure storage for catalog (and marketing) photos is not directly supported, but you can accomplish it by editing the file `k8s/helm/catalog-api/templates/configmap.yaml`. Search for lines:
|
||||
|
||||
```
|
||||
catalog__PicBaseUrl: http://{{ $webshoppingapigw }}/api/v1/c/catalog/items/[0]/pic/
|
||||
```
|
||||
|
||||
And replace it for:
|
||||
|
||||
```
|
||||
catalog__PicBaseUrl: http://<url-of-the-storage>/
|
||||
```
|
||||
|
||||
In the same way, to use Azure storage for the marketing service, have to edit the file `k8s/helm/marketing-api/templates/configmap.yaml` and replacing the line:
|
||||
|
||||
```
|
||||
marketing__PicBaseUrl: http://{{ $webshoppingapigw }}/api/v1/c/catalog/items/[0]/pic/
|
||||
```
|
||||
|
||||
by:
|
||||
|
||||
```
|
||||
marketing__PicBaseUrl: http://<url-of-the-storage>/
|
||||
```
|
||||
|
||||
# Using Helm Charts to deploy eShopOnContainers to a local Kubernetes in Windows with 'Docker for Windows'
|
||||
|
||||
## Additional pre-requisites
|
||||
|
||||
In addition to having Docker for Windows/Mac with Kubernetes enabled and having kubectl ayou also need the following pre-requisites:
|
||||
|
||||
### Install Helm
|
||||
|
||||
You need to have helm installed on your machine, and Tiller must be installed on the local Docker Kubernetes cluster. Once you have [Helm downloaded](https://helm.sh/) and installed on your machine you must:
|
||||
|
||||
1. Create the tiller service account, by running `kubectl apply -f helm-rbac.yaml` from `/k8s` folder
|
||||
2. Install tiller and configure it to use the tiller service account by typing `helm init --service-account tiller`
|
||||
|
||||
## Install eShopOnContainers with Istio using Helm
|
||||
|
||||
All steps need to be performed on `/k8s/helm` folder. The easiest way is to use the `deploy-all-istio.ps1` script from a Powershell window:
|
||||
|
||||
```
|
||||
.\deploy-all-istio.ps1 -imageTag dev -useLocalk8s $true
|
||||
```
|
||||
|
||||
The parameter `useLocalk8s` to $true, forces the script to use `localhost` as the DNS for all Helm charts.
|
||||
|
||||
This will install all the [eShopOnContainers public images](https://hub.docker.com/u/eshop/) with tag `dev` on the Docker local Kubernetes cluster. By default all infrastructure (sql, mongo, rabbit and redis) is installed also in the cluster.
|
||||
|
||||
Once the script is run, you should see following output when using `kubectl get deployment`:
|
||||
|
||||
```
|
||||
NAME DESIRED CURRENT UP-TO-DATE AVAILABLE AGE
|
||||
eshop-apigwmm 1 1 1 1 2h
|
||||
eshop-apigwms 1 1 1 1 2h
|
||||
eshop-apigwwm 1 1 1 1 2h
|
||||
eshop-apigwws 1 1 1 1 2h
|
||||
eshop-basket-api 1 1 1 1 2h
|
||||
eshop-basket-data 1 1 1 1 2h
|
||||
eshop-catalog-api 1 1 1 1 2h
|
||||
eshop-identity-api 1 1 1 1 2h
|
||||
eshop-keystore-data 1 1 1 1 2h
|
||||
eshop-locations-api 1 1 1 1 2h
|
||||
eshop-marketing-api 1 1 1 1 2h
|
||||
eshop-mobileshoppingagg 1 1 1 1 2h
|
||||
eshop-nosql-data 1 1 1 1 2h
|
||||
eshop-ordering-api 1 1 1 1 2h
|
||||
eshop-ordering-backgroundtasks 1 1 1 1 2h
|
||||
eshop-ordering-signalrhub 1 1 1 1 2h
|
||||
eshop-payment-api 1 1 1 1 2h
|
||||
eshop-rabbitmq 1 1 1 1 2h
|
||||
eshop-sql-data 1 1 1 1 2h
|
||||
eshop-webmvc 1 1 1 1 2h
|
||||
eshop-webshoppingagg 1 1 1 1 2h
|
||||
eshop-webspa 1 1 1 1 2h
|
||||
eshop-webstatus 1 1 1 1 2h
|
||||
```
|
||||
|
||||
Note that istio ingress gateway is bound to DNS localhost and the host is also "localhost". So, you can access the webspa by typing `http://localhost` and the MVC by typing `http://localhost/`
|
||||
|
||||
As this is the Docker local K8s cluster, you can see also the containers running on your machine. If you type `docker ps` you'll see all them:
|
||||
|
||||
```
|
||||
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
|
||||
fec1e3499416 a3f21ec4bd11 "/entrypoint.sh /ngi…" 9 minutes ago Up 9 minutes k8s_nginx-ingress-controller_nginx-ingress-controller-f88c75bc6-5xs2n_ingress-nginx_f1cc7094-e68f-11e8-b4b6-00155d016146_0
|
||||
76485867f032 eshop/payment.api "dotnet Payment.API.…" 2 hours ago Up 2 hours k8s_payment-api_eshop-payment-api-75d5f9bdf6-6zx2v_default_4a3cdab4-e67f-11e8-b4b6-00155d016146_1
|
||||
c2c4640ed610 eshop/marketing.api "dotnet Marketing.AP…" 2 hours ago Up 2 hours k8s_marketing-api_eshop-marketing-api-6b8c5989fd-jpxqv_default_45780626-e67f-11e8-b4b6-00155d016146_1
|
||||
85301d538574 eshop/ordering.signalrhub "dotnet Ordering.Sig…" 2 hours ago Up 2 hours k8s_ordering-signalrhub_eshop-ordering-signalrhub-58cf5ff6-cnlm8_default_4932c344-e67f-11e8-b4b6-00155d016146_1
|
||||
7a408a98000e eshop/ordering.backgroundtasks "dotnet Ordering.Bac…" 2 hours ago Up 2 hours k8s_ordering-backgroundtasks_eshop-ordering-backgroundtasks-cc8f6d4d8-ztfk7_default_47f9cf10-e67f-11e8-b4b6-00155d016146_1
|
||||
12c64b3a13e0 eshop/basket.api "dotnet Basket.API.d…" 2 hours ago Up 2 hours k8s_basket-api_eshop-basket-api-658546684d-6hlvd_default_4262d022-e67f-11e8-b4b6-00155d016146_1
|
||||
133fccfeeff3 eshop/webstatus "dotnet WebStatus.dll" 2 hours ago Up 2 hours k8s_webstatus_eshop-webstatus-7f46479dc4-bqnq7_default_4dc13eb2-e67f-11e8-b4b6-00155d016146_0
|
||||
00c6e4c52135 eshop/webspa "dotnet WebSPA.dll" 2 hours ago Up 2 hours k8s_webspa_eshop-webspa-64cb8df9cb-dcbwg_default_4cd47376-e67f-11e8-b4b6-00155d016146_0
|
||||
d4507f1f6b1a eshop/webshoppingagg "dotnet Web.Shopping…" 2 hours ago Up 2 hours k8s_webshoppingagg_eshop-webshoppingagg-cc94fc86-sxd2v_default_4be6cdb9-e67f-11e8-b4b6-00155d016146_0
|
||||
9178e26703da eshop/webmvc "dotnet WebMVC.dll" 2 hours ago Up 2 hours k8s_webmvc_eshop-webmvc-985779684-4br5z_default_4addd4d6-e67f-11e8-b4b6-00155d016146_0
|
||||
1088c281c710 eshop/ordering.api "dotnet Ordering.API…" 2 hours ago Up 2 hours k8s_ordering-api_eshop-ordering-api-fb8c548cb-k68x9_default_4740958a-e67f-11e8-b4b6-00155d016146_0
|
||||
12424156d5c9 eshop/mobileshoppingagg "dotnet Mobile.Shopp…" 2 hours ago Up 2 hours k8s_mobileshoppingagg_eshop-mobileshoppingagg-b54645d7b-rlrgh_default_46c00017-e67f-11e8-b4b6-00155d016146_0
|
||||
65463ffd437d eshop/locations.api "dotnet Locations.AP…" 2 hours ago Up 2 hours k8s_locations-api_eshop-locations-api-577fc94696-dfhq8_default_44929c4b-e67f-11e8-b4b6-00155d016146_0
|
||||
5b3431873763 eshop/identity.api "dotnet Identity.API…" 2 hours ago Up 2 hours k8s_identity-api_eshop-identity-api-85d9b79f4-s5ks7_default_43d6eb7c-e67f-11e8-b4b6-00155d016146_0
|
||||
7c8e77252459 eshop/catalog.api "dotnet Catalog.API.…" 2 hours ago Up 2 hours k8s_catalog-api_eshop-catalog-api-59fd444fb-ztvhz_default_4356705a-e67f-11e8-b4b6-00155d016146_0
|
||||
94d95d0d3653 eshop/ocelotapigw "dotnet OcelotApiGw.…" 2 hours ago Up 2 hours k8s_apigwws_eshop-apigwws-65474b979d-n99jw_default_41395473-e67f-11e8-b4b6-00155d016146_0
|
||||
bc4bbce71d5f eshop/ocelotapigw "dotnet OcelotApiGw.…" 2 hours ago Up 2 hours k8s_apigwwm_eshop-apigwwm-857c549dd8-8w5gv_default_4098d770-e67f-11e8-b4b6-00155d016146_0
|
||||
840aabcceaa9 eshop/ocelotapigw "dotnet OcelotApiGw.…" 2 hours ago Up 2 hours k8s_apigwms_eshop-apigwms-5b94dfb54b-dnmr9_default_401fc611-e67f-11e8-b4b6-00155d016146_0
|
||||
aabed7646f5b eshop/ocelotapigw "dotnet OcelotApiGw.…" 2 hours ago Up 2 hours k8s_apigwmm_eshop-apigwmm-85f96cbdb4-dhfwr_default_3ed7967a-e67f-11e8-b4b6-00155d016146_0
|
||||
49c5700def5a f06a5773f01e "docker-entrypoint.s…" 2 hours ago Up 2 hours k8s_basket-data_eshop-basket-data-66fbc788cc-csnlw_default_3e0c45fe-e67f-11e8-b4b6-00155d016146_0
|
||||
a5db4c521807 f06a5773f01e "docker-entrypoint.s…" 2 hours ago Up 2 hours k8s_keystore-data_eshop-keystore-data-5c9c85cb99-8k56s_default_3ce1a273-e67f-11e8-b4b6-00155d016146_0
|
||||
aae88fd2d810 d69a5113ceae "docker-entrypoint.s…" 2 hours ago Up 2 hours k8s_rabbitmq_eshop-rabbitmq-6b68647bc4-gr565_default_3c37ee6a-e67f-11e8-b4b6-00155d016146_0
|
||||
65d49ca9589d bbed8d0e01c1 "docker-entrypoint.s…" 2 hours ago Up 2 hours k8s_nosql-data_eshop-nosql-data-579c9d89f8-mtt95_default_3b9c1f89-e67f-11e8-b4b6-00155d016146_0
|
||||
090e0dde2ec4 bbe2822dfe38 "/opt/mssql/bin/sqls…" 2 hours ago Up 2 hours k8s_sql-data_eshop-sql-data-5c4fdcccf4-bscdb_default_3afd29b8-e67f-11e8-b4b6-00155d016146_0
|
||||
```
|
||||
|
||||
## Known issues
|
||||
|
||||
Login from the webmvc results in following error: HttpRequestException: Response status code does not indicate success: 404 (Not Found).
|
||||
|
||||
The reason is because MVC needs to access the Identity Server from both outside the container (browser) and inside the container (C# code). Thus, the configuration uses always the *external url* of the Identity Server, which in this case is just `http://localhost/identity-api`. But this external url is incorrect when used from C# code, and the web mvc can't access the identity api. This is the only case when this issue happens (and is the reason why we use 10.0.75.1 for local address in web mvc in local development mode)
|
||||
|
||||
Solving this requires some manual steps:
|
||||
|
||||
Update the configmap of Web MVC by typing (**line breaks are mandatory**) and your cluster dns name has to be the same of your environment:
|
||||
|
||||
```
|
||||
kubectl patch cm cfg-eshop-webmvc --type strategic --patch @'
|
||||
data:
|
||||
urls__IdentityUrl: http://**eshoptest**.westus.cloudapp.azure.com/identity
|
||||
urls__mvc: http://**eshoptest**.westus.cloudapp.azure.com/webmvc
|
||||
'@
|
||||
```
|
||||
|
||||
Update the configmap of Identity API by typing (**line breaks are mandatory**):
|
||||
|
||||
```
|
||||
kubectl patch cm cfg-eshop-identity-api --type strategic --patch @'
|
||||
data:
|
||||
mvc_e: http://**eshoptest**.westus.cloudapp.azure.com/webmvc
|
||||
'@
|
||||
```
|
||||
|
||||
Restart the SQL Server pod to ensure the database is recreated again:
|
||||
|
||||
```
|
||||
kubectl delete pod --selector app=sql-data
|
||||
```
|
||||
|
||||
Wait until SQL Server pod is ready to accept connections and then restart all other pods:
|
||||
|
||||
```
|
||||
kubectl delete pod --selector="app!=sql-data"
|
||||
```
|
||||
|
||||
**Note:** Pods are deleted to ensure the databases are recreated again, as identity api stores its client names and urls in the database.
|
||||
|
||||
Now, you can access the MVC app using: `http://**eshoptest**.westus.cloudapp.azure.com/`.
|
||||
|
||||
15
k8s/helm/istio/gateway.yml
Normal file
@ -0,0 +1,15 @@
|
||||
apiVersion: networking.istio.io/v1alpha3
|
||||
kind: Gateway
|
||||
metadata:
|
||||
name: istio-ingressgateway
|
||||
#namespace: istio-system
|
||||
spec:
|
||||
selector:
|
||||
istio: ingressgateway # use Istio default gateway implementation
|
||||
servers:
|
||||
- port:
|
||||
number: 80
|
||||
name: http
|
||||
protocol: HTTP
|
||||
hosts:
|
||||
- "*"
|
||||
59
k8s/helm/istio/virtualservices.yml
Normal file
@ -0,0 +1,59 @@
|
||||
apiVersion: networking.istio.io/v1alpha3
|
||||
kind: VirtualService
|
||||
metadata:
|
||||
name: webmvcvs
|
||||
namespace: default
|
||||
spec:
|
||||
hosts:
|
||||
- "*"
|
||||
gateways:
|
||||
- istio-ingressgateway
|
||||
http:
|
||||
- match:
|
||||
- uri:
|
||||
prefix: /
|
||||
route:
|
||||
- destination:
|
||||
port:
|
||||
number: 80
|
||||
host: webmvc
|
||||
---
|
||||
apiVersion: networking.istio.io/v1alpha3
|
||||
kind: VirtualService
|
||||
metadata:
|
||||
name: webshoppingapigwvs
|
||||
namespace: default
|
||||
spec:
|
||||
hosts:
|
||||
- "*"
|
||||
gateways:
|
||||
- istio-ingressgateway
|
||||
http:
|
||||
- match:
|
||||
- uri:
|
||||
prefix: /webshoppingapigw
|
||||
route:
|
||||
- destination:
|
||||
port:
|
||||
number: 80
|
||||
host: webshoppingapigw
|
||||
---
|
||||
apiVersion: networking.istio.io/v1alpha3
|
||||
kind: VirtualService
|
||||
metadata:
|
||||
name: identityvs
|
||||
namespace: default
|
||||
spec:
|
||||
hosts:
|
||||
- "*"
|
||||
gateways:
|
||||
- istio-ingressgateway
|
||||
http:
|
||||
- match:
|
||||
- uri:
|
||||
prefix: /identity
|
||||
route:
|
||||
- destination:
|
||||
port:
|
||||
number: 80
|
||||
host: identity
|
||||
@ -13,7 +13,7 @@ metadata:
|
||||
heritage: {{ .Release.Service }}
|
||||
data:
|
||||
all__EventBusConnection: {{ .Values.inf.eventbus.constr }}
|
||||
all__InstrumentationKey: {{ .Values.inf.appinsights.key }}
|
||||
all__InstrumentationKey: "{{ .Values.inf.appinsights.key }}"
|
||||
all__UseAzureServiceBus: "{{ .Values.inf.eventbus.useAzure }}"
|
||||
all_EnableLoadTest: "{{ .Values.inf.misc.useLoadTest }}"
|
||||
internalurls__IdentityUrl: http://{{ .Values.app.svc.identity }}
|
||||
|
||||
36
k8s/helm/locations-api/templates/ingress.yaml
Normal file
@ -0,0 +1,36 @@
|
||||
{{- if .Values.ingress.enabled -}}
|
||||
{{- $ingressPath := include "pathBase" . -}}
|
||||
{{- $serviceName := .Values.app.svc.locations }}
|
||||
apiVersion: extensions/v1beta1
|
||||
kind: Ingress
|
||||
metadata:
|
||||
name: {{ template "locations-api.fullname" . }}
|
||||
labels:
|
||||
app: {{ template "locations-api.name" . }}
|
||||
chart: {{ template "locations-api.chart" . }}
|
||||
release: {{ .Release.Name }}
|
||||
heritage: {{ .Release.Service }}
|
||||
{{- with .Values.ingress.annotations }}
|
||||
annotations:
|
||||
{{ toYaml . | indent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
{{- if .Values.ingress.tls }}
|
||||
tls:
|
||||
{{- range .Values.ingress.tls }}
|
||||
- hosts:
|
||||
- {{ .Values.inf.k8s.dns }}
|
||||
secretName: {{ .secretName }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
rules:
|
||||
{{- range .Values.ingress.hosts }}
|
||||
- host: {{ . }}
|
||||
http:
|
||||
paths:
|
||||
- path: {{ $ingressPath }}
|
||||
backend:
|
||||
serviceName: {{ $serviceName }}
|
||||
servicePort: http
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
@ -15,7 +15,7 @@ metadata:
|
||||
heritage: {{ .Release.Service }}
|
||||
data:
|
||||
all__EventBusConnection: {{ .Values.inf.eventbus.constr }}
|
||||
all__InstrumentationKey: {{ .Values.inf.appinsights.key }}
|
||||
all__InstrumentationKey: "{{ .Values.inf.appinsights.key }}"
|
||||
all__UseAzureServiceBus: "{{ .Values.inf.eventbus.useAzure }}"
|
||||
all_EnableLoadTest: "{{ .Values.inf.misc.useLoadTest }}"
|
||||
internalurls__IdentityUrl: http://{{ .Values.app.svc.identity }}
|
||||
|
||||
36
k8s/helm/marketing-api/templates/ingress.yaml
Normal file
@ -0,0 +1,36 @@
|
||||
{{- if .Values.ingress.enabled -}}
|
||||
{{- $ingressPath := include "pathBase" . -}}
|
||||
{{- $serviceName := .Values.app.svc.marketing }}
|
||||
apiVersion: extensions/v1beta1
|
||||
kind: Ingress
|
||||
metadata:
|
||||
name: {{ template "marketing-api.fullname" . }}
|
||||
labels:
|
||||
app: {{ template "marketing-api.name" . }}
|
||||
chart: {{ template "marketing-api.chart" . }}
|
||||
release: {{ .Release.Name }}
|
||||
heritage: {{ .Release.Service }}
|
||||
{{- with .Values.ingress.annotations }}
|
||||
annotations:
|
||||
{{ toYaml . | indent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
{{- if .Values.ingress.tls }}
|
||||
tls:
|
||||
{{- range .Values.ingress.tls }}
|
||||
- hosts:
|
||||
- {{ .Values.inf.k8s.dns }}
|
||||
secretName: {{ .secretName }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
rules:
|
||||
{{- range .Values.ingress.hosts }}
|
||||
- host: {{ . }}
|
||||
http:
|
||||
paths:
|
||||
- path: {{ $ingressPath }}
|
||||
backend:
|
||||
serviceName: {{ $serviceName }}
|
||||
servicePort: http
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
@ -10,7 +10,7 @@ metadata:
|
||||
release: {{ .Release.Name }}
|
||||
heritage: {{ .Release.Service }}
|
||||
data:
|
||||
all__InstrumentationKey: {{ .Values.inf.appinsights.key }}
|
||||
all__InstrumentationKey: "{{ .Values.inf.appinsights.key }}"
|
||||
all_EnableLoadTest: "{{ .Values.inf.misc.useLoadTest }}"
|
||||
mobileshoppingagg__keystore: {{ .Values.inf.redis.keystore.constr }}
|
||||
internalurls__basket: http://{{ .Values.app.svc.basket }}
|
||||
|
||||
36
k8s/helm/mobileshoppingagg/templates/ingress.yaml
Normal file
@ -0,0 +1,36 @@
|
||||
{{- if .Values.ingress.enabled -}}
|
||||
{{- $ingressPath := include "pathBase" . -}}
|
||||
{{- $serviceName := .Values.app.svc.mobileshoppingagg }}
|
||||
apiVersion: extensions/v1beta1
|
||||
kind: Ingress
|
||||
metadata:
|
||||
name: {{ template "mobileshoppingagg.fullname" . }}
|
||||
labels:
|
||||
app: {{ template "mobileshoppingagg.name" . }}
|
||||
chart: {{ template "mobileshoppingagg.chart" . }}
|
||||
release: {{ .Release.Name }}
|
||||
heritage: {{ .Release.Service }}
|
||||
{{- with .Values.ingress.annotations }}
|
||||
annotations:
|
||||
{{ toYaml . | indent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
{{- if .Values.ingress.tls }}
|
||||
tls:
|
||||
{{- range .Values.ingress.tls }}
|
||||
- hosts:
|
||||
- {{ .Values.inf.k8s.dns }}
|
||||
secretName: {{ .secretName }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
rules:
|
||||
{{- range .Values.ingress.hosts }}
|
||||
- host: {{ . }}
|
||||
http:
|
||||
paths:
|
||||
- path: {{ $ingressPath }}
|
||||
backend:
|
||||
serviceName: {{ $serviceName }}
|
||||
servicePort: http
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
@ -16,5 +16,5 @@ data:
|
||||
ordering__EnableLoadTest: "{{ .Values.inf.misc.useLoadTest }}"
|
||||
urls__IdentityUrl: http://{{ $identity }}
|
||||
all__EventBusConnection: {{ .Values.inf.eventbus.constr }}
|
||||
all__InstrumentationKey: {{ .Values.inf.appinsights.key }}
|
||||
all__InstrumentationKey: "{{ .Values.inf.appinsights.key }}"
|
||||
all__UseAzureServiceBus: "{{ .Values.inf.eventbus.useAzure }}"
|
||||
@ -1,10 +1,11 @@
|
||||
{{- $name := include "ordering-backgroundtasks.fullname" . -}}
|
||||
{{- $sqlsrv := include "sql-name" . -}}
|
||||
{{- $cfgname := printf "cfg-%s" $name | trunc 63 }}
|
||||
|
||||
apiVersion: v1
|
||||
kind: ConfigMap
|
||||
metadata:
|
||||
name: "cfg-{{ $name }}"
|
||||
name: "{{ $cfgname }}"
|
||||
labels:
|
||||
app: {{ template "ordering-backgroundtasks.name" . }}
|
||||
chart: {{ template "ordering-backgroundtasks.chart" .}}
|
||||
@ -14,7 +15,7 @@ data:
|
||||
ordering__ConnectionString: Server={{ $sqlsrv }};Initial Catalog={{ .Values.inf.sql.ordering.db }};User Id={{ .Values.inf.sql.common.user }};Password={{ .Values.inf.sql.common.pwd }};
|
||||
ordering__EnableLoadTest: "{{ .Values.inf.misc.useLoadTest }}"
|
||||
all__EventBusConnection: {{ .Values.inf.eventbus.constr }}
|
||||
all__InstrumentationKey: {{ .Values.inf.appinsights.key }}
|
||||
all__InstrumentationKey: "{{ .Values.inf.appinsights.key }}"
|
||||
all__UseAzureServiceBus: "{{ .Values.inf.eventbus.useAzure }}"
|
||||
graceperiodmanager__CheckUpdateTime: "{{ .Values.cfg.checkUpdateTime }}"
|
||||
graceperiodmanager__GracePeriodTime: "{{ .Values.cfg.gracePeriodTime }}"
|
||||
@ -1,11 +1,11 @@
|
||||
{{- $name := include "ordering-backgroundtasks.fullname" . -}}
|
||||
{{- $cfgname := printf "%s-%s" "cfg" $name -}}
|
||||
{{- $cfgname := printf "cfg-%s" $name | trunc 63 }}
|
||||
|
||||
apiVersion: apps/v1beta2
|
||||
kind: Deployment
|
||||
metadata:
|
||||
name: {{ template "ordering-backgroundtasks.fullname" . }}
|
||||
labels:
|
||||
ufo: {{ $cfgname}}
|
||||
app: {{ template "ordering-backgroundtasks.name" . }}
|
||||
chart: {{ template "ordering-backgroundtasks.chart" . }}
|
||||
release: {{ .Release.Name }}
|
||||
|
||||
@ -12,7 +12,7 @@ metadata:
|
||||
heritage: {{ .Release.Service }}
|
||||
data:
|
||||
all__EventBusConnection: {{ .Values.inf.eventbus.constr }}
|
||||
all__InstrumentationKey: {{ .Values.inf.appinsights.key }}
|
||||
all__InstrumentationKey: "{{ .Values.inf.appinsights.key }}"
|
||||
all__UseAzureServiceBus: "{{ .Values.inf.eventbus.useAzure }}"
|
||||
signalr__StoreConnectionString: {{ .Values.inf.redis.keystore.constr }}
|
||||
urls__IdentityUrl: http://{{ $identity }}
|
||||
@ -11,5 +11,5 @@ metadata:
|
||||
heritage: {{ .Release.Service }}
|
||||
data:
|
||||
all__EventBusConnection: {{ .Values.inf.eventbus.constr }}
|
||||
all__InstrumentationKey: {{ .Values.inf.appinsights.key }}
|
||||
all__InstrumentationKey: "{{ .Values.inf.appinsights.key }}"
|
||||
all__UseAzureServiceBus: "{{ .Values.inf.eventbus.useAzure }}"
|
||||
@ -16,5 +16,5 @@ data:
|
||||
urls__IdentityUrl: http://{{ $identity }}
|
||||
urls__IdentityUrlExternal: http://{{ $identity }}
|
||||
all__EventBusConnection: {{ .Values.inf.eventbus.constr }}
|
||||
all__InstrumentationKey: {{ .Values.inf.appinsights.key }}
|
||||
all__InstrumentationKey: "{{ .Values.inf.appinsights.key }}"
|
||||
all__UseAzureServiceBus: "{{ .Values.inf.eventbus.useAzure }}"
|
||||
@ -1,5 +1,6 @@
|
||||
{{- if .Values.ingress.enabled -}}
|
||||
{{- $ingressPath := include "pathBase" . -}}
|
||||
{{- $serviceName := .Values.app.svc.webhooks }}
|
||||
apiVersion: extensions/v1beta1
|
||||
kind: Ingress
|
||||
metadata:
|
||||
@ -23,11 +24,13 @@ spec:
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
rules:
|
||||
- host: {{ .Values.inf.k8s.dns }}
|
||||
{{- range .Values.ingress.hosts }}
|
||||
- host: {{ . }}
|
||||
http:
|
||||
paths:
|
||||
- path: {{ $ingressPath }}
|
||||
backend:
|
||||
serviceName: {{ .Values.app.svc.webhooks }}
|
||||
serviceName: {{ $serviceName }}
|
||||
servicePort: http
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
||||
@ -2,7 +2,6 @@
|
||||
{{- $identity := include "url-of" (list .Values.app.ingress.entries.identity .) -}}
|
||||
{{- $webshoppingapigw := include "url-of" (list .Values.app.ingress.entries.webshoppingapigw .) -}}
|
||||
{{- $mvc := include "url-of" (list .Values.app.ingress.entries.mvc .) -}}
|
||||
{{- $mongo := include "mongo-name" . -}}
|
||||
|
||||
|
||||
apiVersion: v1
|
||||
@ -15,7 +14,7 @@ metadata:
|
||||
release: {{ .Release.Name }}
|
||||
heritage: {{ .Release.Service }}
|
||||
data:
|
||||
all__InstrumentationKey: {{ .Values.inf.appinsights.key }}
|
||||
all__InstrumentationKey: "{{ .Values.inf.appinsights.key }}"
|
||||
all__UseAzureServiceBus: "{{ .Values.inf.eventbus.useAzure }}"
|
||||
all_EnableLoadTest: "{{ .Values.inf.misc.useLoadTest }}"
|
||||
webmvc__keystore: {{ .Values.inf.redis.keystore.constr }}
|
||||
|
||||